
Actionable Workforce Analytics Data with
Teramind UAM
Robust and detailed user activity monitoring for insider threat detection, productivity optimization and employee monitoring




Objective Data Insights Into Your Operation
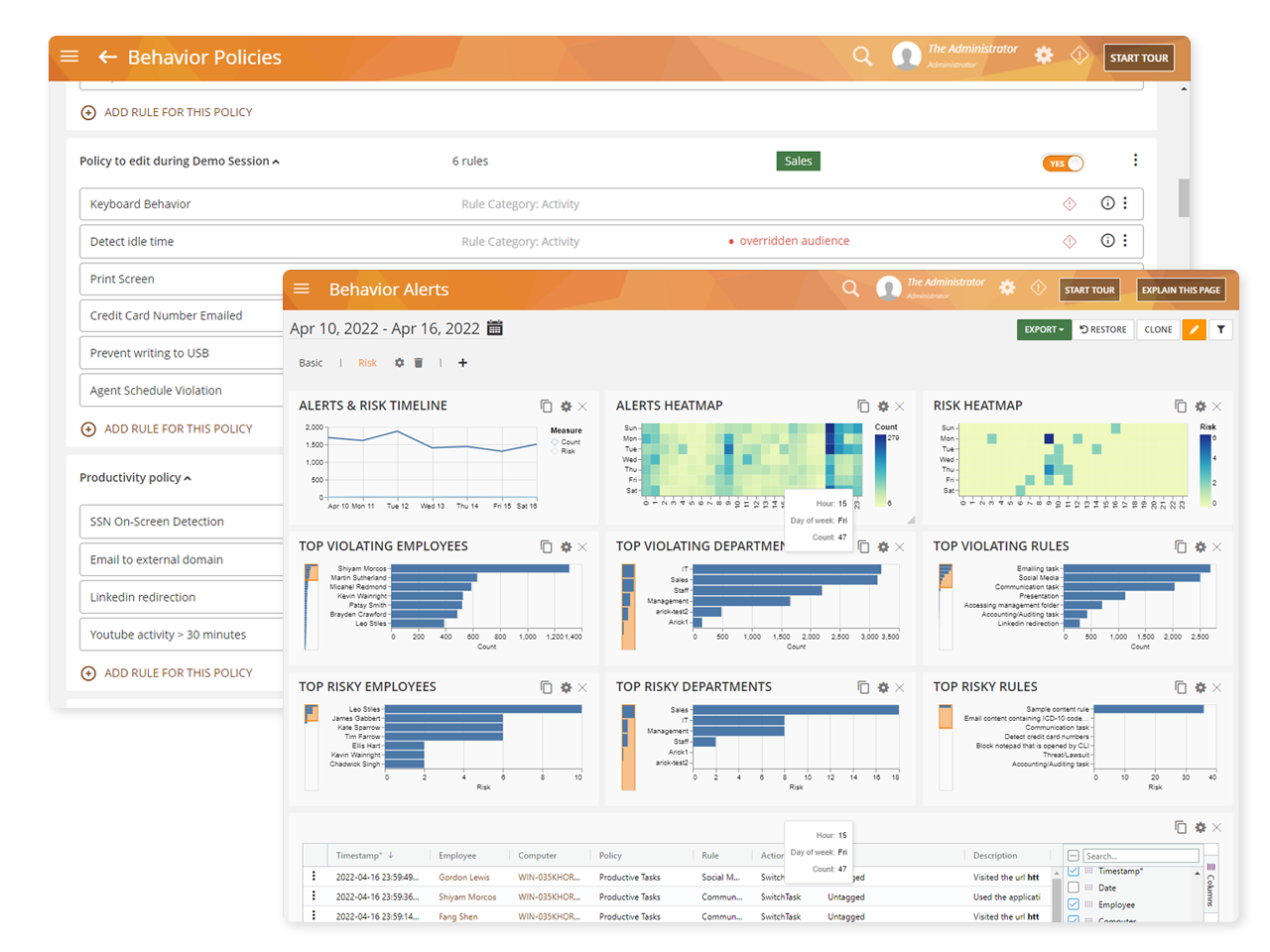
Insider Threat Detection
Learn moreWorkforce Productivity Optimization
Learn moreBusiness Process Optimization
Learn moreRemote Employee Monitoring
Learn moreThe Features That Power Teramind
Flexible Deployment
Deploy Teramind in a way that works for your organization

Cloud
Get up and running in minutes with Teramind cloud deployment. Automatic updates with no licenses or hardware
Explore the
Teramind Suite
Not sure this is the right fit for your organization? Check out the other solutions in our product suite
Teramind Starter
