Secure Your Business from
Third-Party Threats
Teramind’s powerful third party risk management (TPRM) software provides monitoring and control over external vendors accessing your critical systems and data.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce efficiency.







Why Choose Teramind for
Third Party Risk Management
Complete Visibility Across Your Extended Enterprise
Gain full visibility into all activities performed by third party vendors with detailed session recordings, live views, and historical playback features.
Proactive Risk Mitigation and Remediation
Identify potential threats before they become security incidents with behavior alerts and block malicious actions in real-time.
Customizable Access Controls and Compliance
Meet regulatory compliance requirements while protecting sensitive data with custom access profiles and detailed audit trails for all third party relationships.
Core Teramind Features for TPRM
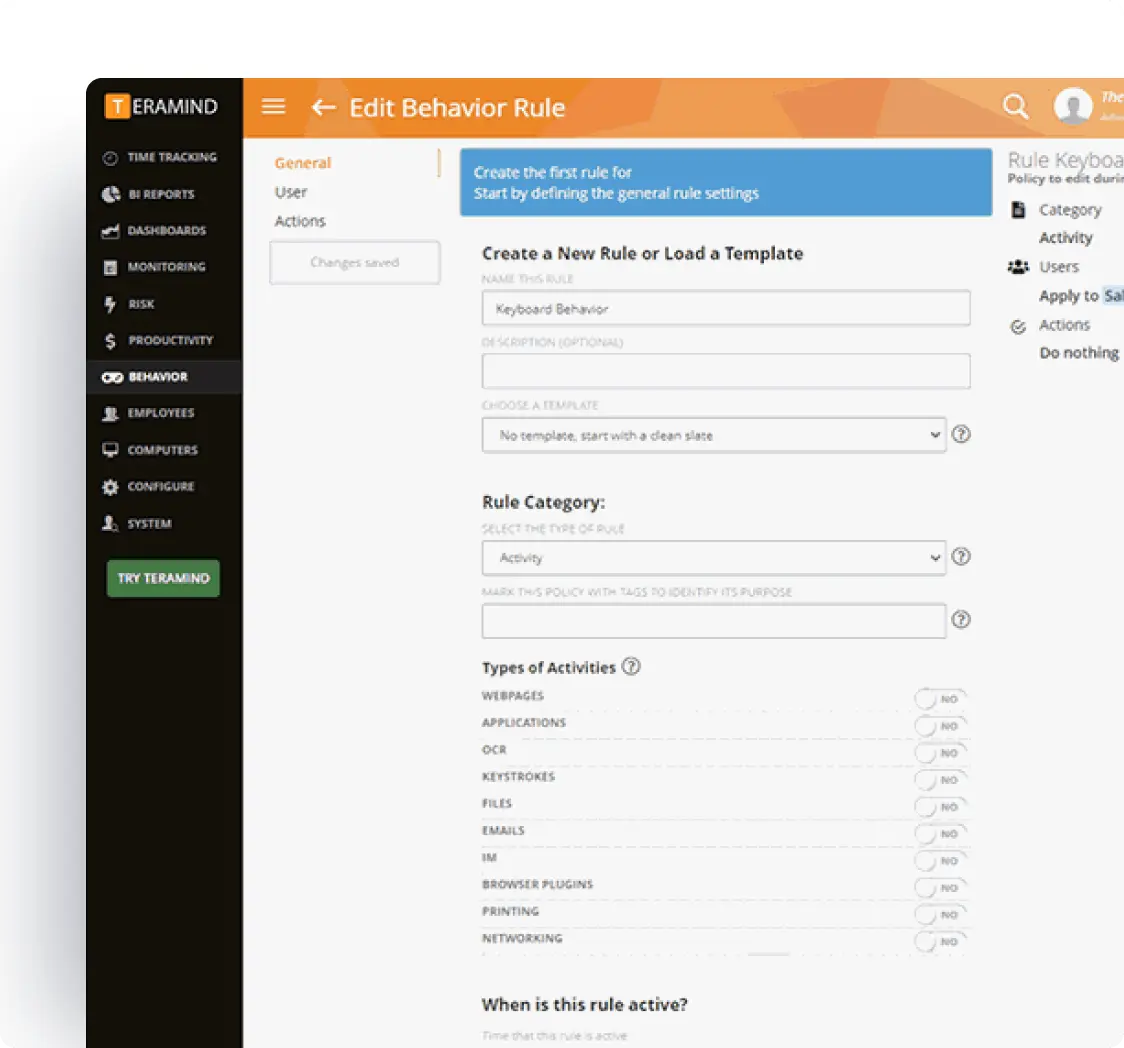
Customizable Monitoring: Hidden or Revealed Agent
Choose the monitoring approach that fits your organization’s needs and transparency requirements.
