Employee Behavior Analysis
Are your employees also your biggest blind spots?
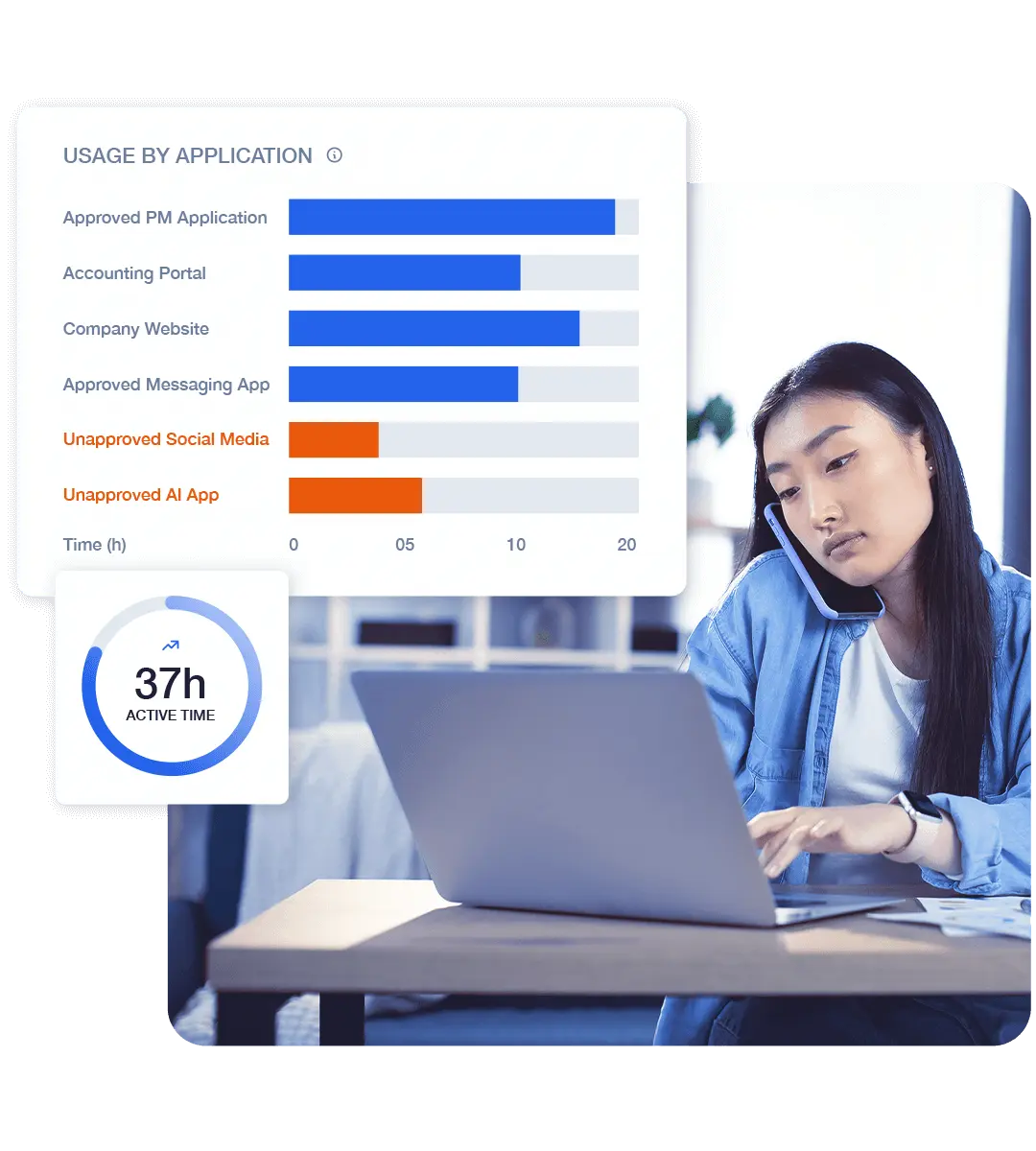
Set baselines, make changes, and measure the results over time.
Step 4
Did you
know?
Early, visible indicators of an insider threat are often productivity related:
- Frequent tardiness
- Policy violations
- Disengagement

Proactive leaders rely on accurate data to make better decisions about efficiency, team design, and security controls.
Fuel Comprehensive Behavior Analysis With Teramind’s Unparalleled Features
OMNI: What will you uncover?
