Unified Security through Endpoint Monitoring for Energy & Utilities
Monitor and protect systems, user endpoints and confidential information while shoring up compliance management
Protect critical systems and infrastructure from
negligent and malicious insider misuse
Defend against insider threats and data breaches
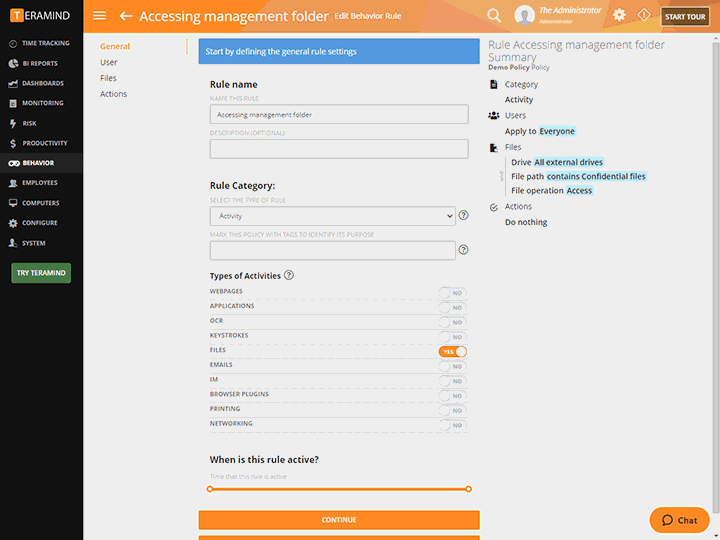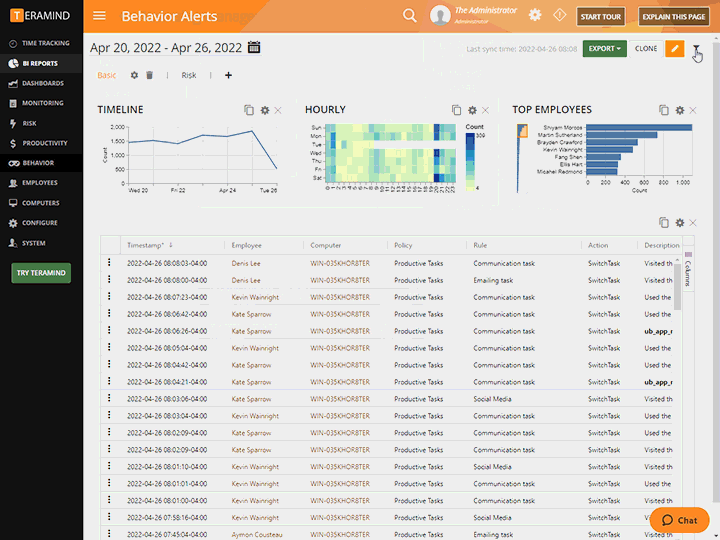