Insider Threat Detection Software To Protect Your Sensitive Data
Teramind uses detailed behavioral analytics to detect insider threats in real time, predict future security risks, and prevent data leaks.
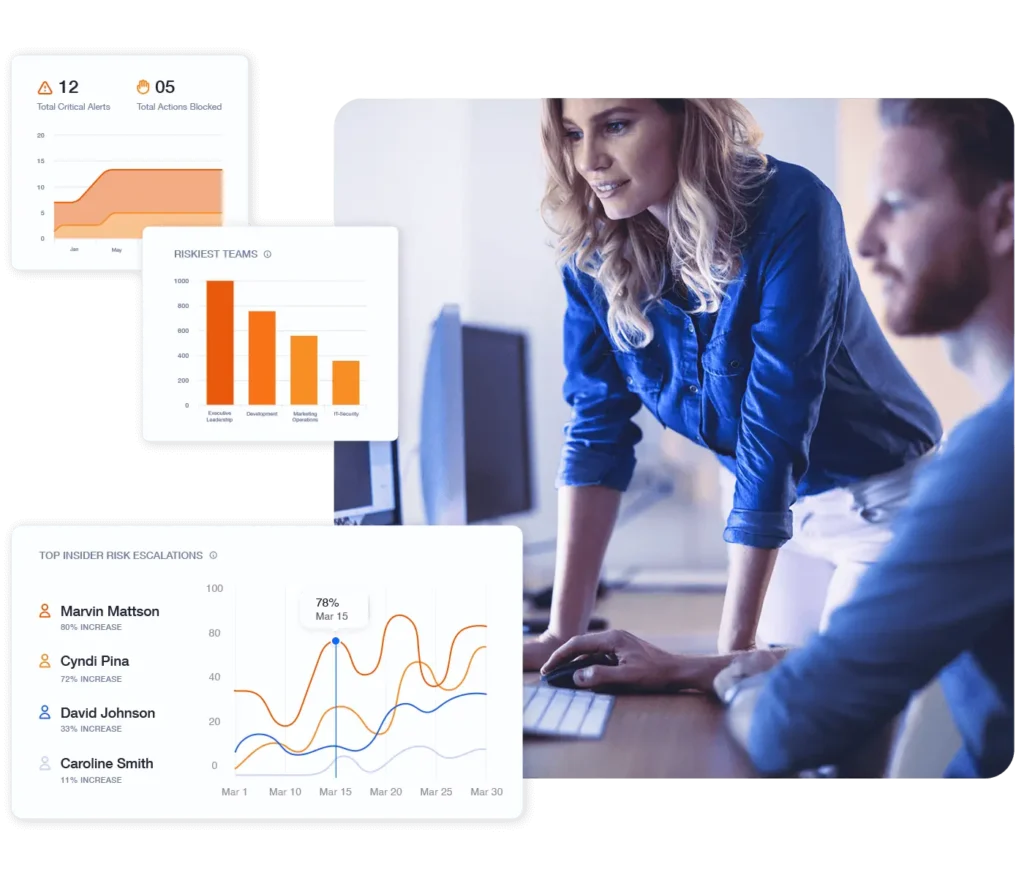
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics









Nearly 75% of Security Professionals Feel Vulnerable to Insider Threats
Malicious insiders are only part of the problem. IT and security teams need to be prepared to handle:
Change
Constantly changing landscape of technologies, apps, and devices
Flexibility
Unmonitored access to sensitive information on growing teams
Risks
Compromised insiders who pose a security risk to companies and data
Lax Security
Contractors and remote teams with lax security and access protocols
See How Teramind Proactively Protects Your Sensitive Data
Teramind collects and analyzes endpoint user data to help teams stay safe, secure, and productive.
Automated Intelligent Alerts
Real-time alerts of data leaks, exfiltration, and malicious activity from insider threats.
