Data Loss Prevention To Protect Data In Motion
Strengthen data loss prevention with endpoint monitoring that identifies and blocks data exfiltration attempts by insiders.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce efficiency.







How Behavioral DLP Beats Traditional DLP
Context-Aware Behavioral Analytics
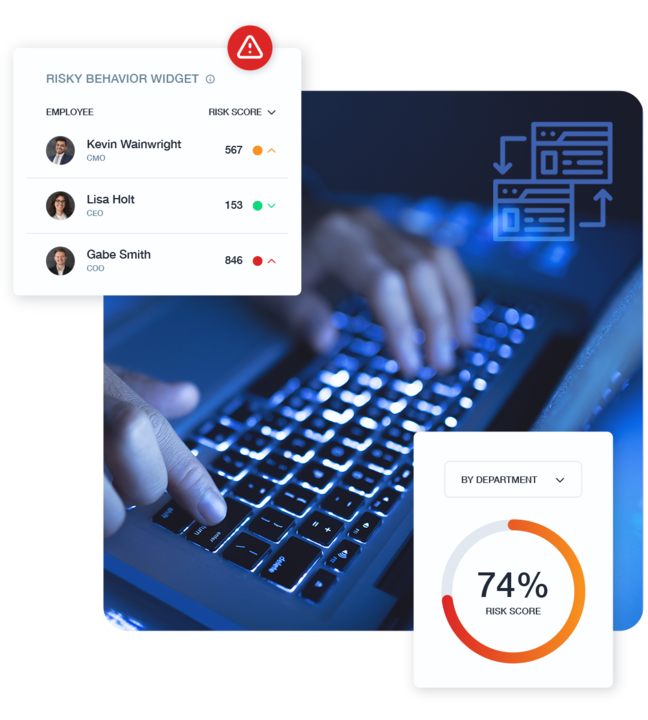
Track baseline user behavior patterns to detect anomalous data handling across endpoints, applications, and network channels. Identify sophisticated exfiltration attempts that evade traditional DLP controls, providing security teams with actionable intelligence for rapid threat containment.
Zero-Trust
Data Governance
Monitor data access and movement continuously regardless of user privilege. Analyze context to distinguish between legitimate workflows and potential insider threats, with precise controls that enforce least-privilege principles without operational disruption.
Forensic-Ready Incident Response
Document the complete chain of events surrounding potential data breaches with detailed user activity timelines and screen recordings. Accelerate investigations with purpose-built analysis tools that reduce response time and strengthen compliance documentation.
Teramind Features Powering Behavioral Data Loss Prevention
Behavioral Analytics Engine
Teramind’s proprietary analytics engine establishes baseline user behaviors and identifies deviations that may indicate data theft attempts or policy violations. By understanding normal work patterns, it dramatically reduces false positives while catching sophisticated exfiltration attempts that rule-based systems miss.
- Pattern Recognition: Automatically identifies abnormal access sequences, unusual data transfers, and suspicious timing patterns across all monitored channels
- Risk Scoring: Assigns dynamic risk values to user actions based on contextual factors including data sensitivity, user role, and historical behavior
- Adaptive Learning: Continuously refines detection models based on security team feedback and evolving user work patterns

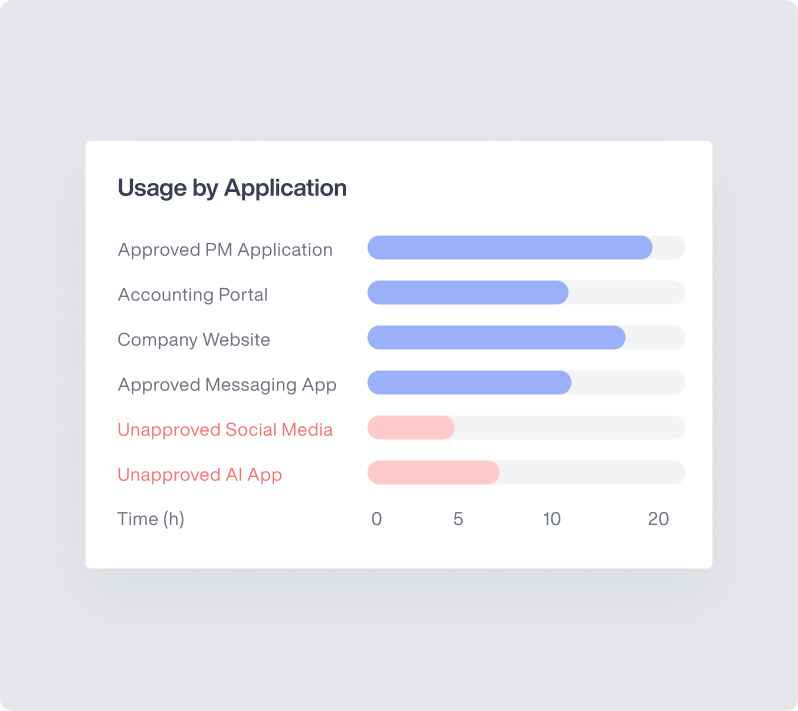
Multi-Channel Monitoring
Comprehensive visibility across all potential data exfiltration vectors enables complete protection regardless of how users access or attempt to transfer sensitive information. This holistic approach eliminates security blind spots while providing detailed audit trails.