Hidden Agent: Operates silently in the background, monitoring users without visible indicators
Revealed Agent: Provides a user interface that allows third parties to know they’re being monitored
Easily switch between modes as your relationship with vendors evolves
Configure each agent with specific monitoring parameters based on vendor risk levels
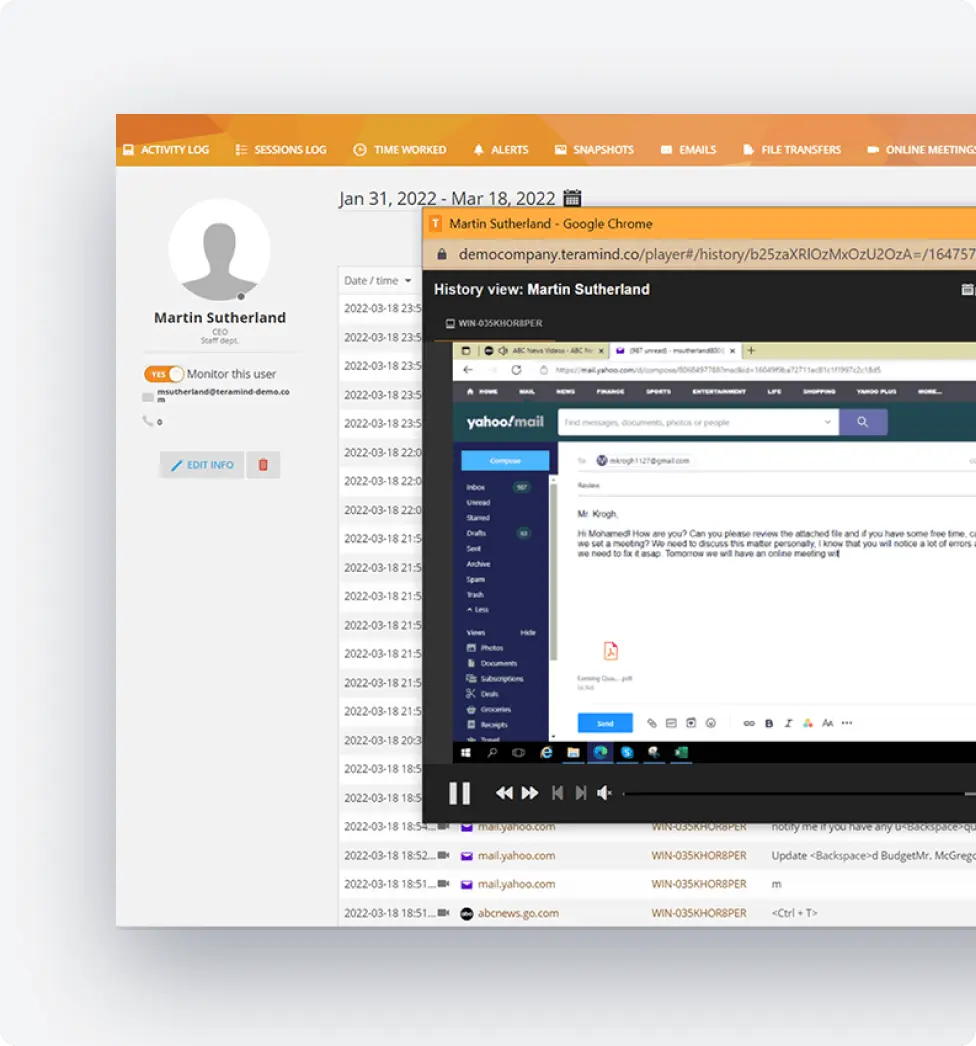
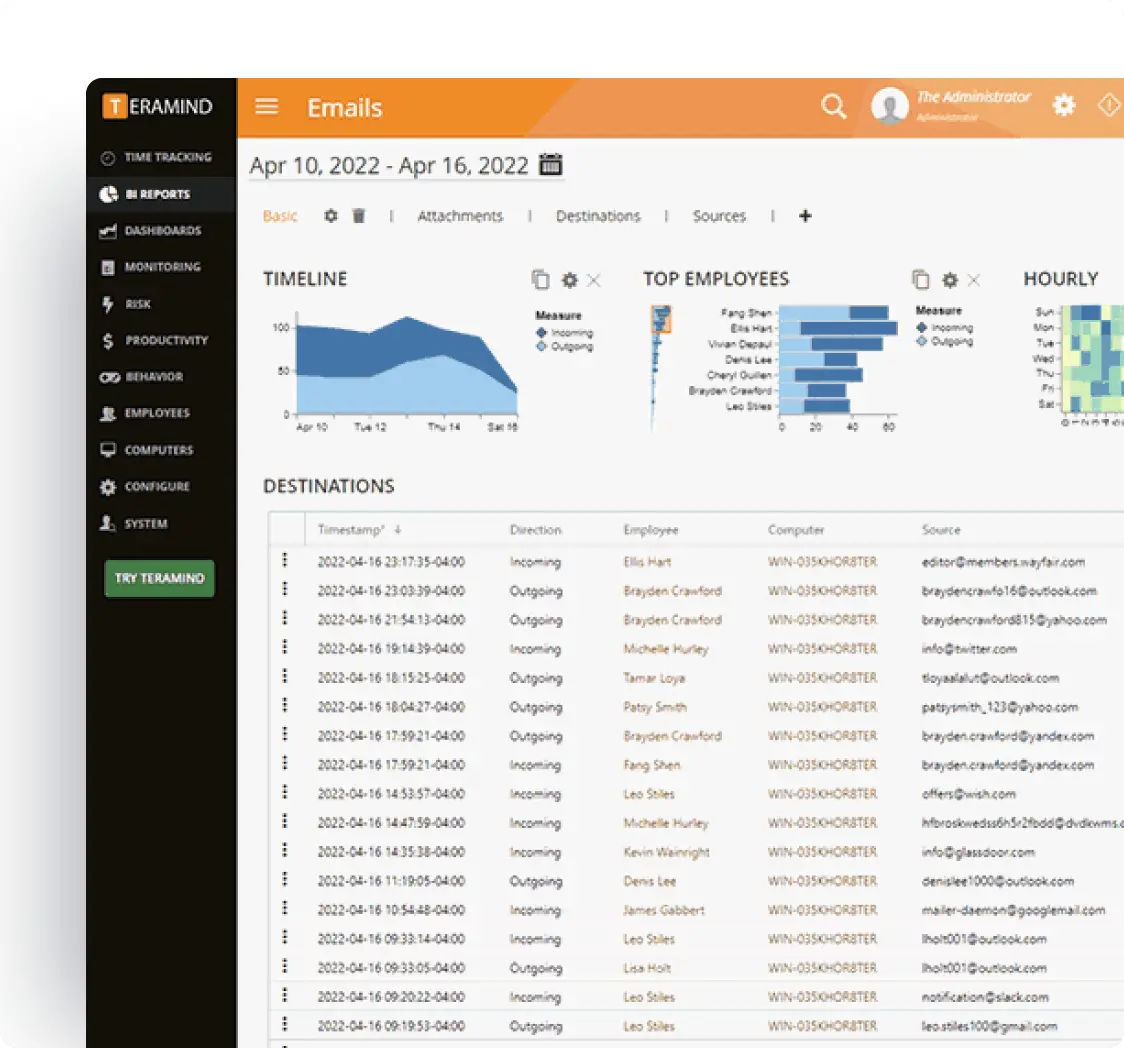
Insightful Activity Tracking
Gain complete visibility into what contractors and vendors are doing within your systems.
