Intelligent Compliance Management
Stay on top of your compliance management with an automated system that accounts for the human element and keeps your organization in line with regulations
Ensure regulation compliance across the entire organization
with intelligent behavior analysis
For enterprises down to SMBs, organizations need compliance management solutions that account for the biggest variable in compliance- the human element.
Teramind’s compliance management solution ensures compliance in user behavior-based activities across multiple regulatory bodies including GDPR, HIPAA, PCI DSS and more.
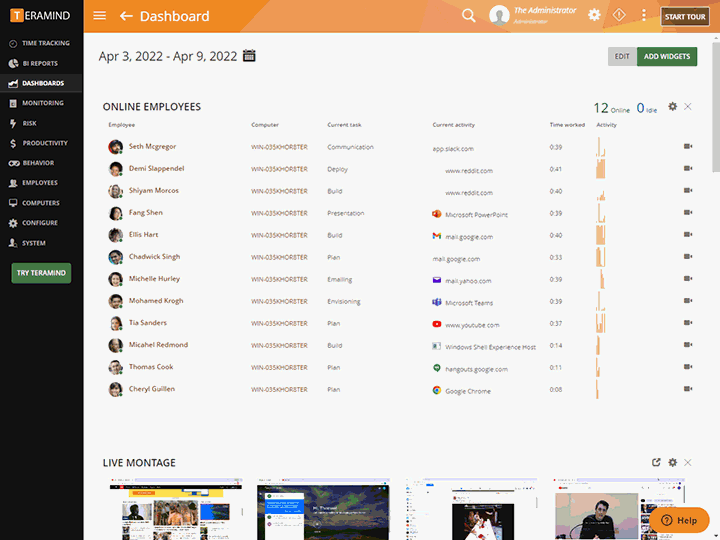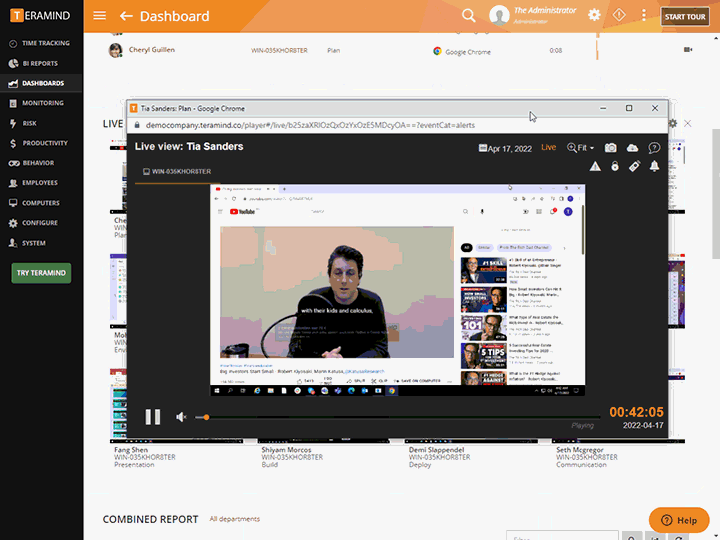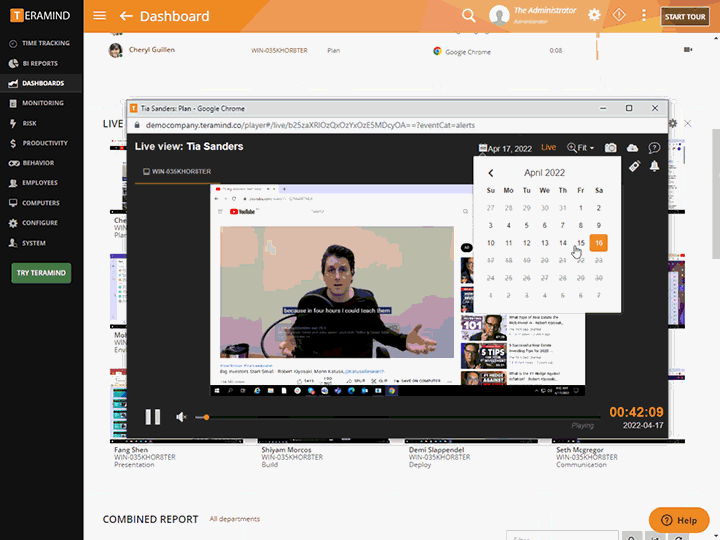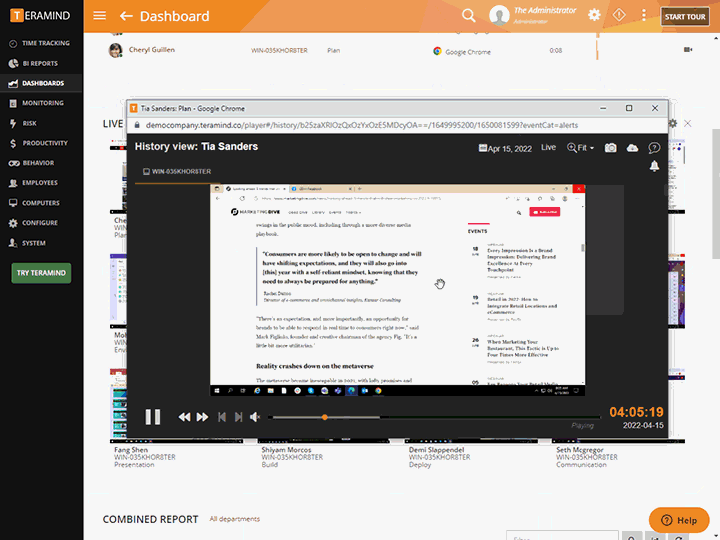
Monitor activities in real-time to ensure compliance & policy enforcement
Teramind’s automated compliance management system ensures employee and user activity conforms with industry regulations in real-time
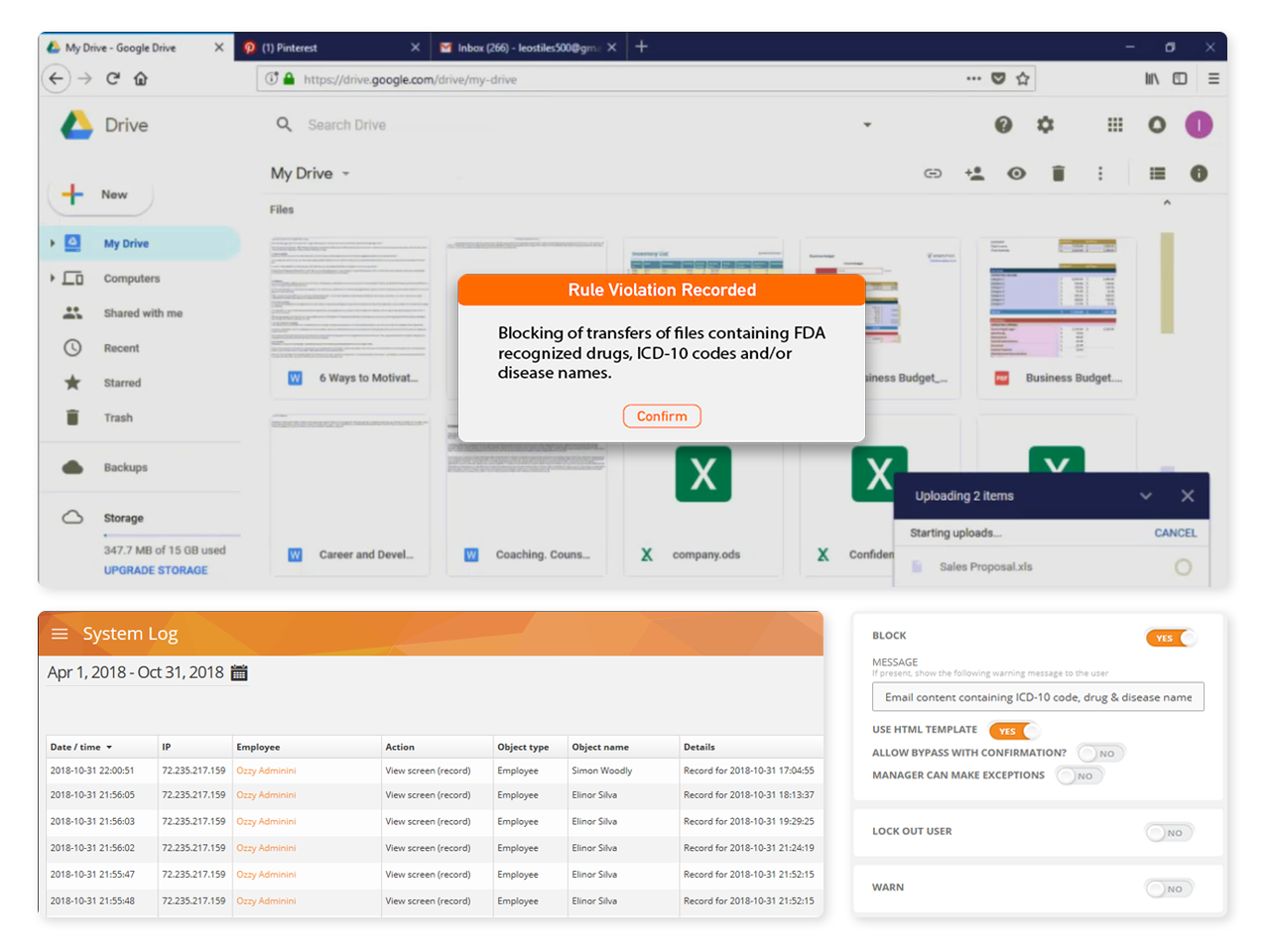
Prohibit noncompliant activity with automated actions that detect and prevent data mishandling on the system
Manage the human element of compliance risk with behavior analytics that identify anomalous activities
Automatically detect unprotected sensitive data with prebuilt rules pertaining to PII, PFI, PHI and PCI
Track data access and data usage to satisfy purpose and access limitations
