Privileged User Monitoring
Protect sensitive data against those who can do the most harm
Privileged User Monitoring, Privileged Access Management and DLP Technology to Protect Your Data & IT Systems
Privileged users have access to your core IT systems, network, applications, and data. The threats associated with privileged user accounts can be incredibly difficult to detect before they cause damage.
Teramind’s real-time privileged user monitoring and data loss prevention solutions help you monitor privileged users to automatically detect anomalous behavior and suspicious activity.
System Wide Monitoring and Control
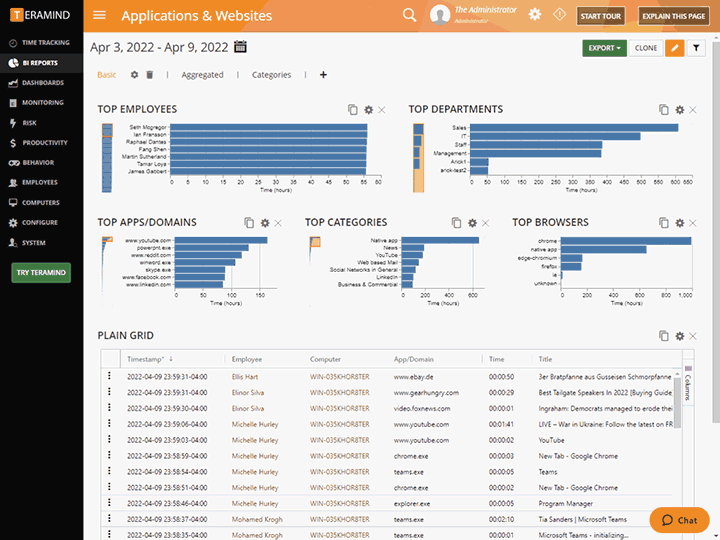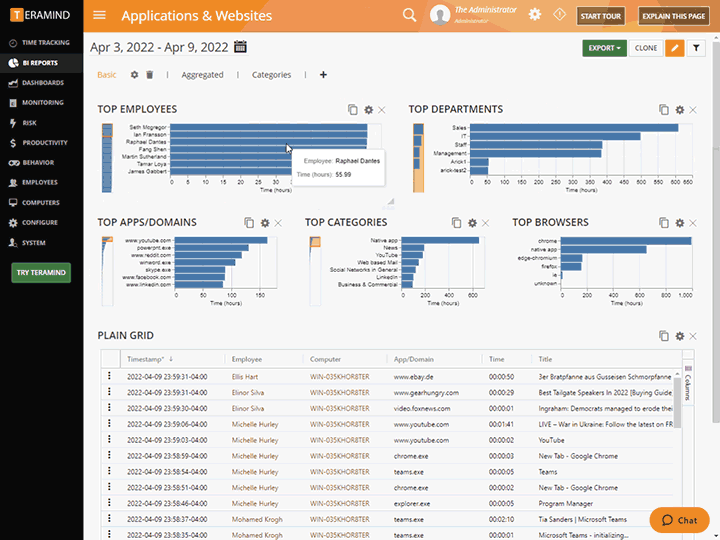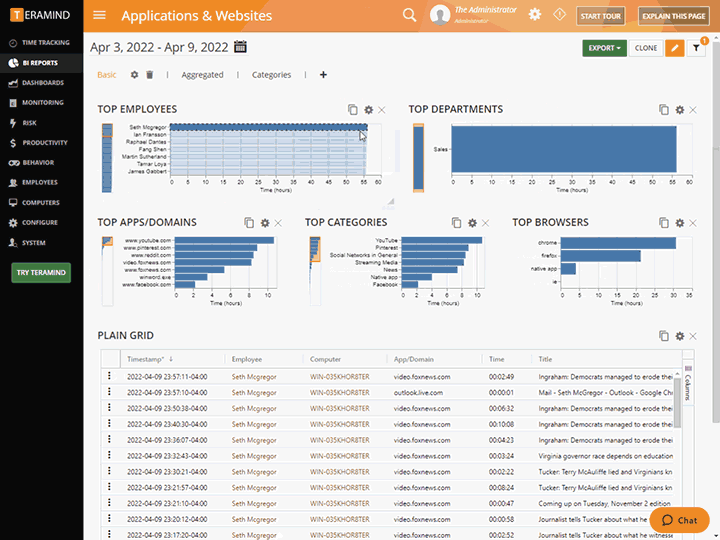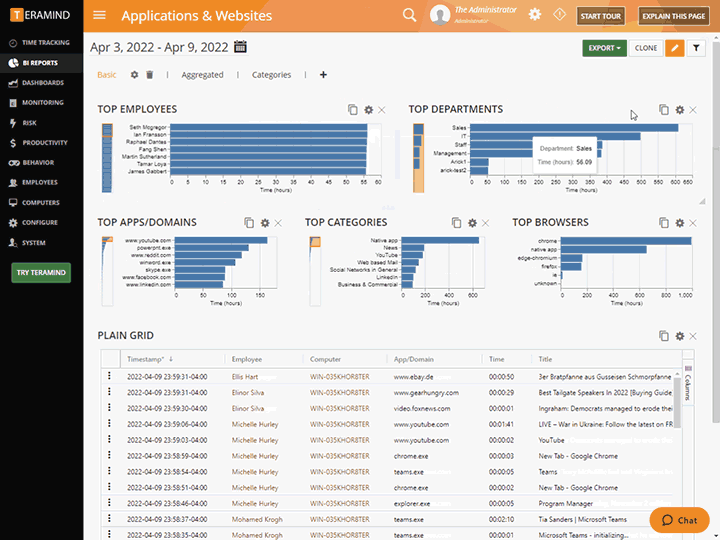
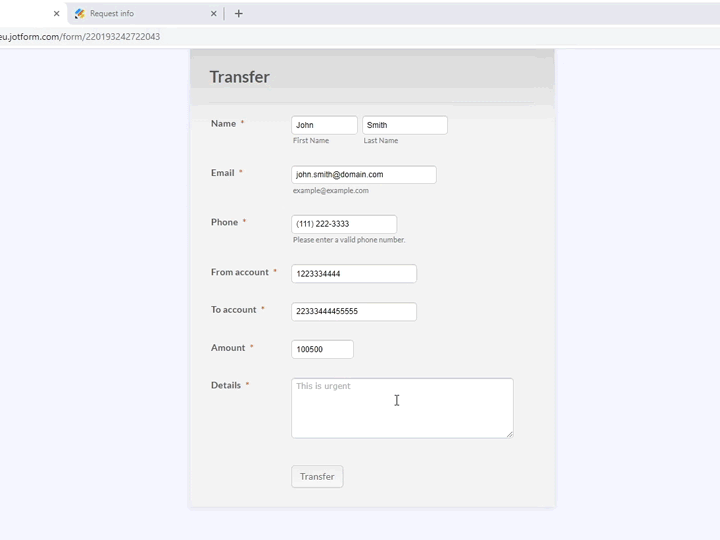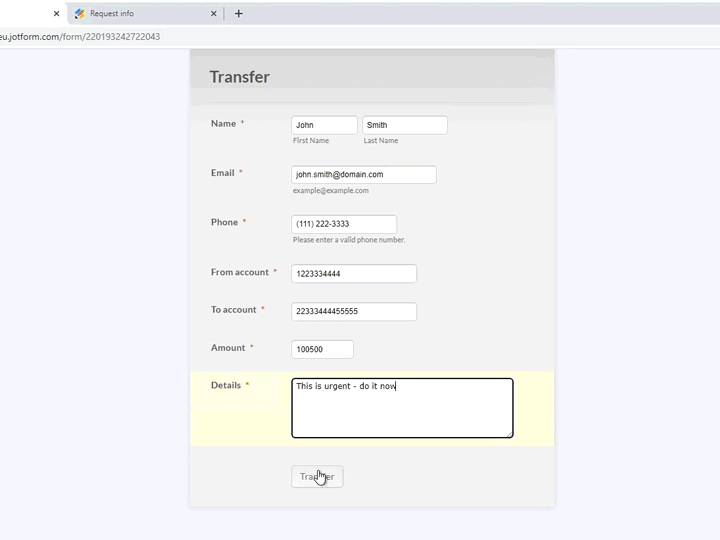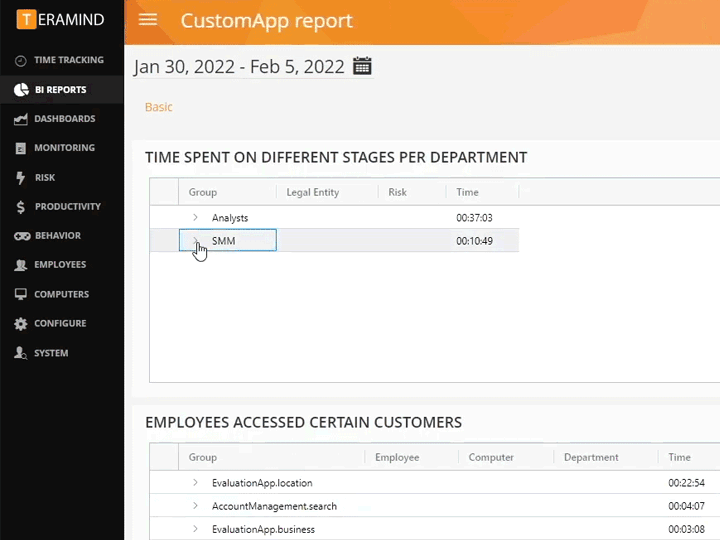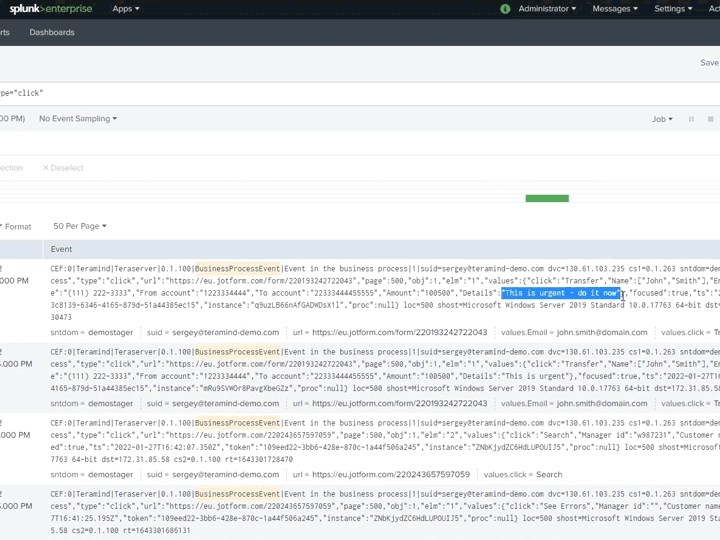
Teramind’s privileged user monitoring visually records every action that a privileged user makes on your IT systems, including endpoints, servers/terminal servers, network, and the Cloud
Monitor virtually all activities including actions taken in custom apps, web use, app use, file transfer and more
Uncover what your users are up to, both online and offline using privileged user monitoring
