Hybrid Workforce Security Software for Remote and Office Environments
Teramind’s hybrid workforce security solution protects sensitive data, prevent insider threats, and ensures secure access across hybrid work environments while maintaining the employee experience and business continuity.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics.







Why Choose Teramind for
Hybrid Workforce Security
Unified Security Measures for Hybrid Work Models
Our platform provides robust security measures whether employees work from office environments or remote locations. Protect company resources and sensitive information consistently across your entire hybrid workforce, addressing security vulnerabilities unique to hybrid work environments.
Combat Insider Threats Across All Access Points
Our security solutions detect external threats whether employees connect through corporate networks, home networks, or public wi fi networks. Secure access to sensitive data while preventing data breaches across your distributed workforce.
Balance Security Controls with Employee Experience
Implement security strategies that protect against cyber threats without disrupting the work life balance that makes hybrid work successful. Our approach to hybrid workforce security ensures business continuity while enabling the flexibility your remote workforce needs.
Core Teramind Features for Hybrid Workforce Security
Our platform addresses the unique security challenges of protecting hybrid work models across multiple devices and various locations.
Endpoint Security for Hybrid Environments
Comprehensive protection across all devices and networks:
Monitor corporate devices and authorized personal devices in hybrid work setups
Track secure access to company resources from office space or remote locations
Implement security controls that work across corporate network and home networks
Maintain endpoint security regardless of where hybrid workers connect
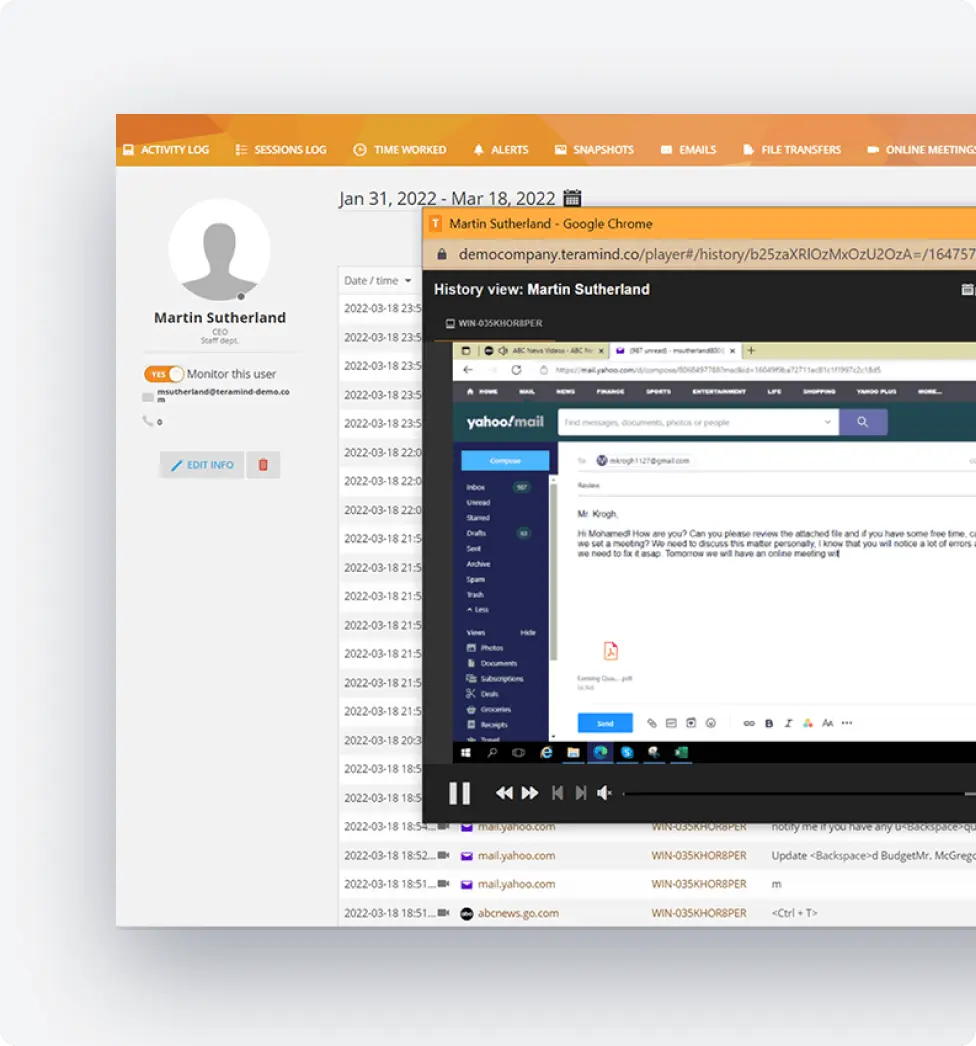
Advanced Threat Detection and Prevention
Identify cyber threats unique to hybrid workforce environments:
Monitor for internal threats targeting remote workers and office-based staff
Track suspicious access patterns suggesting security vulnerabilities
Alert security teams to potential threats in real-time
Prevent other cyber threats specific to hybrid work models
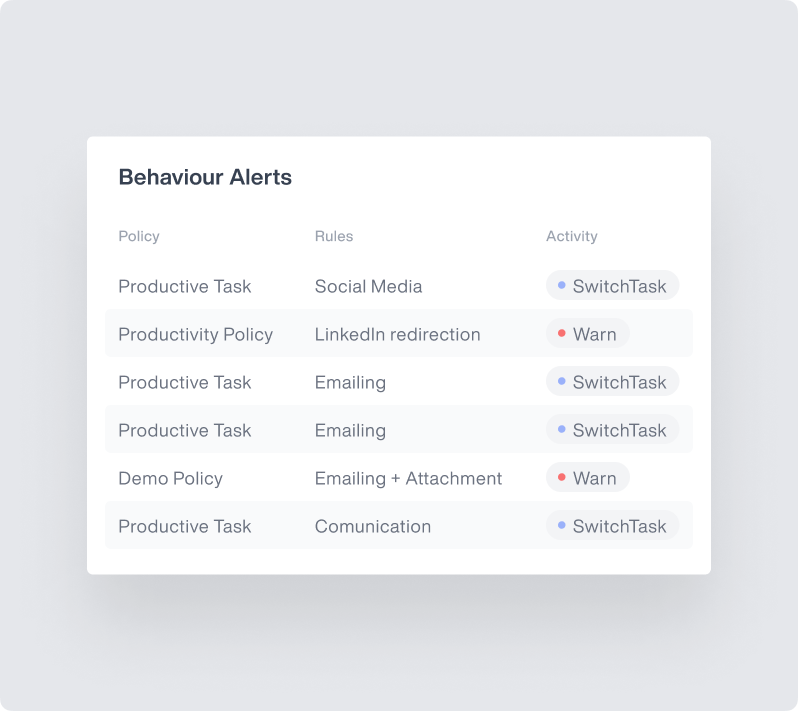
Network Security Monitoring
Protect against vulnerabilities across diverse networks:
Monitor connections from corporate network, home networks, and remote access
Detect when hybrid workers connect through unsecured networks
Track VPN usage to ensure secure network connections
Independently ensure network security across all locations
Reduce attack surface by controlling network access
Compliance and Security Awareness
Build security culture in hybrid work environments:
Provide security awareness training based on detected security risks
Monitor compliance with security policies across hybrid workforce
Track usage of approved versus shadow IT tools
Generate reports for enhancing security measures
Support overall security through continuous improvement
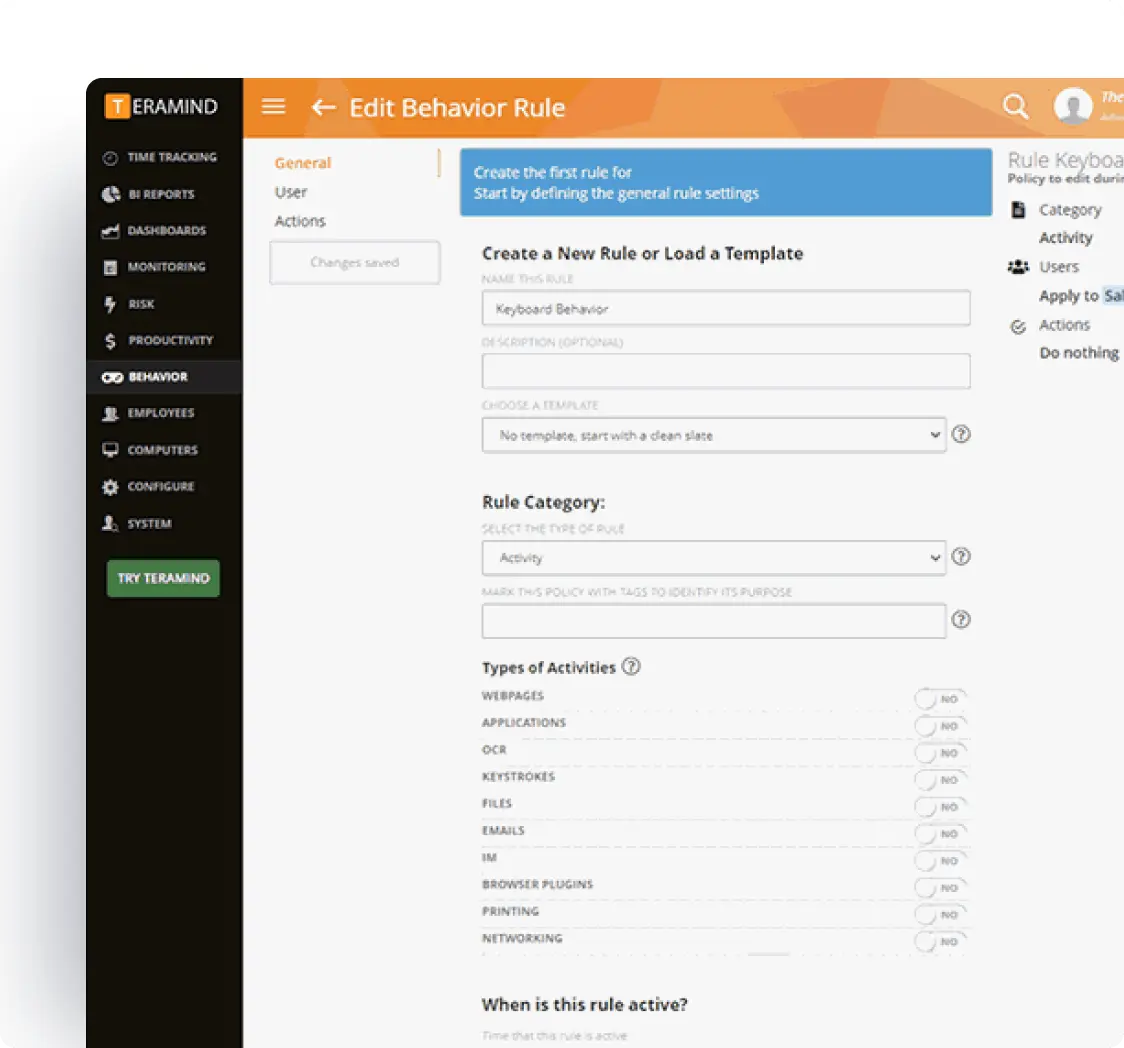
Security Rules and Policies
Create customized security policies tailored to your specific security needs.
- Develop rules to identify and protect various categories of personal data
- Automatically enforce data handling policies across your organization
- Create custom compliance playbooks using automated blocking and alerts
- Establish regulatory standards for handling consumer data throughout your business
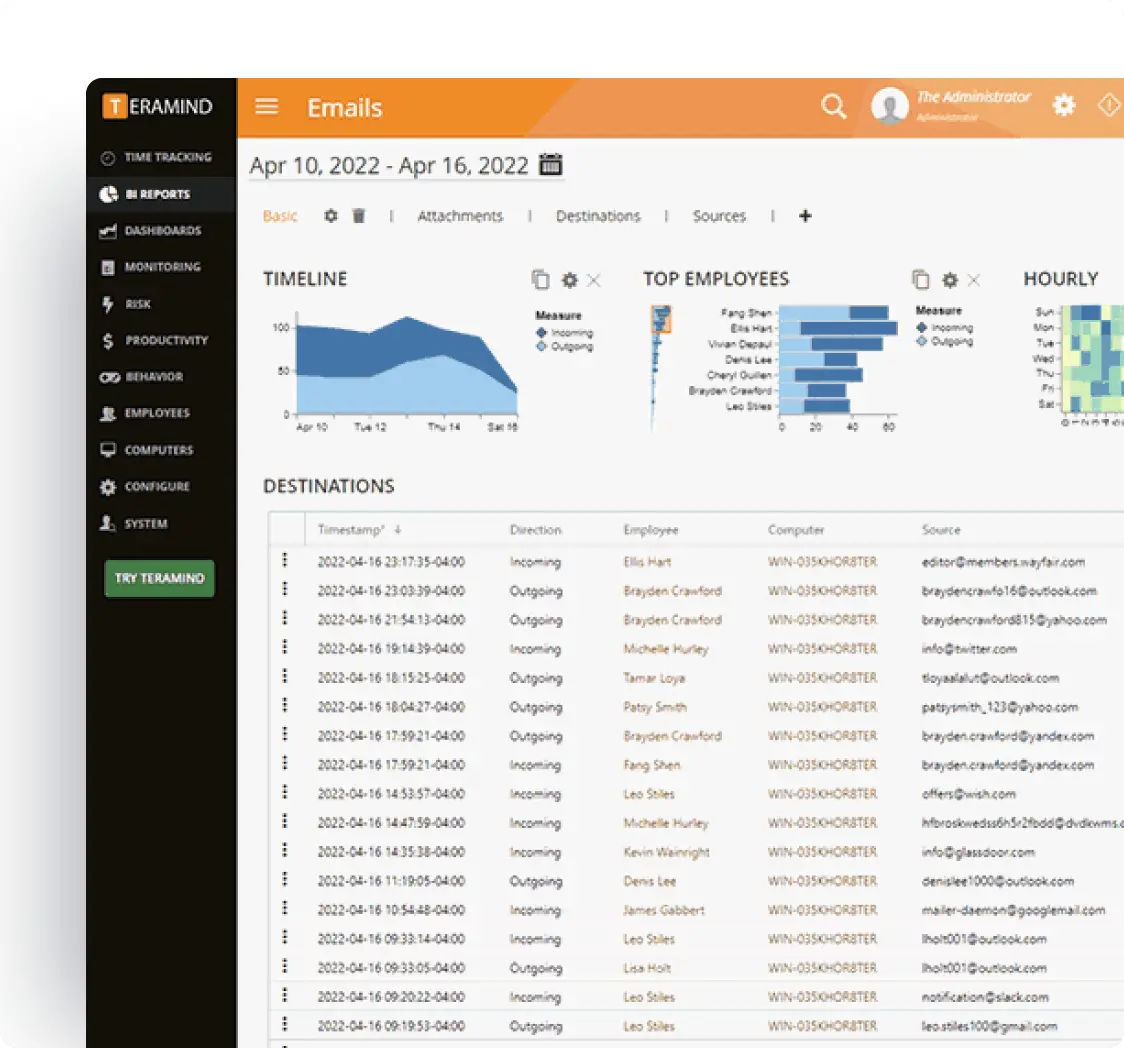
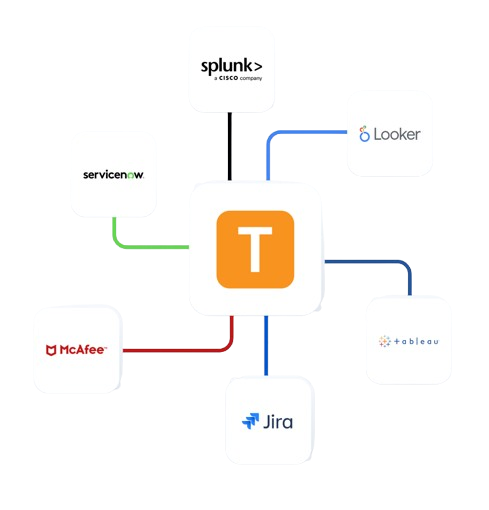
Enterprise Integrations
Integrate Teramind with your existing infrastructure to enhance security.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