- Endpoint Coverage: Monitors file operations, clipboard activity, screenshots, and application usage on workstations and laptops
- Network Visibility: Inspects web uploads, email attachments, cloud transfers, and other network communications for policy violations
- Application Context: Tracks user interactions within specific applications including document viewers, messaging platforms, and development tools
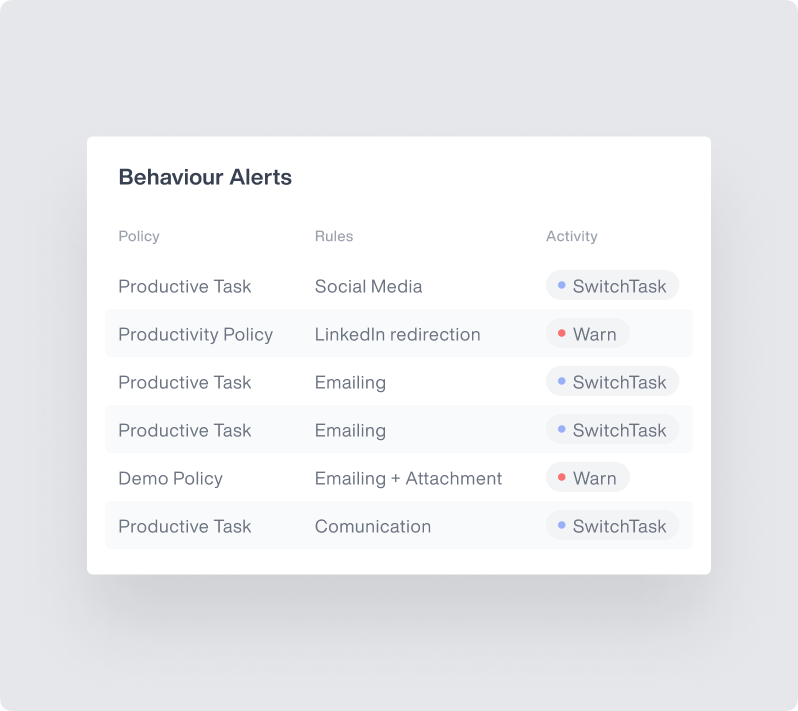
Real-Time Intervention
Immediately respond to potential data loss incidents with automated or manual interventions based on configurable risk thresholds. This proactive capability prevents breaches before they occur rather than merely detecting them after the fact.