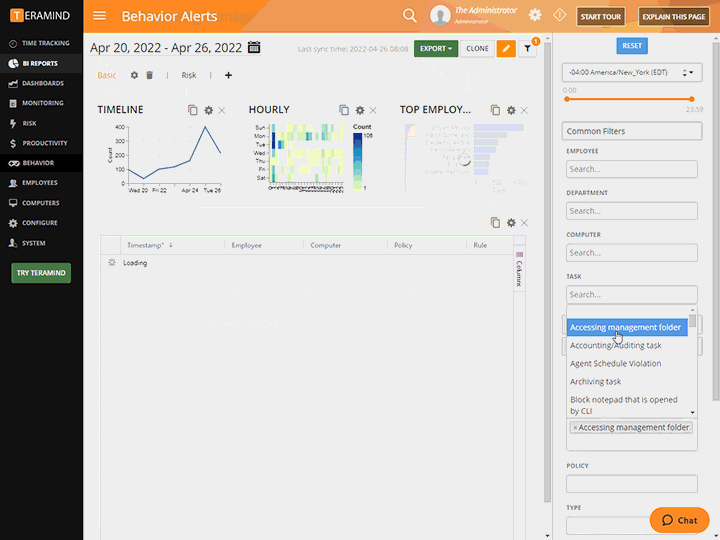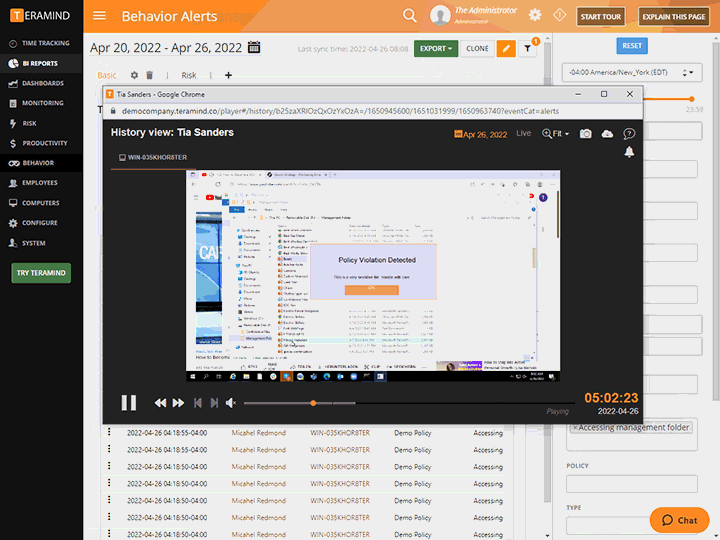
Use Teramind’s Scriptable Rule Logic and Automated Rules and Alerts to:
Detect and block malicious and anomalous user activity on endpoints
Build comprehensive data handling rules and policies
Prevent data exfiltration and unauthorized file transfer & data sharing