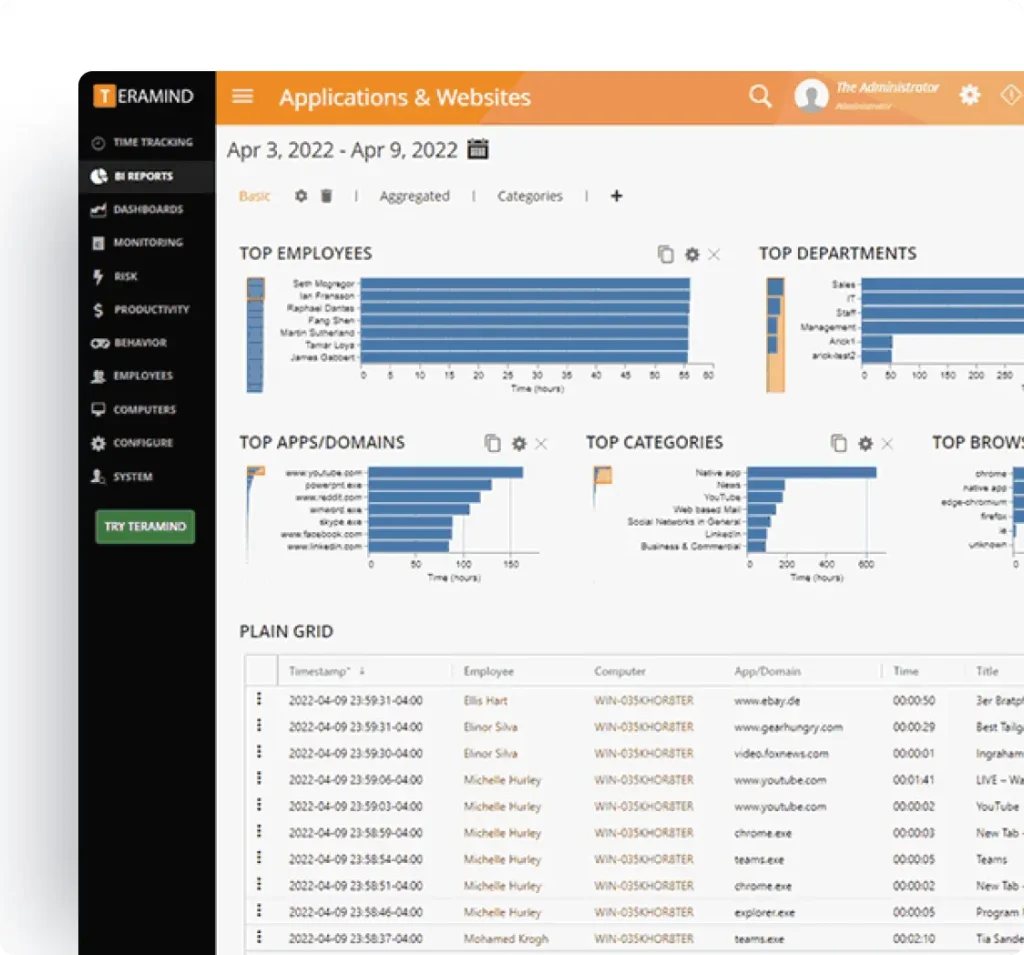
Monitor Employee Behavior
Establish baselines of employee activity to quickly identify suspicious activity and deviations.
⚠ 05 Rules violatedControl Data Sharing
Limit how your organization's data and files are handled with clear privileged access management tools and time restrictions.