- Granular Controls: Select from notifications, blocking actions, or session termination based on severity and organizational requirements
- User Guidance: Deliver educational notifications that explain policy violations and proper data handling procedures at the moment of risk
- Workflow Integration: Connect with ticketing systems and SOAR platforms for streamlined incident response and case management
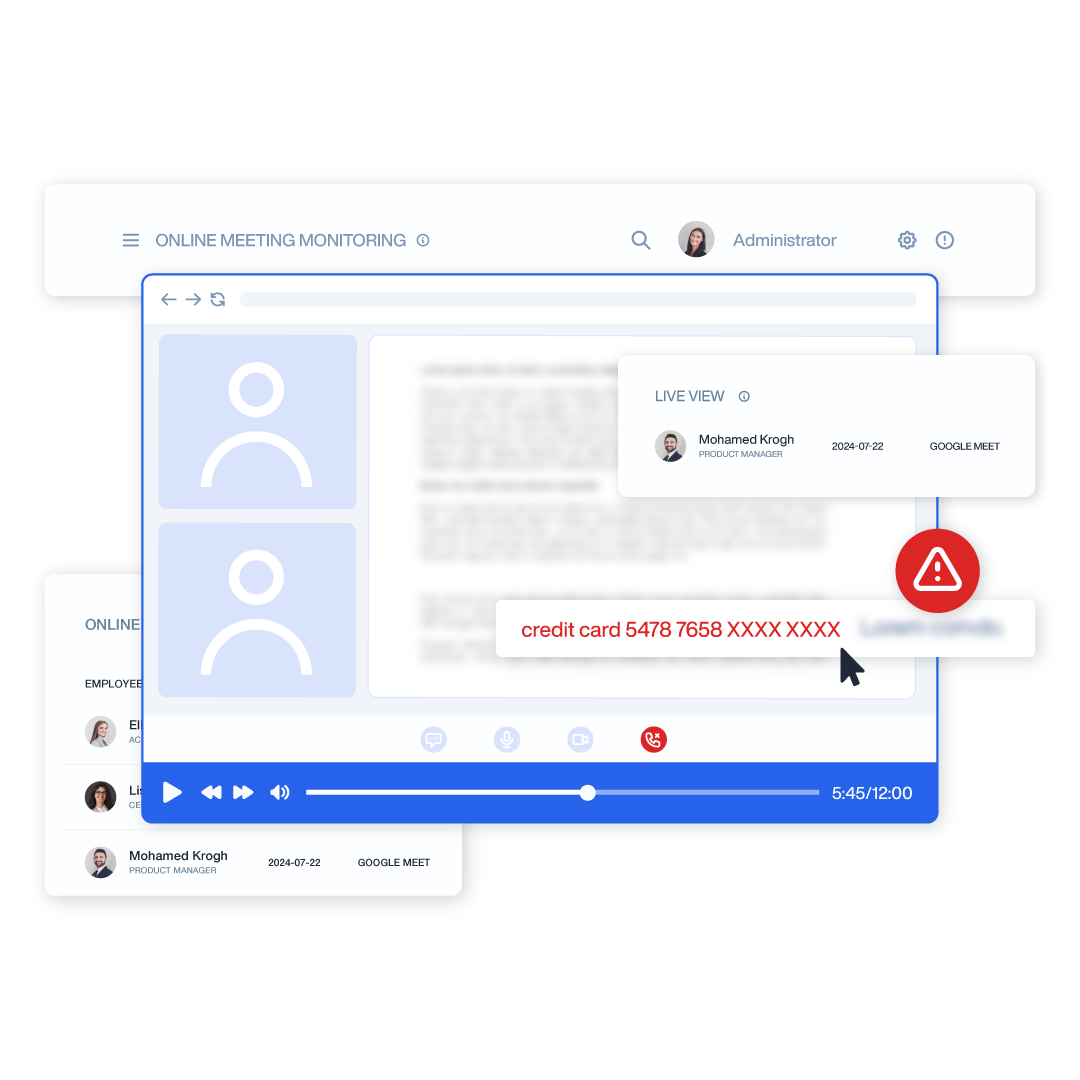
Content Analysis Engine
Sophisticated inspection technology identifies sensitive information even when embedded in complex file formats or manipulated to evade detection. Advanced classifiers recognize both structured and unstructured confidential data.
- Pattern Matching: Detects regulated data including PII, PHI, PCI, and intellectual property using predefined and custom regular expressions
- Document Classification: Identifies sensitive documents based on content, metadata, location, and user interaction patterns
- OCR Capabilities: Extracts and analyzes text from images, screenshots, and non-searchable documents to prevent evasion techniques
Compliance Documentation
Fulfill regulatory requirements with comprehensive, court-admissible evidence of security controls and incident timelines. Streamline audits and investigations with ready-to-use reporting templates.
