ChatGPT DLP Software: Prevent Data Exfiltration Through AI Tools
Advanced DLP software that monitors and blocks sensitive data sharing with ChatGPT and other AI tools, protecting your organization from AI-driven data exfiltration.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics.







Why Choose Teramind for ChatGPT DLP
Block Sensitive Data Before It Reaches AI Models
Our ChatGPT DLP software detects and prevents employees from sharing confidential information, trade secrets, and regulated data with AI systems in real-time, stopping data leaks before they happen.
Comprehensive AI Platform Coverage
Monitor data sharing across all AI access points – browsers, desktop apps, and API integrations. Our DLP solution tracks ChatGPT, Google’s Gemini, Claude, and other generative AI tools your employees might use.
Intelligent Content Detection & Data Classification
Advanced DLP capabilities that understand context, not just keywords. Detect when employees attempt to share source code, financial data, customer information, or proprietary content with AI models.
Core Teramind Features for ChatGPT DLP
Our data loss prevention software provides specialized protection against AI-related data exfiltration risks.
Real-Time Data Loss Prevention
Stop sensitive information from leaving your organization:
- Block copy/paste of confidential data into ChatGPT prompts
- Prevent uploads of sensitive documents to AI platforms
- Detect and redact PII, financial data, and regulated information
- Monitor file attachments and image uploads to AI tools
- Create custom DLP rules for your specific data types
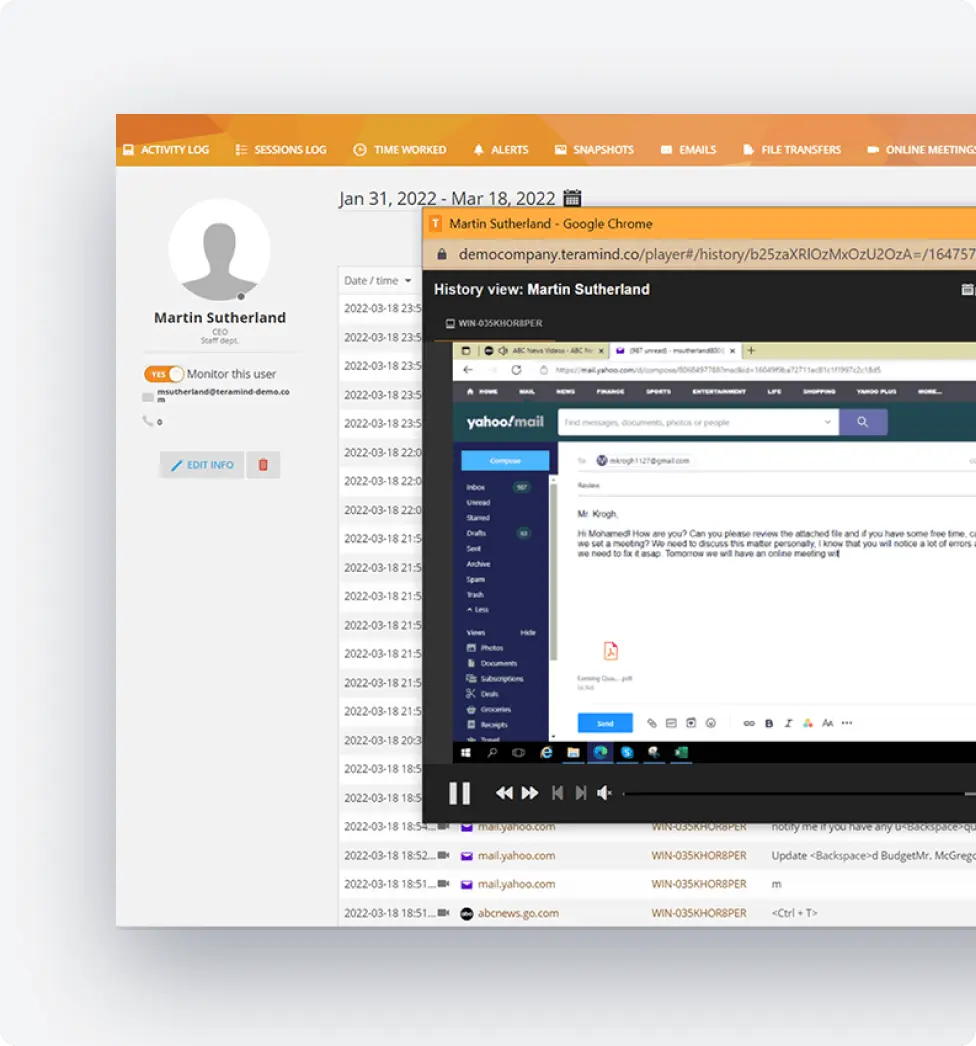
AI-Specific DLP Policies
Configure protection tailored to AI risks:
- Define what constitutes sensitive data for AI sharing
- Create department-specific rules for AI usage
- Configure blocking, warning, or logging actions
- Implement role-based DLP controls
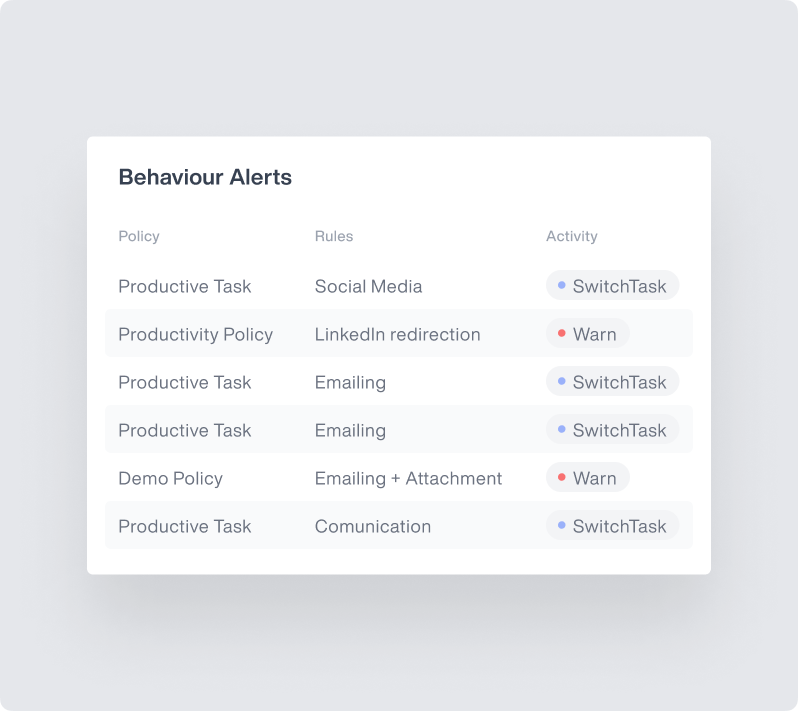
Content Inspection and Classification
Understand what data employees share with AI:
- Inspect prompts before they reach AI models
- Classify data types being shared (code, documents, spreadsheets)
- Identify patterns of risky AI usage behavior
- Track attempted circumvention of DLP policies
- Analyze trends in sensitive data exposure
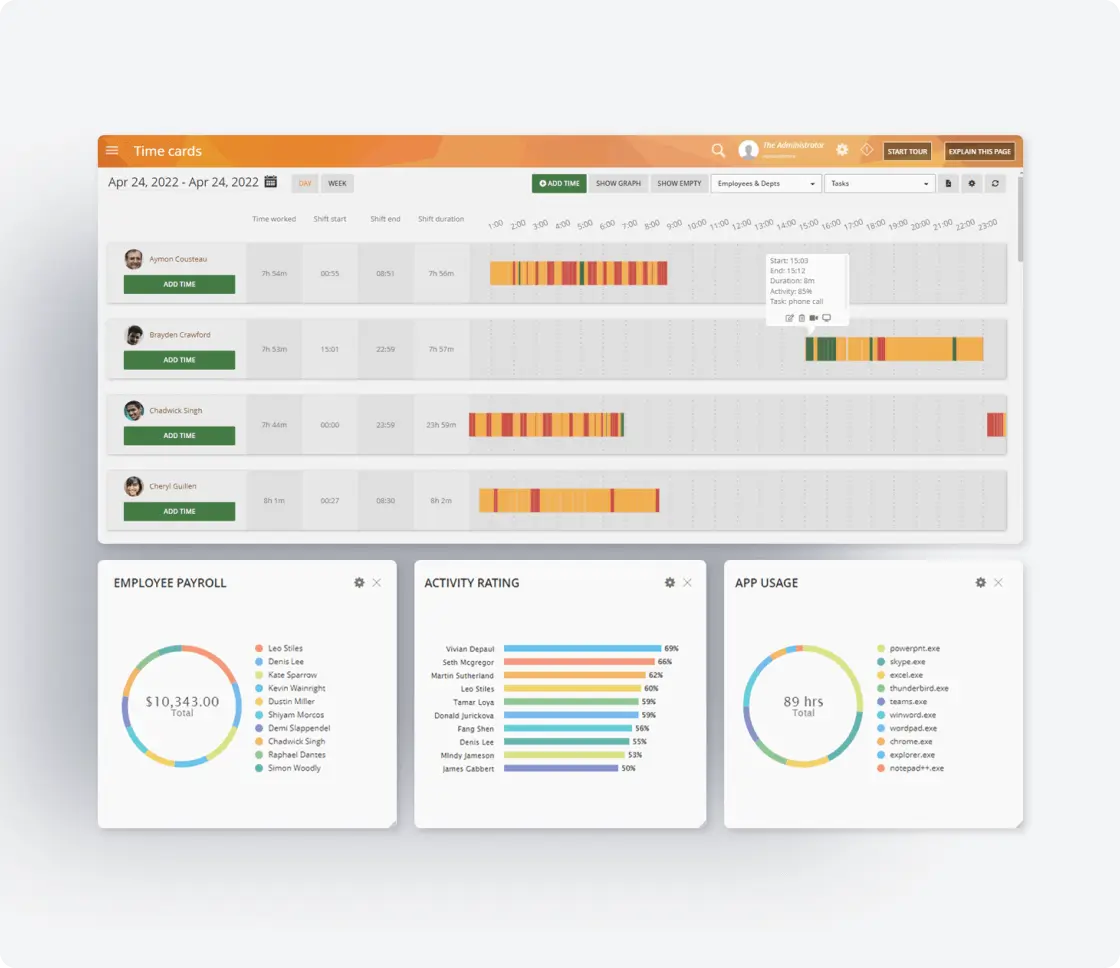
Incident Response and Forensics
Comprehensive tools for security teams:
- Generate detailed incident reports with full context
- Access screen recordings of DLP violations
- Track data movement from source to AI platform