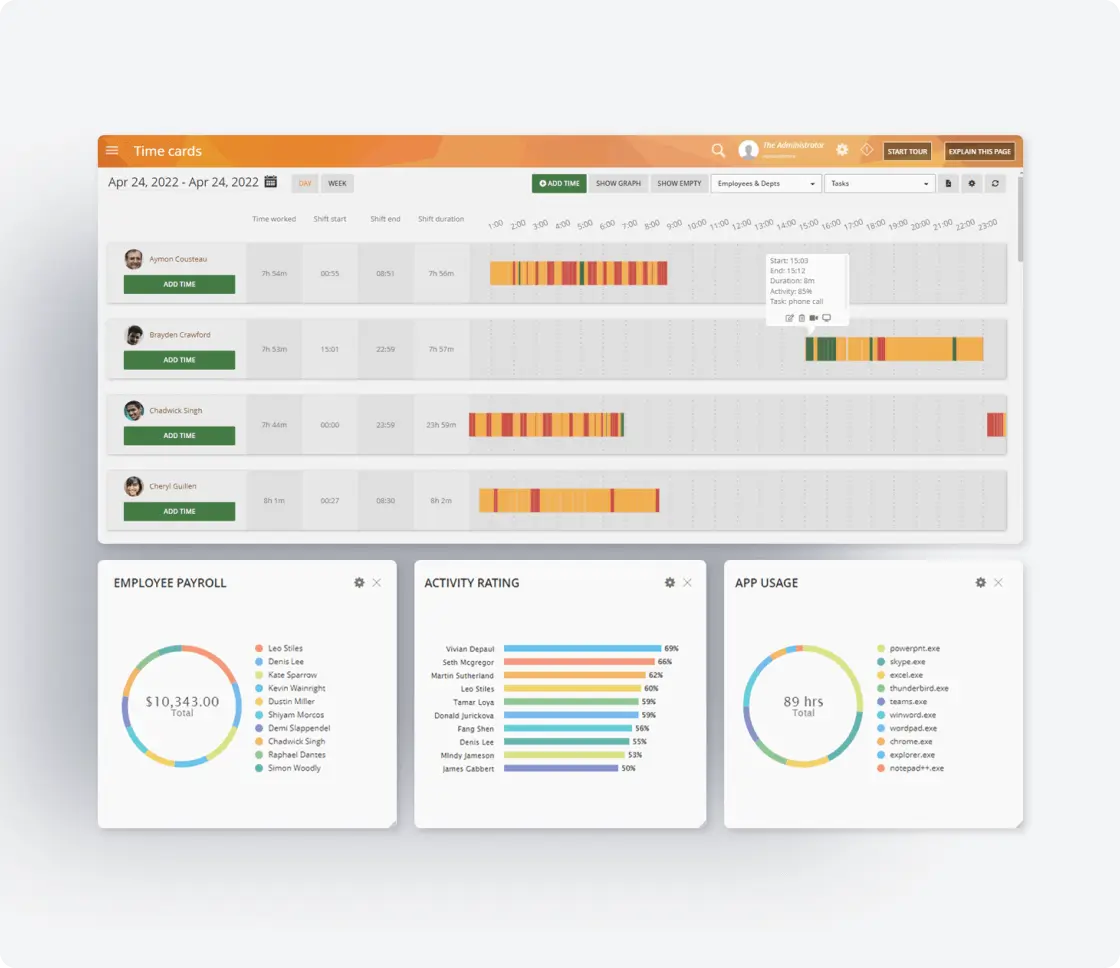
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What are the main security challenges in hybrid workforce models?
Hybrid workforce security faces unique security challenges including expanded attack surface, inconsistent security controls across locations, and increased use of personal devices. The hybrid workforce model creates security vulnerabilities when employees switch between office environments and remote work, potentially using less secure home networks or public wi fi networks. Additionally, hybrid work environments make it harder for security teams to maintain consistent security measures across all access points.
How can organizations ensure secure hybrid work without impacting productivity?
Effective hybrid work security balances robust security measures with positive employee experience. This includes implementing secure access service edge technology, deploying multi factor authentication that's user-friendly, and using security solutions that work transparently. Organizations should focus on security strategies that enable business continuity rather than hinder it, using built in protection and automated security controls that don't disrupt the work life balance essential to successful hybrid work models.
What security measures are essential for protecting sensitive data in hybrid environments?
Essential security measures for hybrid workforce security include comprehensive endpoint security, multi factor authentication mfa, and continuous monitoring for phishing and malware attacks. Organizations need multiple layers of protection including network security monitoring, data security controls, and security awareness training. Protecting sensitive information requires addressing both cyber threats and the human element, ensuring secure access while monitoring for potential threats across all devices and networks.
How does Teramind address security risks specific to hybrid workforce environments?
Teramind provides comprehensive visibility across the entire hybrid workforce, monitoring security risks whether employees work from corporate networks or remote locations. Our platform detects potential threats including unauthorized access attempts, data breaches, and other cyber threats while providing security teams with real-time alerts. By tracking user behavior patterns across office space and remote work locations, we help identify security vulnerabilities specific to hybrid work setups and provide valuable information for improving security and enhancing security measures continuously.