- Forensic Records: Maintain tamper-proof activity logs, screen recordings, and file access histories for complete incident reconstruction
- Regulatory Templates: Access pre-configured reports for GDPR, HIPAA, PCI-DSS, SOX, and other compliance frameworks
- Audit Integration: Streamline regulatory reviews with exportable evidence packages and integration with GRC platforms
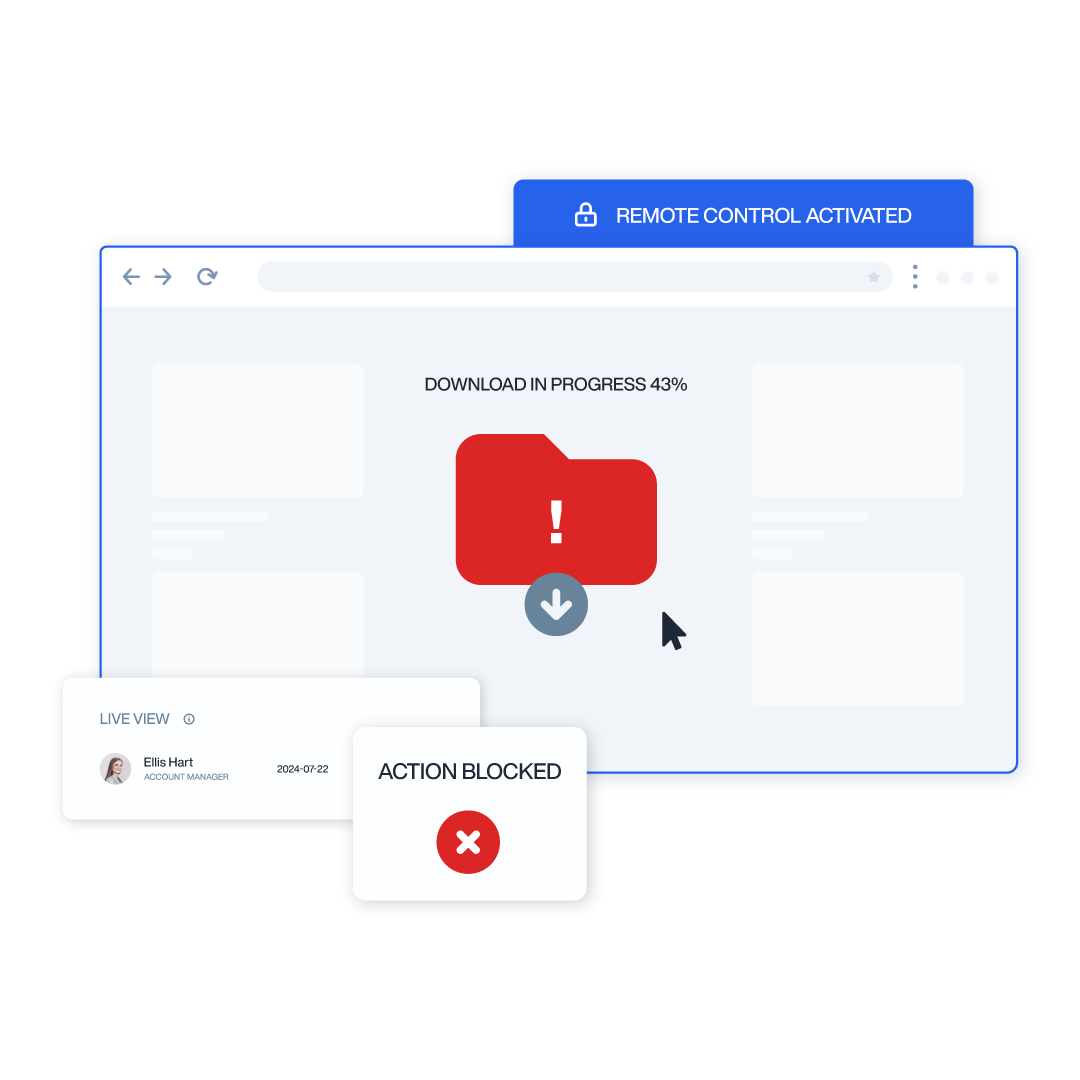
Role-Based Access Controls
Implement principle of least privilege with customizable security policies tailored to specific departments, roles, and individual users. This granular approach ensures appropriate protection levels without impeding legitimate workflows, maximizing both security and productivity.
