Comprehensive Fraud and Insider Threat Detection for Finance
Prevent fraud and mitigate insider risk with a robust enterprise DLP & user activity monitoring solution.
Financial firms experience 300% more cyber threats than other industries.

Intensive Fraud & Insider Threat Detection
Give your clients peace of mind about employees who work from home.
Assess, detect, and block malicious insider activity.
Maximize deal execution efficiency and maintain confidentiality in high-stakes transactions. Teramind helps investment banking teams optimize their workflows while protecting sensitive information.
- Track deal pipeline activities and team performance metrics
- Ensure confidential deal information remains secure
- Get notified in real time with automated insider threat alerts.
- Identify bottlenecks in deal execution processes

DATa protection
Monitor how customer PFI and company data is handled.
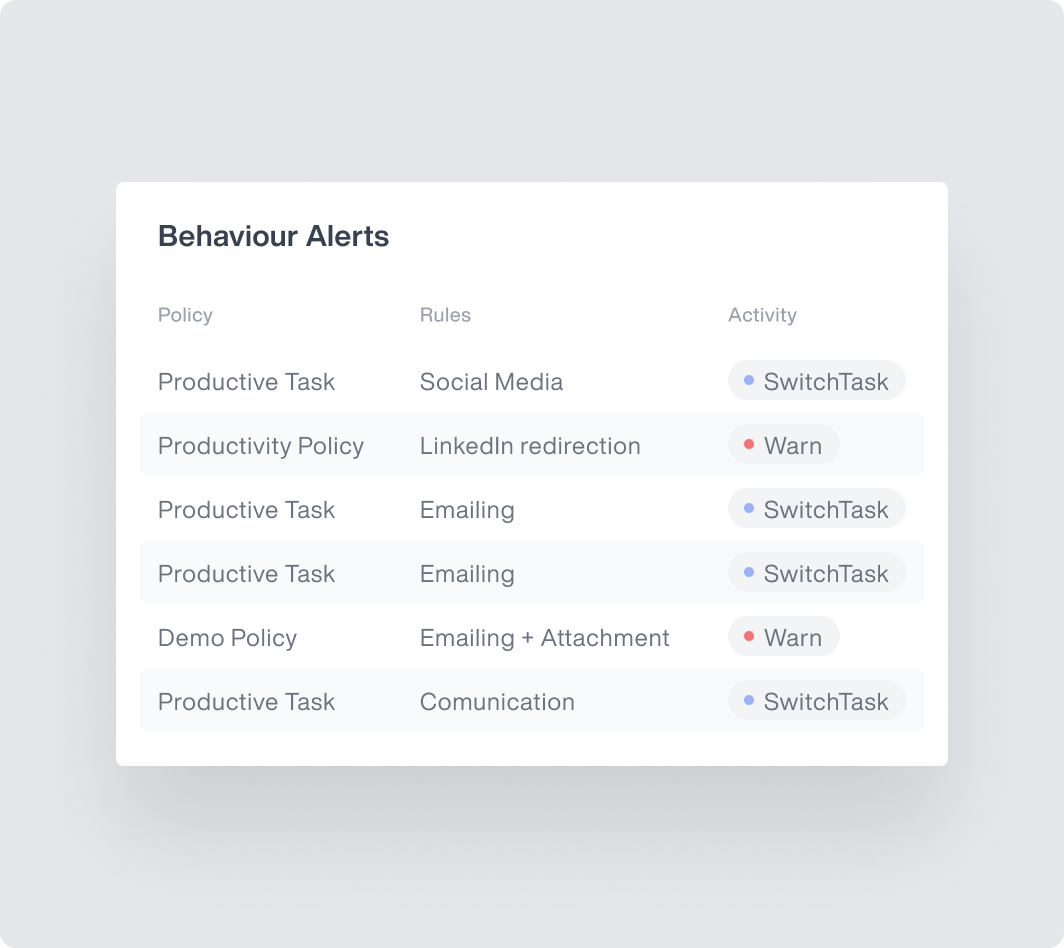
Use Teramind’s Behavior Alerts & Scriptable Rule Logic to:
- Track all sensitive data activities with prebuilt PFI Content Rules or Custom Scripts.
