Third-Party Risk Management (TPRM)
Protect sensitive data and monitor the behaviors and activities of all users
Teramind Provides Third-Party Risk Management (TPRM), Threat Detection and Data Loss Prevention in a Single Platform
Third-party vendors, partners, consultants, and outsourced contractors often have privileged access to a company’s internal systems. As privileged insiders, they can change system configuration, steal company data, and sabotage critical infrastructure
Teramind offers an unrivaled third-party risk management platform to monitor, control, and protect third-party contractors. Decrease the chances of irreversible damage to your business and help improve IT safety measures with Teramind’s third-party risk management.
Authentication and Access Control
Use third-party vendor risk management to identity-based authentication and segregate access control. TPRM prevents unauthorized access or sharing of confidential data outside your organization
Set up an access account for each third-party or contractor that is going to need authorized clearance
Track what each contractor, freelancer, or other third-partiy is doing at any given time
Create profiles for regular, privileged, and contract/external users using Teramind’s third-party risk management software
Segment access to third-parties based on their profiles and what access needs they require
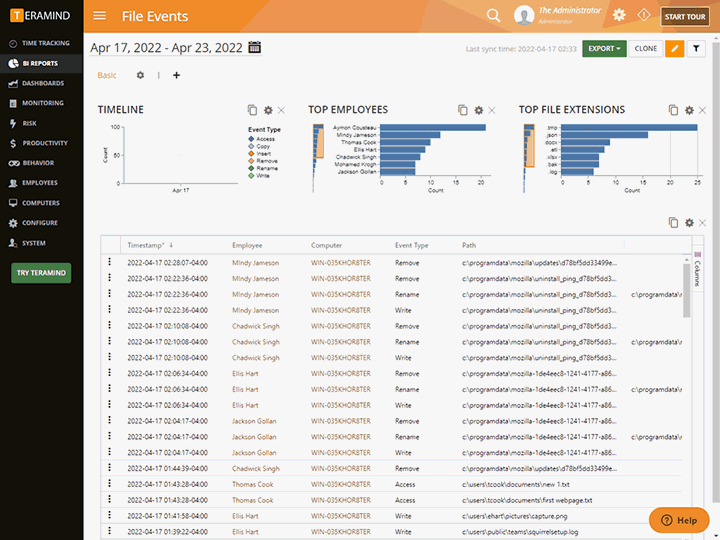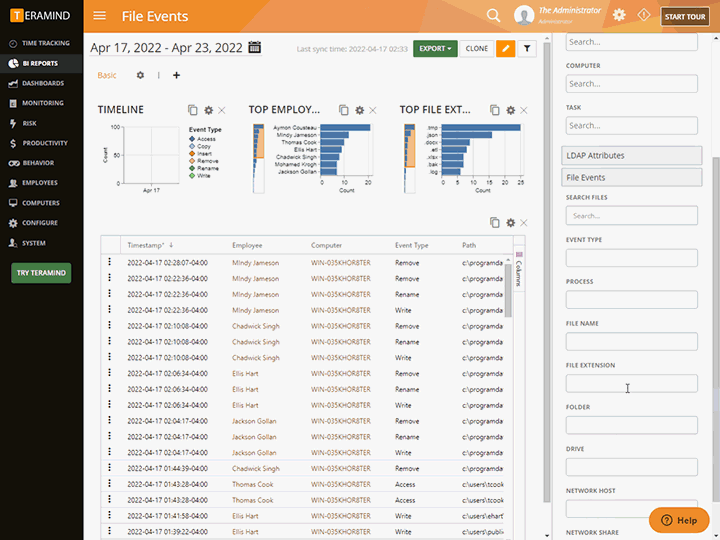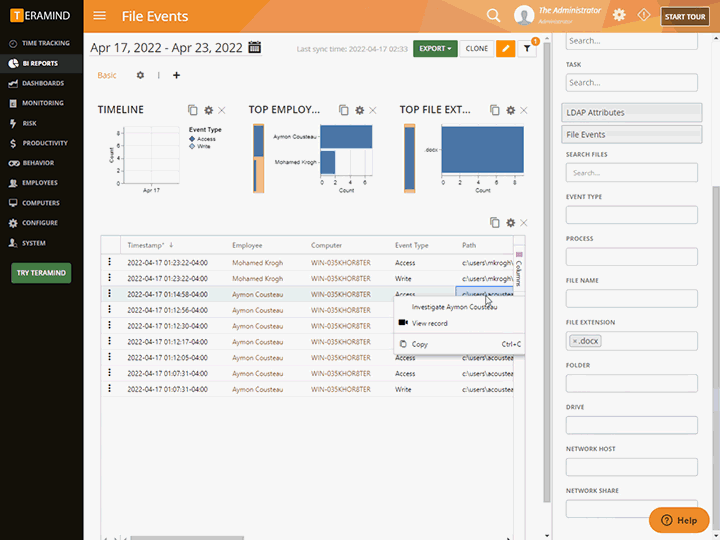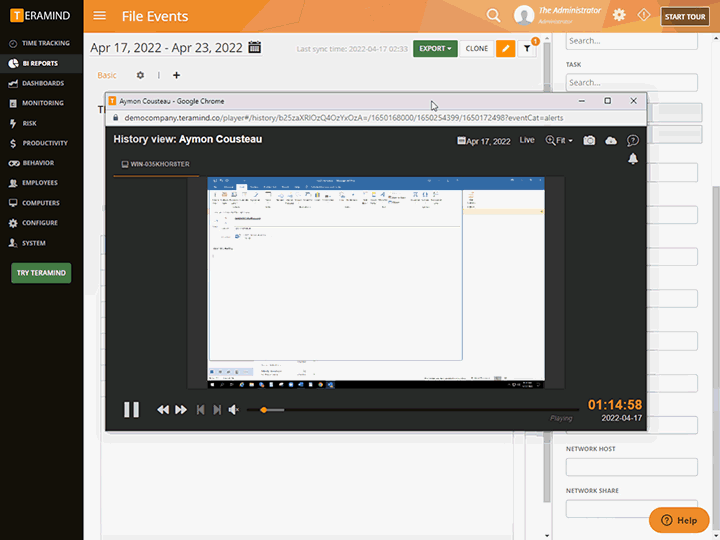
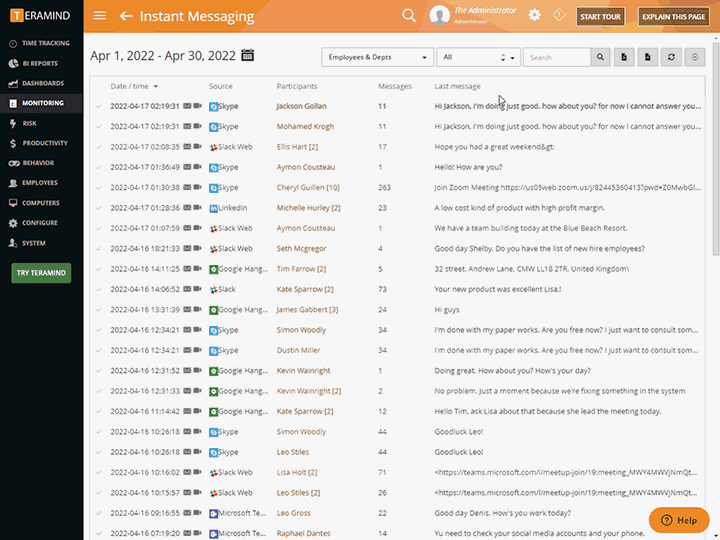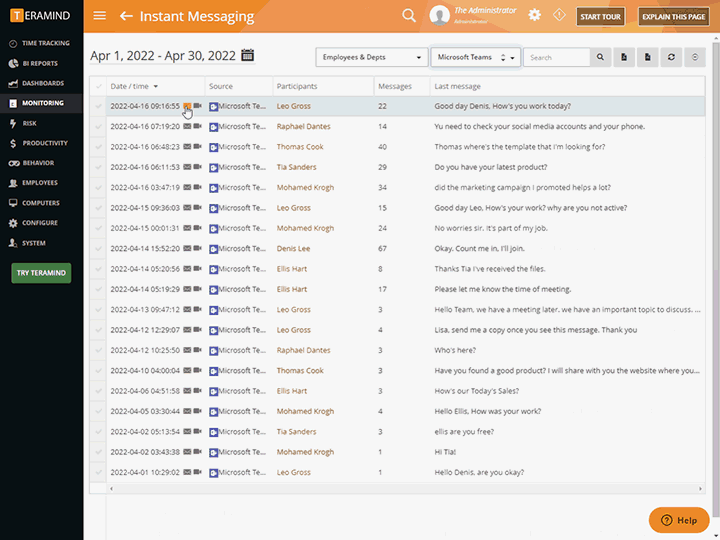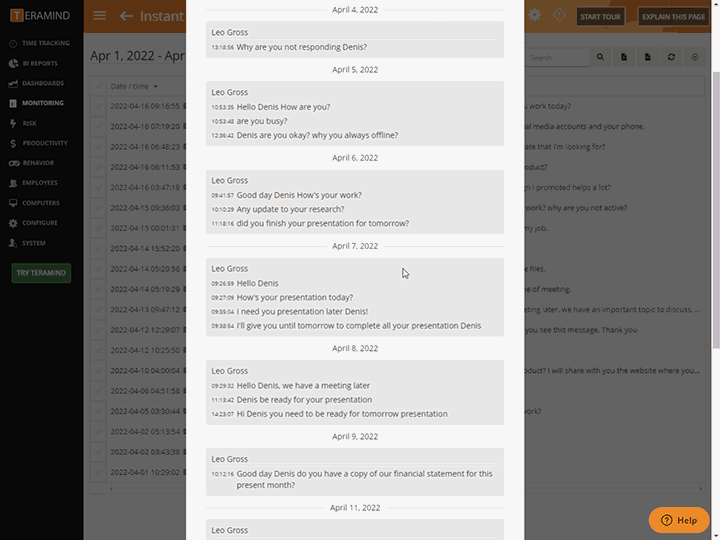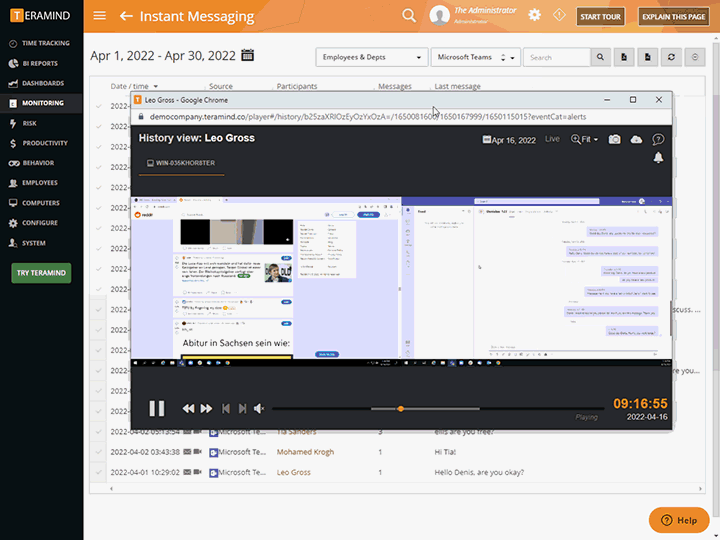