Secure sensitive data and trade secrets against loss
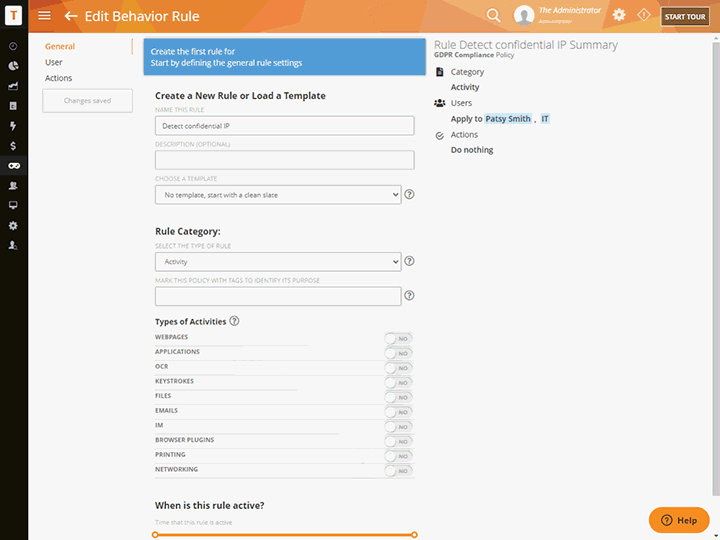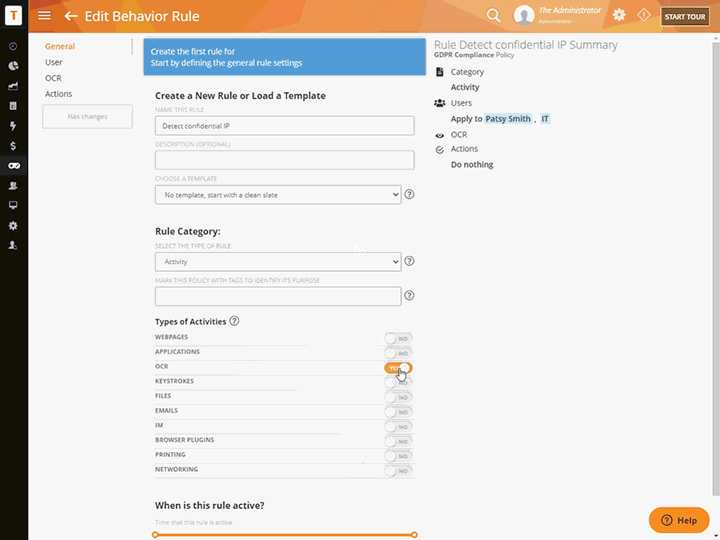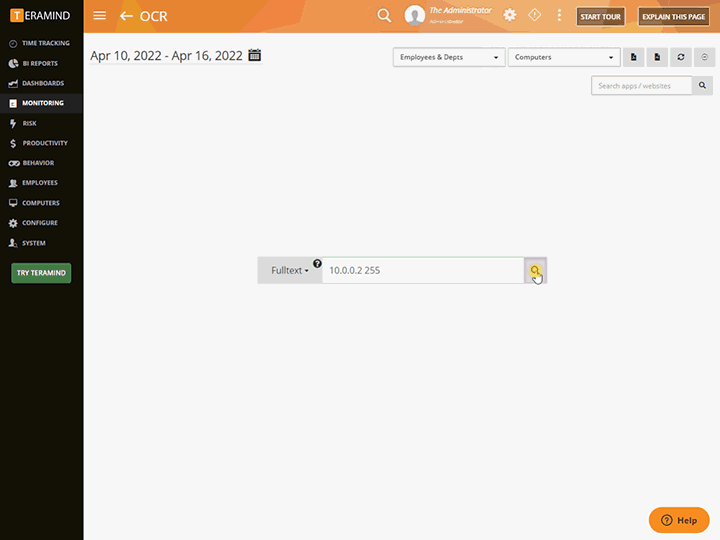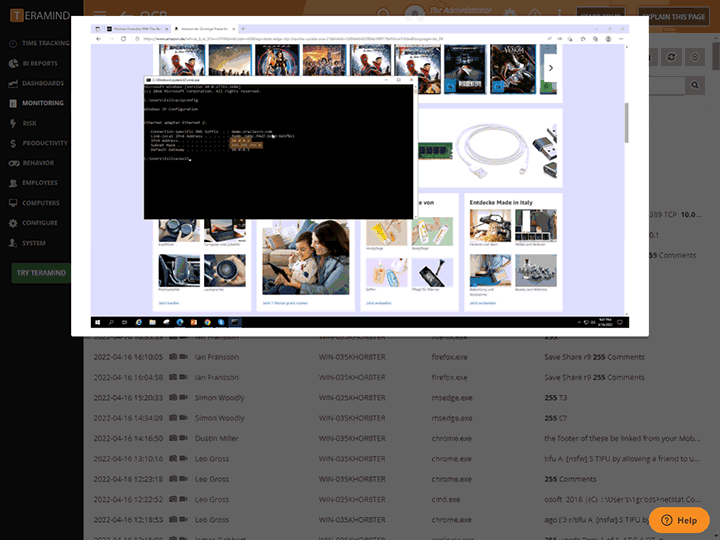
Use Teramind’s Content Discovery, Data Fingerprinting and OCR to:
Discover sensitive and confidential data in-use, in-motion and hidden in unstructured data like images and videos