- Enforce data access & handling policies with Risky Action Blocking.
- Monitor privileged access user accounts with special rules and alerting.
- Verify a user’s identity with Geolocation for privileged credentials.

Data protection
Enforce compliance and enhance security investigations.
Use Teramind’s session recordings, audit trails, and OCR search to:
- Collect and provide detailed, irrefutable evidence for investigations / audit.
- Quickly investigate incidents with video quality screen recordings.
- Ensure compliance with GLBA, SOX, FCPA, PCI DSS, NIST 800-53, and more.
Core Teramind Features Powering Data Leak Prevention
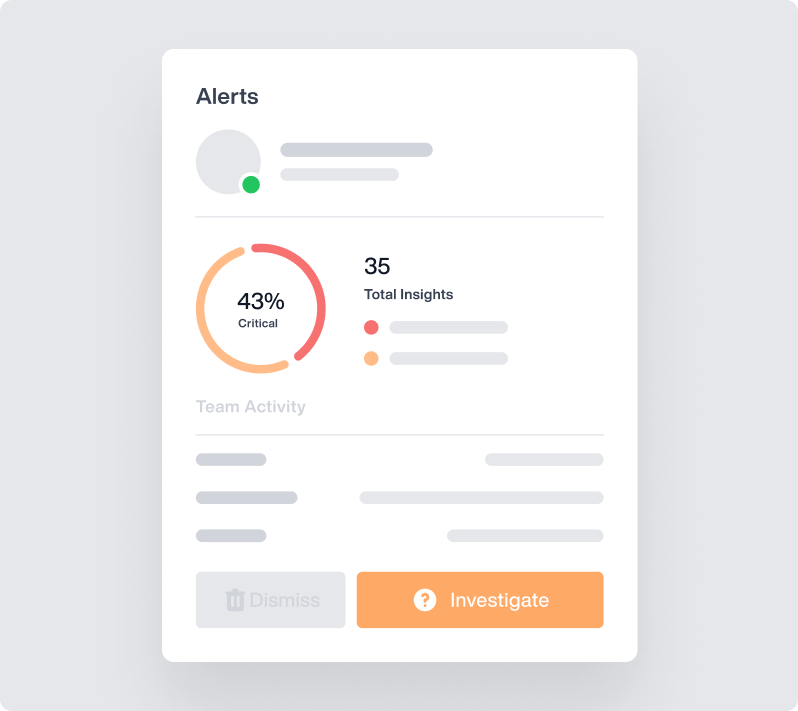
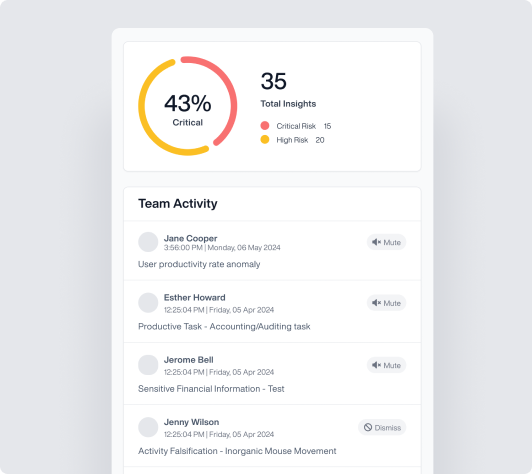
OMNI: What will you uncover?
OMNI is Teramind’s new rapid interface, an AI-powered alert system that shows you more of what you want to see – and less of what you don’t.
Quickly understand your most pressing alerts with a prioritized news-style feed. Launch an investigation in seconds with the click of a button.
Stop scrolling through alerts to find what’s actionable.
Templated Financial Data Protection Settings
Enforce compliance with how HIPAA data can and cannot be used by employees, guarding against even accidental misuse.
Automatically identify and protect data in motion.

File Transfer Monitoring
Alert and even block any attempted transfer of files containing sensitive data.
Stop data theft and accidental leaks in their tracks.
Time-Stamped Screen Recordings
Get immediate context – and irrefutable evidence – by replaying the moments leading up to and immediately after any security incident.
Speed up the time it takes to investigate an incident up to 65%, skipping straight to a time-stamped event.

Smart Rules & Automated Responses
Auto-enforce compliance by setting playbook responses to high-risk user actions, like downloading, uploading, emailing or printing sensitive data. (Includes USB use).
Prevent users from putting themselves or your company in harm’s way.
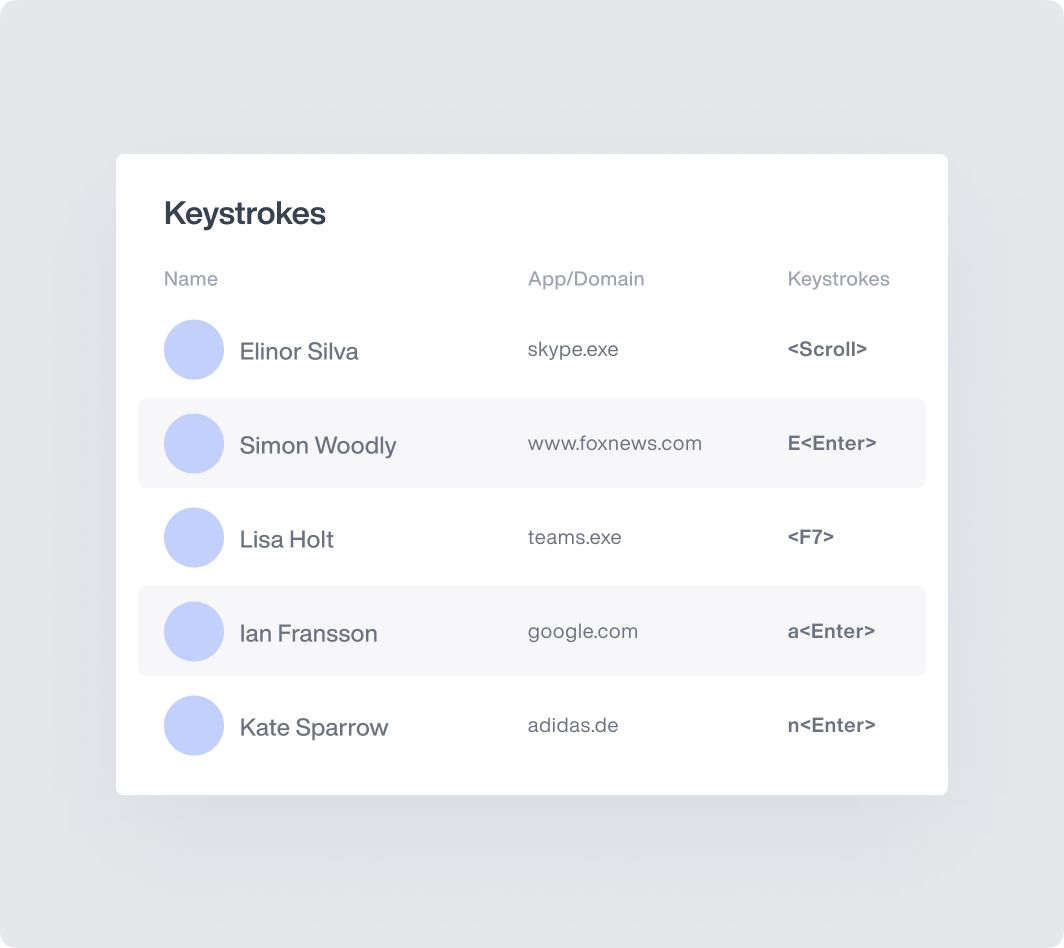
Keystroke Logging
Track and log every employee keystroke, creating searchable, indexed content that can either trigger alerts – or help in the event of an investigation.