Session Recording and Playback
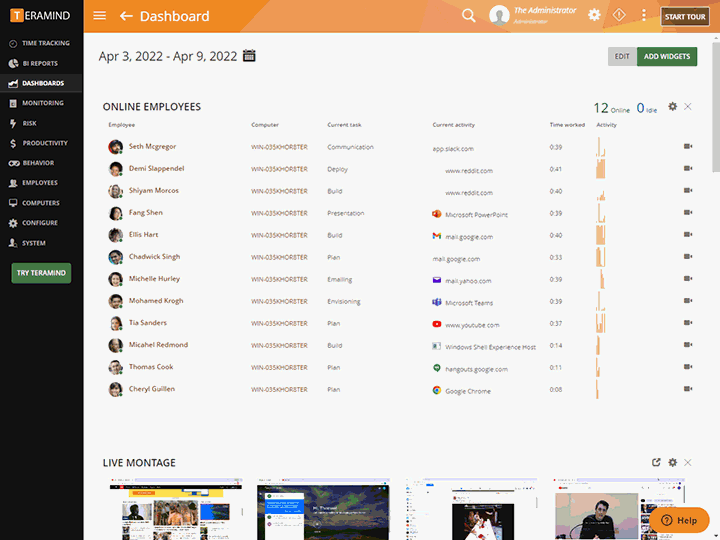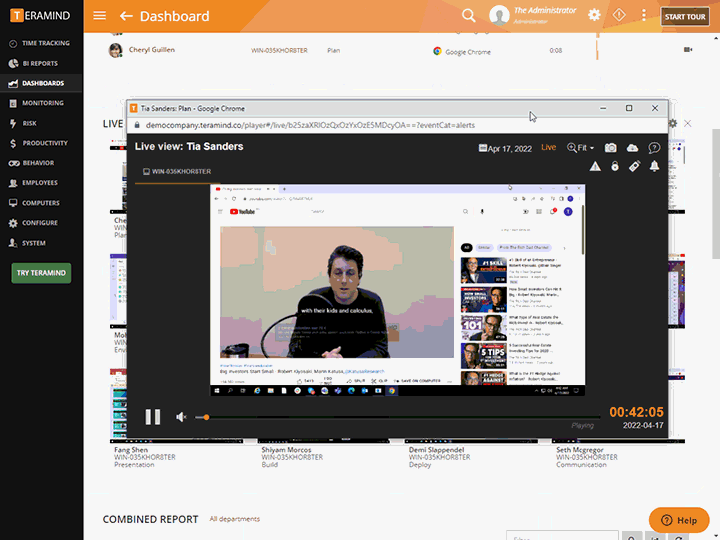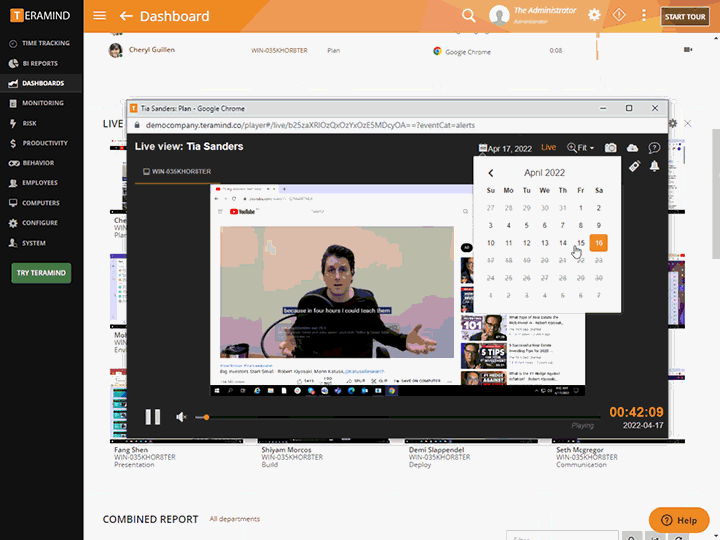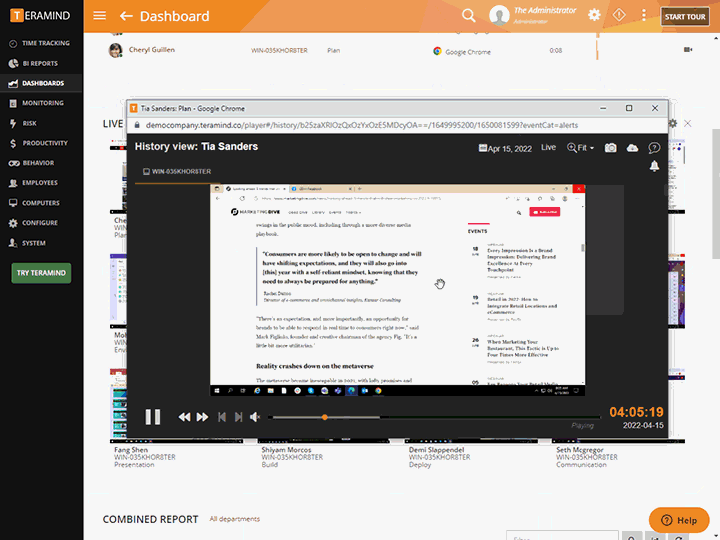
Teramind’s third-party management has live view and history playback to provide seamless real-time streaming of third-party vendor activity
Quickly view live sessions of active users or playback historical sessions directly on the dashboard
Collect extensive visual history of all actions taken for both on-site and remote vendors
Search user sessions and activity using metadata, regular expression, and natural language
Tag recordings by time and date, highlighting any alerts and notifications
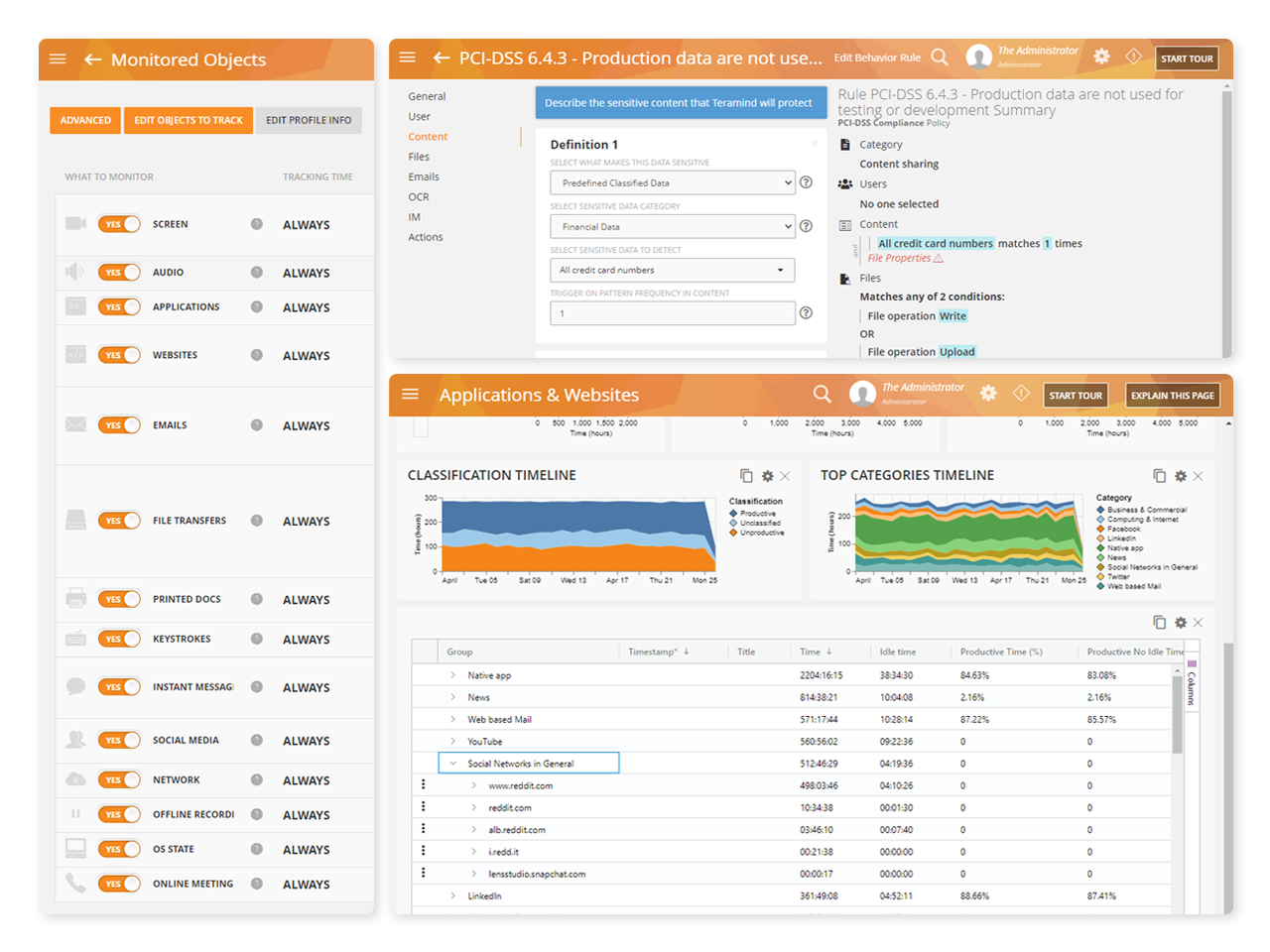
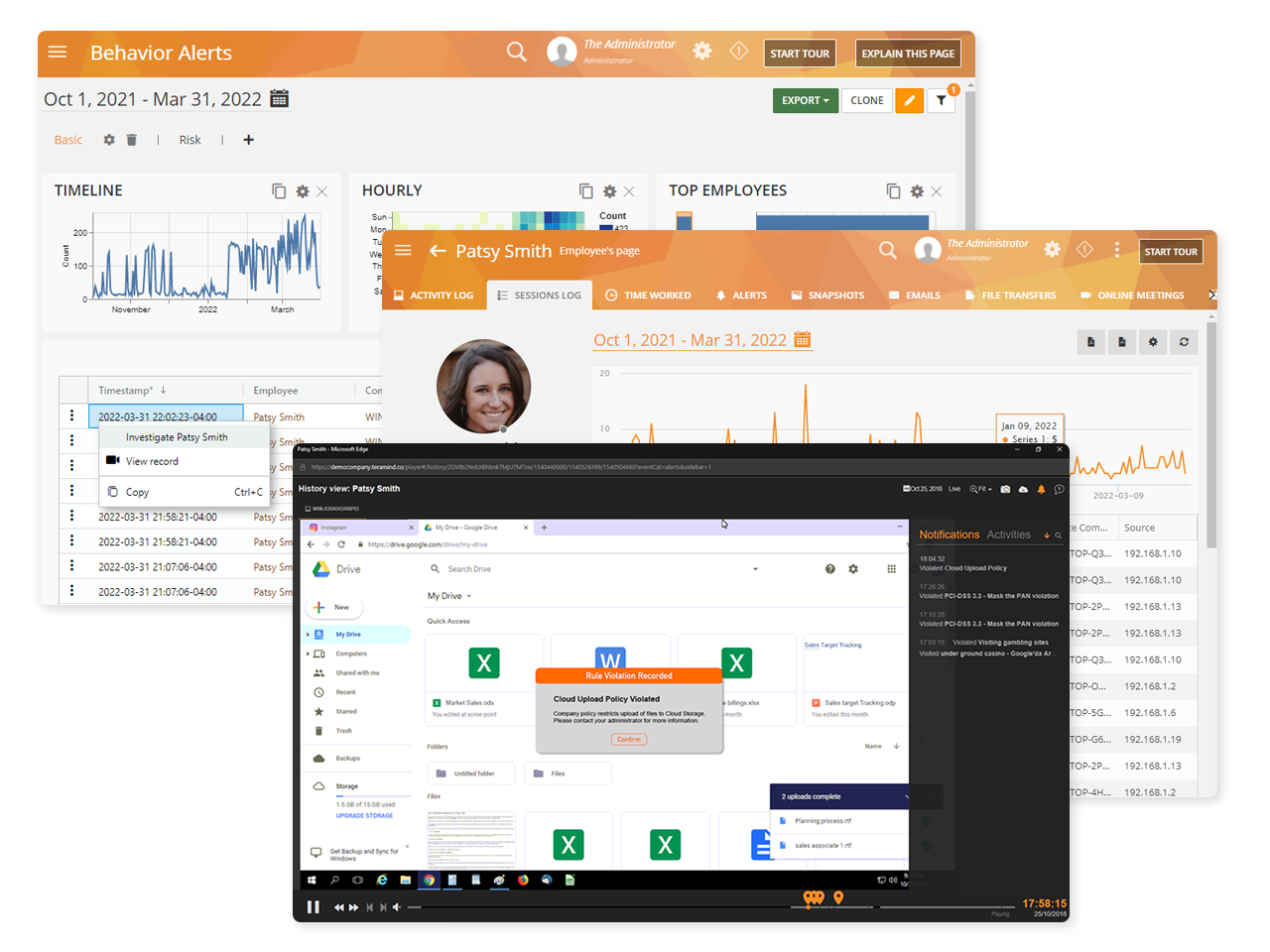