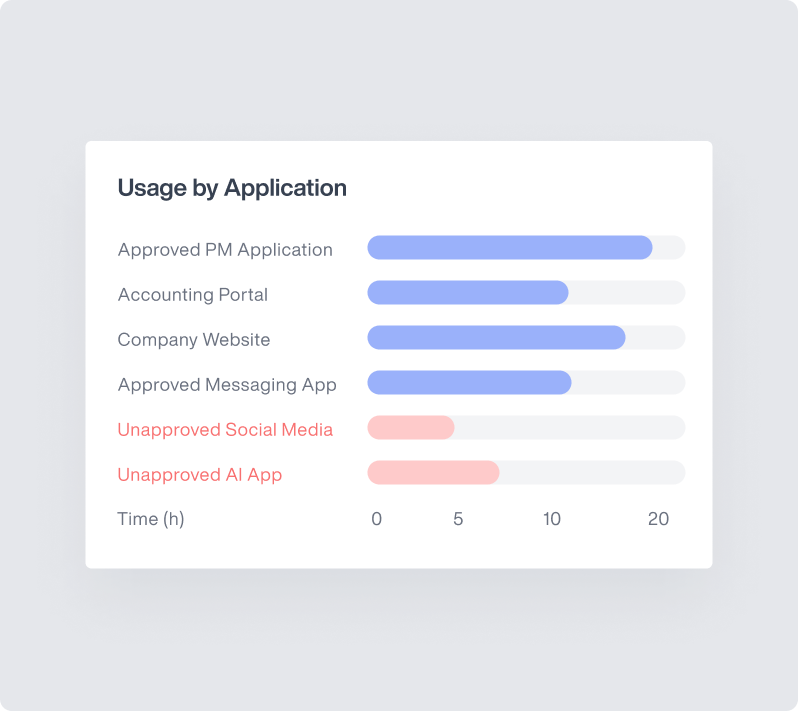
Website & Application Monitoring
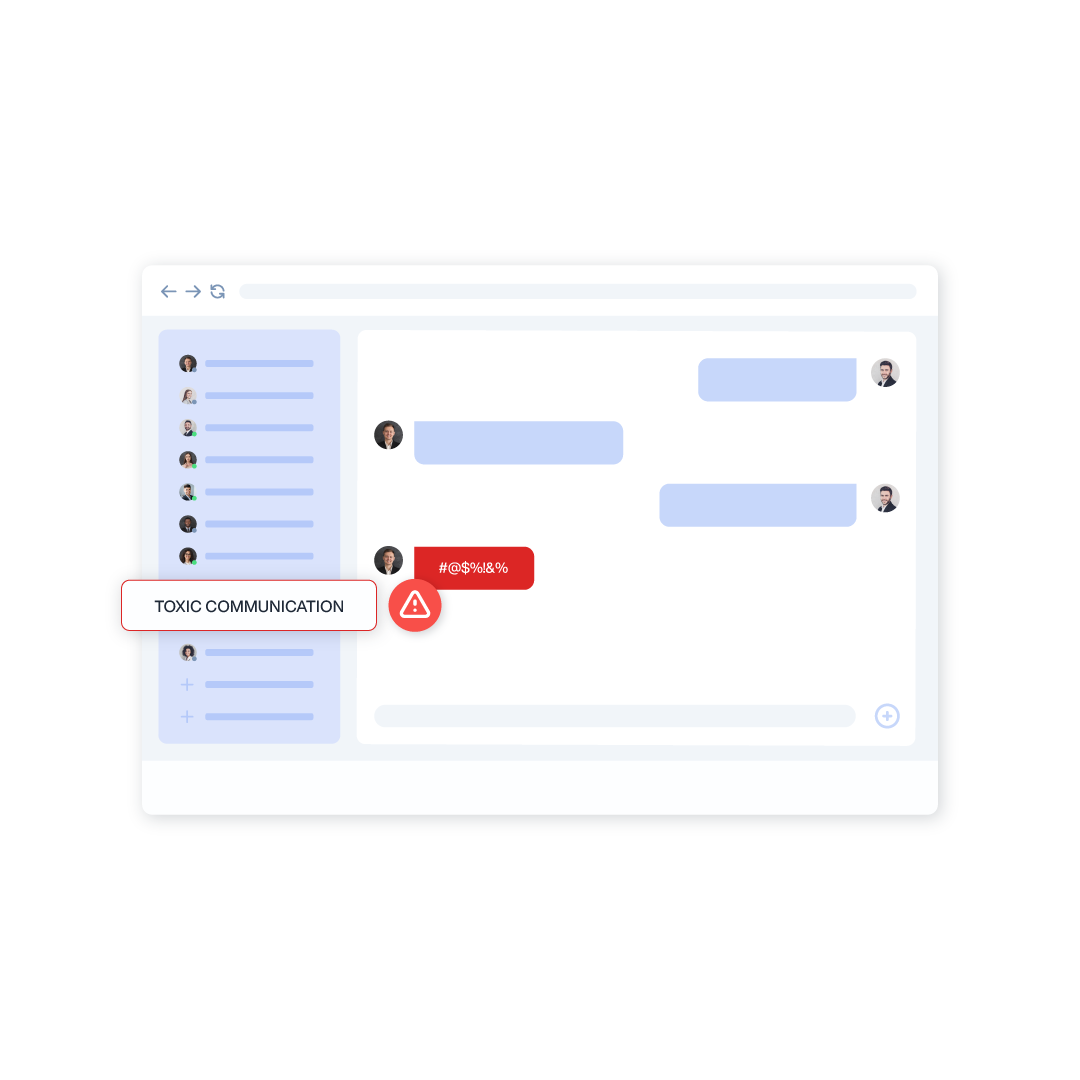
Instant Messaging Monitoring
Time-Stamped Screen Recordings

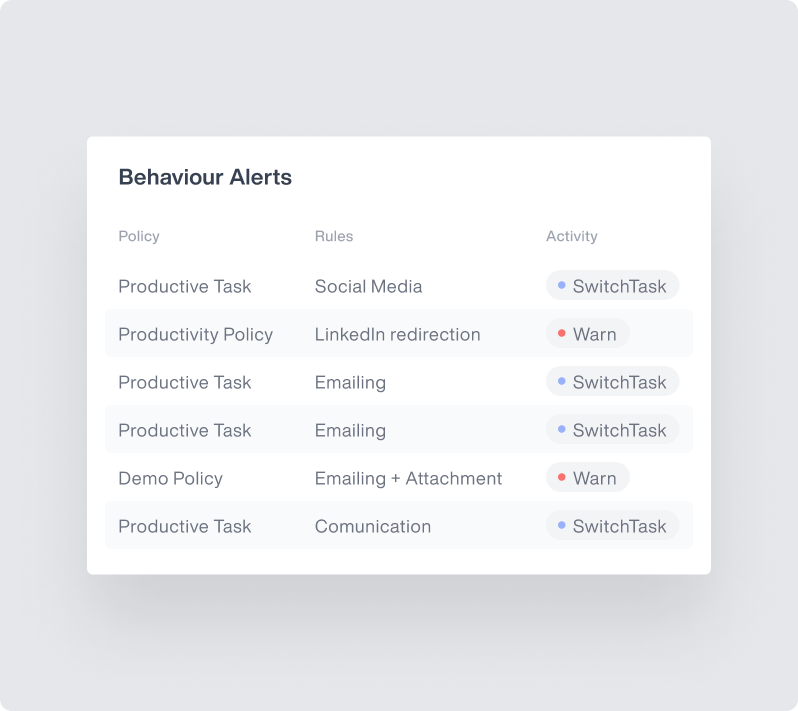
Smart Rules & Automated Responses
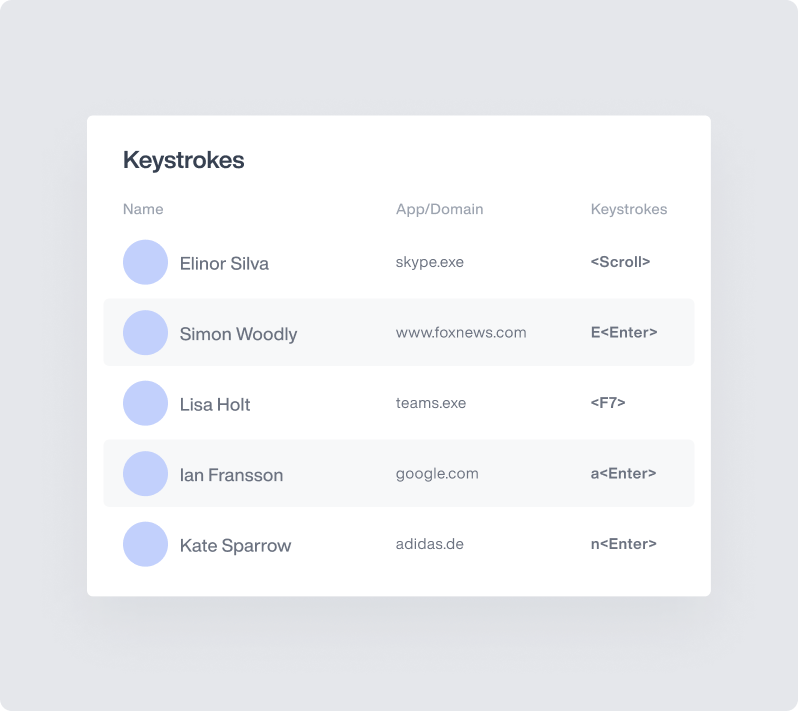
Keystroke Logging
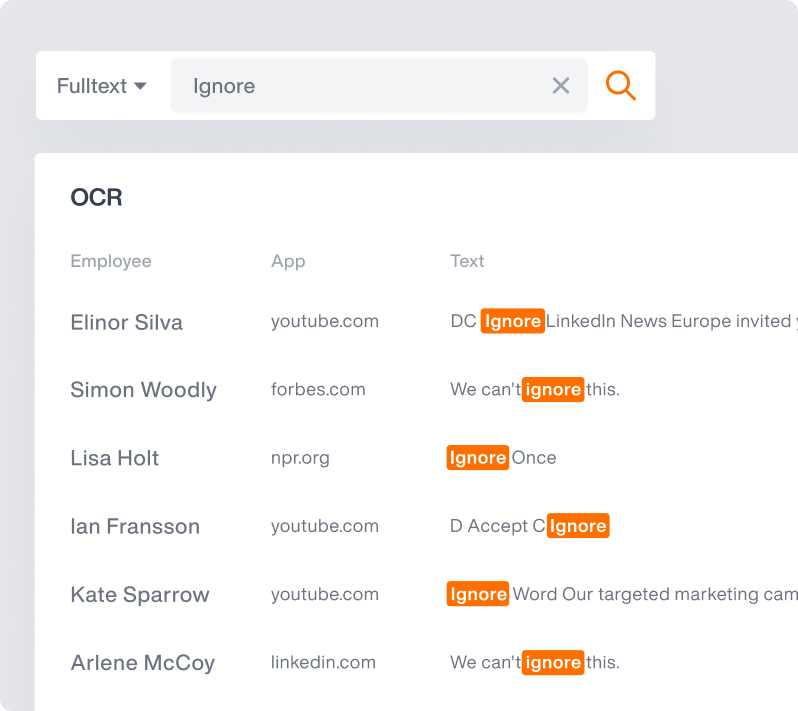
Optical Character Recognition
Gain Predictive Insights With Teramind’s AI Engine
Teramind AI gives you real-time insights – so you get the answers you need, faster.
Are we overlooking employees who could become great leaders?
How do HR inputs affect employee productivity rates?
Is my employee’s risky behavior an accident or intentional?
Humans are complex, and the stakes are high. Basing conclusions on a single data point can lead to wrong assumptions. Teramind AI learns from numerous behavioral data points to give you a clearer picture of what’s happening.
How do I know when to step in and help an employee to avoid a threat?
Teramind’s predictive insights help you identify red flags early on – like withdrawal, antisocial behavior, and more. Use your org’s real-time data to apply real-time solutions.
How can I predict when an employee has crossed the line and intends to commit an insider threat act?
People who intend to commit insider acts often show warning signs first. Teramind AI draws from employee behavioral changes to understand how close – or far away – they are from becoming a threat.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“Overall, it’s great and it works for what it was implemented for. It accurately tracks hours and it is both app and web based so you can use it wherever you go. It’s easy to use and can work for employees and independent contributors alike. A great tool for small business owners.”
IT Security & Risk Manager
$7B Manufacturing Enterprise
“Cost effective and feature reach DLP and User Behaviour Monitoring Tool. Easy to set up even on-premises. No end-user impact. Cost-effective. Both DLP and User behavior Monitoring.”
IT Manager
$3B Managed Services Provider
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Renee H
Head of IT Security
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics









