Compliance Monitoring Software
Ensure regulatory compliance through employee activity monitoring. Our platform helps your team detect potential compliance risks, streamline compliance processes, and provide the evidence needed to demonstrate compliance with regulatory requirements and internal policies.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce efficiency.







How Teramind Makes Compliance Monitoring Easy
Real-Time Visibility
Leverage continuous monitoring, screen recordings and real-time data to ensure adherence to compliance regulations and regulatory obligations across your entire organization.
Automated Evidence Collection
Eliminate manual effort in compliance activities by automatically capturing evidence needed for compliance audits, reducing manual processes while creating comprehensive audit trails.
Risk Management Intelligence
Transform monitoring data into actionable risk data that helps compliance officers identify and mitigate risks before they escalate into non-compliance issues and potential reputational damage.
Teramind's Compliance Monitoring Tools
Our specialized compliance software provides the compliance tools organizations need to maintain ongoing compliance and stay ahead of evolving regulations in today’s complex regulatory environments.
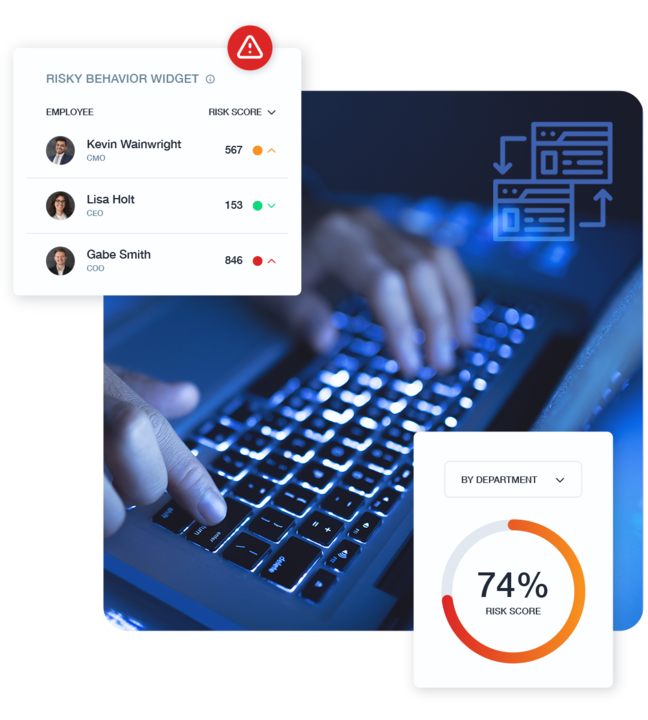
Employee Activity Monitoring
Track all user activities to ensure adherence to compliance requirements and internal policies.