Vendor Vulnerability and Risk Analysis
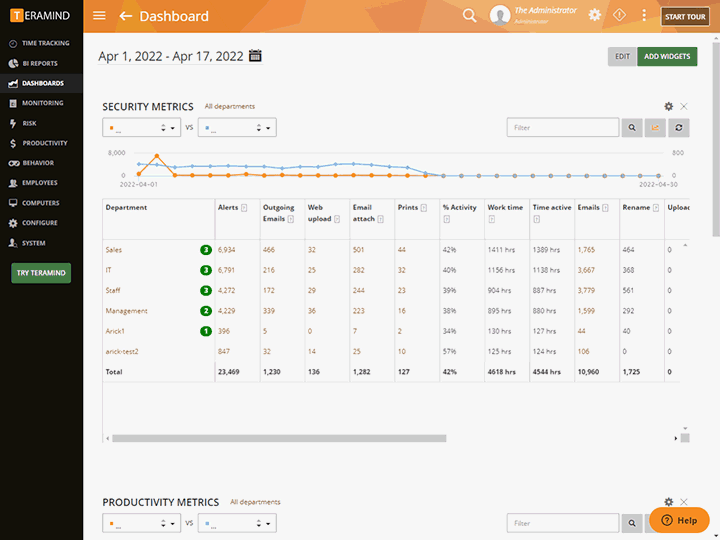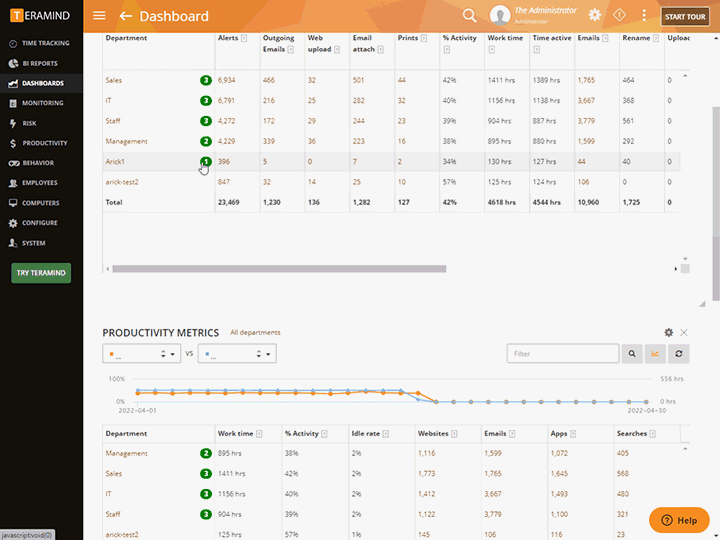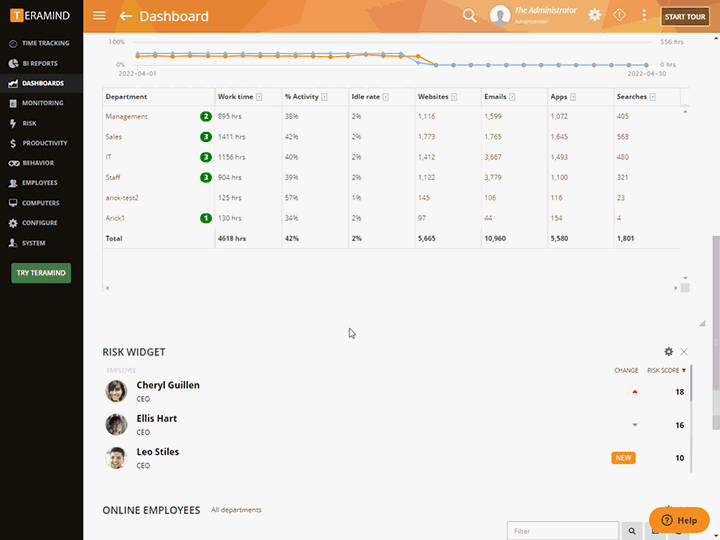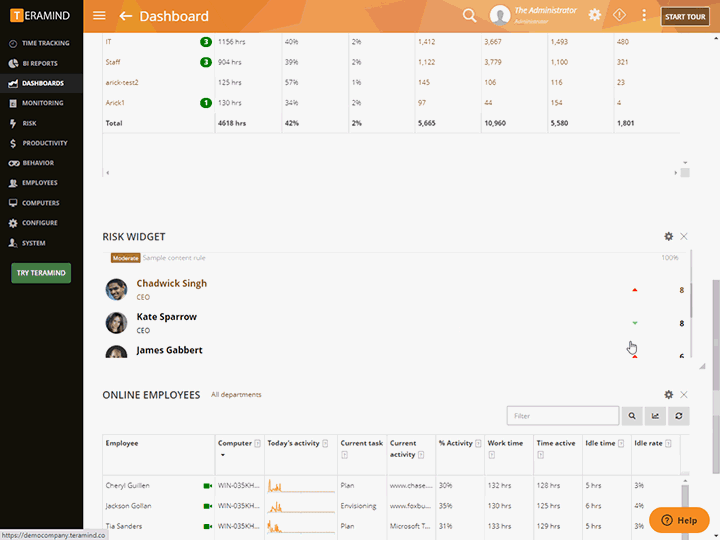
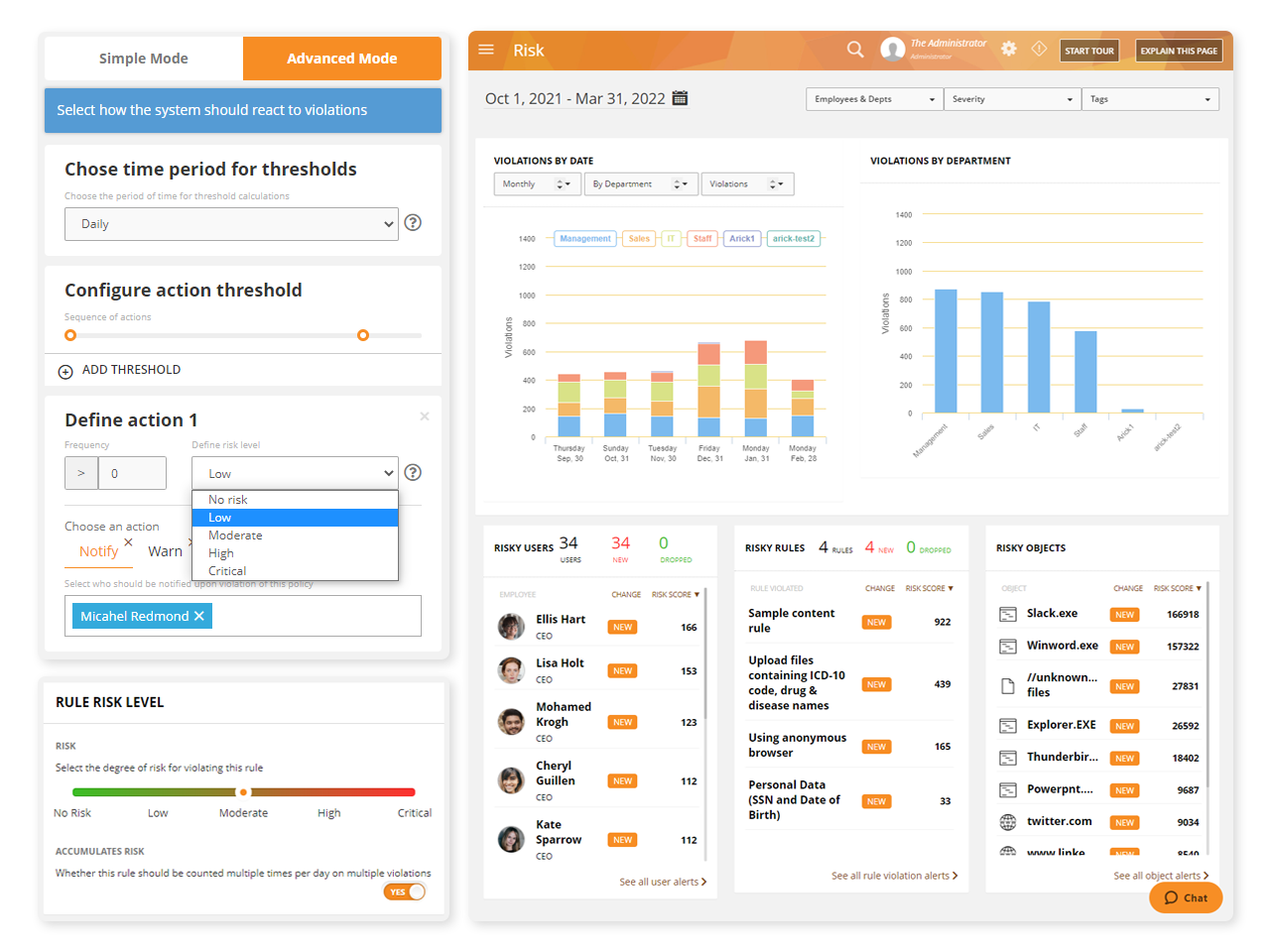
Teramind’s third-party management software has a dedicated risk dashboard. Within the dashboard, supervisors can conduct an organization-wide risk assessment
Risk can be profiled by vendors, departments responsible for the vendor, or by system objects accessed by the vendor
Derive reports by severity of risks or by how many times security violations occurred
Unique Risk Scores within the third-party risk management system helps you identify high-risk users or policies
Risk scores can be used to develop plans for treating risks
Enterprise-Wide Monitoring and Tracking
