Keystroke Logging Software for Workforce Analytics & Security
Our keystroke logging software transforms keyboard activity into actionable insights for security, compliance, employee productivity, and operational efficiency.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce efficiency.







Why Choose Teramind for Employee Keystroke Monitoring
Complete Visibility Into Employee Computer Activity
Our keystroke logging software provides comprehensive monitoring across any operating system. Track keystrokes alongside screen recordings, application usage, and web activity to understand exactly how work gets done across your organization – all while respecting employee privacy.
Protect Sensitive Data with Detailed Audit Trails
Monitor and document access to confidential information, financial data, other sensitive data, and critical computer systems. Create forensic-quality keystroke data records showing who accessed sensitive information and what actions they took.
Transform Keystroke Data Into Business Intelligence
Convert logged keystrokes into actionable insights about employee productivity, workflow efficiency, and security compliance. Our keylogger software helps identify training needs, optimize processes, and improve overall performance.
Core Teramind Features for Employee Keystroke Monitoring
Our keystroke software provides enterprise-grade monitoring capabilities designed for professional workplace analytics and security.
Comprehensive Keystroke Logger Technology
Deploy advanced keylogging software across your organization:
Track keystrokes in all computer programs and applications
Monitor web forms, instant messages, and browser extensions activity
Capture keystrokes from any computer keyboard with full context
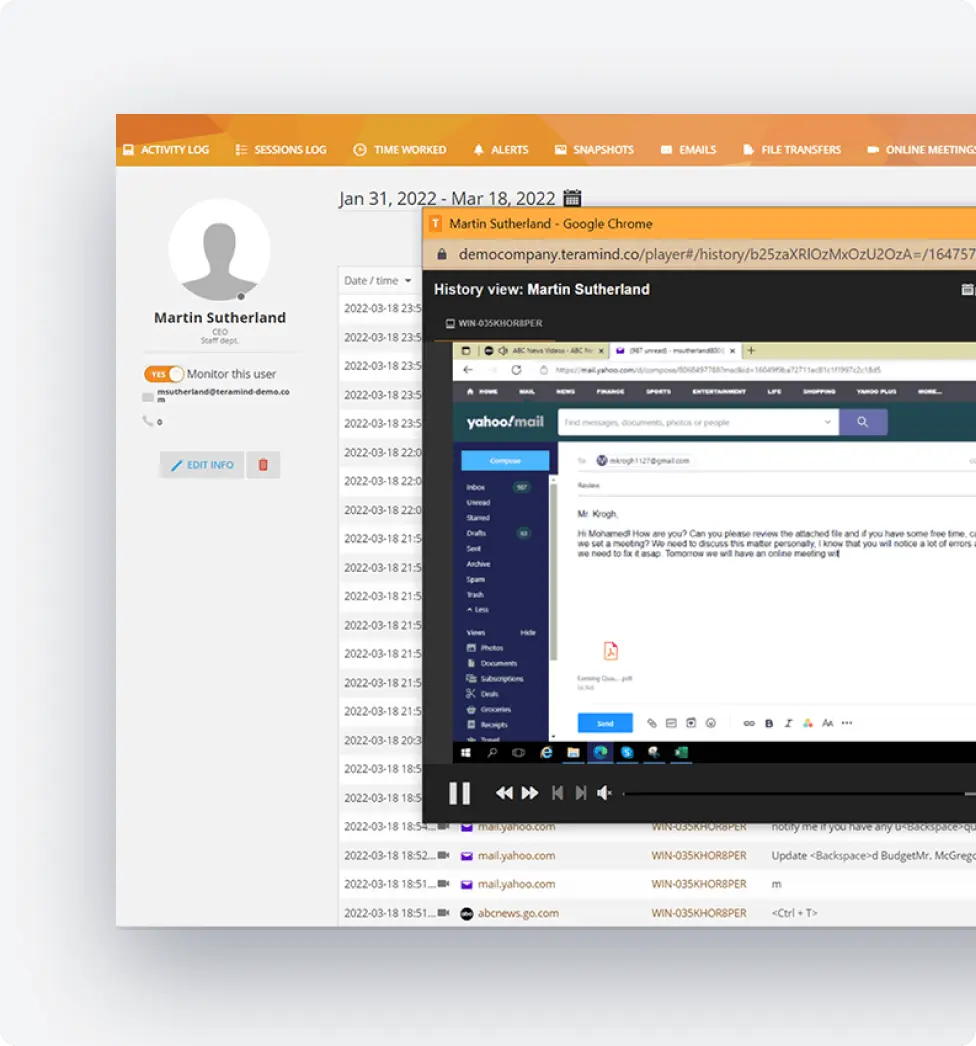
Privacy Controls and Configuration
Implement keystroke monitoring with appropriate safeguards:
Configure based keyloggers permissions by department or role
Set monitoring schedules for work hours only
Exclude personal devices from monitoring scope
Control access to keylogger activity logs
Maintain transparency about keystroke data collection
Security and Data Protection Monitoring
Use keystroke logging to protect sensitive data:
Monitor access to financial data and prevent unauthorized purchases
Track handling of sensitive information across all applications
Document employee activities with confidential information
Create detailed keylogger records for compliance requirements
Identify attempts to gain unauthorized access to restricted systems
Employee Productivity Analysis
Transform keystroke monitoring into productivity insights:
Measure employee productivity through typing patterns and activity levels
Analyze time spent in productive versus unproductive applications
Track workflow patterns across different computer programs
Generate reports combining keystroke data with other metrics
Troubleshoot technical problems through activity reconstruction
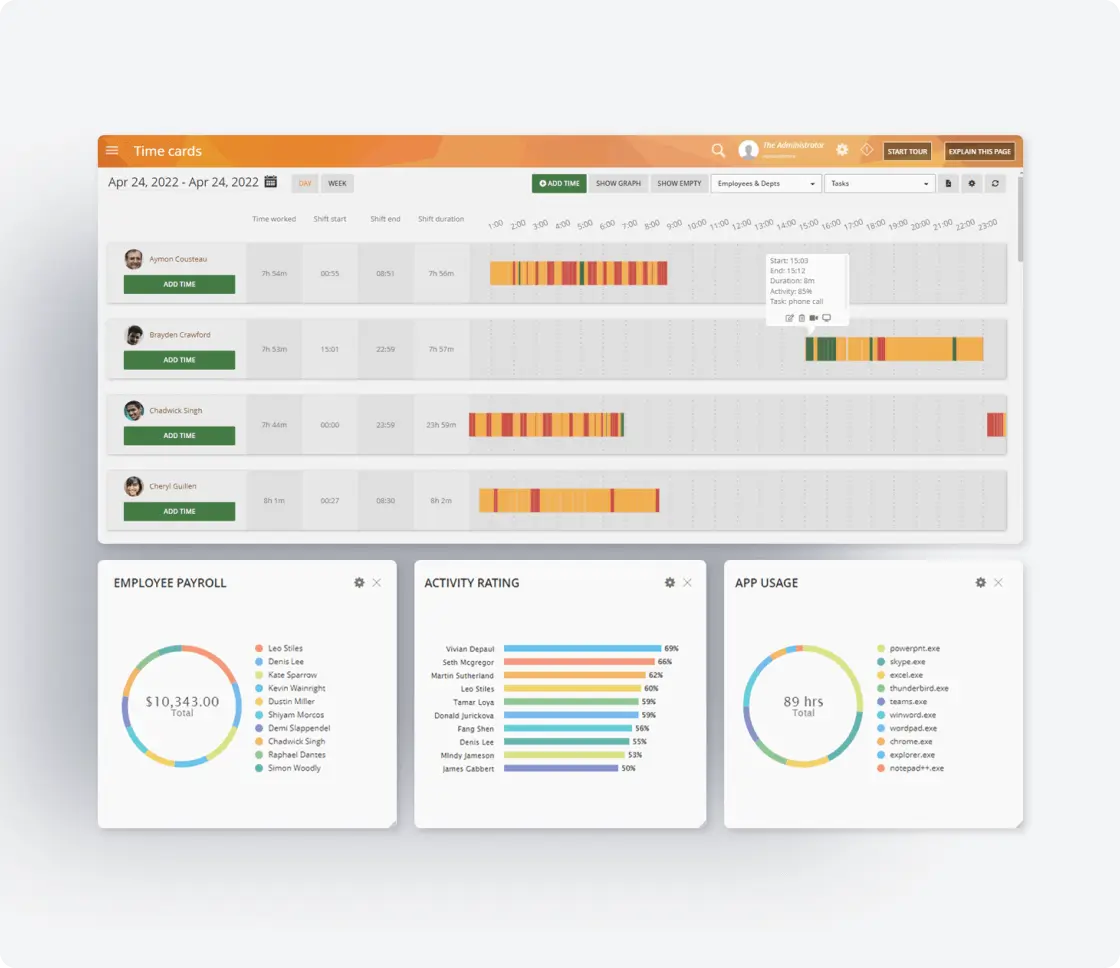
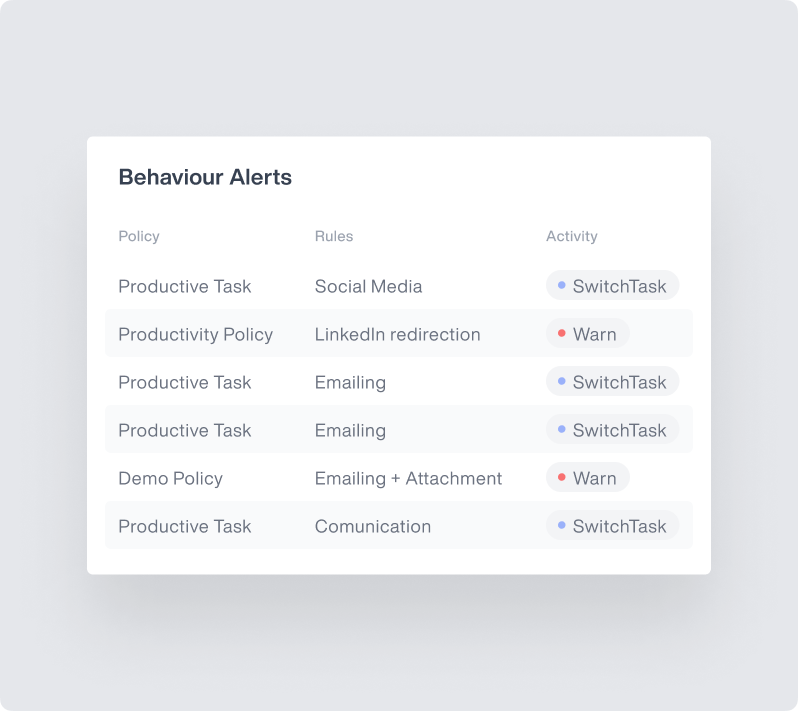
Real-Time Monitoring and Alerts
Proactive protection with intelligent alerts:
Set alerts for specific keywords or sensitive data access
Monitor instant messages and communications for compliance
Track unusual activity patterns in real-time
Receive notifications for policy violations or security events
Generate automatic alerts for suspicious behavior patterns
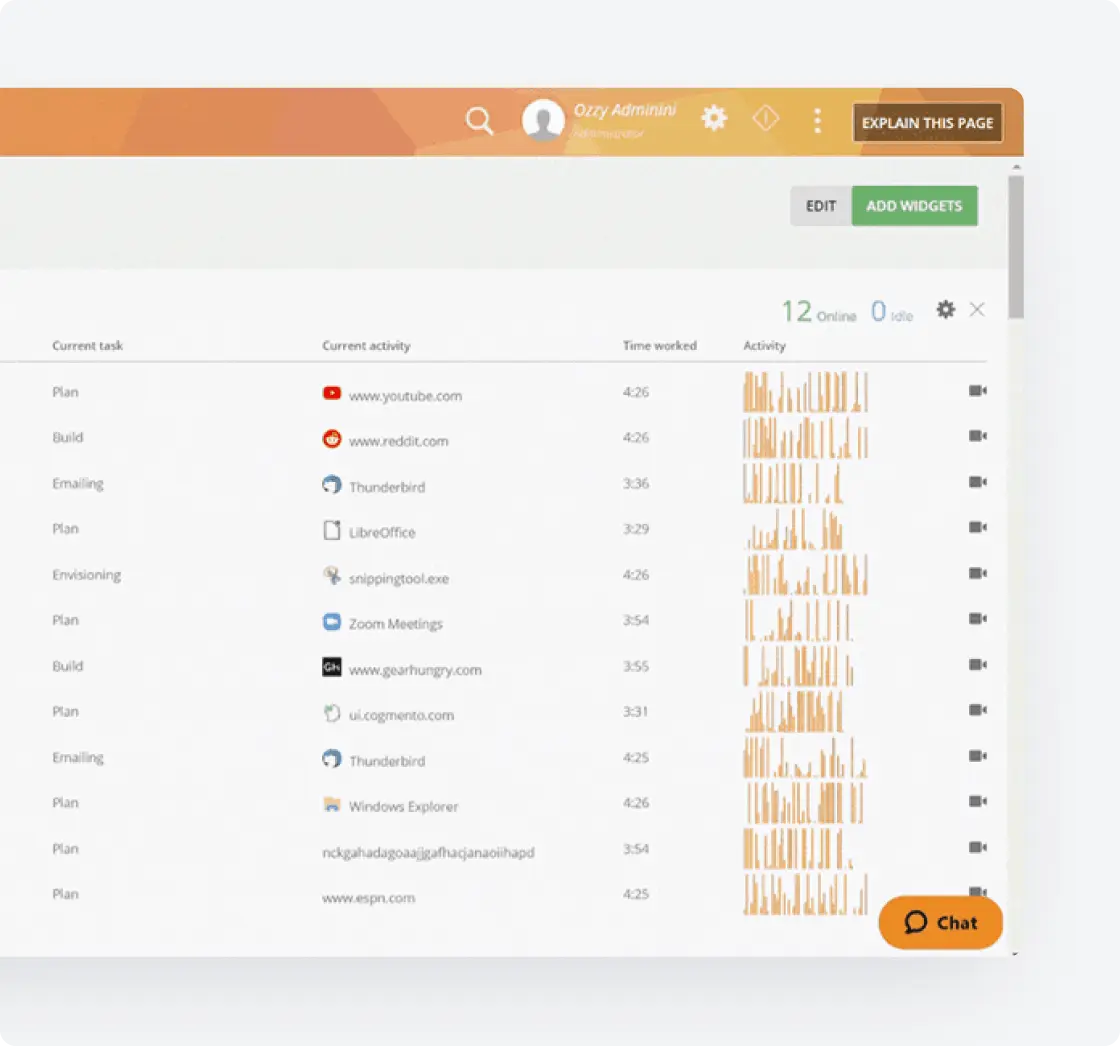
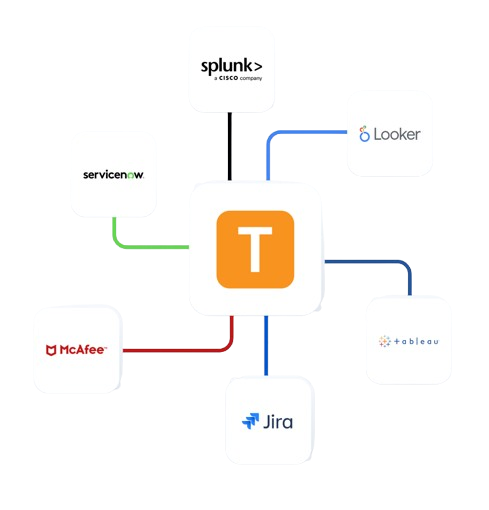
Enterprise Integrations
Integrate Teramind with your existing infrastructure to enhance monitoring.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
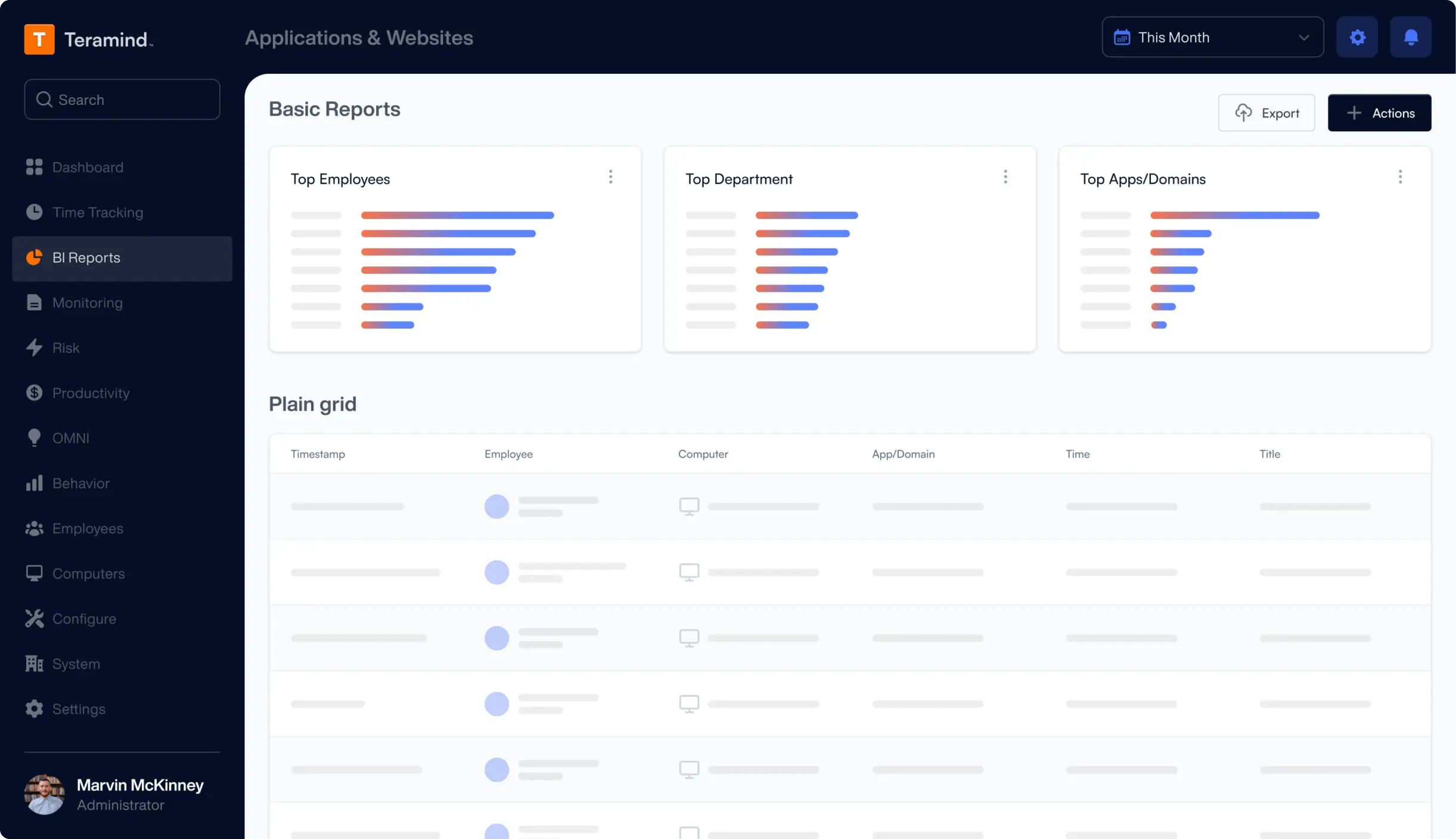
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What types of keyloggers are best for employee monitoring?
Software based keyloggers are ideal for employee monitoring because they provide comprehensive keystroke data while being easy to deploy and manage across the operating system. All types of keyloggers, whether hardware or software, operate at the computer system level, so understanding the system architecture is crucial for effective monitoring and implementing security measures. Unlike hardware based keyloggers that require physical access to each computer, software keyloggers can be centrally managed and configured. API keyloggers offer additional flexibility by capturing data at the application level, providing context about which programs employees use while typing.
How does keystroke logging software improve workplace security?
Keystroke logger software creates detailed audit trails showing exactly how employees interact with sensitive information, financial data, and critical systems. By monitoring keystrokes, organizations can detect unauthorized access attempts, document compliance with security policies, and investigate incidents. The software tracks login credentials usage, monitors data entry into web forms, and captures passwords entered into business applications, providing comprehensive security oversight.
What employee productivity insights can keystroke monitoring provide?
Keylogging software reveals detailed patterns about how employees work, including typing speed, active versus idle time, and time spent in different applications. By analyzing logged keystrokes alongside other metrics, managers can identify workflow inefficiencies, training needs, and best practices. Keystroke data helps measure actual productive output rather than just time spent at the computer, providing objective metrics for performance evaluation.
How should organizations implement employee keystroke monitoring?
Professional keystroke logging requires clear policies about what keystroke data is collected and how it’s used. Organizations should configure their keylogger software to monitor only work-related activities on company computer systems during business hours. The keylogging programs should be installed transparently, with employees aware of monitoring policies. Regular reviews of keylogger records ensure the system is used appropriately while maintaining employee trust and meeting compliance requirements.
It is also crucial to secure keystroke logs to prevent unauthorized access or data breaches, as these logs can contain sensitive information that may be targeted by cybercriminals.
Request Your
Custom Demo Now