Monitor employee interactions with regulated systems to identify potential risks
Record screen activity as evidence for your compliance program
Track communications to verify compliance with industry standards
Leverage OCR to capture on screen information
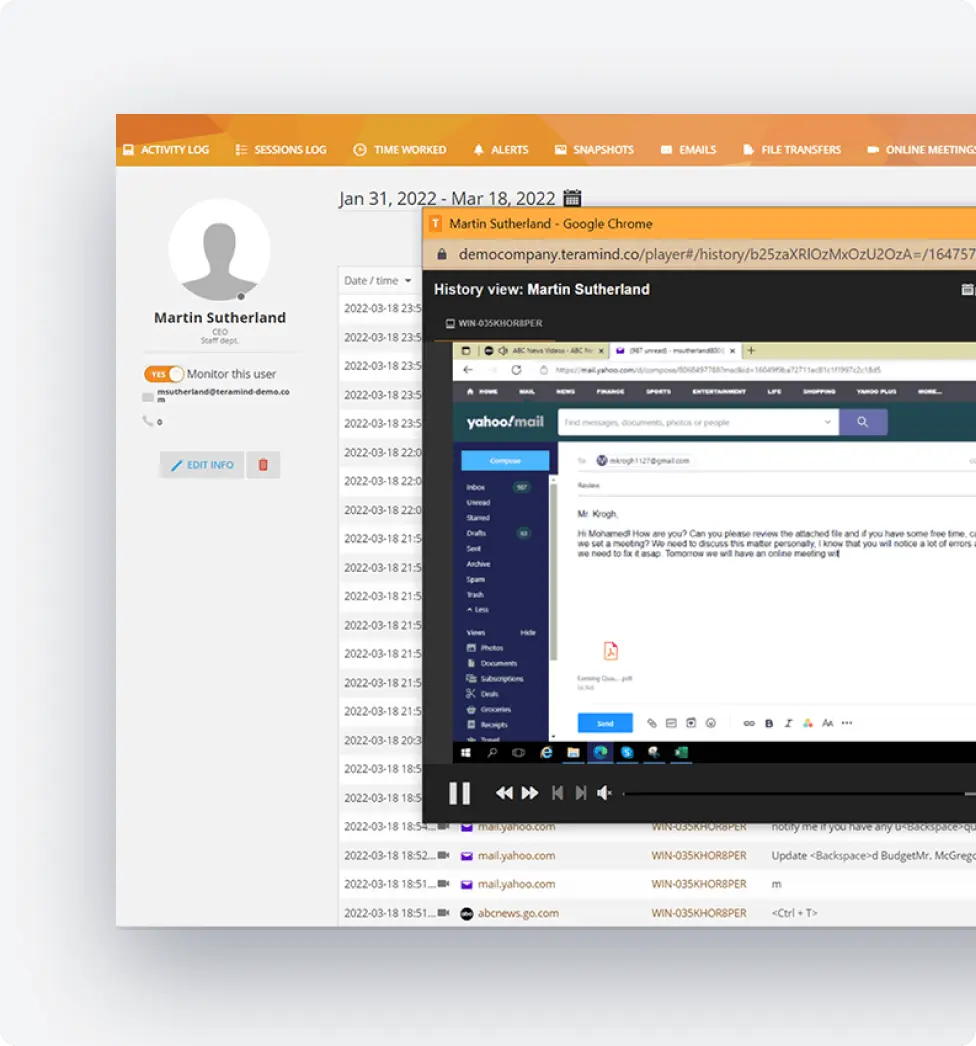
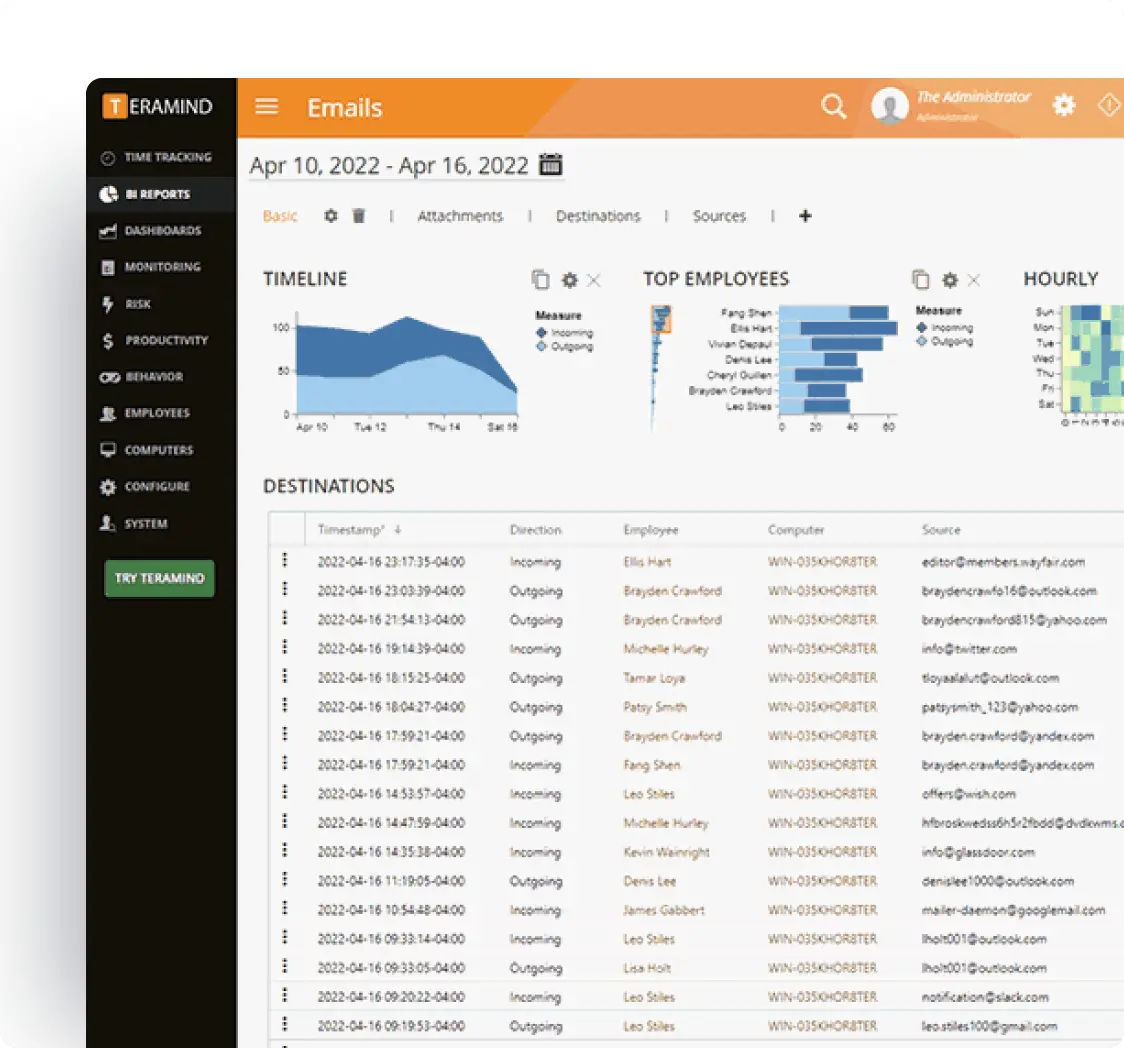
Data Loss Prevention
Address regulatory obligations related to sensitive information handling and protect against compliance risks.
Monitor file transfers to ensure compliance with data regulations
Detect unauthorized access that could lead to compliance issues
Prevent data leakage that could trigger non-compliance