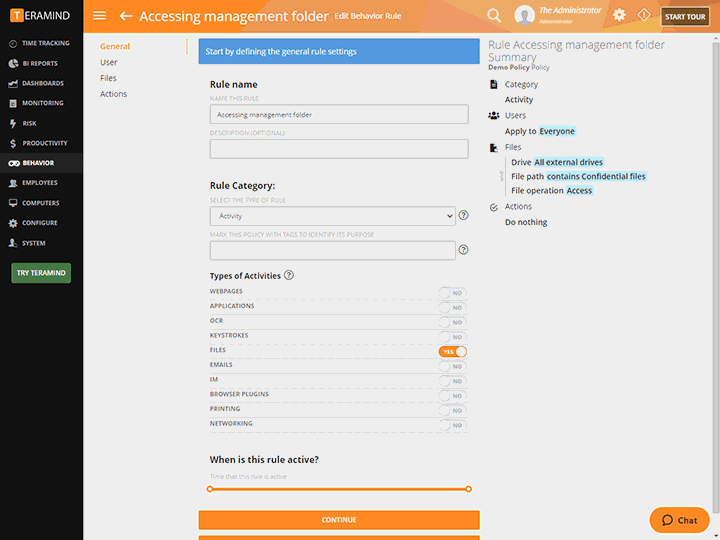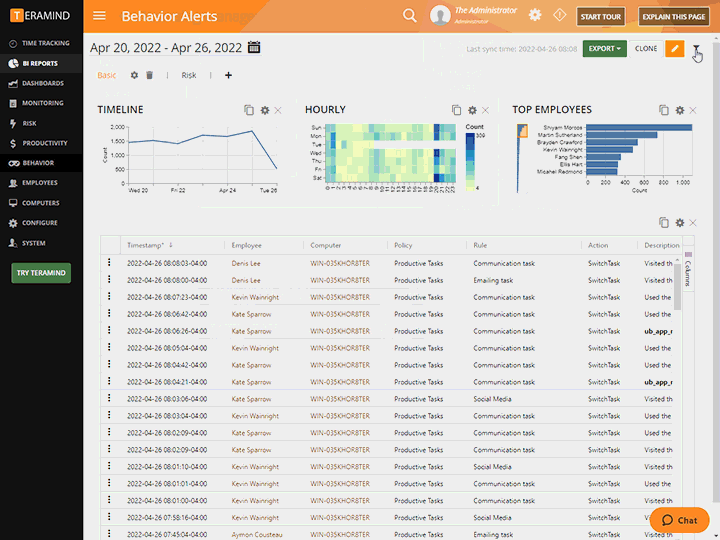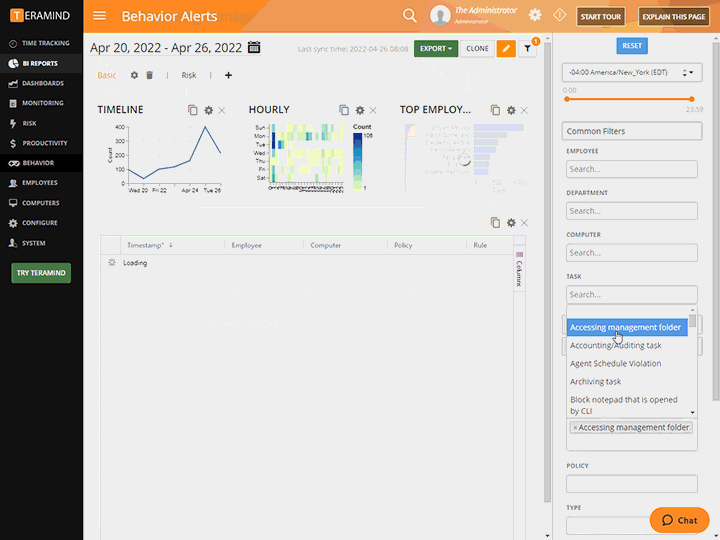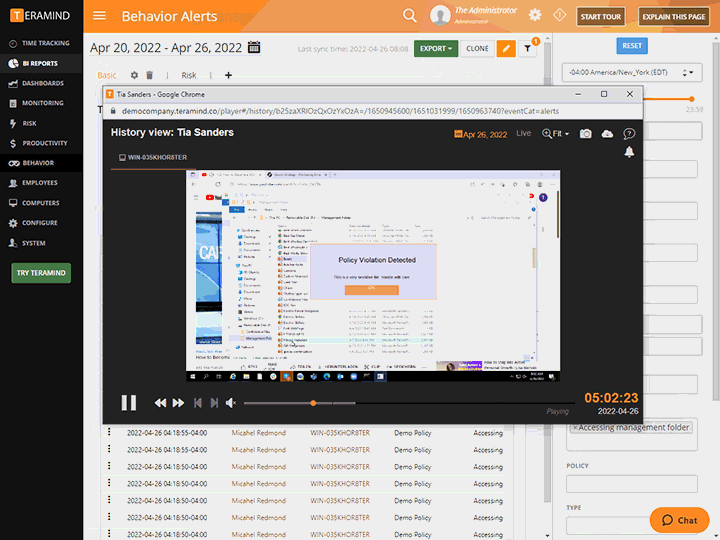
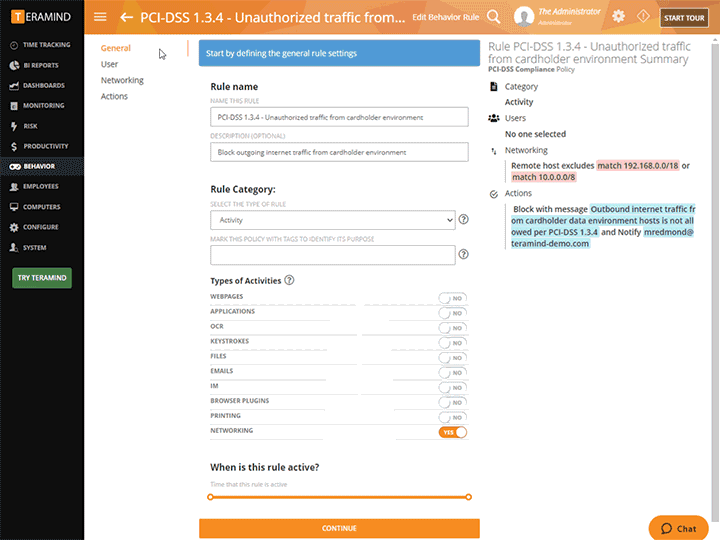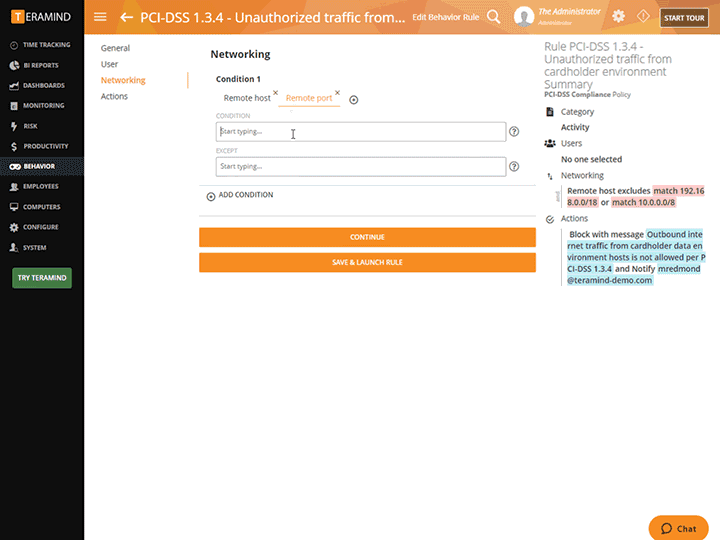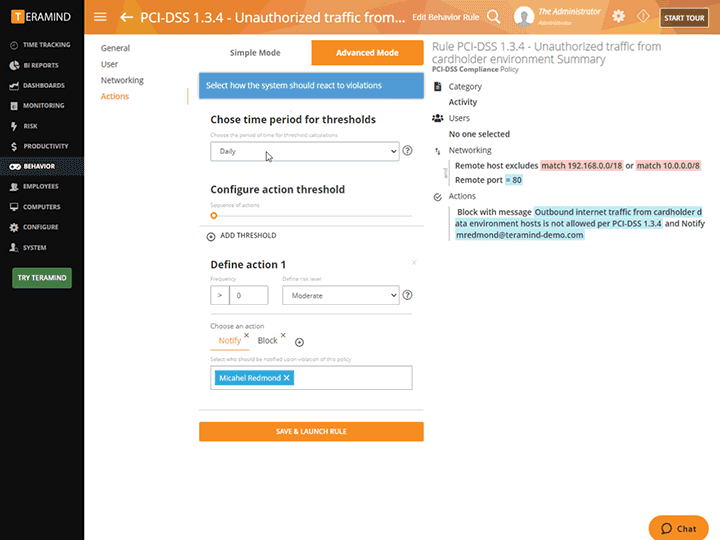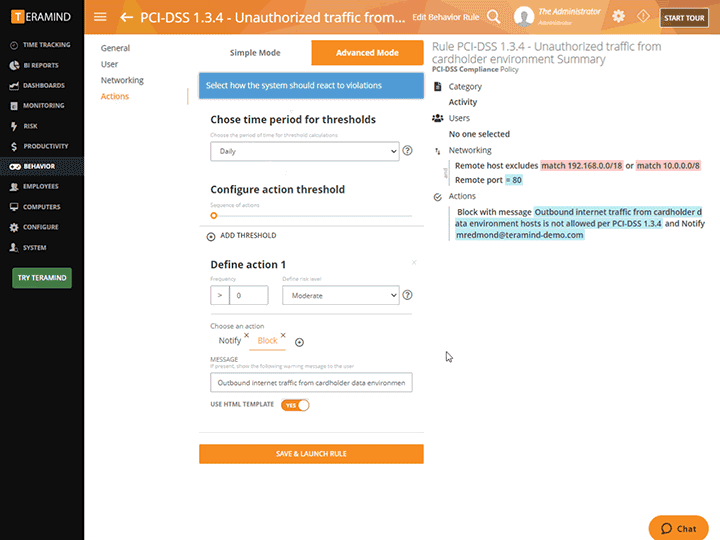
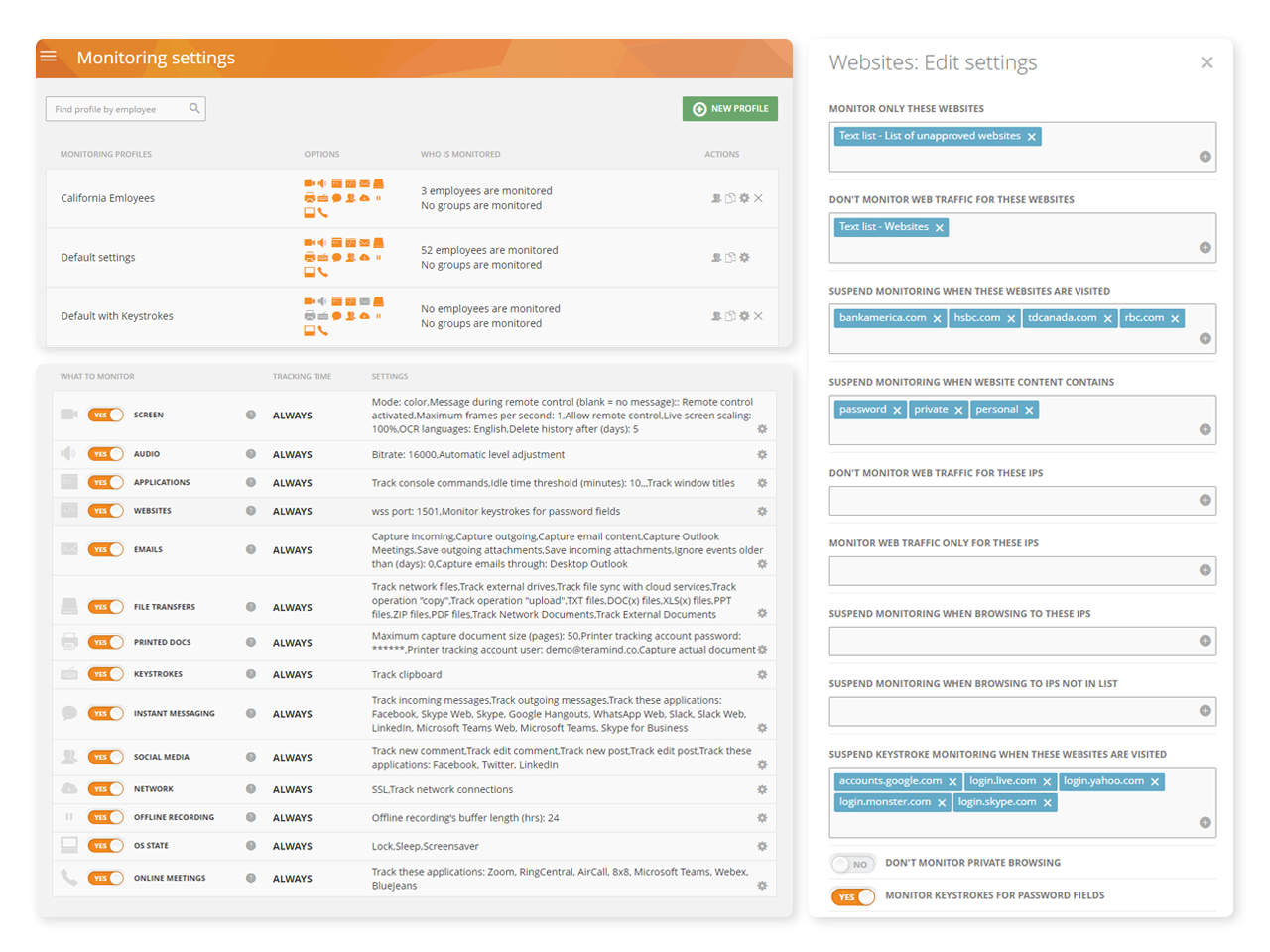
Configure rules and policies with consideration to what needs to be monitored and who has access to monitored data
Get instant administrative oversight that helps to satisfy privacy compliance requirements
Intelligent Policy & Rule Engine
The core of Teramind’s privileged access monitoring platform is its automation. Teramind comes with hundreds of pre-defined policies and rules
Block email containing sensitive keywords, stop uploads of sensitive files, detect screen captures and prohibit external drives
Templates cover almost every use-case for data loss prevention, insider threat detection and privileged-user security
Use pre-built compliance templates to enforce compliance, user privacy and privileged user monitoring
Easily load templates then customize them to fit your specific monitoring needs
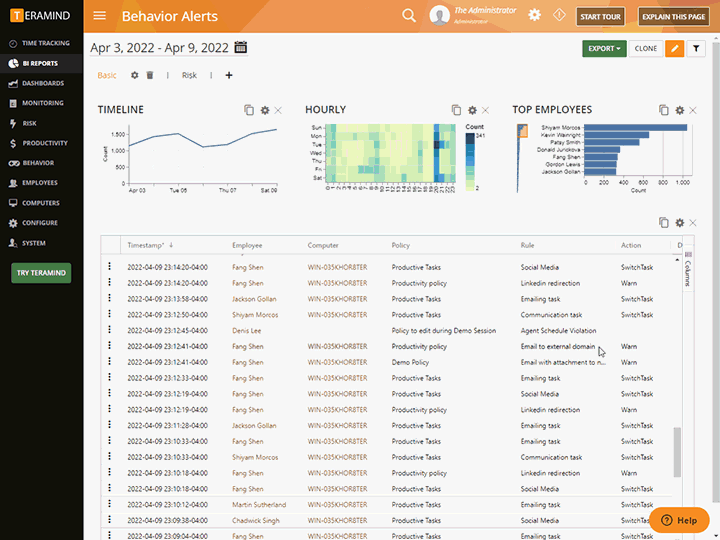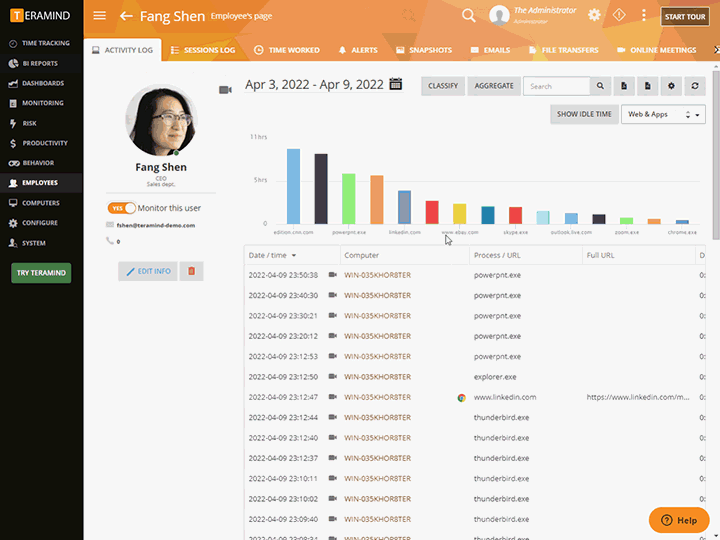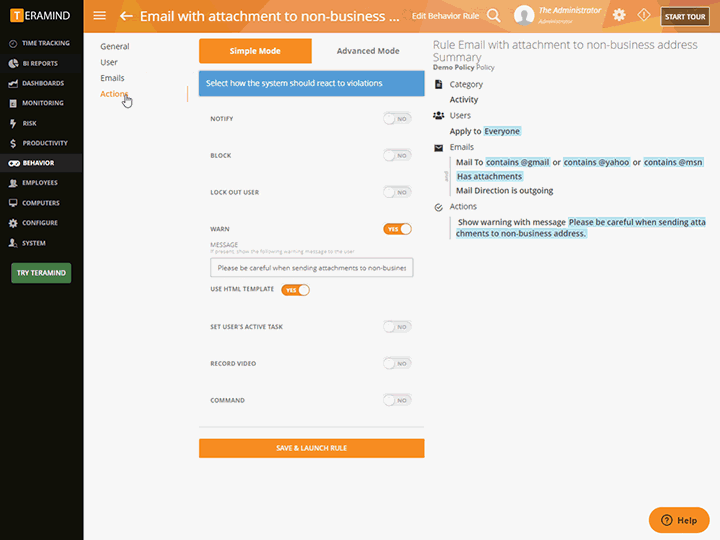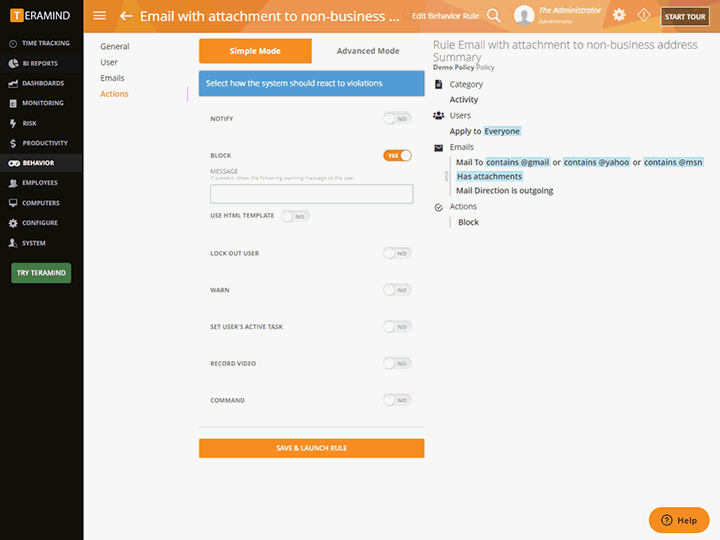
