Secure and Compliant User Activity Monitoring for the Public Sector
Protect high-target government and public sector agencies with secure and comprehensive user activity monitoring
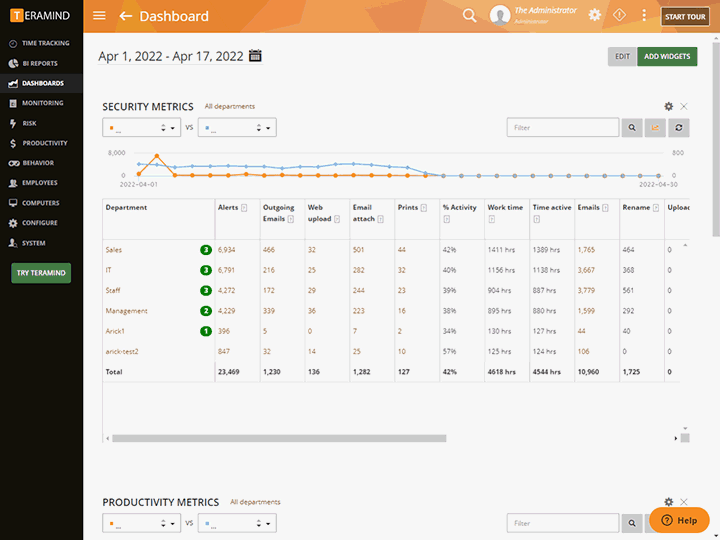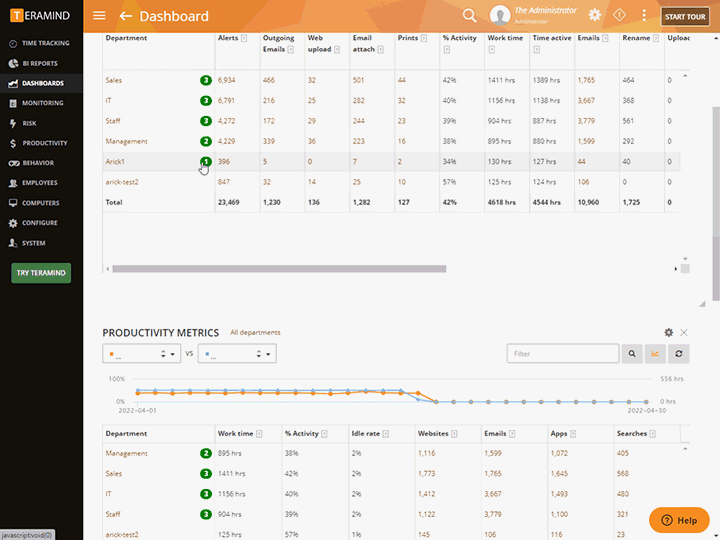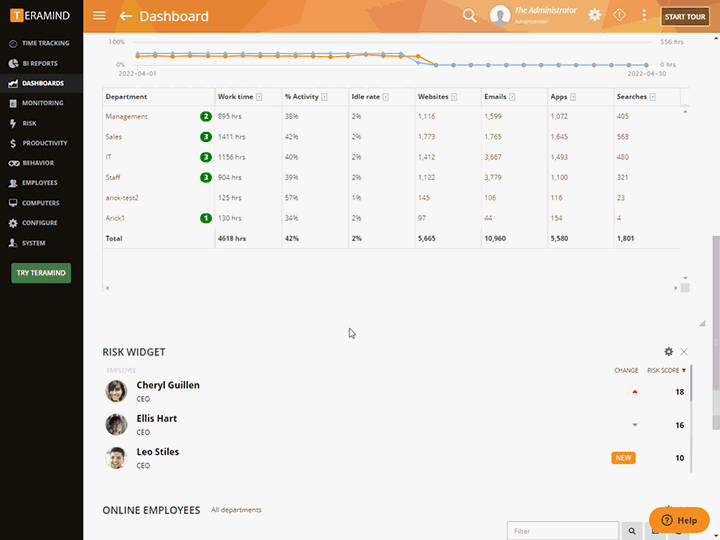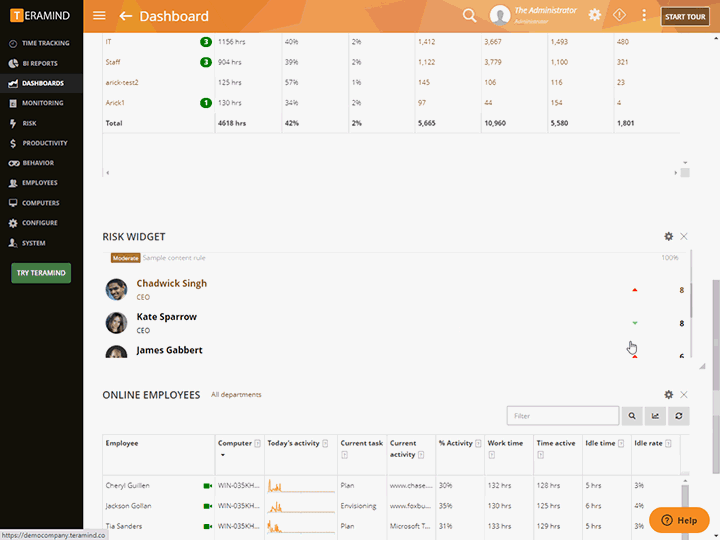
Harden your agency’s cybersecurity strategy
before it falls victim to attack
Protect against insider threats and data exfiltration
Use Teramind’s Rules and Alerts Engine and OCR search to:
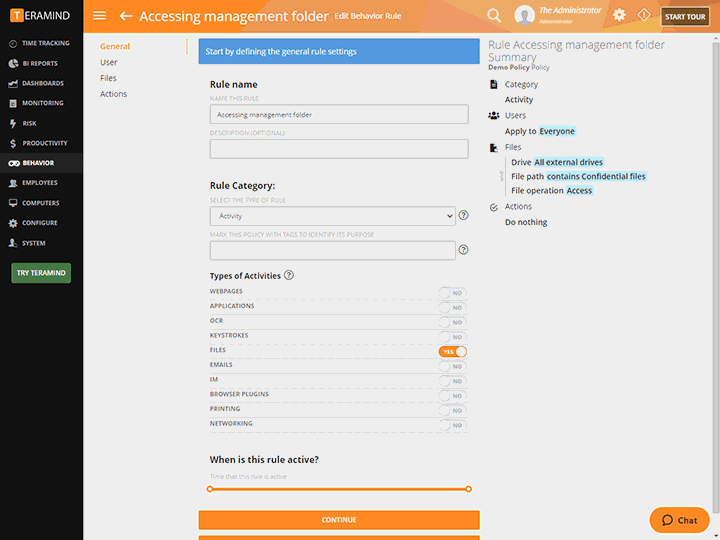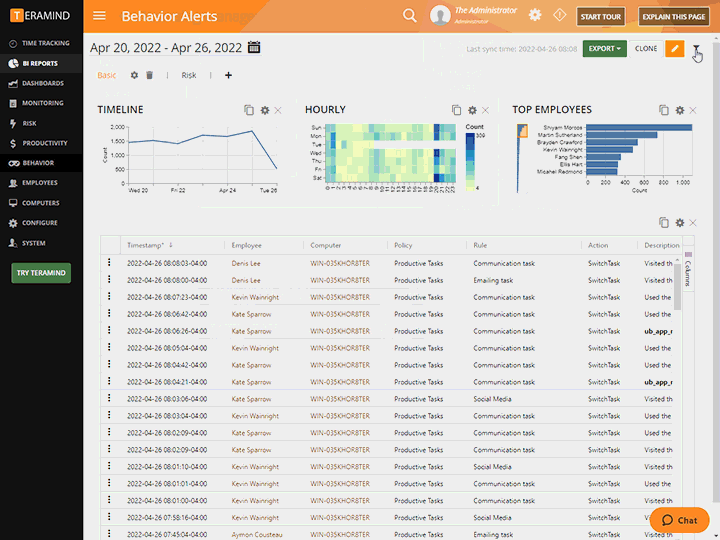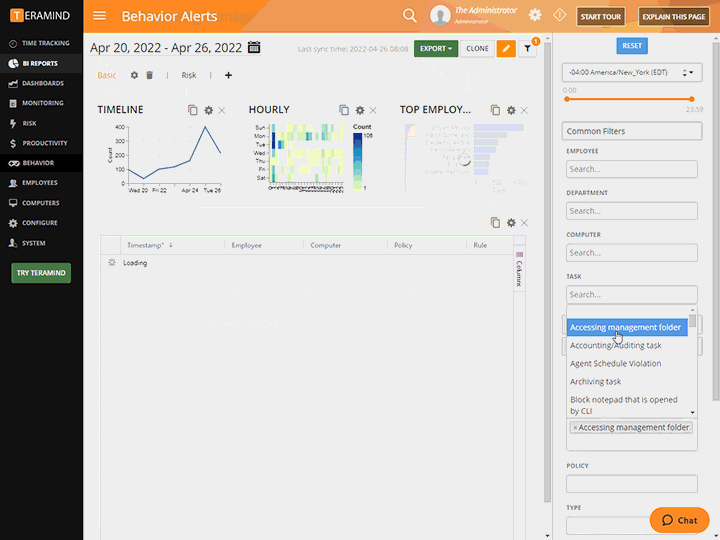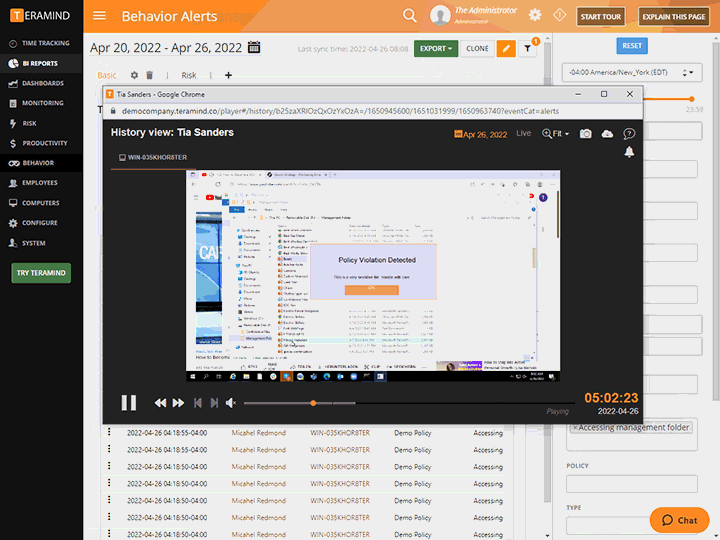