Generate status reports showing data handling compliance
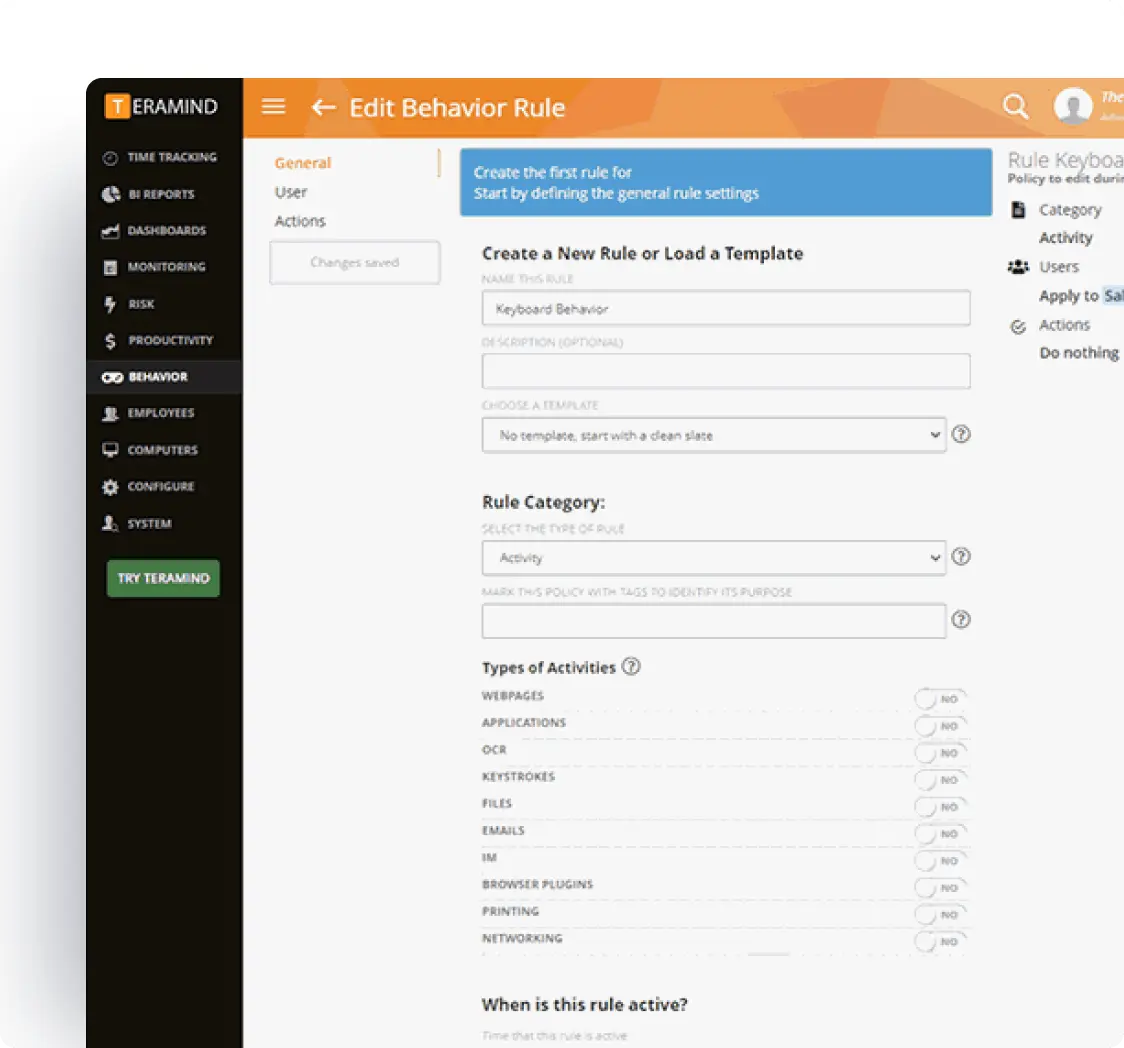
Industry-Specific Compliance Monitoring
Adapt to various industries and their unique regulatory requirements (HIPAA, FISMA, NIST, PCI DSS, etc.) with specialized monitoring.
Industry-specific monitoring templates to address changing regulations
Customized solutions for financial services, healthcare, and other regulated sectors
Focused detection of industry-specific compliance risks
Support for operational efficiency while maintaining regulatory compliance
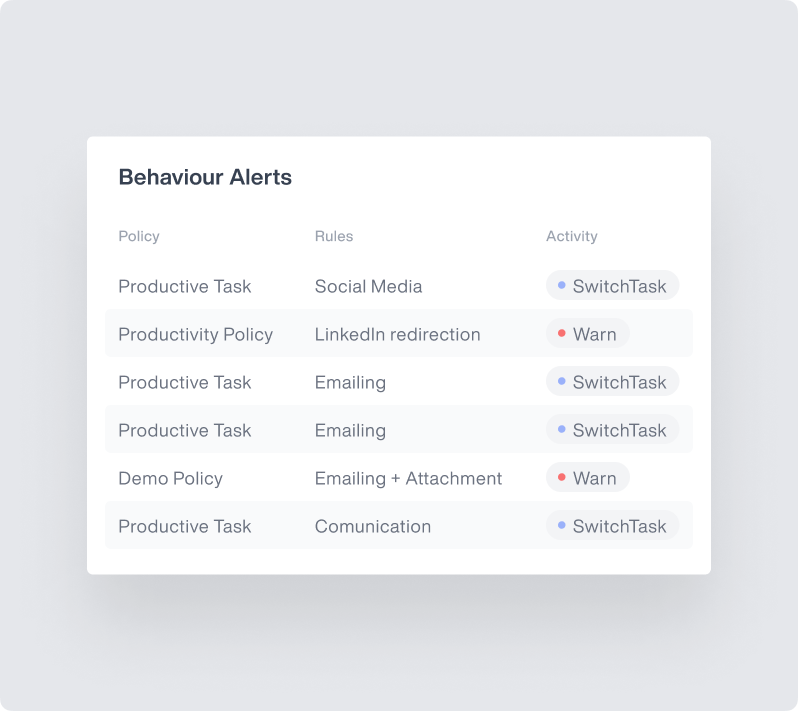
Compliance Risk Detection
Leverage advanced analytics to identify potential compliance risks through employee behavior analysis.