Real-Time Alerts and Notifications
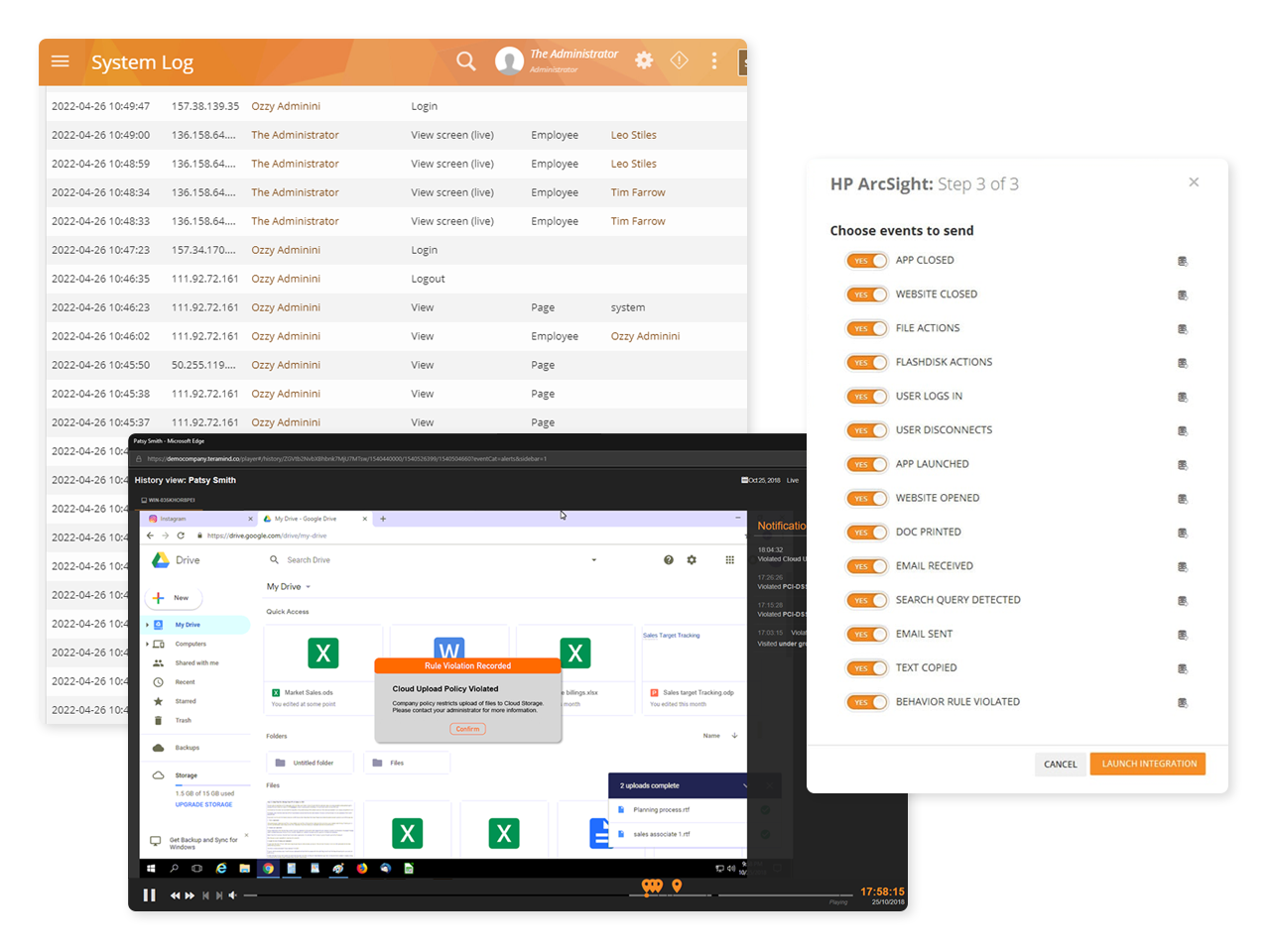
Real-time alerts from the privileged user access monitoring system show what rules were broken, when they were broken and what user was in violation
Get alerted to privileged user rule violations as soon as they happen with instant alerts
Receive alert and notification reports on what actions were taken and in what context
Send privileged users instant warnings when their risky and suspicious activities are detected
Set up a monitoring widget on the dashboard for real-time privileged user monitoring updates active users
Behavioral Anomaly Detection
Define what constitutes dangerous or harmful user behavior within privileged access monitoring then automatically detect it with Teramind anomaly detection
Define baselines then automatically detect when a user, department, or group deviates from their normal parameters
Leverage behavior anomaly detection to get alerts when acceptable risk levels are exceeded
Detect behavior anomalies in apps, emails, network use, file activities or printing
Stop malicious attempts by locking users out or taking remote control of the compromised system after an anomaly alert is received
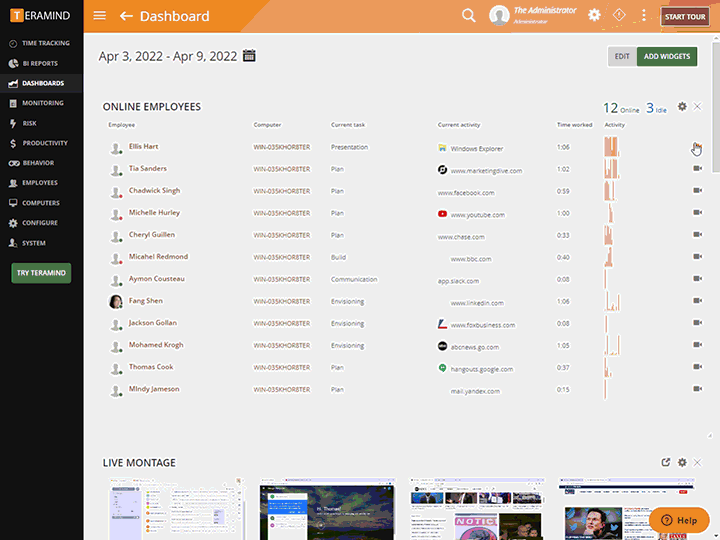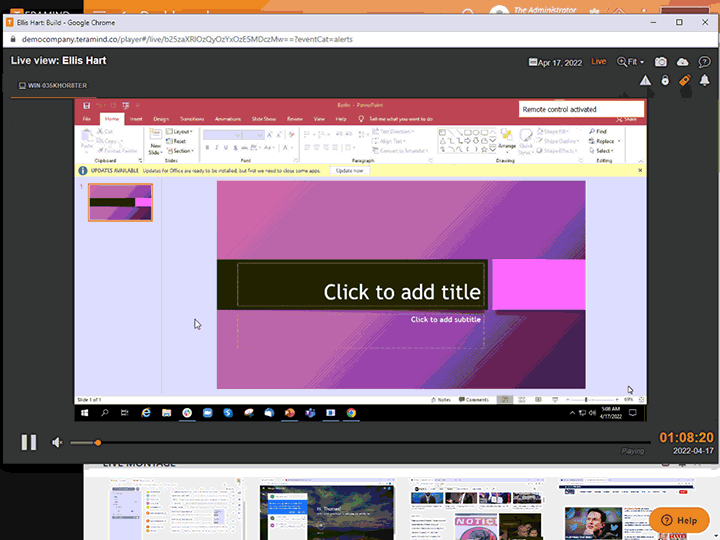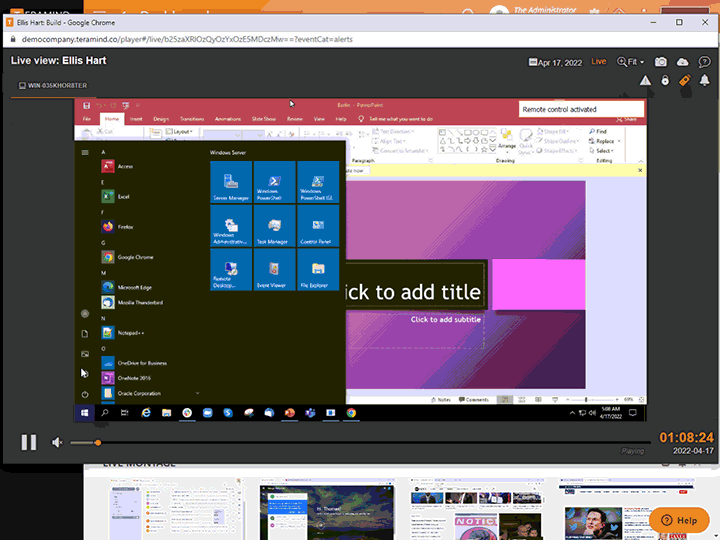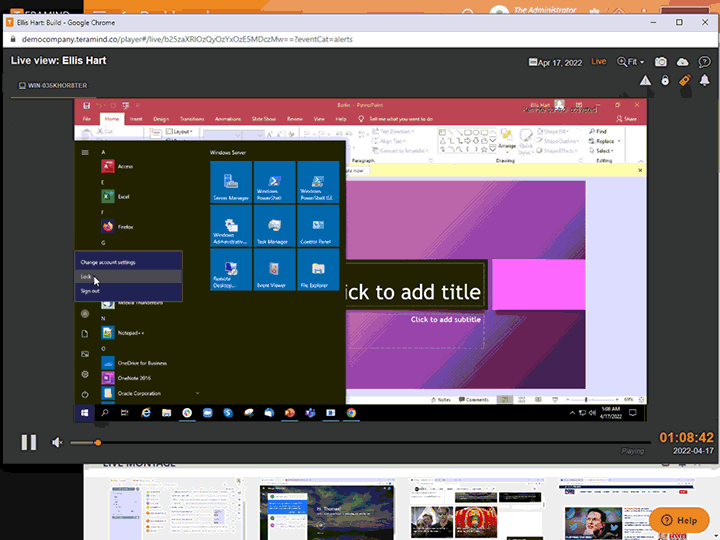