Get acquainted with the power of data analytics through our introductory monitoring solution suited for organizations in need of basic monitoring. Gain workforce visibility with all of the most essential features
Learn more
Teramind UAM
Enhance your monitoring capabilities while providing detailed behavioral analysis with Teramind’s award-winning platform that offers more robust features
Learn more
Teramind DLP
Safeguard data, protect against insider threats and strengthen your overall defensive posture through behavioral analysis and insights with our most popular and comprehensive solution
Learn more
Teramind Enterprise
Create a completely customized user activity and endpoint monitoring platform that supplies the power of Teramind’s data collection tailored to your organization’s exact needs
Learn more
Teramind Agent
Quick Facts
Hidden or Revealed Agents
Unobtrusive & transparent
Low Resource Consumption
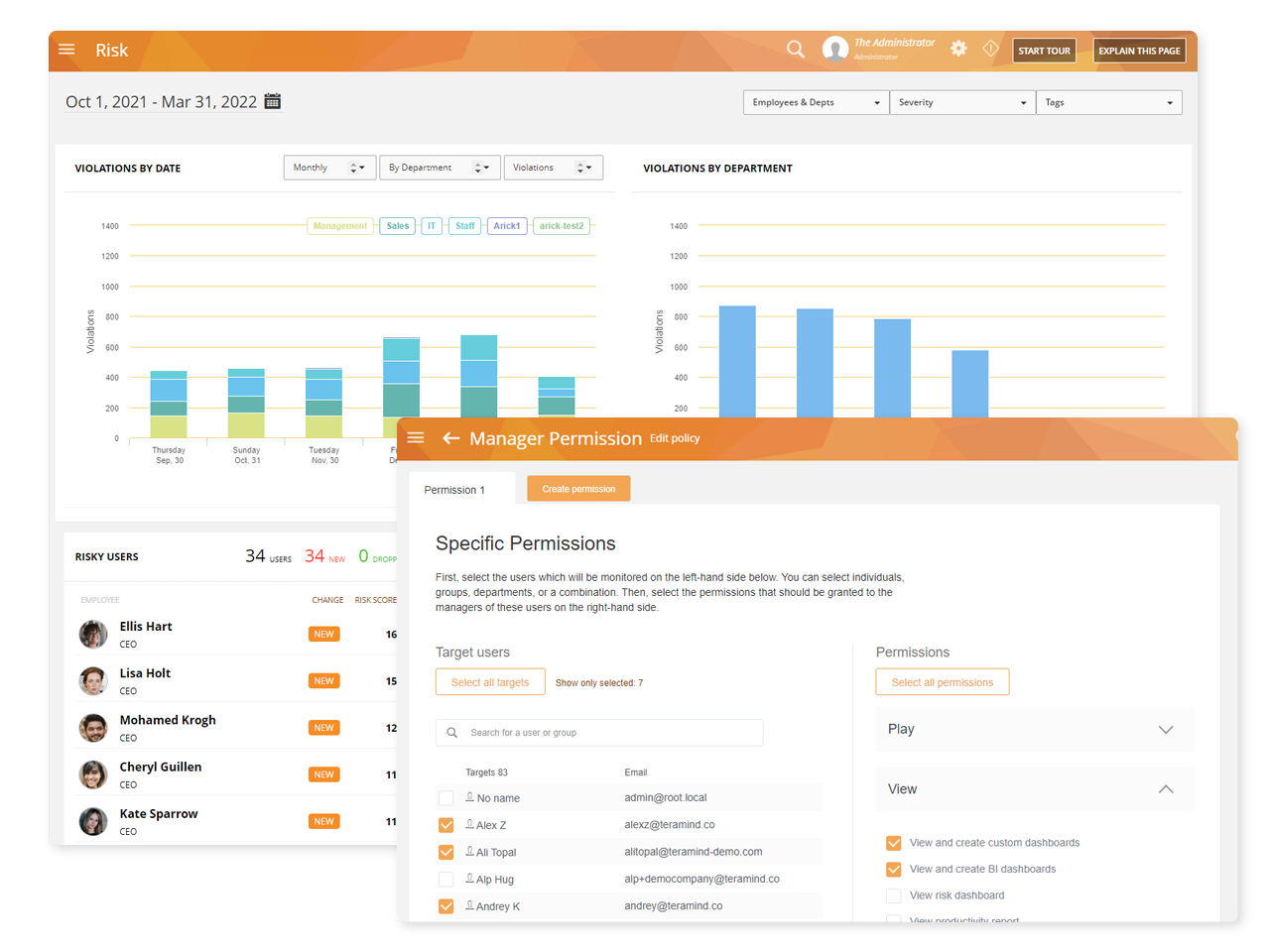
Integrations
Teramind easily integrates with your organization’s security and
project management systems directly from the dashboard
The Experience
Speaks For Itself
Learn More About User Activity Monitoring
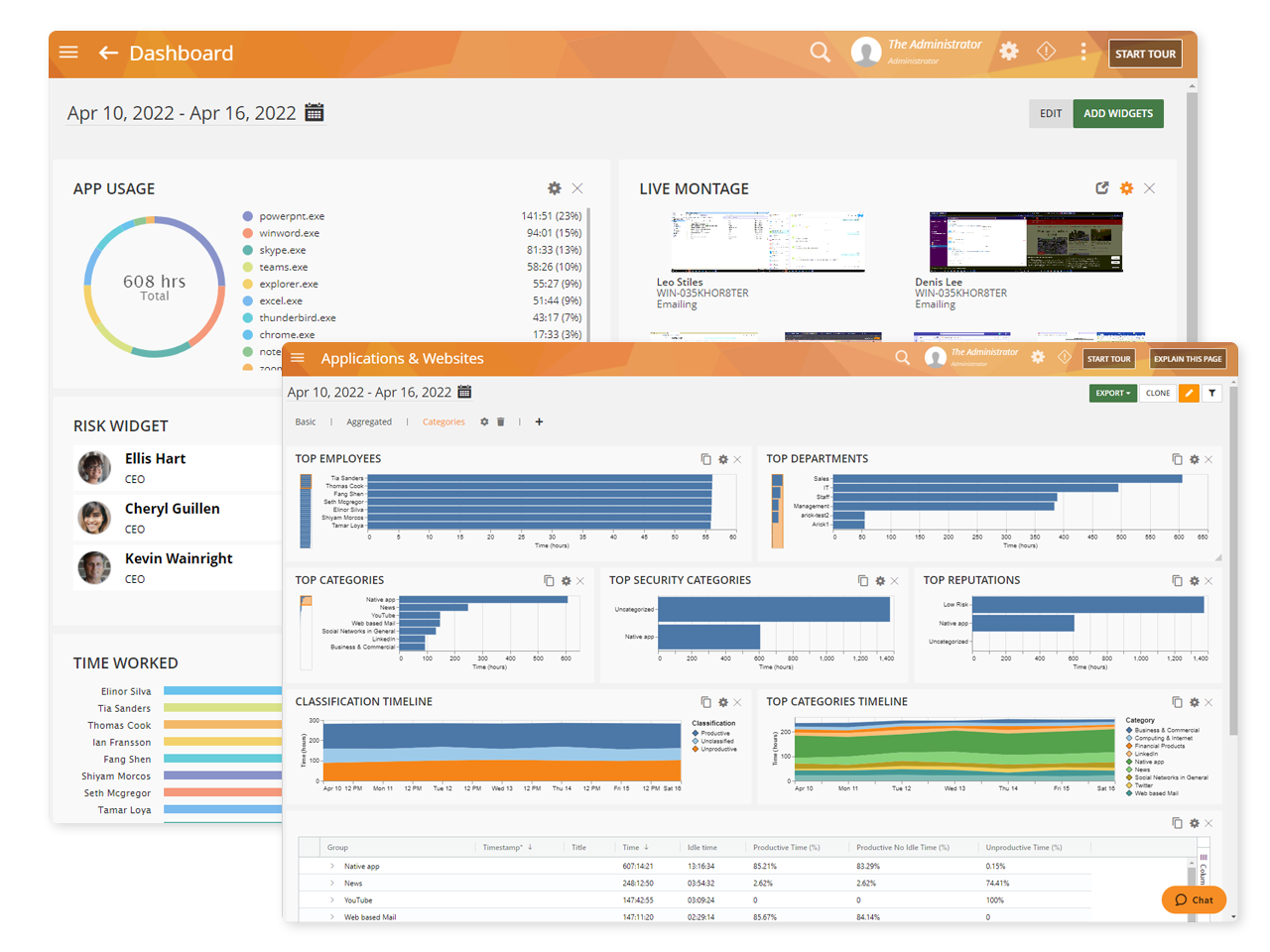
After installation, the monitoring agent tracks and logs the activity and actions conducted by the end user on the monitored machine. The activity and actions that are logged depend on the user activity monitoring software used.
Our essential monitoring product, Teramind Starter, has the ability to track and log activity like keystrokes, while our other products in the Teramind product suite offer more comprehensive monitoring solutions that track file activity, web and application use and more.