Early detection of activities that may indicate compliance function weaknesses
Use machine learning to identify patterns that could lead to compliance issues
Automated tools for risk assessments based on employee activities
Continuous monitoring for compliance and risk indicators in employee behavior
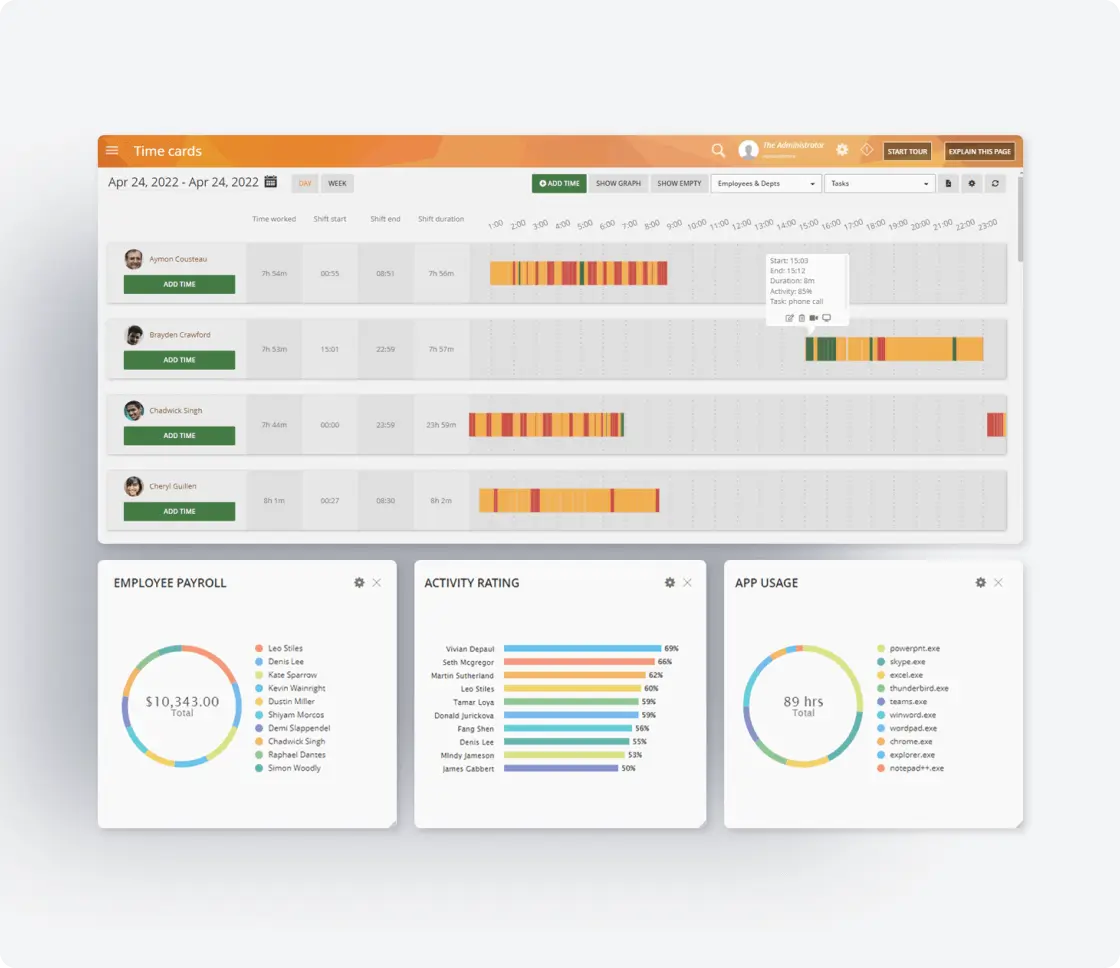
Compliance Reporting
Generate comprehensive documentation for demonstrating compliance to internal audit teams and external regulators.