Remote Desktop Control
Teramind’s remote control feature gives you the ability to remove users, contain activity, and eliminate threats associated with privileged user accounts
Instantly take away a user’s ability to access a desktop with Teramind’s privileged access monitoring
Manually override an account and remove users or disable mouse and keyboard control so no further action can be taken
Access the remote control feature from any live session with a single click
Authentication and Access Control
Role Based Access Control (RBAC), authentication and segregated privileges prevent unauthorized access or sharing of confidential data
Set up account access for each privileged user that requires authorized clearance and easily track what each user is doing at any given time
Use group profiles to create different access levels based on departments, job function, or source of access (i.e. remoteor third-party)
See what information and system resources each group or department can access
Session Recording and Audit
Teramind visually records every action that a user makes while on a machine, allowing for both live viewing and past recordings. Extensive metadata and fast indexing from privileged user monitoring allow past incidents to be searched and retrieved in seconds.
Investigate user actions, rule violations and other incidents using session recordings
Export logs detailing privileged user sessions as PDF or CSV or import logs into monitoring and analytics systems like LogRhythm
Options to access audio through privileged user monitoring supports audio input/output monitoring
Activate audio support then download and export privileged user monitoring sessions with audio as MP4s
Risk Analysis and Mitigation
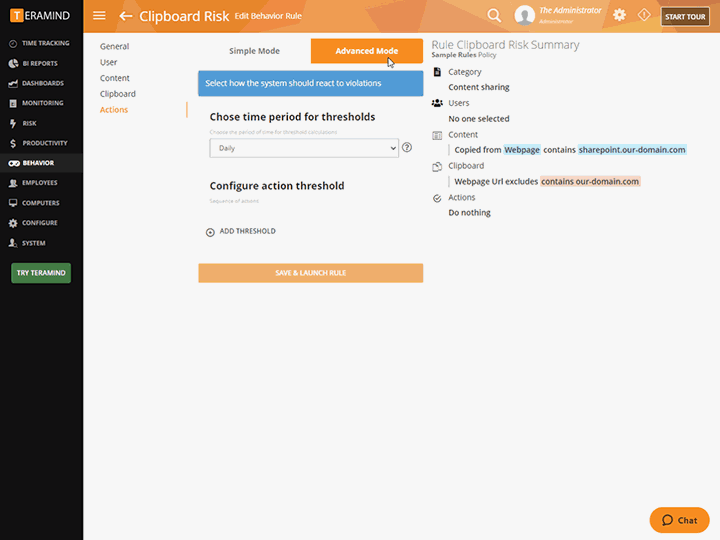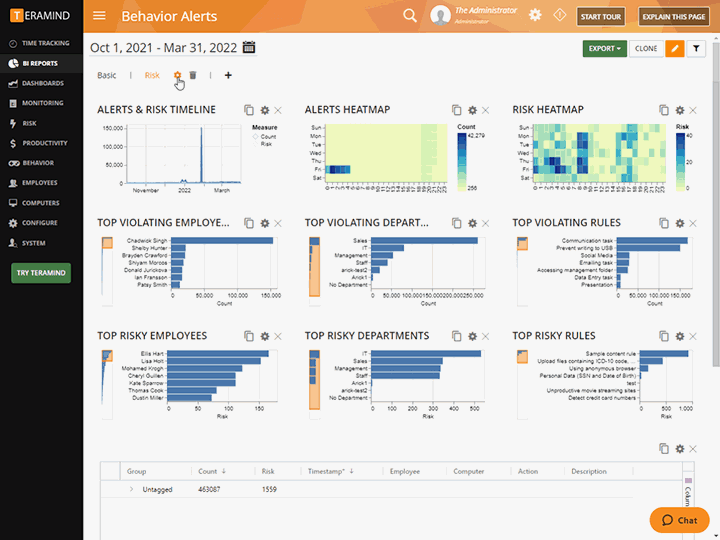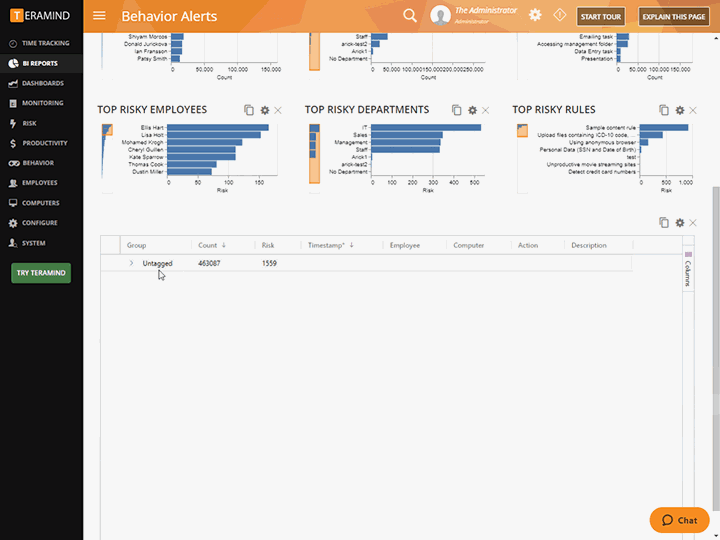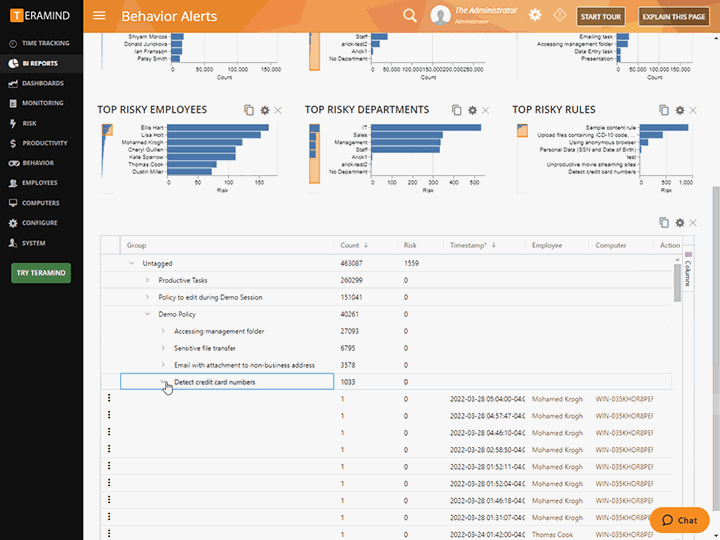
Use Teramind’s dedicate Risk Assessment dashboard to conduct organization-wide risk assessments and risk assessments of privileged users
Profile risk by user, team, department or across the entire organization or by content
Derive reports by severity of risks or by how many times security violations occurred
Unique Risk Scores within the privileged user monitoring system help you identify high-risk users or policies
Risk scores can be used to develop plans for treating risks
IAM/PAM/SIEM Integration
Teramind privileged user monitoring allows you to share reports and threat intelligence with your security team or other departments and easily integrate with SIEM and other analytics tools
Integrate Teramind into your project management system or SIEM directly from the dashboard