Monitor all applications, websites, emails, file transfers, and network activities
Maintain detailed audit trails for compliance and forensic purposes
Track time spent on specific tasks to validate vendor billing
Create custom rules to flag unusual or unauthorized behaviors
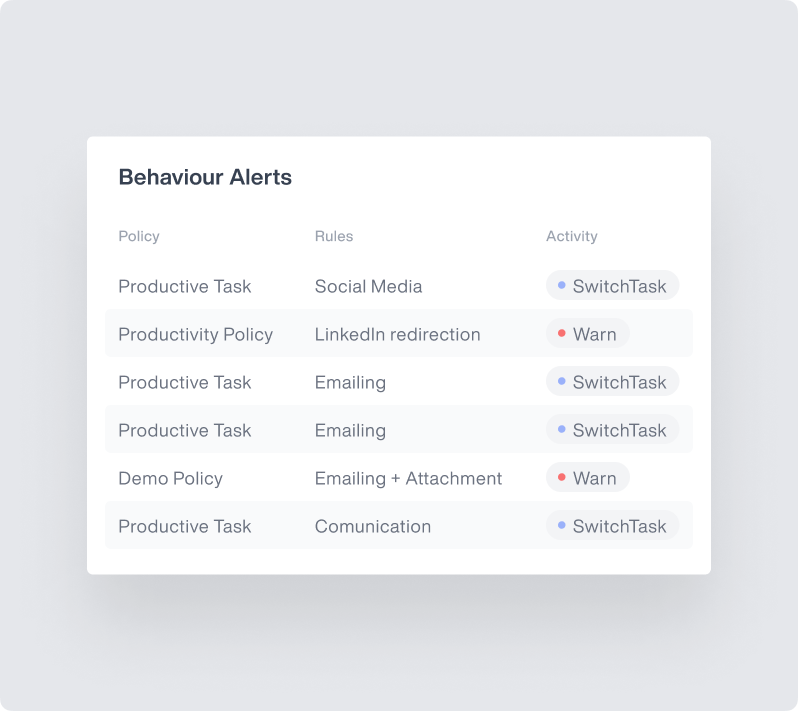
Real-Time Risk Alerts
and Dashboards
Access a dedicated risk dashboard to continuously assess and manage third party risk.
View risk assessments at-a-glance with intuitive visualization tools
Monitor risk metrics across your entire third-party ecosystem
Receive alerts about potential security issues as they emerge
Track trends over time to identify recurring problems
Secure Terminal
Server Access
Protect your internal networks while enabling controlled third-party access.
Create virtual servers on Windows or VMware Horizon for secure third-party access
Keep vendors isolated from internal networks using RDP for sign-in
Record all activities performed while signed into terminal servers
Maintain complete control with immediate lock-out capabilities when needed
Remote Control
and Intervention
Take immediate action when suspicious third-party activities are detected.
Remotely view and control sessions to address security concerns
Disable keyboard and mouse control to prevent unauthorized actions
Remove users instantly when necessary to protect sensitive information
Provide remote support to legitimate vendors experiencing difficulties
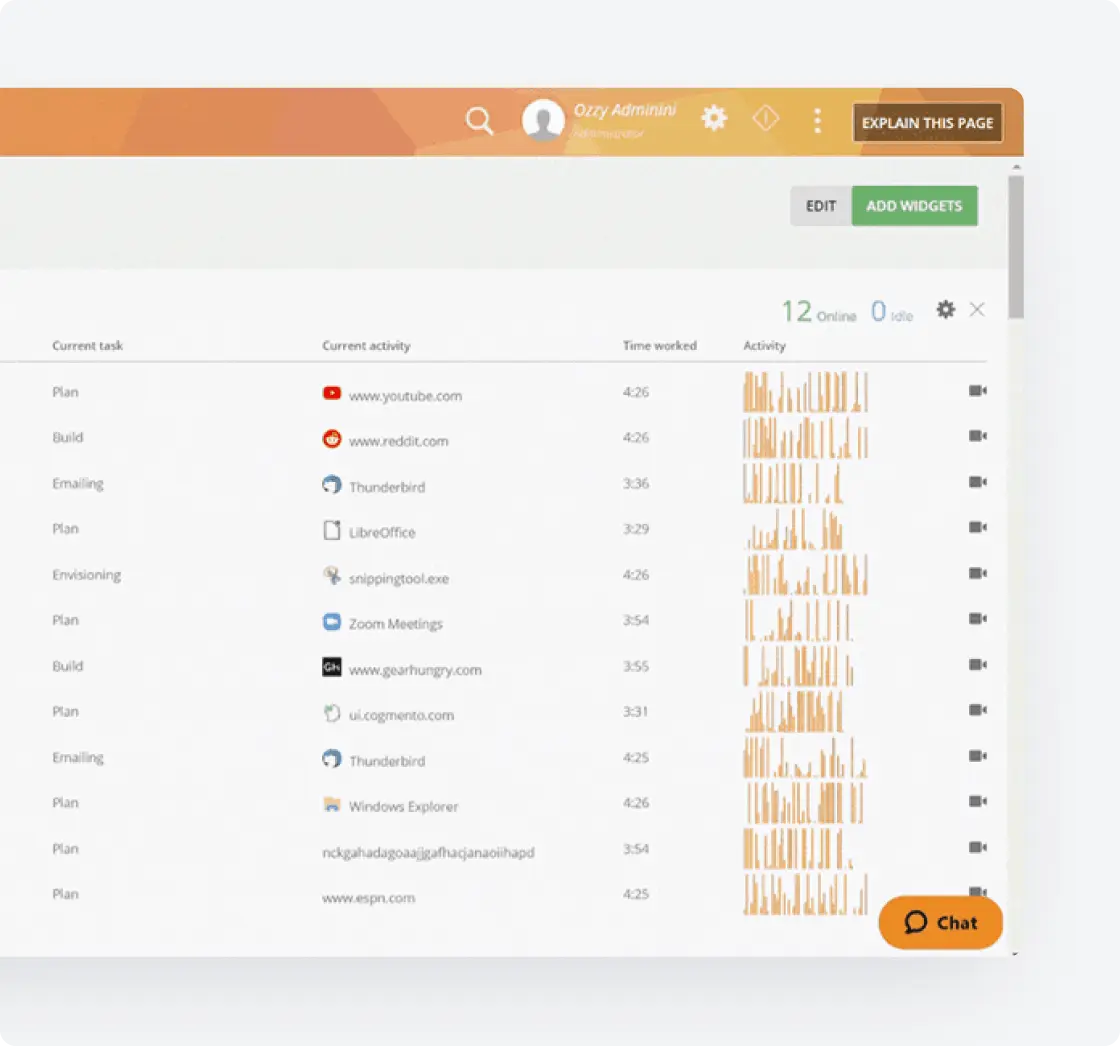