Monitor organization specific data like IP, trade secrets, seismic readings and prospecting plans
Track how sensitive data, files and documents journey through a network, with or without being edited
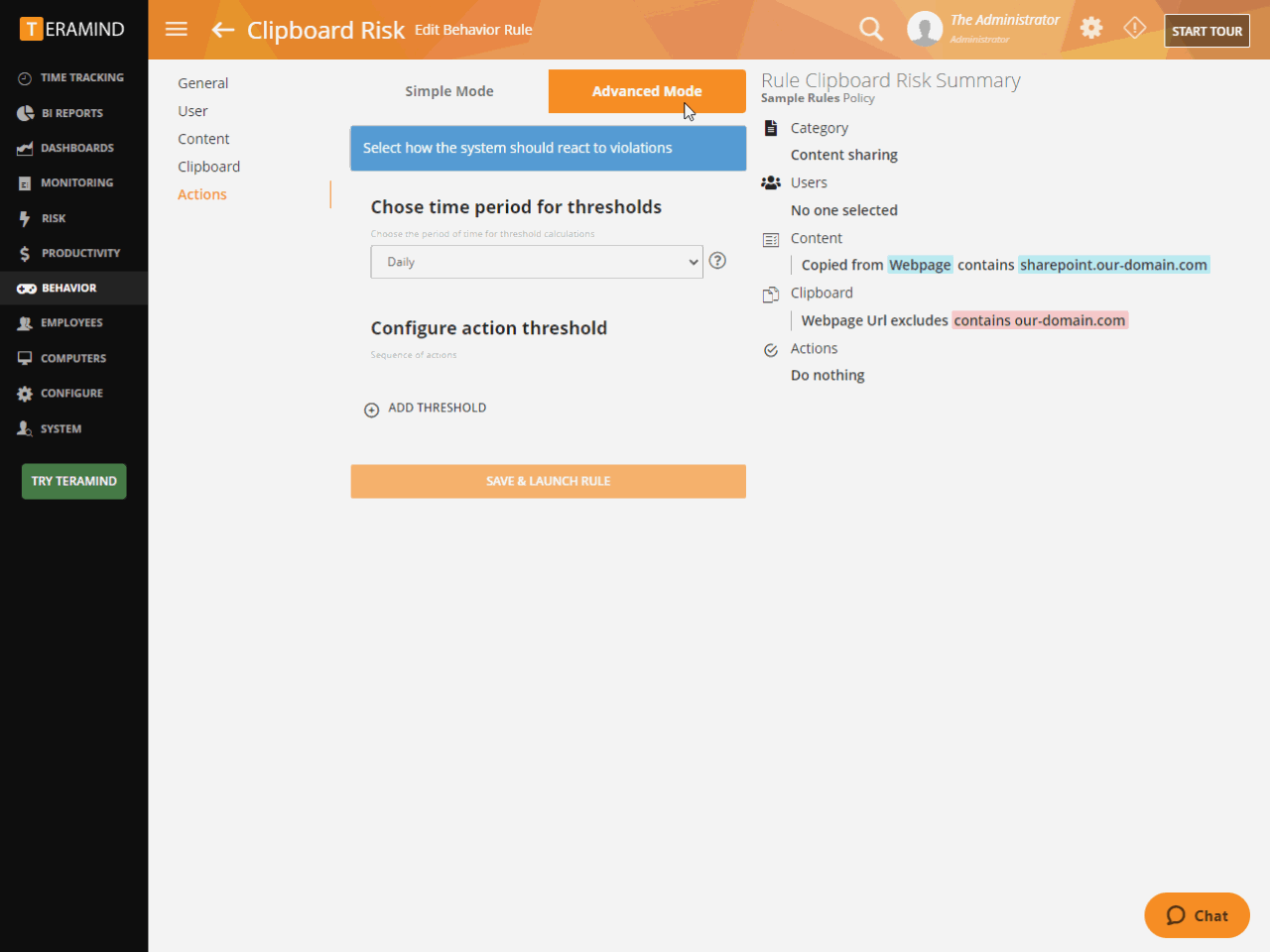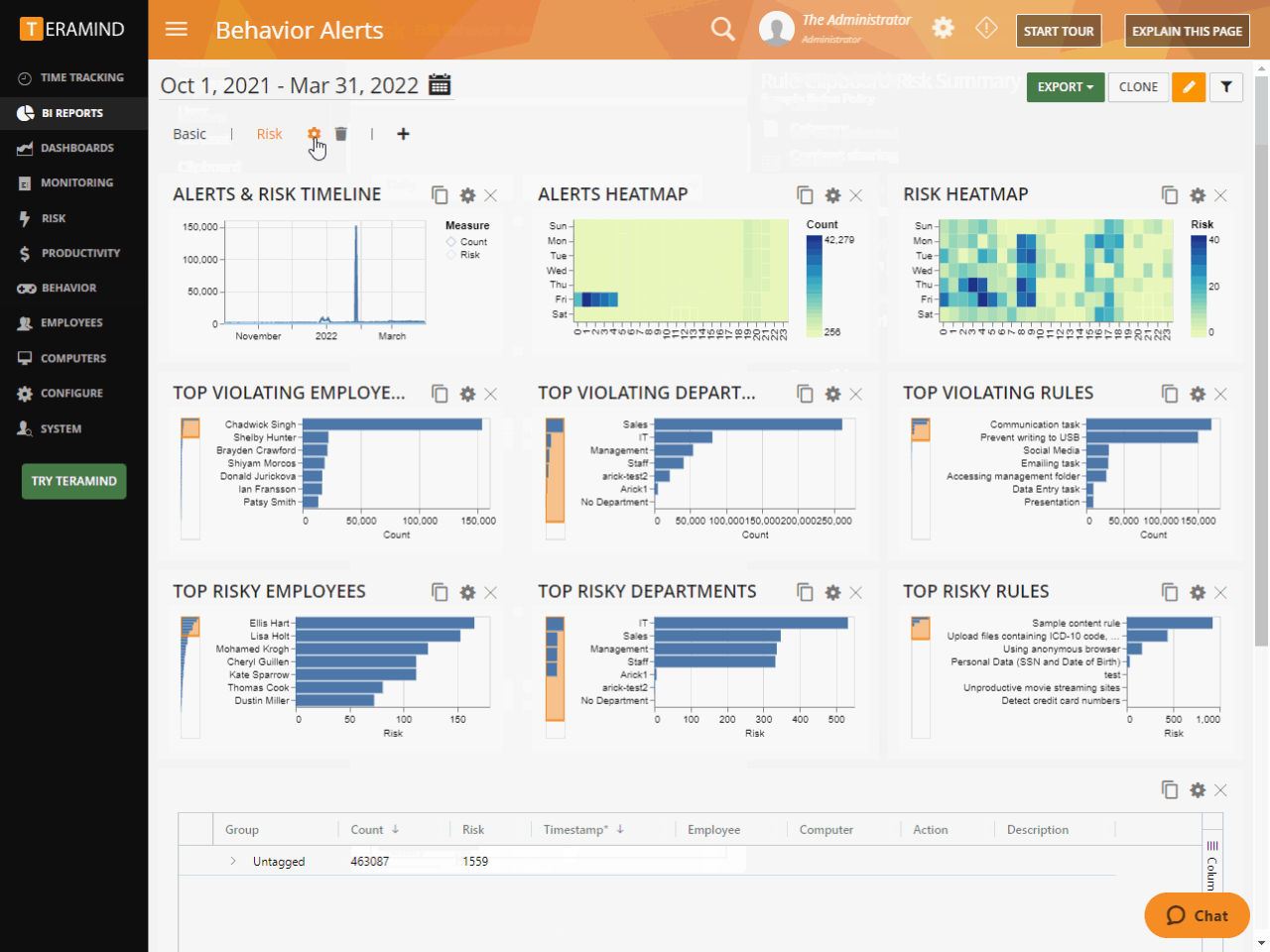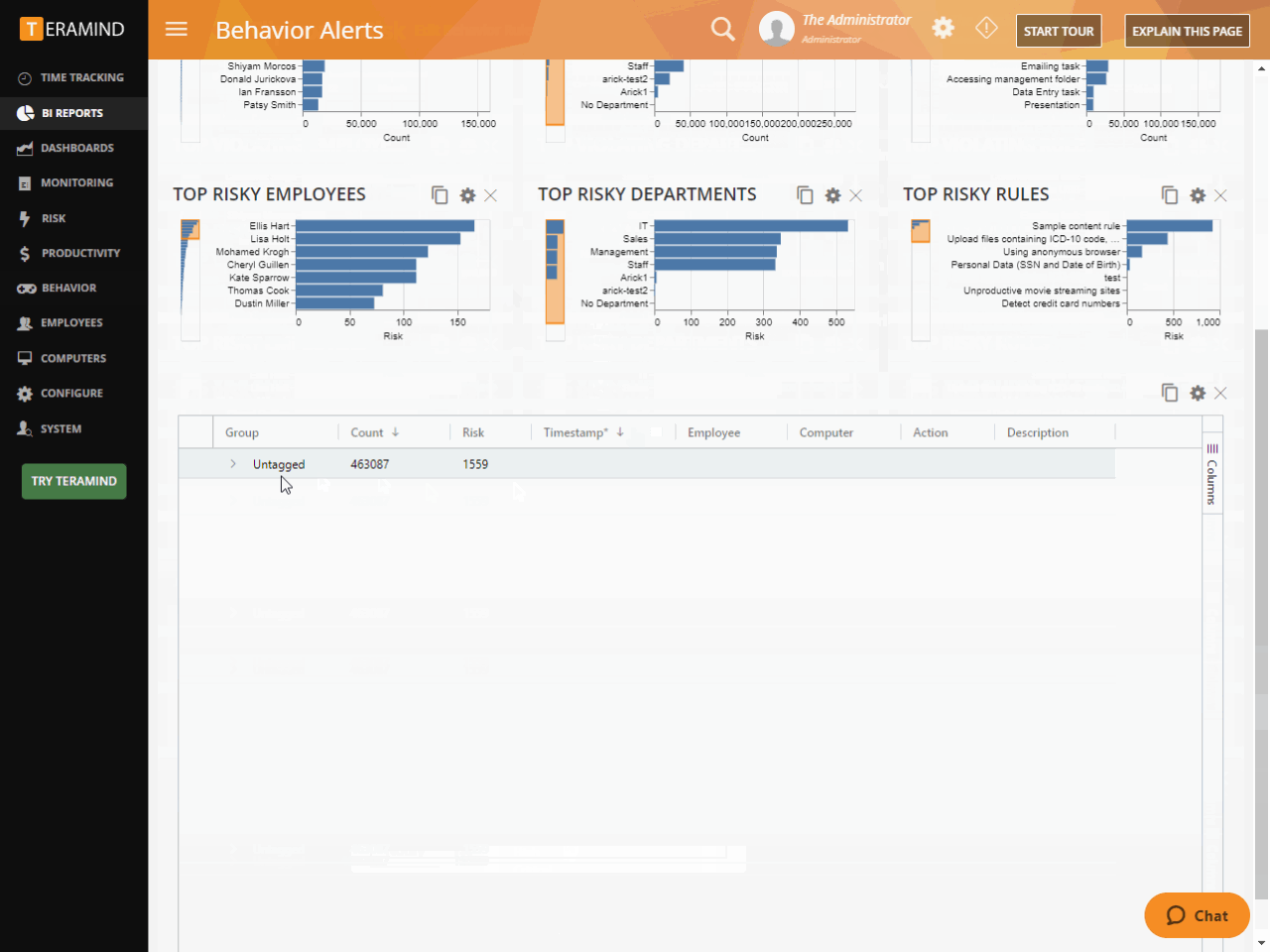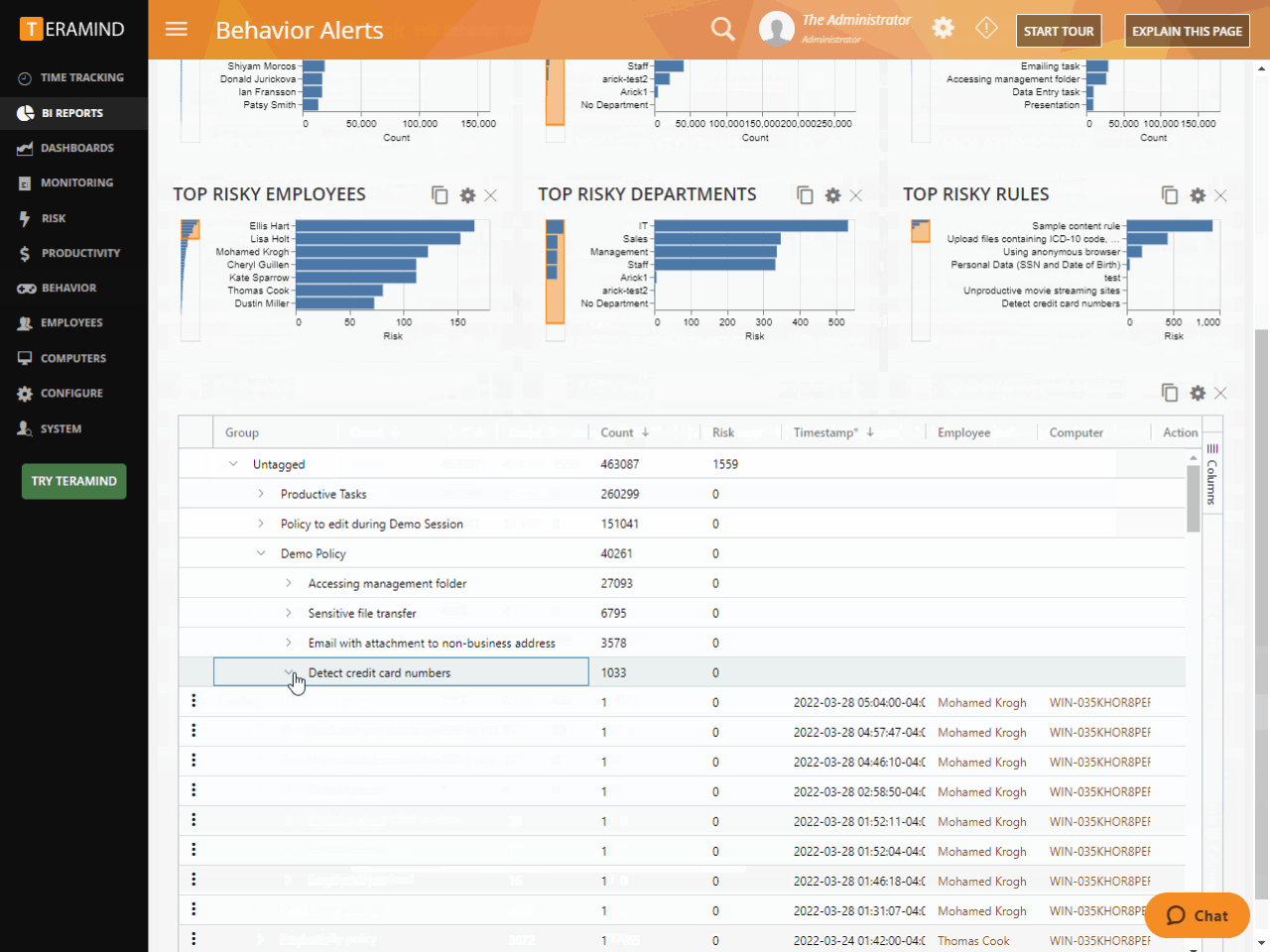
Gain complete visibility of endpoint activity
Use Teramind to user activity monitoring to:
View and control how employees use, access and transfer confidential trade data
Pinpoint process bottlenecks and system inefficiencies
Monitor contracts, third-parties or other vendors that have privileged access to sensitive data and the network
Identify user behaviors on the network that put your IP and other sensitive company data at riska and the network
Manage and fulfill industry compliance requirements
Use Teramind’s compliance management toolkit to:
Conform with security and regulatory standards like NERC, FISMA, FERC, ISO 27001 and GDPR
Gather detailed evidence for investigations and audits like immutable activity logs, session video recordings and audit trails
Strengthen in-house cybersecurity training for employees with risk-targeted sessions
The Features That Power Teramind
We bring businesses peace of mind through our award-winning user activity monitoring solution
The Experience
Speaks For Itself
Ready to get started?
Improve your security posture, detect insider threats and manage regulation compliance
while improving productivity along the way