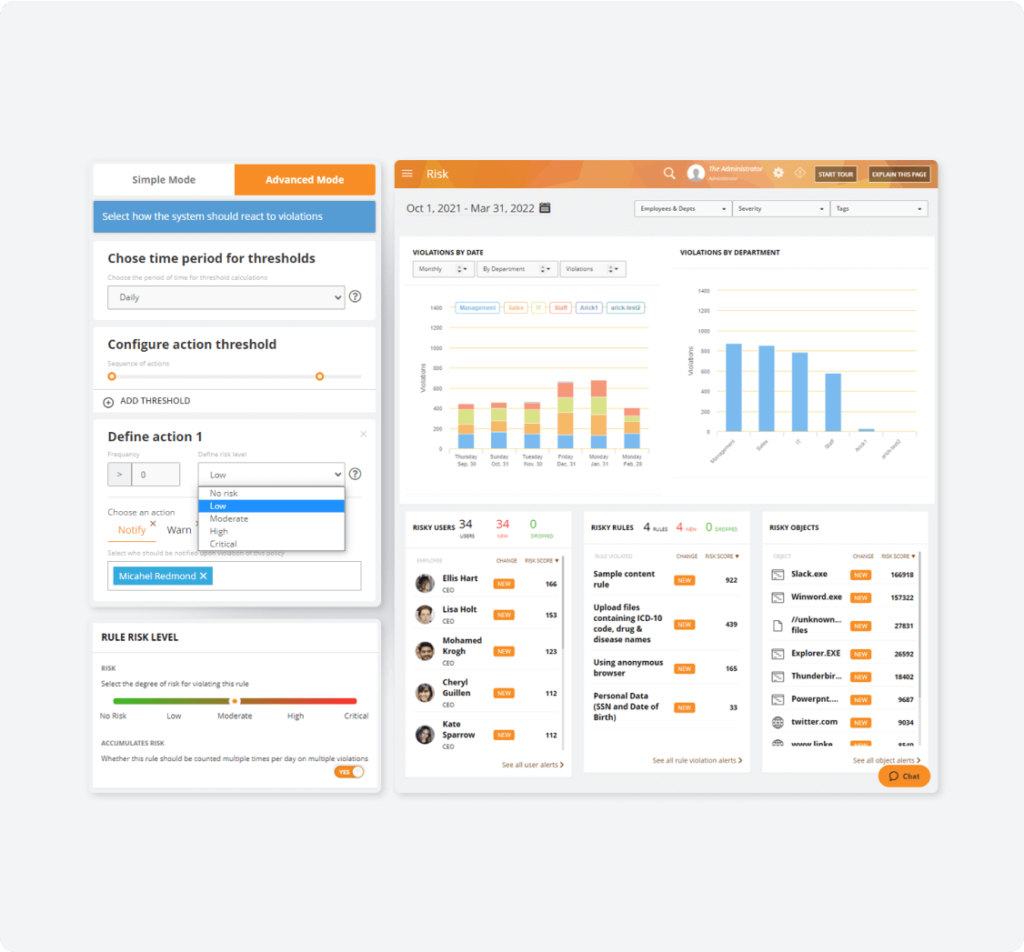
Investigate Security Incidents
Compile forensic evidence for all incidents, including timelines of user actions and administration actions and OCR searches of structured data.
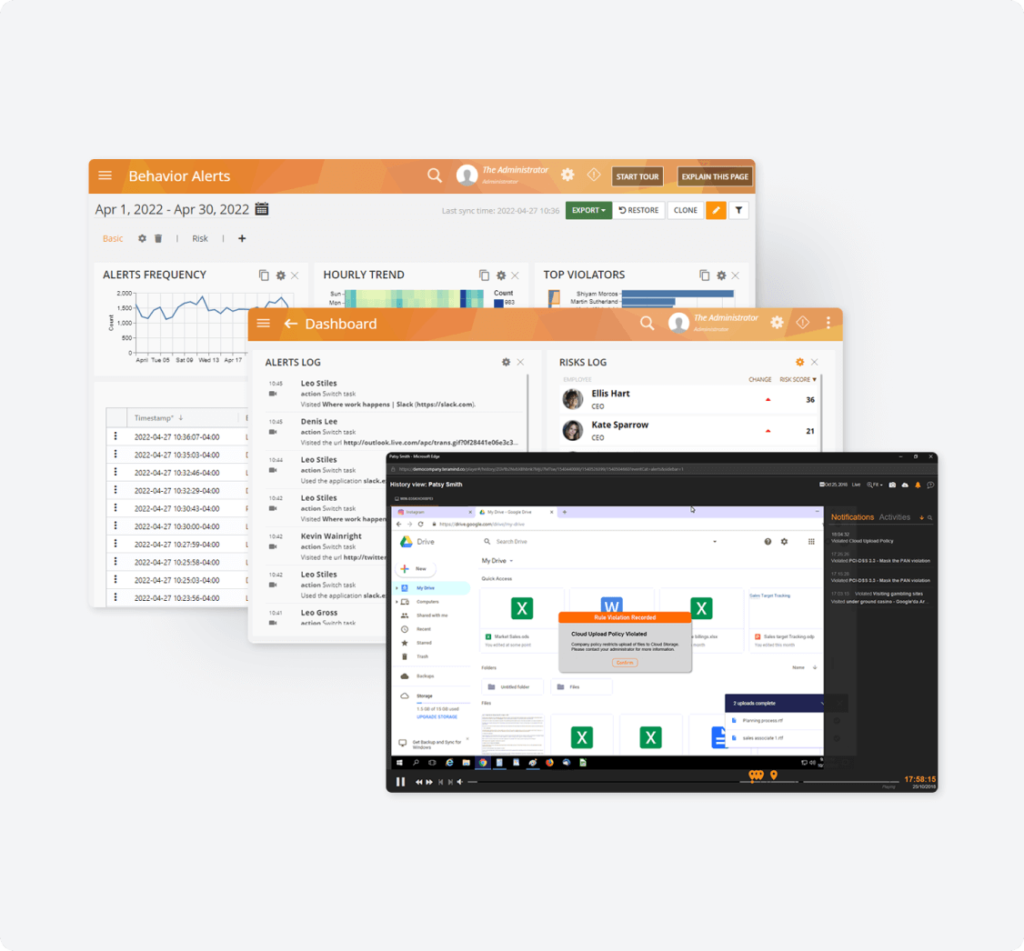
Automated Behavioral Data Loss Prevention
Hundreds of customizable responses to prevent suspicious email activity, unauthorized file uploads, and after-hours access.