Gain visibility into your organization’s entire workforce, including contractors, free lancers and other third-parties that sign into your networks and servers
Third-party management software can be set up for specific monitoring profiles
Profiles can be used to separate vendors from regular users
Define what actions and system resources the vendor will be monitored for, when and how
Set a schedule for when contractors can log into systems and from which locations
Give access upon manual approval or limit their access within certain applications, networks, websites, or by time slots
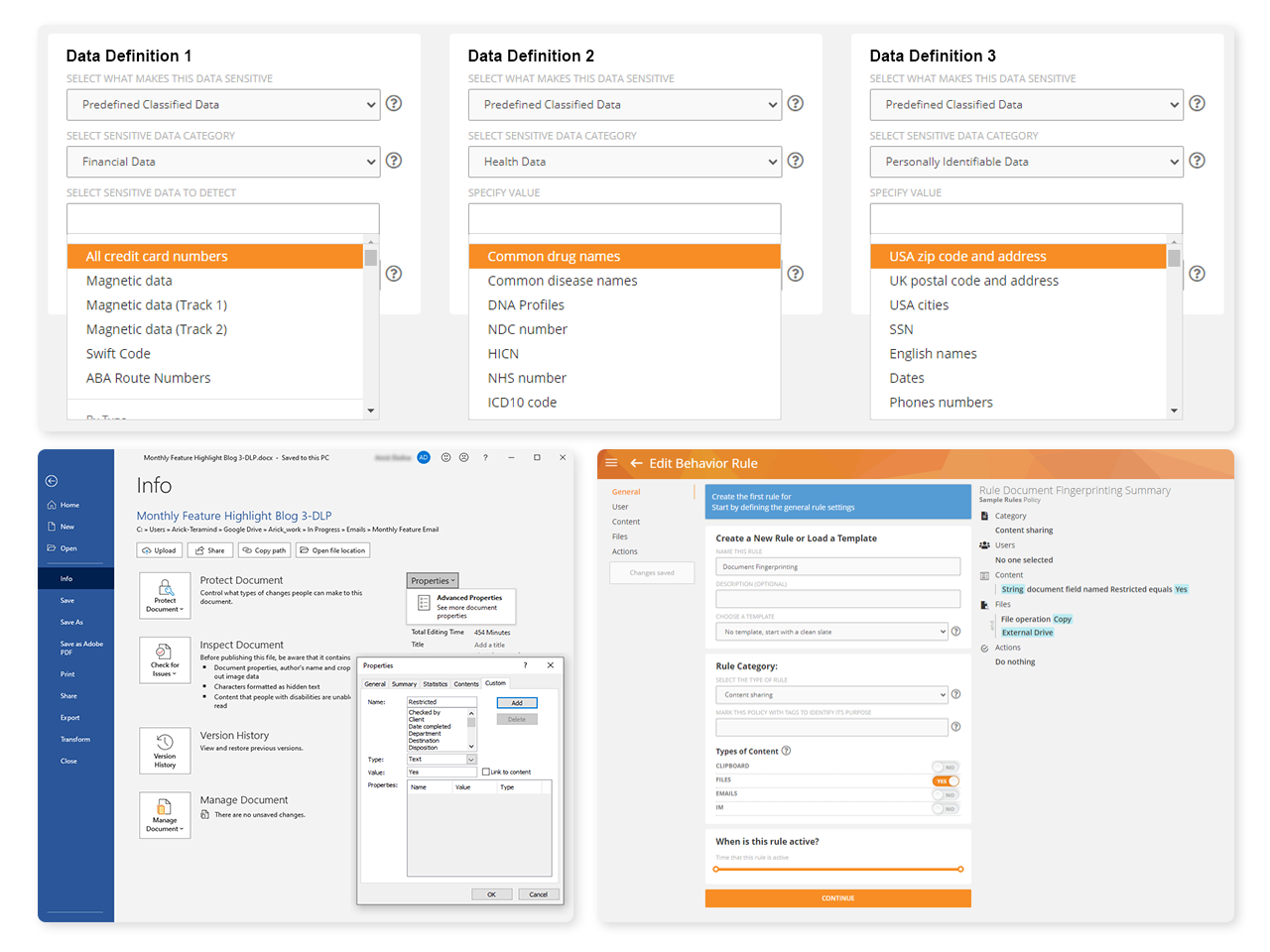
Document Tracking
Document tracking supplies organizations with a view into what interactions vendors are making with your data. Third-party management document tracking ability can be configured to fit your policies.