RESTful APIs can be easily utilized by access/identity management (IAM/PAM) applications to create a single-sign-on (SSO) policy or share logs
Support plug-and-play integrations include HP ArcSight, Splunk, IBM QRadar, McAfee, LogRhythm and more
The Features That Power Teramind
Monitor Privileged Users & Contractors with Teramind
Industry Statistics Show the Need for
Privileged User Activity Monitoring
Privileged users pose the biggest insider threat and security risk
According to crowd-based research, 60% of risk comes from internal users and 57% from consultants and contractors

Majority of enterprise breaches involve privileged accounts
A survey confirmed that 74% of enterprise breaches involved privileged accounts while 66% of companies were breached 5+ times

Hackers see privileged accounts as the best route to sensitive data
Almost one-third of respondents at the Black Hat 2021 said privileged accounts were the best choice to access critical data and 70% believe traditional security is obsolete.




Most businesses expect the risk of privileged user abuse to increase
One survey found that 70% of respondents believe privileged users access data for no discernible business need, 61% believe privilege access is misused, while 55% think it’s only going to get worse.




Protect Your Sensitive Data with Privileged Access Monitoring
Learn more about privilege user monitoring and Teramind
Threats associated with privileged user accounts are one of the biggest threats facing businesses today. Stolen or hacked privileged accounts are also the number one choice for many external criminals looking to gain access to otherwise ‘secure’ systems.
The complexity and constantly changing world of IT has made privileged access monitoring a necessity for every business. Threats associated with privileged user accounts are becoming more complex every day.
Teramind’s real-time privileged user monitoring and data loss prevention solutions help you monitor privileged users to automatically detect anomalous behavior and suspicious activity.
Suspicious behavior can signal a compromised or malicious privileged user. For example: creation of back-door accounts, transmission of sensitive data outside the company, etc.
Teramind’s Intelligent Policy & Rules Engine then automatically enforces data protection and access control rules. The rules prevent compromised users from data exfiltration, IP theft, fraud, industrial espionage, sabotage, and other malicious attempts.
With Teramind Privileged User Monitoring, you can conduct threat analysis, forensic investigation, and security auditing. The privileged user access monitoring tools also have complete session recording, metadata analysis, and immutable logging features.
Finally, extend your privileged user security coverage with built-in integration. Security information, event management (SIEM), and threat analytics systems are all included in privileged access monitoring.
> Identify and track all privileged users, including system administrators, DBAs, network engineers, system architects, developers, IT auditors, remote users, third-party vendors, etc
> Implement a ‘zero-trust’ data loss prevention (DLP) strategy utilizing activity, system-access, schedule, and content-based rules
> Create monitoring and access profiles based on a user’s role, separation of duties, existing Active Directory Group Policy, or on a need-to-know basis
> Audit privileged sessions with immutable logs, session recording and real-time alerts, and notifications to detect credential sharing and other abuse of root accounts.
Flexible Deployment
Deploy Teramind in a way that works for your organization


Cloud
Get up and running in minutes with Teramind cloud deployment. Automatic updates with no licenses or hardware
We bring businesses peace of mind through our award-winning insider threat prevention solution
Ready to get started?
Improve productivity and data security with the
global leader in behavior analytics.