Integrate with SIEM and PM tools
Get detailed alerts sent directly to your existing Security Information and Event Management (SIEM) and project management tools.
How Organizations Use Teramind’s Insider Threat Prevention
Monitor contractors, remote, and hybrid workforces
Keep tabs on your team — wherever they are. Teramind alerts you to anomalous behaviors that could indicate potential data leaks or compromised admins and privileged users.
Block users when incidents occur
Quickly take control during security incidents with easy access to file, network, and access privileges.
Predict oncoming threats with intelligent risk assessment.
Prevent unauthorized sharing, downloading, or printing of sensitive data — including HIPAA, PII, PHI, or intellectual property (IP) — with access controls and risky file sharing alerts.
Conduct detailed investigations and collect irrefutable evidence
Perform detailed forensic investigations with Teramind’s forensics features like session playback and OCR to find out exactly what happened during a breach.
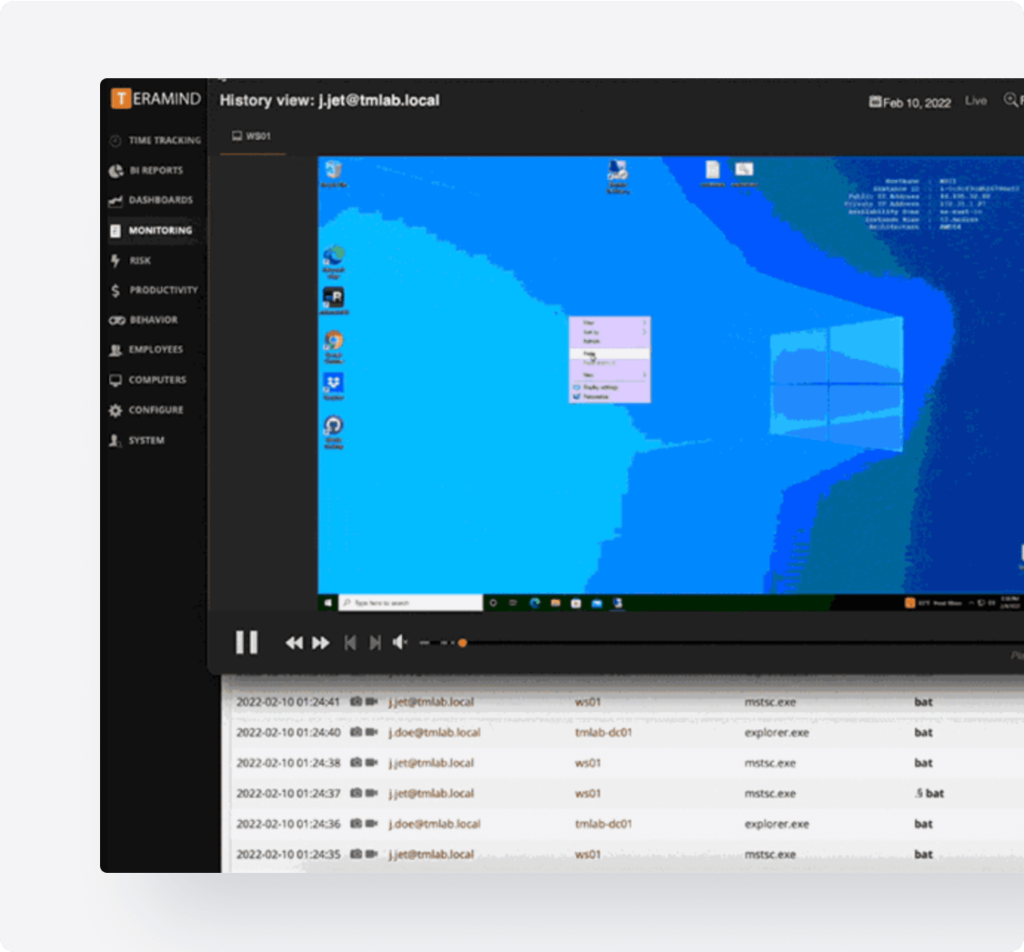
Investigate data security event investigation
Give authorized stakeholders a 360° view of security issues or insider behavior to uncover and neutralize threats.