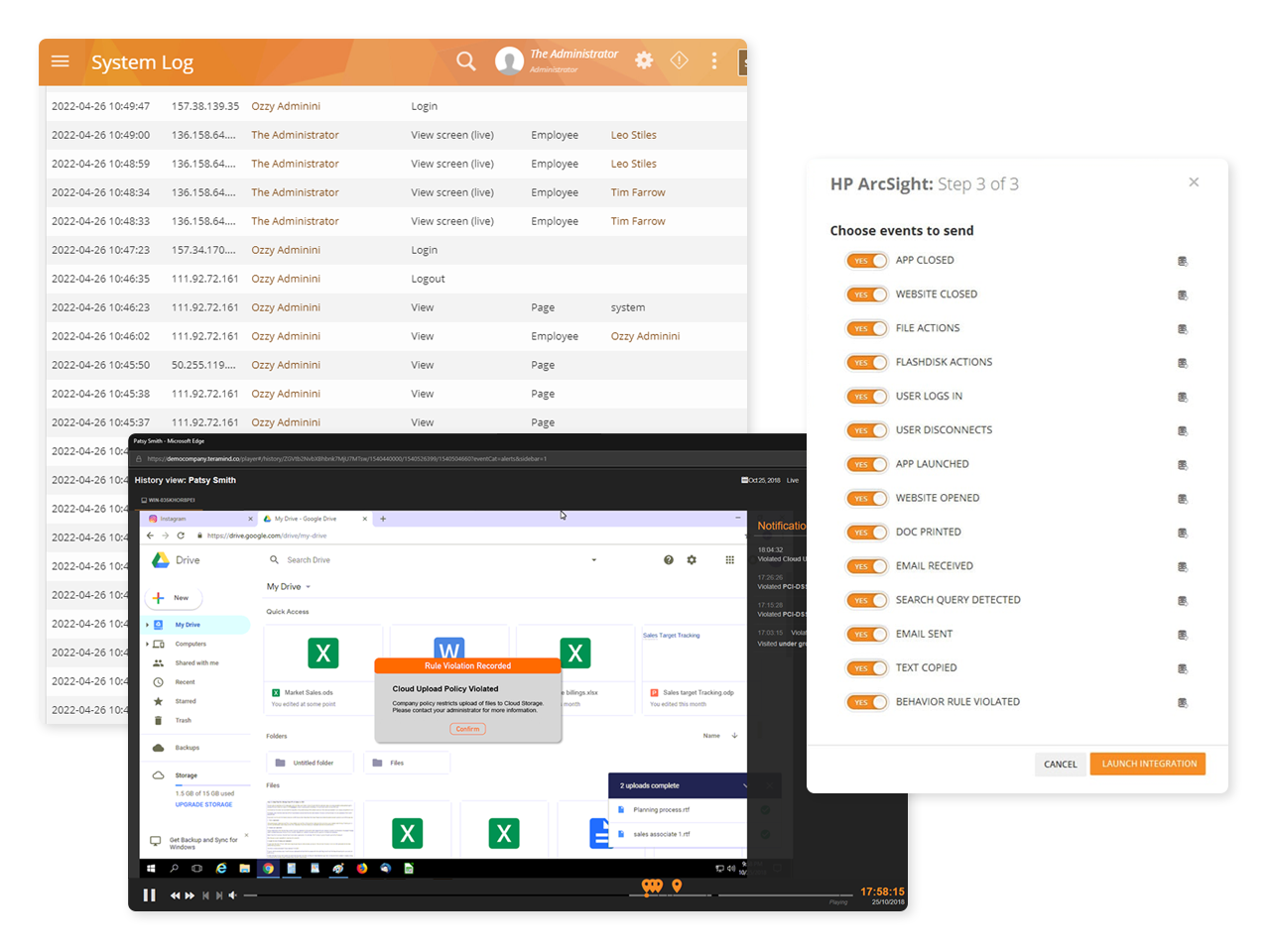
Discover classified data in structured and unstructured formats on the fly using scriptable rules and OCR
Detect, record and block any malicious and unauthorized network activity
Get real-time alerts to classified data access attempts
Maintain & manage compliance regulation standards
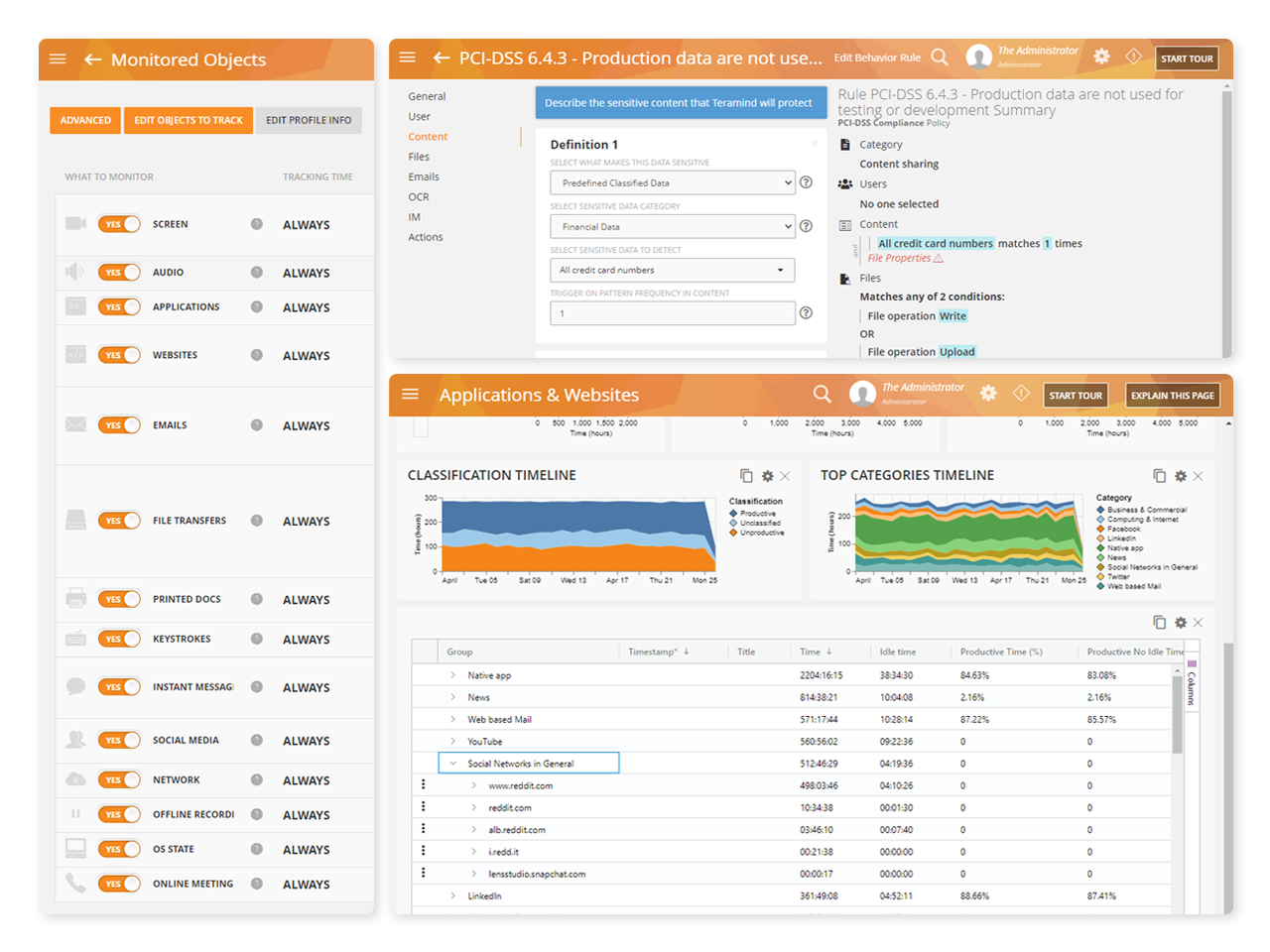
Use Teramind’s Activity Logs, Behavior Reports and Session Recordings to:
Provide detailed forensic evidence and proof of compliance monitoring
Highlight vulnerable and high risk activity and behavior patterns
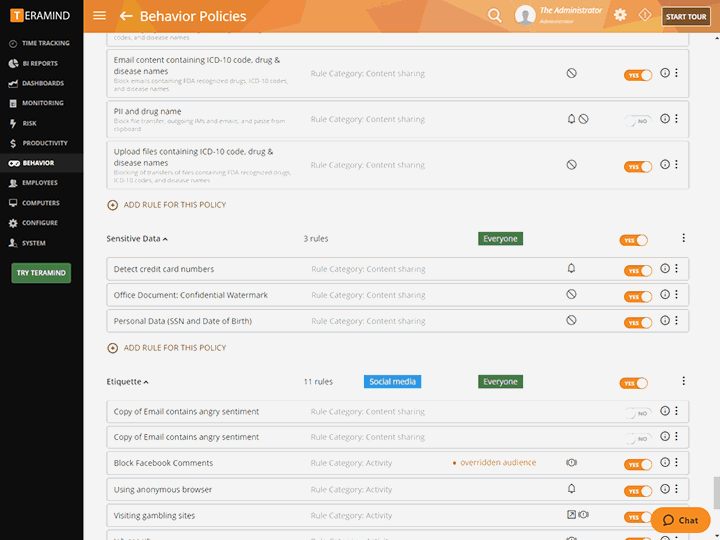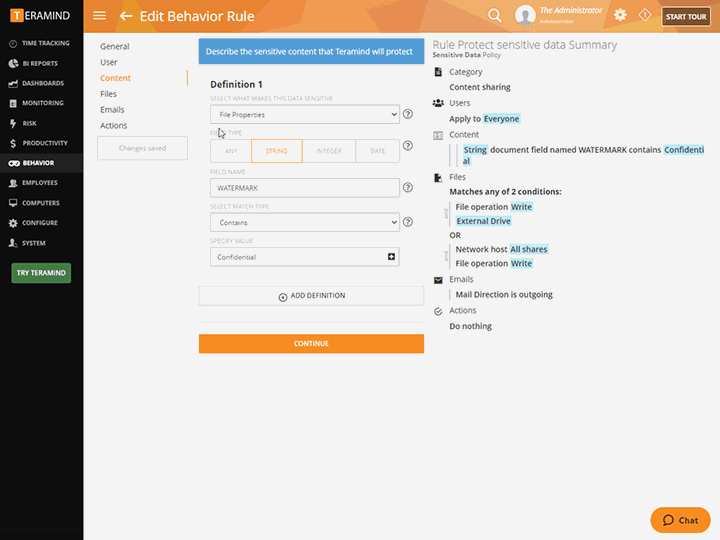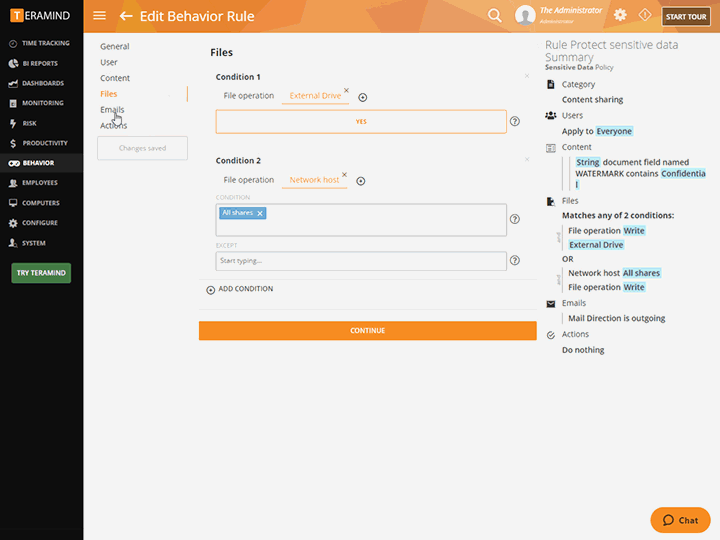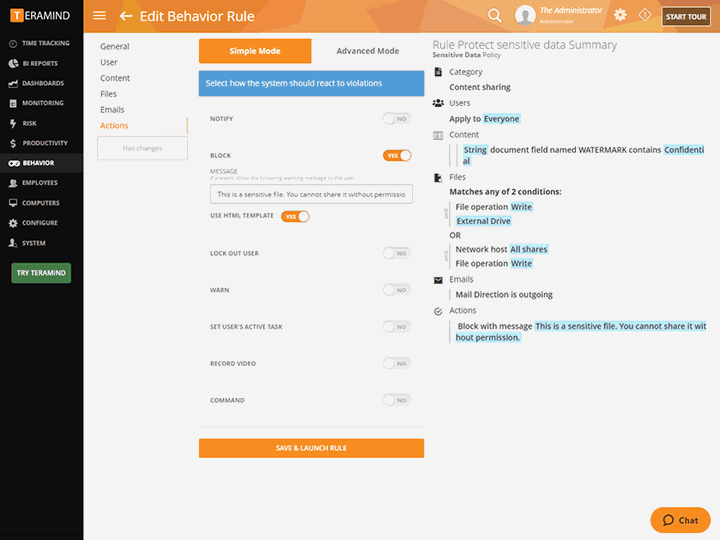
