Cyberhaven built its data loss prevention (DLP) platform around data lineage—i.e., tracking a file’s history to determine sensitivity and risk. The approach works, and for organizations that need that level of context, it’s proven effective.
But it’s also complex, expensive, and often overkill for teams that just need reliable data protection without the operational overhead.
The result is a growing number of security teams evaluating alternatives that deliver strong DLP without requiring dedicated analysts to manage the system or budgets that only enterprises can justify.
They want visibility into insider risk, enforcement that doesn’t slow users down, and deployment timelines measured in weeks.
This guide breaks down 13 alternatives, including what they do well, where they fall short, and which use cases they’re actually built for.
Why look for an alternative to Cyberhaven DLP?
While Cyberhaven solves data protection with deep context, it does come with some trade-offs that don’t work for every organization. Here’s what users consistently flag as friction points:
Policy configuration requires SQL knowledge
- Building custom policies in Cyberhaven isn’t intuitive — especially if you’re not familiar with complex conditional logic.
- Multiple users report that the filtering system works more like writing database queries than setting up straightforward rules, which means you can accidentally exclude data you meant to capture [*].
High false positive rates
- Early deployments generate loads of false positives that require continuous policy adjustments to get under control.
- Users report spending significant time tweaking rules to reduce noise, which delays time-to-value and pulls cybersecurity teams away from actual threat response [*].
Incomplete evidence capture and no native SIEM integration
- Cyberhaven doesn’t always capture 100% of the evidence you need, and when it does, finding it buried in data lineage trails is difficult.
- The platform doesn’t export logs in common SIEM formats, which means you can’t easily ingest Cyberhaven data into your existing security operations workflow [*].
AI detection limitations and steep learning curve
- Linea AI (the platform’s detection engine) still has accuracy gaps that require manual review to catch what it misses.
- The console UI isn’t intuitive, which adds another layer of learning curve on top of the already complex policy logic.
- Plus, integration issues compound the problem. For example, Outlook plugins are difficult to maintain, and the O365 cloud sensor can’t inspect attachments in emails [*].
Key features and functionalities to consider in Cyberhaven DLP alternatives
When evaluating alternatives, the aim isn’t to ‘replicate’ Cyberhaven’s data lineage model. Instead, it’s to find a solution that provides the protection you need without the operational complexity of Cyberhaven DLP.
Here are the capabilities that actually matter:
Native insider risk and behavior analytics
Cyberhaven’s DDR (data detection and response) model provides strong lineage tracking, but newer solutions expand that with user and entity behavior analytics (UEBA) to detect anomalies in human activity. These systems build behavioral baselines, flag deviations, and correlate them with data interactions to distinguish between careless mistakes and malicious intent.
Deep integration with your security ecosystem
Look for tools that integrate seamlessly with SIEM, SOAR, CASB, IAM, and collaboration platforms. Open APIs and prebuilt connectors allow you to automate incident response, streamline alerts, and enrich correlation across systems.
Cloud and SaaS application coverage
As organizations adopt SaaS and multi-cloud infrastructure, DLP must follow the data wherever it goes. Opt for alternatives that offer API-based monitoring and content inspection for platforms like Microsoft 365, Google Workspace, Slack, and Salesforce. This ensures consistent protection across both on-prem and cloud-based environments.
Streamlined policy creation and management
Consider platforms that simplify policy configuration with visual editors, templates, and guided workflows instead of complex query-based logic. This lets you build layered policies with natural-language rules and dynamic conditions.
Flexible reporting and forensic visibility
Prioritize DLP tools that include intuitive dashboards and advanced forensics, allowing analysts to trace every data interaction without navigating complex lineage graphs. Ensure they also support export in standard formats (e.g., JSON, syslog, CEF) for easy ingestion into SIEMs and analytics platforms.
Granular role-based access
Choose a Cyberhaven alternative that lets you define policies by department, geography, or data type, with clear role-based permissions. This ensures that each business unit has protection tailored to its data sensitivity level, without disrupting workflows or overwhelming users with unnecessary restrictions.