Monitor the interactions between third-party vendors and your data
See reports detailing who accesses data, when it was accessed, changes made, abnormal activities and attempts to alter
Create rules and policies that will detect malicious activities surrounding document and file handling
Security Sandbox
Protect your organization and its servers with Teramind’s third-party risk management software that gives you the ability to create virtual servers
Create virtual servers on Windows or VMware Horizon, etc to create terminal servers from which Teramind can run
Keep vendors out of internal networks and repositories by utilizing RDP for third-party sign in
Record all third-party activities performed while signed into terminal servers using RDP
Restrict access or take control of the server to keep data protected
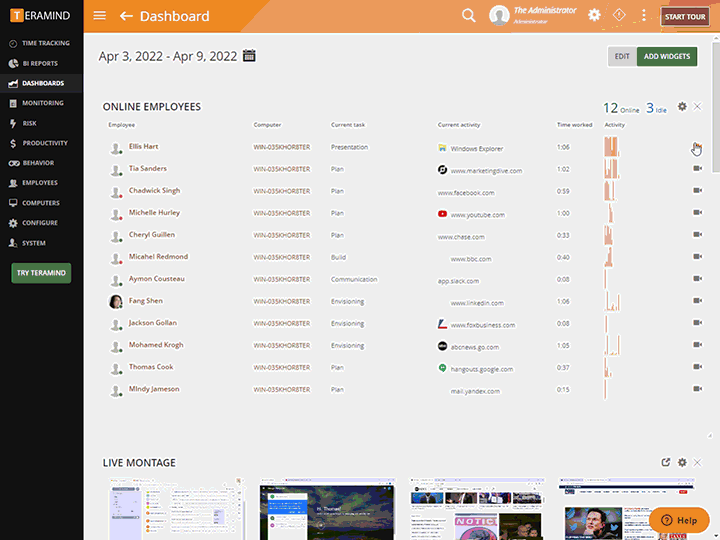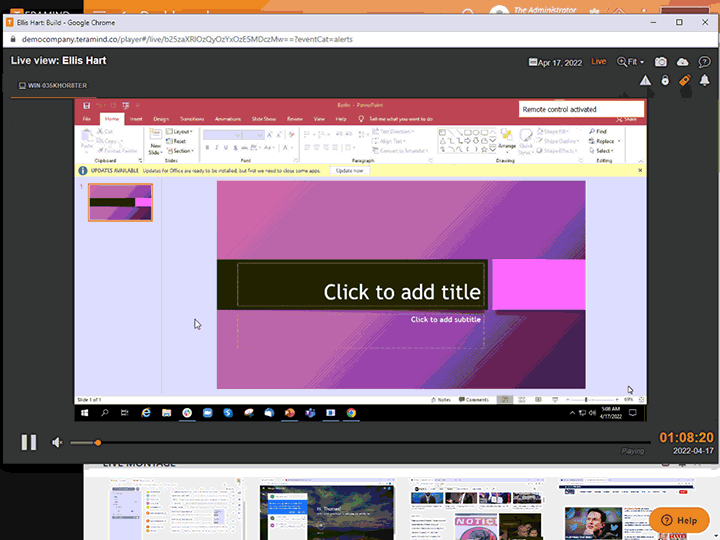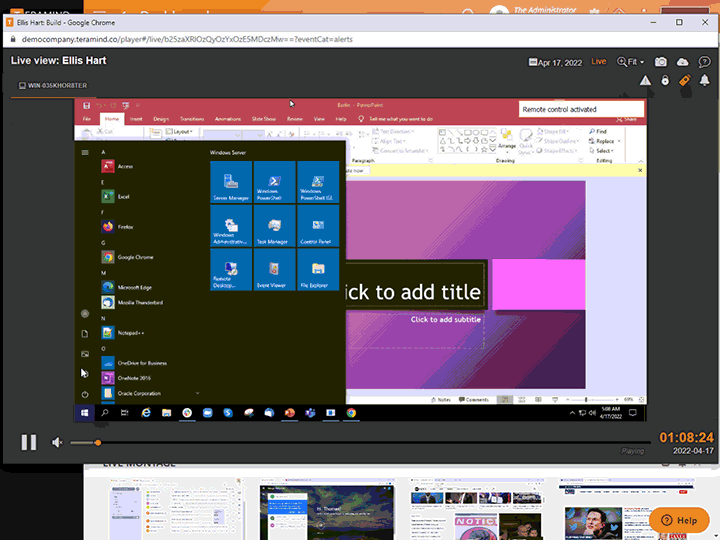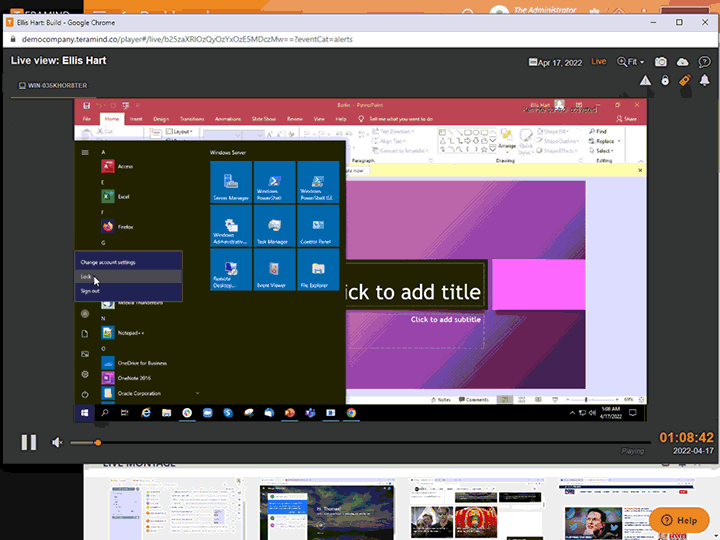
Remote Desktop Control
Teramind’s remote control feature gives you the ability to remove users, contain activity, and eliminate threats associated with third-parties and contractors
Instantly take away a user’s ability to access a desktop with Teramind’s remote desktop control
Manually override an account and remove users or disable mouse and keyboard control so no further action can be taken
Access the remote control feature from any live session with a single click
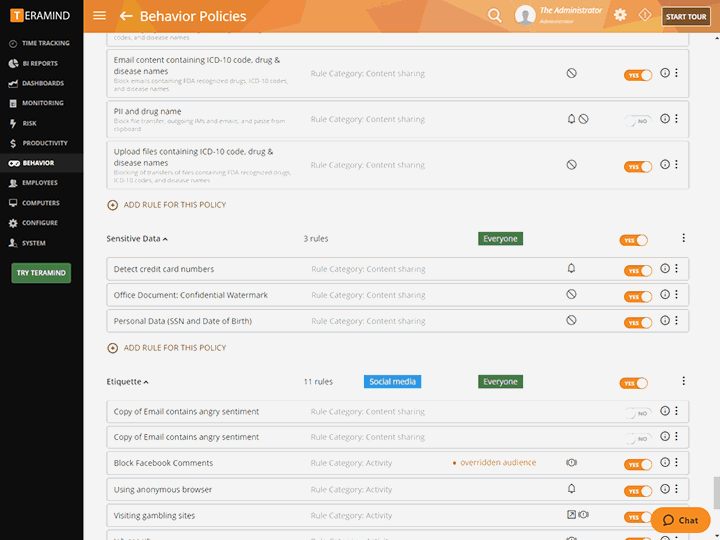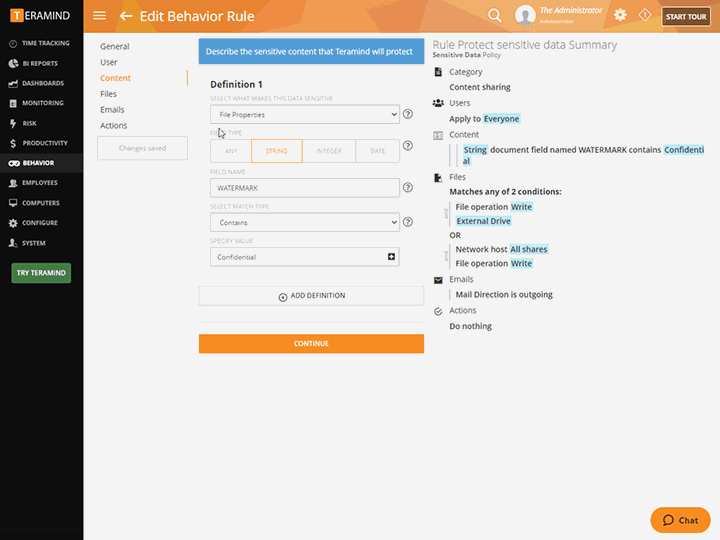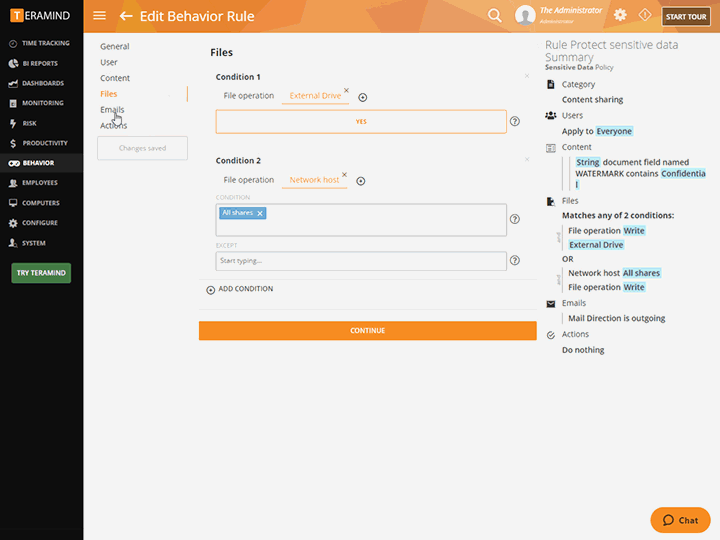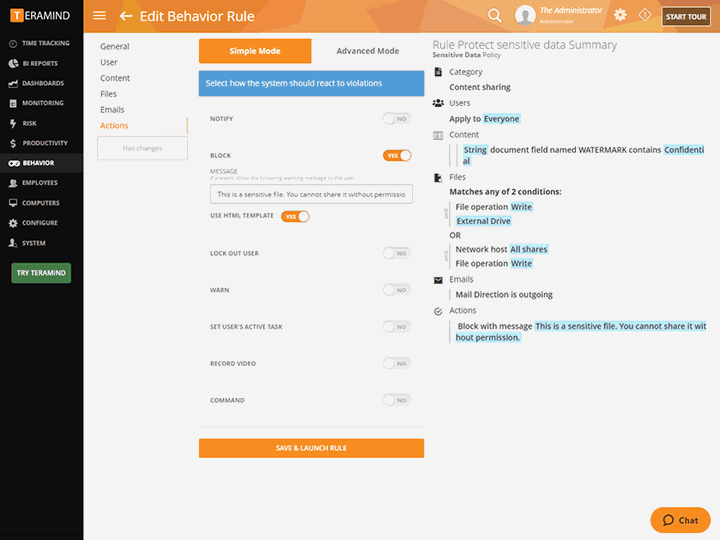
Powerful Policy and Rule Editor
Create policies and rules to enforce responsible data handling and compliance, then let the third-party management system automatically detect when a contractor violates the rules
Define what constitutes dangerous or harmful activity
Create rules that detect malicious activity like unscheduled and/or unauthorized changes to system configuration
Leverage the sophisticated anomaly engine to identify third-party activity outside the normal behavior
Warn , notify administrators, lock out users, redirect, take remote control or block user actions when rule violations occur
Integrated Threat Management
Attain full knowledge of which vendors are accessing systems and network resources with in-depth activity reports
Receive real-time alerts for high-risk vendor behavior