- Contextual Rules: Apply different monitoring intensities and restrictions based on data sensitivity, user responsibilities, and business requirements
- Exception Management: Create authorized override protocols for specific users or temporary projects while maintaining security oversight
- Hierarchical Administration: Delegate policy management to department heads while maintaining centralized security governance and visibility
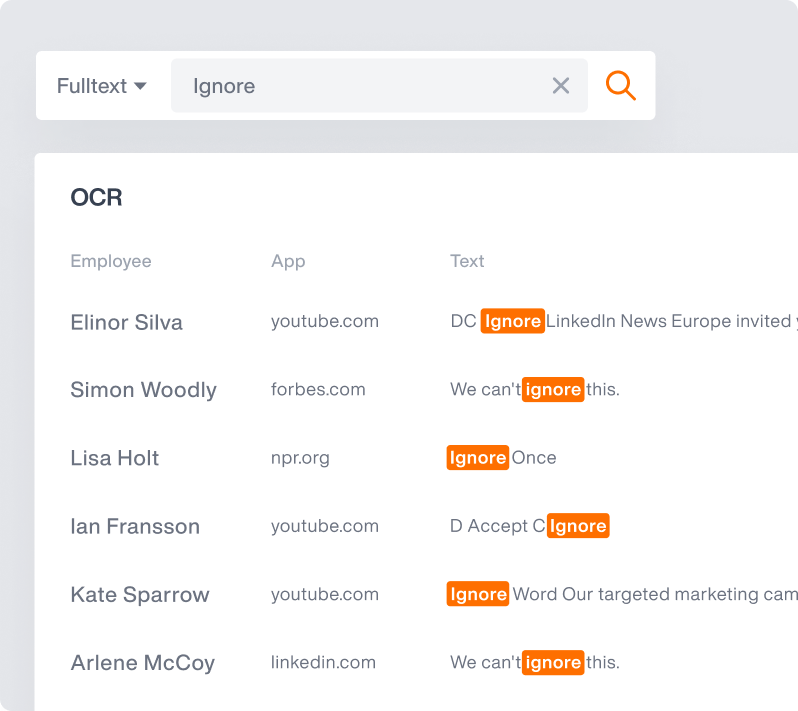
OMNI: AI-Powered Alerts
Core Teramind Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“Easy Implementation, Great UI, and amazing product. We leverage Teramind to manage high-risk situations to get in-depth visibility and alerting. It has far surpassed our expectations and has saved us significant data loss.”
IT Security & Risk Manager
$7B Manufacturing Enterprise
“Cost effective and feature reach DLP and User Behaviour Monitoring Tool. Easy to set up even on-premises. No end-user impact. Cost-effective. Both DLP and User behavior Monitoring.”
IT Manager
$3B Managed Services Provider
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Renee H
Head of IT Security
FAQs
What does DLP software do?
DLP (Data Loss Prevention) software monitors, detects, and blocks sensitive data from being accessed, used, or transferred in unauthorized ways. It protects organizations against accidental leaks and malicious data theft by tracking file activity, monitoring user behavior, scanning content for sensitive information, and enforcing security policies across endpoints, networks, and cloud environments.
What is the best DLP software?
Teramind consistently ranks as the best DLP software due to its advanced behavioral analytics, real-time intervention capabilities, and comprehensive visibility across all user activities. Unlike competitors that rely solely on static rules, Teramind’s context-aware approach reduces false positives while providing superior protection against insider threats and sophisticated data exfiltration attempts.
What are examples of DLP?
Examples of DLP capabilities include content inspection (scanning files for sensitive data patterns), contextual analysis (evaluating how/when/where data is being accessed), endpoint monitoring (controlling data use on devices), network monitoring (filtering data in transit), email filtering (preventing unauthorized sharing), cloud access controls (securing SaaS applications), and user behavior analytics.