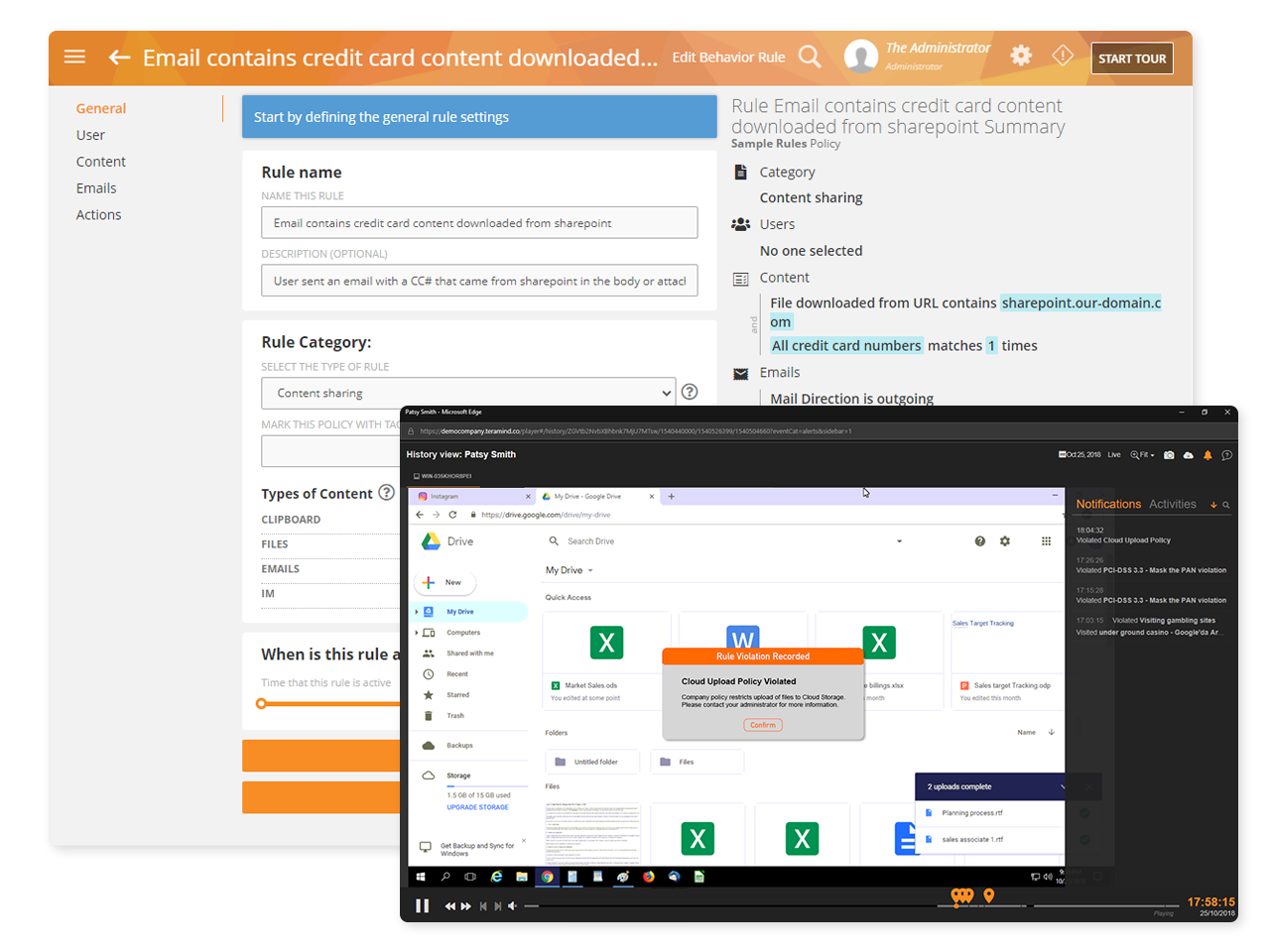
Privacy settings and configurations in user activity monitoring software like Teramind make it possible to collect detailed productivity and behavior analytics without monitoring, seeing or collecting personal data.
As a privacy-first organization, Teramind’s product suite including Teramind UAM includes customizable privacy options that provide ways for organizations to monitor activity relating to the organization while blocking personal information and activities from being monitored and collected.
As an organization that provides user activity monitoring, Teramind also employs its own software within its workforce. To do so, we rely on the privacy settings within the agent and full monitoring transparency with our employees in order to monitor for success and privacy. To find out more about our stance on privacy, visit Privacy with Teramind.
Let’s Get You Started
Secure data, manage compliance and get more done with
Teramind UAM