Detailed activity logs that serve as reporting tools for compliance audits
Real-time dashboards showing compliance status across the organization
Evidence collection supporting informed decision making
Automated reports that demonstrate compliance with minimal manual effort
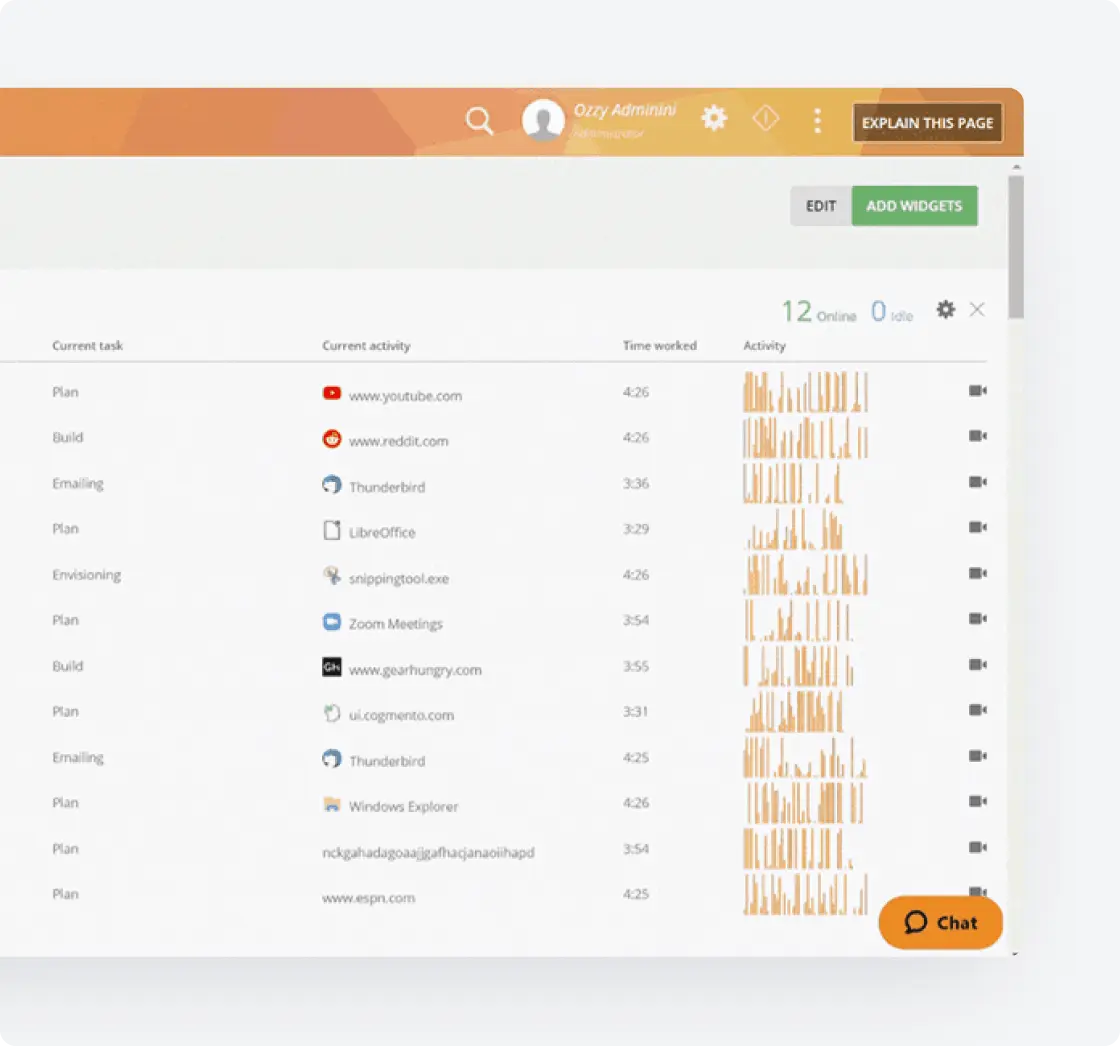
Violation Alerting & Case Management
Quickly address compliance issues when monitoring detects potential violations.