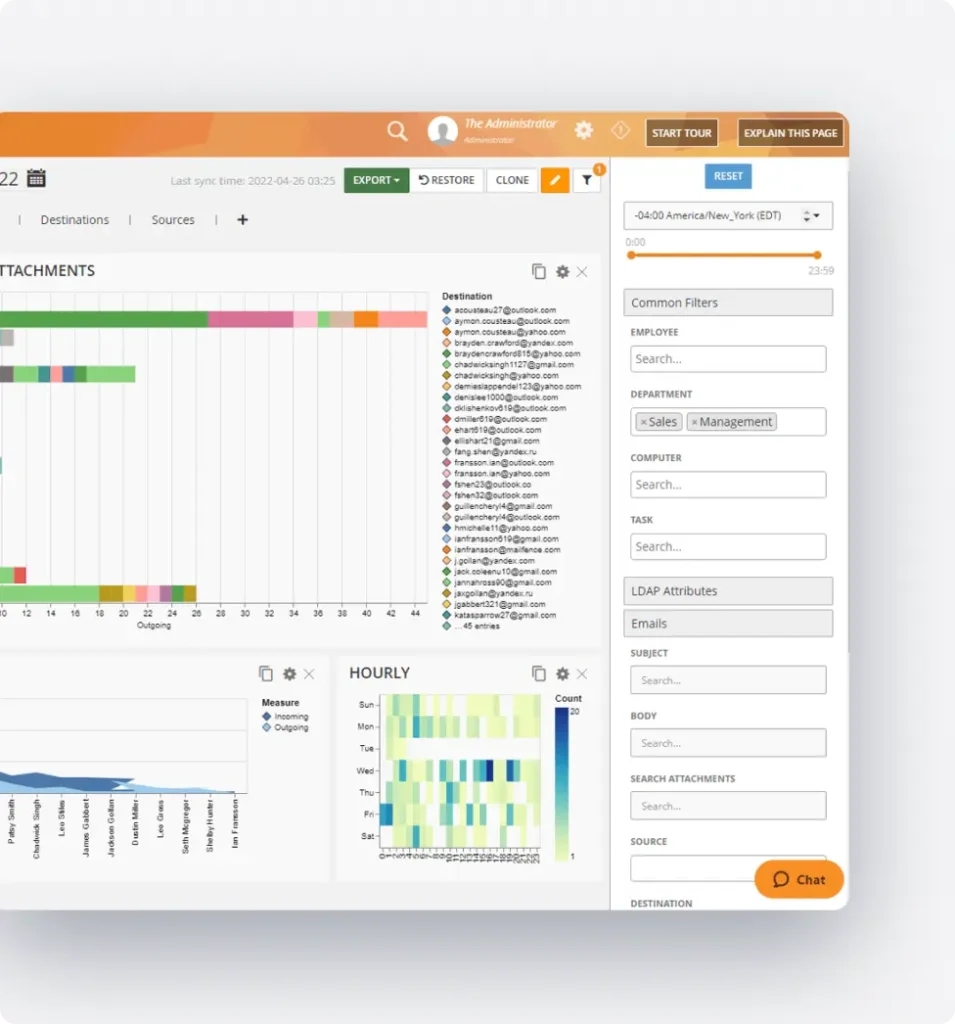
What our Customers Say
Larissa H.
IT Support Specialist
Yakir D.