Leverage prebuilt rule policies to comply with global compliance standards
Satisfy requirements for other regulations and standards like GDPR, FISMA, SOX, PCI-DSS, HIPAA and ISO 27001
Monitor third parties and contractors that use the network
Use Teramind’s Third-Party Risk Management toolkit to:
Track the activity of outsourced contractors and third-party vendors
Protect against accidental and intentional data exfiltration attempts
Leverage scriptable rule logic to create custom policies in line with ITAR, EAR, OGD, GSCP regulations as well as others
Customize solutions to fit your agency
Use Teramind’s Customization and Professional Services to:
Create a secure endpoint monitoring solution targeting your sector’s security, compliance and productivity needs
Collect organization-specific user, compliance, security and workforce data and behavior trends individual to your operations
Compliantly protect against insider threats and monitor user activity
Teramind satisfies regulatory requirements for classified network user activity monitoring as prescribed by Directive 504 from the Committee on National Security Systems (CNSSD 504) and the Insider Threat Program (InTP) Maturity Framework set forth by the National Insider Threat Task Force (NITTF):
Deploy and manage the five minimum UAM capabilities necessary for classified networks— keystroke logging, full app content capture, screen recording, file activity tracking, trigger-based activity alerting, and profile-based monitoring
Capture full application content including email, chat and instant messaging, social media, search activity and more
Utilize the powerful Behavior Policies and Rules engine to create trigger-based alerting and automated responses
Align with NITTF’s InTP Maturity Framework for activity monitoring with real-time data analytics, behavioral risk scoring and UEBA
Implement controls for additional government regulations:
- NIST SP 800-53 Insider Threat Programs
- Executive Order 14028 on Improving the Nation’s Cybersecurity
- NISTIR 7874 Guidelines for Access Control System Evaluation Metrics
- 21 CRF Part 21 – Code of Federal Regulations Protection of Privacy
The Features That Power Teramind
Deployment Options
Find a Teramind deployment option that fits your agency

AWS GovCloud
Combine the scalability of the cloud with the security and compliance of on-premise with the leader in private cloud.

Azure Government Cloud
Get agility, scalability and reliability and meet compliance needs with Teramind deployed via Azure Government.
We bring businesses peace of mind through our award-winning activity monitoring solution
The Experience
Speaks For Itself
Ready to get started?
Improve your security posture, detect insider threats and manage regulation compliance
while improving productivity along the way