Real-time alerts for activities that may violate compliance regulations
Immediate notification to compliance officers about detected risks
Comprehensive case management for identified non-compliance issues
Complete audit trails to support remediation plans
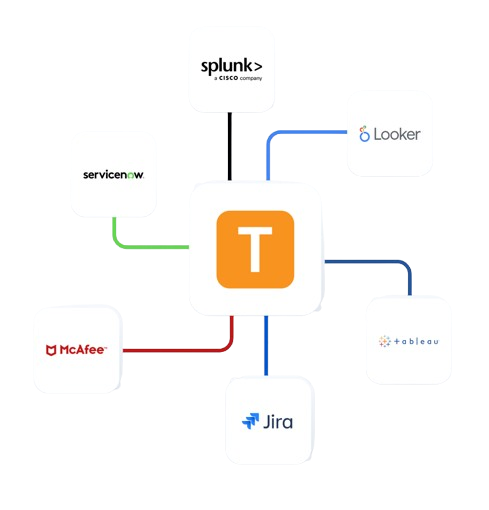
Enterprise Integrations
Integrate Teramind with your existing security infrastructure to enhance compliance monitoring.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What is a compliance monitoring program?
A compliance monitoring program is a structured component of an organization's overall compliance management system designed to ensure employees consistently adhere to regulatory requirements and internal policies. It combines continuous monitoring of user activities with risk management principles to identify potential compliance risks before they result in violations or reputational damage. Effective compliance monitoring software like Teramind automates these compliance processes, providing compliance teams with the tools they need to manage risks and maintain regulatory compliance with minimal manual effort.
What is the best way to monitor compliance?
The best way to monitor compliance is through a comprehensive approach that provides real-time visibility into employee activities related to regulatory obligations. By implementing automated tools for continuous monitoring and risk assessments, organizations can efficiently identify compliance issues before they escalate. Teramind's compliance monitoring software offers these capabilities while enabling compliance officers to focus on addressing potential risks rather than struggling with manual processes. This integrated platform approach helps streamline compliance processes while ensuring that compliance activities are consistently performed across the organization.
How do you track compliance?
Tracking compliance effectively requires monitoring employee interactions with regulated systems and data across your organization. This includes tracking application usage, communications, and file handling relevant to compliance requirements. Compliance teams can eliminate manual effort by utilizing compliance management tools that automate evidence collection, conduct ongoing monitoring of employee activities, and generate status reports that demonstrate compliance. Teramind provides these monitoring capabilities in one comprehensive solution, helping organizations stay ahead of evolving regulations while maintaining operational efficiency.
What is SOX compliance software?
SOX compliance software is specialized monitoring technology designed to help organizations meet the requirements of the Sarbanes-Oxley Act, which establishes standards for corporate governance and financial reporting. These compliance tools monitor employee interactions with financial systems, track access to sensitive financial data, and provide the evidence needed to demonstrate compliance during compliance audits. Teramind's monitoring capabilities include features specifically designed for SOX compliance, helping organizations identify potential compliance risks and ensuring adherence to these critical regulatory obligations through comprehensive user activity monitoring in accordance with industry standards.