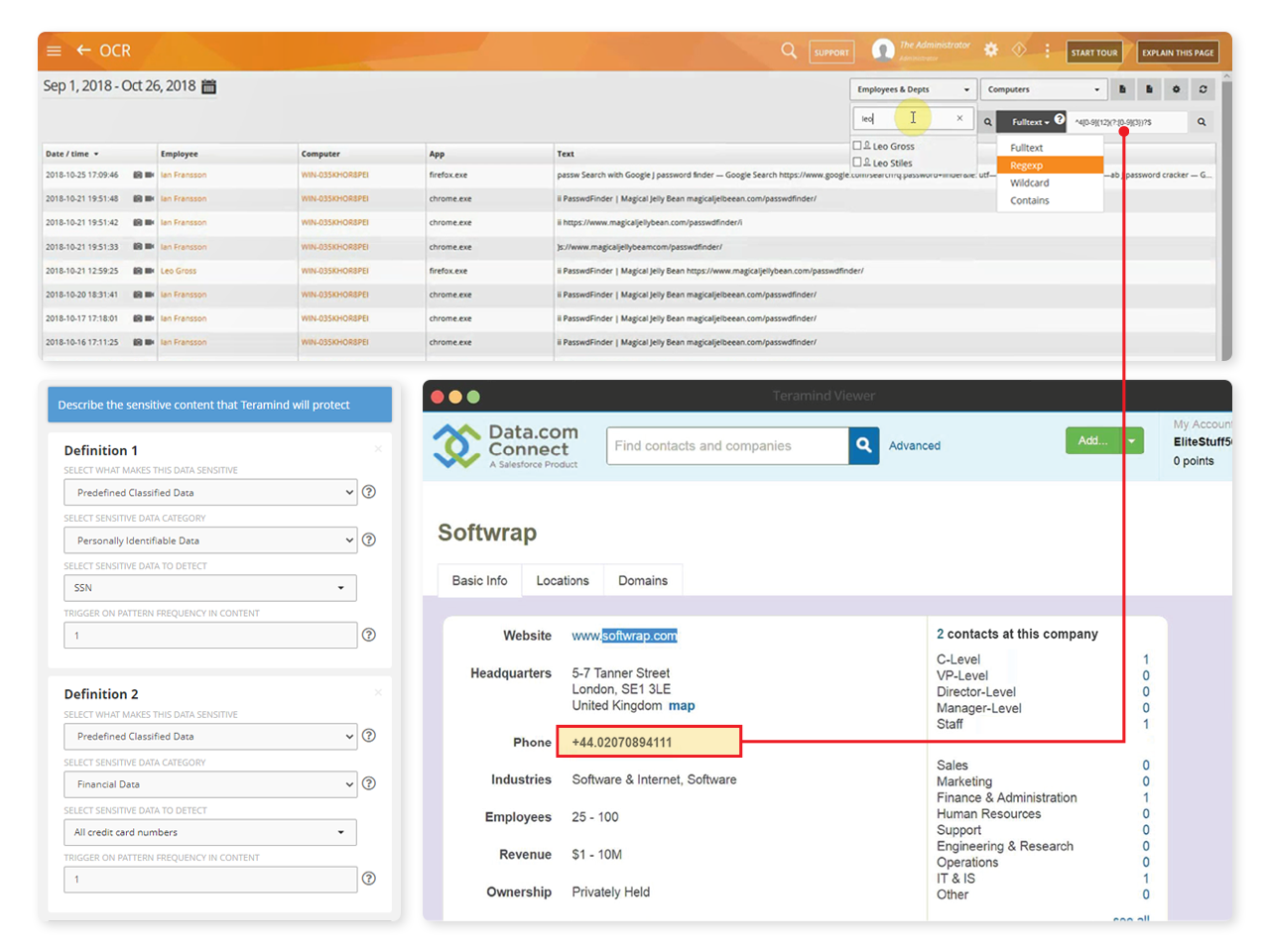
Protect personal and sensitive data however it appears on screen
Teramind’s compliance management solution detects and blocks noncompliant uses of personal and sensitive data in structured and unstructured formats
Automatically discover sensitive content in images and videos using OCR search of session recordings
Get alerts whenever data misuse is detected in unstructured data with OCR-based rule features
Guarantee compliant use of PII, PFI, PCI, PHI with prebuilt template rules for sensitive data
Automatically detect activity containing PHI like DNA profiles, health ID numbers & ICD10 codes
Maintain PCI DSS compliance requirements with prebuilt template rules that focus credit card data
Get detailed reporting that satisfies compliance audits and breach requirements
Teramind’s in-depth report, logs and session recordings prepare organizations for compliance audits and risk management certifications
Prepare for audits with reports outlining security events with immutable logs, session recordings and risk reports
Enrich cybersecurity assessments and policy development
Develop organization-tailored employee training programs using the Risk Assessment dashboard
Collect irrefutable evidence of data & security maintenance for compliance requirements like burden of proof
The Features That Power Teramind
We bring businesses peace of mind through our award-winning compliance management solution
The Experience
Speaks For Itself
Discover Compliance Management
Compliance management is the process of ensuring the systems, employees and processes within an organization are in-line with any applicable industry laws, regulations and requirements and any governing body overseeing an organization or its employees, like a corporate head office or even a labor union.
Compliance varies depending on the industry an organization is operating in and therefore compliance management in each industry varies as well. For instance, highly regulated industries like finance and healthcare that deal with sensitive personal data are held to stricter compliance standards and regulations than other industries. The endpoint monitoring compliance management solution Teramind assists organizations in maintaining these types of data compliance regulations.
A compliance management system, or CMS, is an integrated system of tools and processes that simplify complying with regulation requirements and compliance standards. These systems don’t just help organization’s avoid the hefty penalties and fines associated with failure to comply with standards and regulations, they also minimize risk to the organization’s customers and clients and therefore work to protect an organization’s reputation.
Using a CMS allows organizations to understand their compliance status and implement procedures that allows them to better maintain their compliance practices.
One example of a compliance management system is Teramind’s endpoint monitoring compliance solution.
Compliance risk management is the process of assessing, evaluating and identifying potential compliance vulnerabilities within an organization.
Assessments to determine compliance risk include looking over the processes, systems and internal controls of an organization that were put into place to maintain and manage their compliance to applicable regulations. One aspect of compliance risk management that is often overlooked is the human element of compliance; a single misstep by a single employee could result in millions of dollars worth of penalties.
The compliance management solution built into Teramind directly addresses the human element of compliance risk. By monitoring all user activity and providing reports, logs and session recordings outlining that activity, organizations implementing Teramind as a compliance management solution are able to complete a full assessment of all compliance risk types in order to address any vulnerabilities that exist in their compliance plan.
Ready to get started?
Improve your security, productivity and compliance management
with the global leader in behavior analytics.