User Activity Monitoring and Endpoint Security for Retail & E-Commerce
Protect your retail business and customer data with intelligent user activity monitoring that can detect compromises to company data
One solution to protect and manage
retail & E-Commerce business data
Automate and manage employee compliance
Use Teramind’s compliance management toolkit to:
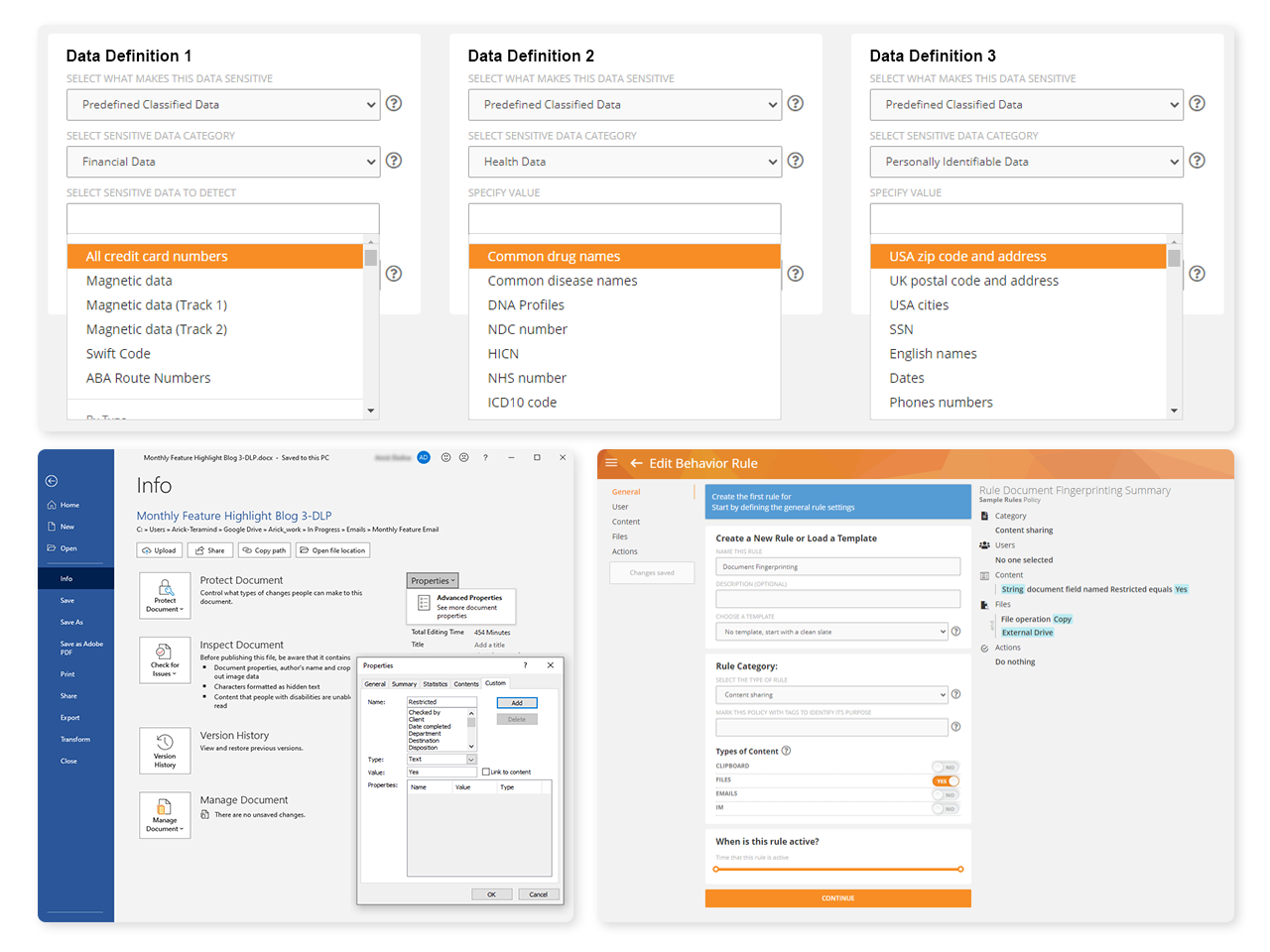
Monitor activity with prebuilt rule templates for PCI DSS, financial information and other types of sensitive data
Automatically block noncompliant data actions
Collect detailed evidence like immutable logs and session recordings for audits
Use Teramind’s OCR to comb unstructured data to locate company data applicable to regulations
Harness compliance risk assessments to create focused and relevant cybersecurity training