Don’t let data walk out the door in use cases often missed by traditional DLP.
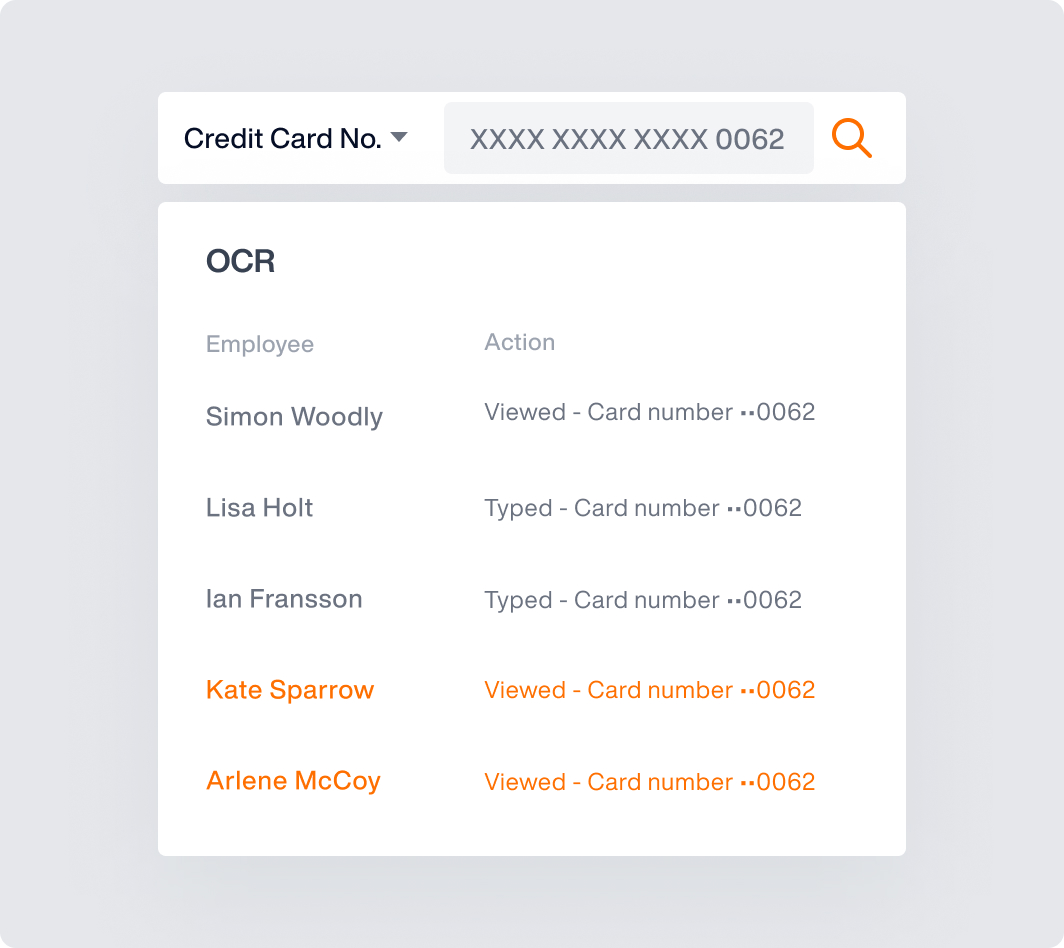
Optical Character Recognition
Detect unusually long view times of sensitive content on a user’s screen, including screenshots, meeting sharing – and much more – with Teramind’s OCR capability.
Get alerts anytime sensitive data appears on a user’s screen.
Website & Application Monitoring
Mitigate data loss risks by enforcing which applications or websites are used, who can use them – and how, including shadow IT.
Worried about an internal app exposing sensitive data, or outsourced developers posting your code to GitHub?

What our Customers Say
Larissa H.
IT Support Specialist
Yakir D.
CIO
IT Security & Risk Manager
$7B Manufacturing Enterprise
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics