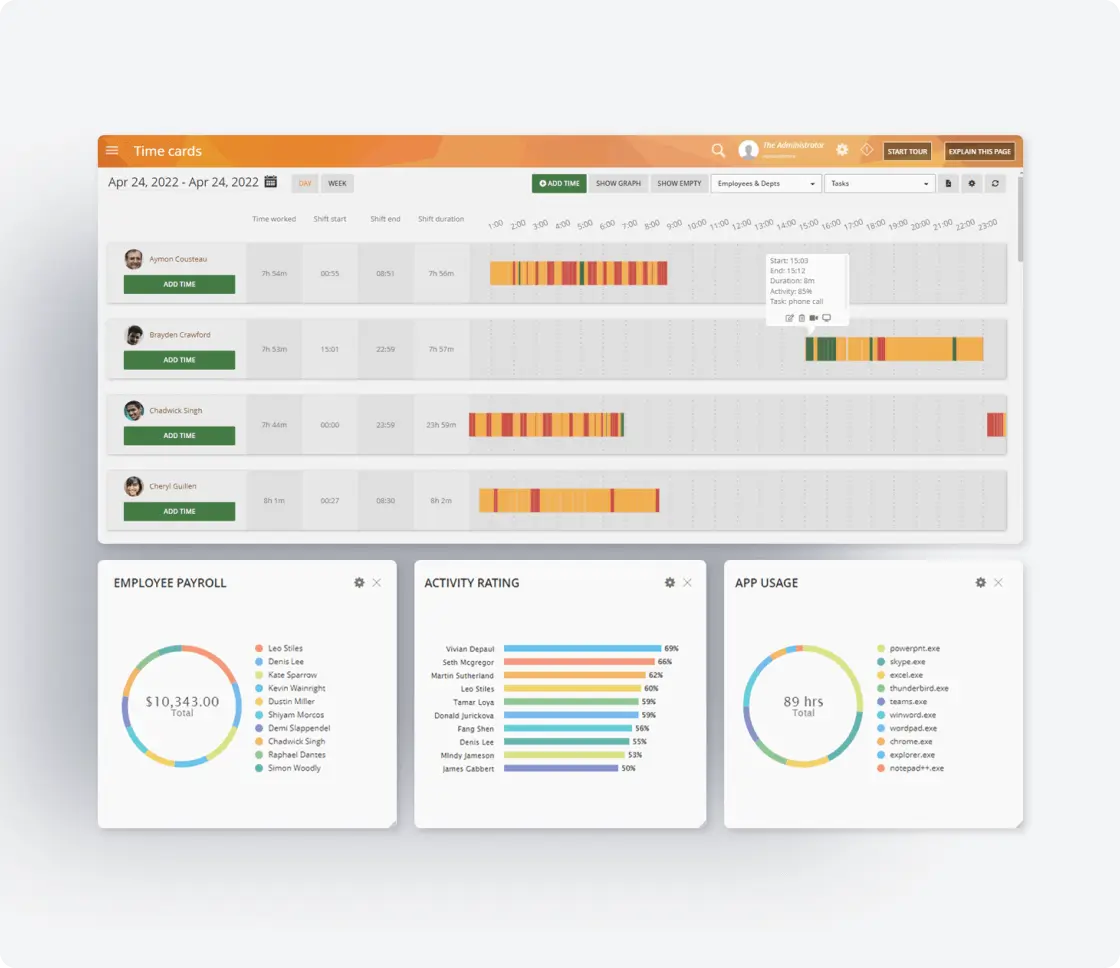
Customized Reporting
and Analytics
Generate detailed reports tailored to your specific risk management needs.
Track performance metrics for each vendor and contractor
Create customized reports for leadership and compliance teams
Schedule automated reports to ensure regular review
Export data for integration with other security and risk management solutions
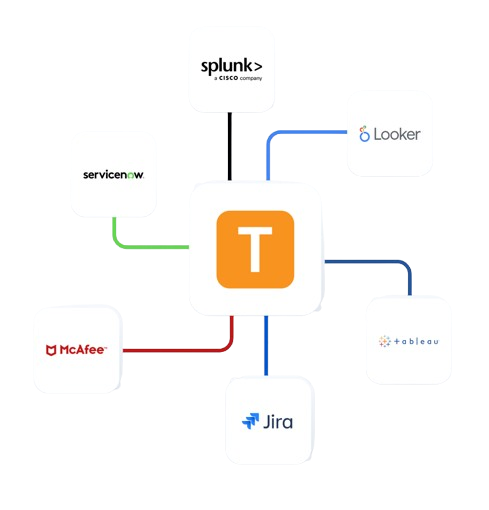
Enterprise Integrations
Integrate Teramind with your existing security infrastructure to enhance third party risk management.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What is third-party risk management software?
Third-party risk management software (TPRM) is a solution that helps organizations identify, assess, monitor, and mitigate risks from external vendors. Teramind's platform provides comprehensive activity tracking, real time alerts, and customizable security policies that protect against data breaches while ensuring regulatory compliance across all third party relationships and throughout the vendor lifecycle.
What is the best risk management software?
The best risk management software provides comprehensive monitoring capabilities with real time alerts and detailed reporting features. Teramind offers a complete TPRM software solution with continuous monitoring, customizable dashboards, and flexible monitoring agents that deliver the security controls needed for effective third party risk management in today's complex business environment.
What is the NIST standard for third party risk management?
The NIST standard for third party risk management is outlined in Special Publication 800-161, focusing on cybersecurity supply chain risk management. Teramind aligns with these guidelines by enabling thorough risk assessments, implementing appropriate access controls, maintaining documentation, and providing continuous monitoring of third party activities to detect and mitigate potential security threats across your supply chain.
What is an example of a third party risk management framework?
A comprehensive party risk management framework typically includes vendor identification, risk assessments, due diligence, contract management, ongoing monitoring, and incident remediation. Teramind supports this framework with tools for detailed vendor management, risk profiling, access controls, continuous monitoring, and rapid response capabilities that help build an effective party risk management program.
How do you create a third party risk management program?
Creating an effective party risk management program involves developing a vendor inventory, establishing risk criteria, implementing appropriate controls, developing policies, ensuring continuous monitoring, creating incident response procedures, and regularly updating your program. Teramind provides the technology foundation needed to implement and maintain a robust program that protects your organization from third party threats throughout the entire vendor lifecycle.