Track and supervise all activities relating to sensitive data anywhere on the system
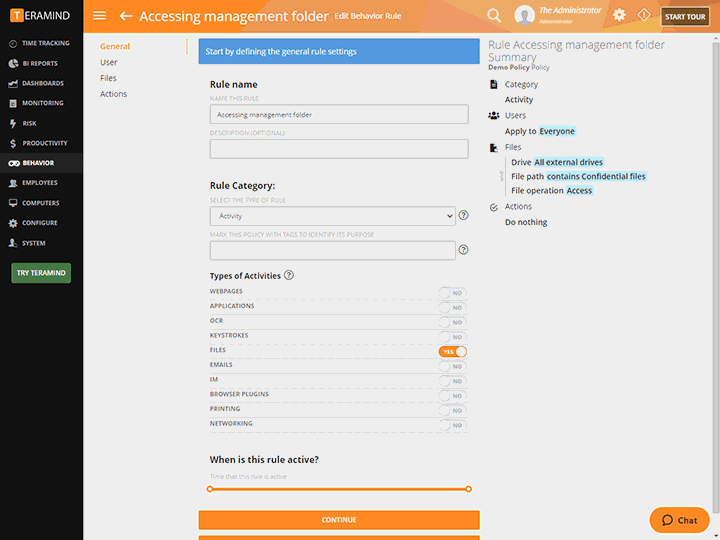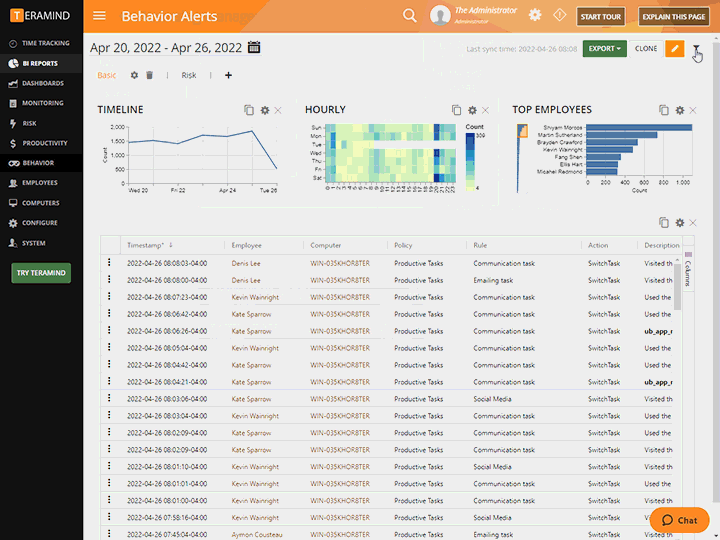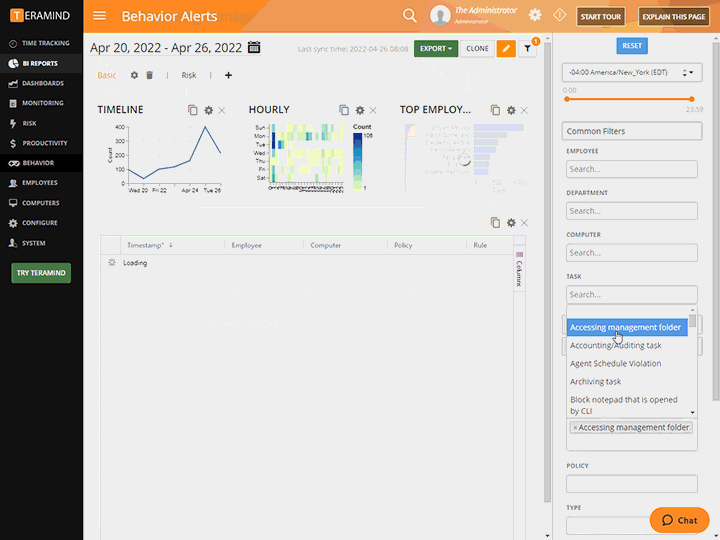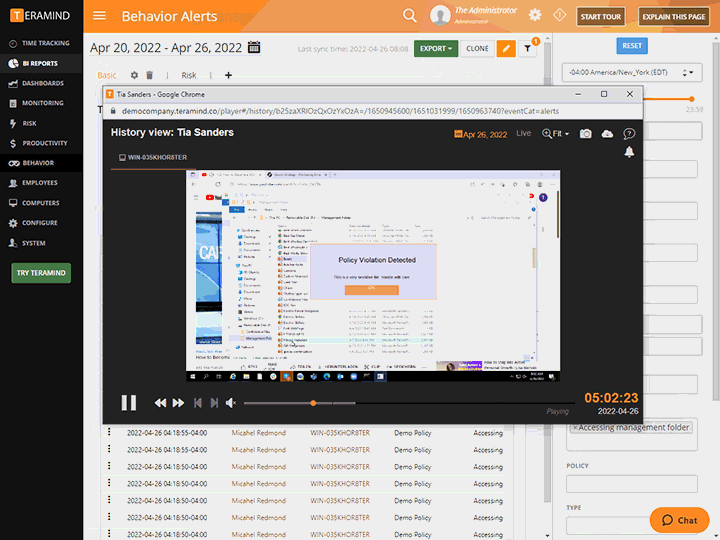
Use Teramind’s Behavior Rules and Alerts and scriptable rule logic to:
Monitor all user actions relating to sensitive data from access to editing to transfers
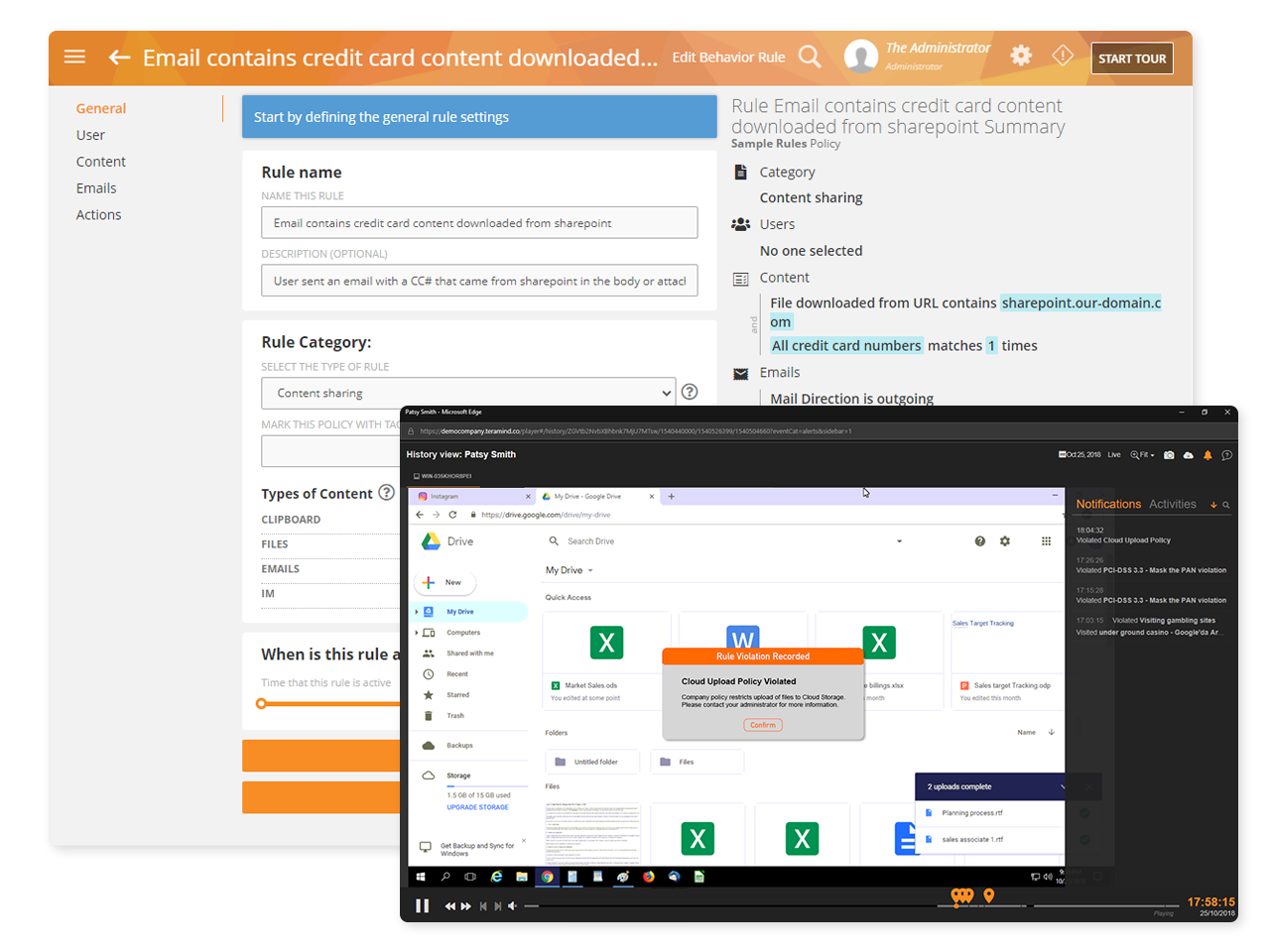
Block actions, lock users out and notify administrators when actions are high-risk
Leverage prebuilt rule templates to automatically monitor and log customer PFI data activities
Secure sensitive data residing on POS systems, back-office workstations, on the network or on the cloud
Protect against PFI and PCI data exfiltration
Use Teramind’s user activity monitoring to:
Identify malicious behavior and insider threats to sensitive data in real time
Monitor third party vendors and contractors with privileged access to data
Limit access to cardholder/transaction servers and databases
Prevent users from sharing classified PFI and PCI on the web, to unauthorized apps, via email and more
Get risk assessments and threat alerts for the organization, departments or individual users
The Features That Power Teramind
We bring businesses peace of mind through our award-winning user activity monitoring solution
The Experience
Speaks For Itself
Ready to get started?
Improve your security posture, detect insider threats and manage regulation compliance
while improving productivity along the way