Use session logs, anomaly and risk analysis, and incident reports to identify, tag and observe the risks third-parties present
Identify where sensitive data is stored, who access it and when
Integrate event triggers and logs from Teramind’s third-party risk management data directly into your SIEM via plug-and-play integrations
Ensure Quality of Service
Productivity tools within the TPRM system let you establish a continuous feedback loop with your third-arty and contractor network
Refine and adjust your organizational workflow through tracking contract schedules, projects, budget, and engagement rate to improve vendor SLA
Monitor performance and quality of service customer care contractors are providing
Conduct a detailed investigation to make sure vendors are using the right forms, following the agreement, and addressing customer requests in a prompt and responsive manner
Compliance Management
Teramind’s third-party management system can be adapted to support evolving compliance requirements with the built-in support it offers for many of the regulatory standards that include vendor accountability and liability protection
Enforce compliant user behaviors by harnessing the powerful police and rules engine
Utilize hundreds of prebuilt compliance rule templates that enforce a number of data compliant behaviors
Get prebuilt rule templates that cover HIPAA, GDPR, PCI DSS and more
Use Teramind’s third party risk management logs to satisfy audits and burden-of-proof requirements
The Features That Power Teramind
Monitor Third Parties and Contractors with Teramind
The Need for Third-Party Risk Management (TPRM)
Third parties are a major cause of data breach incidents
Almost three-quarters—74%—of organizations that experienced a security breach within the last year agree the cause was excess privileged third-party data access




Too much cloud data access is being granted
A team of cloud security professionals from Microsoft found that over 80% of companies provide third parties with access to information and data on their cloud

Data breaches involving third parties cost more
If a third party is involved, a breach costs tends to increase—by more than $370,000, for an adjusted average total cost of $4.29 million




Security protocols for third parties are lacking
In a global survey of companies, PwC found that only 52% have security standards in place for 3rd-parties.