CIO
IT Security & Risk Manager
$7B Manufacturing Enterprise
| Feature Category | Teramind | Proofpoint ITM | DTEX | Mimecast Incydr |
|---|---|---|---|---|
| Data Collection & Analysis | Advanced data discovery with content analysis | No AI/ML features | Has AI/ML capabilities | Limited monitoring capabilities |
| UEBA (User Behavior Analytics) | Comprehensive monitoring across all applications and systems | Limited user activity monitoring. (No OCR, IMs, audio recording). | No granular activity monitoring | No employee monitoring or UEBA |
| Real-time Threat Detection | Comprehensive monitoring across all applications and systems | Lacks anomaly detection | Comprehensive monitoring across applications | Limited detection for network, email, and files |
| Incident Response & Forensics | AI-driven alert prioritization and forensic tools (OCR, Screen Recording) | Efficient incident management console | Lacks investigation tools such as screen recording | No OCR detection |
| Policy Enforcement | Highly customizable policies with real-time enforcement | Not Publicly Listed | Has block action, but less varied than Teramind | Not Publicly Listed |
| SIEM & PM Integrations | Integrates with SIEM and PM platforms (Splunk, etc.) | SIEM integrations available | SIEM integrations available | SIEM integrations available |
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

FAQs
How To Prevent the Latest Insider Threats
How does insider threat detection software work?
Insider threat detection software uses AI and machine learning to analyze user behavior on endpoint devices and create baselines for “safe” activities. When potentially dangerous deviations are identified, companies are notified in real time so they can shut down threats.
This includes unusual or unauthorized file and system access, data exfiltration, or other behaviors that could indicate a cyberattack.
Insider threats can be both intentional — such as a compromised employee sharing company assets with a competitor or external threat— or unintentional — such as a user clicking on a phishing link, accidentally downloading malware, or using unsecured file sharing services.
What are the most common insider threat indicators?
The most common insider threat indicators include:
- Unusual behavior. This can include excessive data exports or transfers, unauthorized download patterns, a sudden increase in printing sensitive documents, sending company files to personal email addresses, or transferring data to off-network locations.
- Access abuse. Threat actors often attempt to gain higher levels of access privileges or may try to access systems using another user’s credentials. Failed login attempts can also signal that a user has been compromised by an external threat.
- System configuration changes. Warning signs can also include insider threats attempting to cover their tracks by changing system or network configurations, using a VPN or proxy, or attempting to disable security tools.
- Behavioral changes. Beware of users who suddenly change when and how they access company data and servers, such as attempting to access files outside of the scope of their position, out of usual working hours, or from an unknown IP address.
- Risky actions. Insider threats can also be unintentional, such as using an unsecured file sharing service or accidentally sharing sensitive documents with people outside of the organization.
What industries are most at risk from insider threats?
Nearly every industry and company has a valid use case for insider threat detection — whether you want to protect sensitive data or secure yourself against costly data breaches.
Some of the most at-risk industries include:
- Healthcare and other companies that collect and protect sensitive data.
- Finance organizations that are prime targets for insider and external threats.
- Technology companies with sensitive and proprietary intellectual property.
- Government agencies that could be targeted by malicious outsiders.
How much can data exfiltration and malicious IP theft cost my company?
According to the latest IBM Cost of a Data Breach report, the global average cost of a data breach in 2024 climbed 10% to USD $4.88 million2 — the highest number ever reported.
What are the most important features you should look for in insider threat detection software?
Security platforms should tackle multiple threat angles, from malicious insider attacks to accidental data leaks, device and account compromise, and more. For example, Teramind’s insider threat management solution includes:
- User entity behavior analysis (UEBA)
- Insider risk management and data loss prevention (DLP)
- File transfer tracking and access management
- Proactive threat detection
- Employee sentiment analysis
How do you implement an effective insider threat detection and mitigation strategy?
A solid strategy can help you prevent insider threats. At a high level, you should:
- Implement an insider threat detection and data loss prevention solution.
- Track employee activity using user activity monitoring software.
- Conduct regular risk assessments and employee sentiment analysis.
- Set limits on file and network access and eliminate idle accounts.
- Train employees on security awareness and enforce account protection policies.
- Conduct regular security audits to uncover cyber threats.
- Apply the principle of least privilege (PoLP).
- Establish an employee reporting program.