- Create audit trails for compliance requirements
- Export evidence for investigations
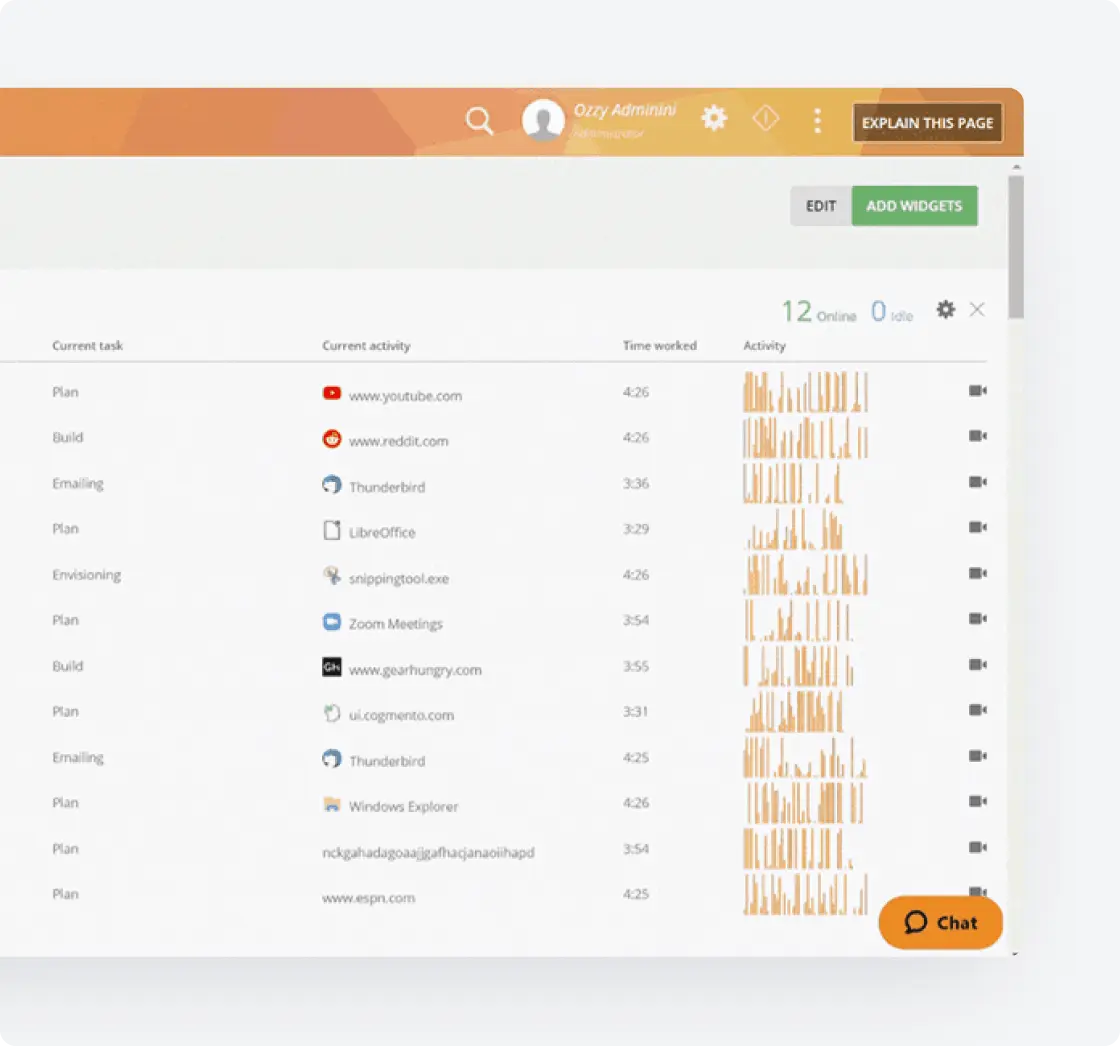
User Education and Feedback
Build security awareness around AI usage:
- Trigger real-time user notifications when DLP triggers
- Send educational messages about safe AI practices
- Coaching opportunities based on violations
- Transparency about what’s being monitored
- Feedback loops to improve security culture
Enterprise Integrations
Integrate Teramind with your existing infrastructure to enhance DLP for ChatGPT.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind's Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What is ChatGPT DLP software?
ChatGPT DLP software is specialized data loss prevention technology designed to monitor and control what information employees share with AI language models like ChatGPT. It works by inspecting data before it's sent to AI platforms, blocking sensitive information, and creating audit trails of all AI interactions. This prevents accidental or intentional data leaks through AI tools while allowing legitimate business use.
How does DLP for AI differ from traditional DLP?
Traditional DLP focuses on email, file transfers, and network traffic, while AI-focused DLP must handle conversational interfaces and understand context within prompts. ChatGPT DLP software needs to inspect natural language inputs, detect when employees are describing sensitive scenarios, and prevent data exfiltration through seemingly innocent conversations. It also must work across various AI platforms and access methods.
Can DLP software block specific types of data from ChatGPT?
Yes, modern ChatGPT DLP software can be configured to detect and block specific data types including source code, customer PII, financial records, intellectual property, and regulated data like healthcare information. The software uses pattern matching, regular expressions, and machine learning to identify sensitive content regardless of how it's formatted in a prompt.
What happens when DLP detects sensitive data in a ChatGPT prompt?
When DLP software detects sensitive information, it can take several actions based on your policies: block the prompt from being sent, redact sensitive portions while allowing safe content through, warn the user but log the activity, or silently monitor and report. Most organizations use a combination of blocking for highly sensitive data and warnings for borderline cases, along with comprehensive logging for audit purposes.