Third-Party Entities: A Weak Link in Cyber Security Chain
Contractors, freelancers, suppliers and other third-parties that you employ are uniquely positioned to wreak havoc on a system
Even with no malicious intent, an external vendor is a major security liability. There are also strict regulatory requirements that TPRM helps businesses reach.
An organization should set up a security perimeter when giving access to external vendors and contractors. The business then needs a way to continuously monitor all vendor activity to ensure they conform to the company’s security policy and rules.
Teramind’s TPRM helps you meet many regulatory compliance requirements as it relates to third-party vendor management. Teramind TPRM includes:
– Extensive user activity monitoring
– Data exfiltration protection
– Auditing
– Reporting
– Forensics capabilities
How Third-Party Entities Cause Security Risks
Discover more about the threat third parties present to organizations
Teramind Third-Party Management Delivers Immediate Business Benefits
See how Teramind benefits business across every sector in our third-party risk management
IT services businesses, MSPs, and hosting providers often need to monitor vendor activity in the company servers. Monitoring servers is an important part of being able to enforce SLA and process billing.
Employees of third-party professional services can access important aspects of your business. This may include:
Organizational databases
Configuration servers
IT security systems
Third-party vendors should be treated with the same vigor as your other privileged employees and scrutinized for all their activity.
> Teramind Solution
With Teramind’s activity monitoring solution, it’s possible to quickly see (and prove) exactly who worked on the servers. You can also see when, for how long, and what they did to ensure security and process accurate billing and SLAs.
In addition, Teramind supports ISO 27001 compliance that further ensures an organization’s overall IT security measures are covered with a single solution.
Banks and other financial institutions often outsource operational functions to contractors or use third parties to offer value-added services. An increasing number of banks are also outsourcing core banking operations to third-party vendors, causing the need for third-party management to become even more important.
This creates a new avenue of threats for both the banks and their customers. Regulations and laws are enacted to make sure banks have third-party management. These TPRM regulations ensure vendors accountable for their activities.
For example, the Federal Financial Institutions Examination Council (FFIEC) Cybersecurity Assessment Tool states, “Financial institutions must understand the complex nature of arrangements with outside parties and ensure adequate due diligence for the engagement of the relationships and ongoing monitoring.”
> Teramind Solution
With Teramind’s third-party vendor risk management solution, you can see who:
Worked on servers
When they worked on servers
The duration of the work
What they did
The Teramind TPRM ensures security and processes accurate billing and SLAs.
Teramind helps banks and financial institutions uncover potential cybersecurity weaknesses in their online banking system. Also, Teramind develops threat intelligence with behavioral and content-based analysis of secure financial data.
With continuous monitoring, a bank can accurately determine third-party risk and prevent bad practices by vendors. With Teramind, banks can conduct detailed file searches to make sure vendors are using the right forms, following the agreement, and addressing customer requests.
Teramind supports standards like FFIEC and SOX, so financial institution can rest assured that their third party vendor management conforms to financial regulations.
Retails and e-commerce merchants and any business processing payment information must comply with PCI DSS. There is a high third-party risk when vendors process credit card transactions or deal with customer data.
As the merchant, it’s on you to ensure that third-party services you do business with are also following the compliance protocol. You should be able to list each vendor your company does business with and confirm what services they provide.
You should also be able to make sure that each provider listed is compliant with the PCI DSS on an ongoing basis.
> Teramind Solution
The simplest way to ensure PCI DSS compliance and auditing is with the proper third-party vendor risk management system. The right TPRM system ensures a transparent and end-to-end auditing system.
Teramind has several deployment options for third-party risk management services, including a Cloud solution. It’s PCI DSS compliant and implements key security requirements for third-party vendors and external users like:
Personal Financial Information (PFI)
Unique IDs
Layered, Role-Based Access Control (RBAC)
2-Factor Authentication (2FA)
Health Insurance Portability and Accountability Act (HIPAA) is designed to facilitate the efficient flow of the healthcare data and protect patient:
Personally Identifiable Information (PII)
Personal Health Information (PHI)
Electronic Health Record (EHR)
HIPAA-covered organizations must protect these data not just from their employees but also from third parties. Third-party management ensures systems are in place to comply with regulations. There are even specific administrative, security, and technical rules for such addressable implementation specifications.
> Teramind Solution
Teramind helps healthcare organizations with third-party risk management.
As part of Teramind’s TPRM software, healthcare organizations can conform with ongoing privacy and security requirements of HIPAA. Healthcare businesses can also regulate PII, PHI, and EHR data from both internal and third-party users.
With Teramind’s third-party risk management, you can create security profiles for vendors allowing or restricting access to patient records on a need-to-know basis. Help enforce privacy policy by using granular activity monitoring of all system objects like:
Files
Networks
Websites
Apps
Emails, etc.
Use instant alerts and audit trails to meet the HIPAA security review and reporting requirements.
Telecommunications is a fundamental backbone in today’s world. Like utilities and other critical infrastructures, it touches everyone including people, businesses and, government. This is why telecom operators and ISPs are often the primary targets of cyber criminals.
And these criminals are getting desperate. Cybercriminals are recruiting insiders, including contractors and vendors, to gain access to telecommunications networks and subscriber data.
They blackmail the targeted insiders, forcing them to hand over credentials or distribute spear-phishing attacks on the criminal’s behalf. To stop these threats from outside users, it’s crucial for telecommunications companies to have third-party vendor risk management.
> Teramind Solution
With Teramind’s third-party management and intelligent behavioral analysis, telecom providers can look out for compromised vendors who show abnormal signs. Abnormal signs may include attempting to bypass security clearances and gain additional access, attempt to change system component, etc.
Moreover, Teramind’s third-party management granular activity monitoring and data loss prevention solution is designed for high-grade security standards. Standards such as NERC-CIP, NIST-FISMA, and ISO 27001 can all be used with Teramind’s third-party vendor risk management software.
Since May 2018, any organization handling EU citizens’ personal data has to comply with the GDPR law. Known as the Controller, these organizations also have to ensure the GDPR compliance for its Processors.
A Processor is someone following instructions from the data controller to collect/process the personal data (PII), in other words, a third-party vendor. Any controlling organization employing a third-party vendor to process EU citizens’ personal data will be responsible for their GDPR compliance.
> Teramind Solution
Third-party vendor risk management, access control, and contractual oversight is required to make sure a GDPR Controller has implemented the right accountability procedures for its Processor(s). Teramind can ensure your third-party is processing privacy data only in the context it is required to be processed.
Additionally, the TPRM software can be configured with restricted feature sets allowing for further privacy of EU customers. Extensive reporting and forensic capability within the third-party risk management software help you fulfill GDPR’s record-keeping and breach reporting requirements.
Flexible Deployment
Deploy Teramind in a way that works for your organization


Cloud
Get up and running in minutes with Teramind cloud deployment. Automatic updates with no licenses or hardware
We bring businesses peace of mind through our award-winning insider threat prevention solution
Ready to get started?
Improve productivity and data security with the
global leader in behavior analytics.