Recommended → The 10 Best Data Loss Prevention (DLP) Vendors for 2026
Top 13 Cyberhaven DLP alternatives on the market right now
| Tool | Best For | Key Differentiator | Starts At | Free Trial |
| Teramind | Organizations needing behavioral analytics and visual forensics for insider threat detection | Screen recording, OCR and user behavior analytics in one platform | $15/user/month | Yes |
| Forcepoint DLP | Large enterprises requiring risk-adaptive protection across all channels | Dynamic enforcement based on real-time user risk scoring | Custom pricing | Contact vendor |
| Fortra’s Digital Guardian | Data-rich organizations in regulated industries needing deep visibility with flexible enforcement | Data-aware protection with Analytics & Reporting Cloud (ARC) that filters noise and surfaces high-fidelity threats | Custom pricing | Contact vendor |
| Mimecast Incydr | Distributed workforces and cloud-first companies needing rapid deployment | Lightweight, file-exfiltration focused with pre-configured policies | Custom pricing | Yes |
| Broadcom Symantec DLP | Complex enterprises needing mature, comprehensive DLP across heterogeneous environments | Exact Data Matching (EDM) and the deepest feature set with 15+ years of development | Custom pricing | Contact vendor |
| DTEX | High-security environments prioritizing insider intent detection with privacy compliance | Metadata-only collection with sentiment analysis and emotional risk indicators | Custom pricing | Contact vendor |
| Microsoft Purview DLP | Microsoft 365-centric organizations wanting native integration | Seamless M365 integration with no additional agents required | Included in E5 licenses | Yes (via M365 trial) |
| Nightfall | SaaS-heavy organizations needing API-based cloud DLP | Pure-play cloud DLP with developer-first approach and secrets detection | Custom pricing | Yes |
| Netwrix Endpoint Protector | Organizations prioritizing device control and USB security across all OS platforms | Cross-platform (Windows/Mac/Linux) with granular device management | Custom pricing | Yes |
| Proofpoint Enterprise DLP | Enterprises facing advanced threats needing email-centric DLP with threat intelligence | Email DLP integrated with BEC protection and threat correlation | Custom pricing | Contact vendor |
| Trellix DLP | Large enterprises requiring centralized policy management at massive scale | Registered Document Protection (RDP) and unified management across all channels | Custom pricing | Contact vendor |
| Cisco Umbrella DLP | Distributed workforces needing cloud-delivered, location-agnostic protection | SASE-integrated DLP with DNS-layer security and zero trust architecture | Custom pricing | Yes (available via Umbrella free trials) |
| Zscaler DLP | Cloud-first organizations implementing zero trust with a global workforce | Zero Trust Exchange with inline inspection and identity-aware policies | Custom pricing | Contact vendor |
1. Teramind DLP
Teramind operates as a unified DLP, employee monitoring, and insider threat prevention platform. It combines user activity monitoring, behavioral analytics, and real-time DLP into a single system.
Unlike Cyberhaven’s data lineage approach, Teramind focuses on user behavior as the primary signal for detecting risk. It tracks what employees are doing, why they’re doing it, and whether those actions indicate malicious intent, negligence, or policy violations.
The platform captures granular activity data across endpoints, applications, websites, and cloud services, then uses that visibility to enforce DLP policies, detect insider threats, and provide visual forensic evidence when incidents occur.
Key features
- Endpoint DLP controls: Teramind monitors and controls USB transfers, clipboard activity, document printing, and unauthorized sharing to block risky data exfiltration methods right at the source.
- Live view & historical playback: Security and IT teams can watch live user sessions or replay historical activity to reconstruct how a data leak or policy violation occurred.
- OCR-enhanced content detection: Optical Character Recognition (OCR) allows Teramind to extract and inspect text from images, screenshots, and video frames. This enables the detection of sensitive data even when it isn’t in traditional text formats.
- Automated policy and response rules: With a flexible rules engine, Teramind lets you define actions such as blocking actions, logging events, locking sessions, or notifying administrators.
- User risk scoring: Using machine learning and statistical models, Teramind applies insider threat analytics and generates risk scores based on deviations from normal behavior.
What are real users saying about Teramind DLP?
- “Its intuitive interface and comprehensive monitoring capabilities make it easy to track and analyze user activity effectively. The real-time alerts and detailed reports help quickly identify risks and ensure compliance, enhancing overall security.” (Read full review).
- “Teramind can be drilled right down to the second of what an employee is doing. You can watch live feed, recorded feed, set up analytics to compare quickly and many other things. The customer support has been wonderful and any issues are taken care of within 24 hours.” (Read full review).
- “One of the most valuable aspects of Teramind is its behavior alerts and customizable policies. These tools allow us to monitor communications, track potentially risky behavior, and understand overall employee sentiment.” (Read full review).
Thinking of switching to Teramind DLP? See how Arrivia stopped an insider data theft ring with Teramind.
2. Forcepoint DLP
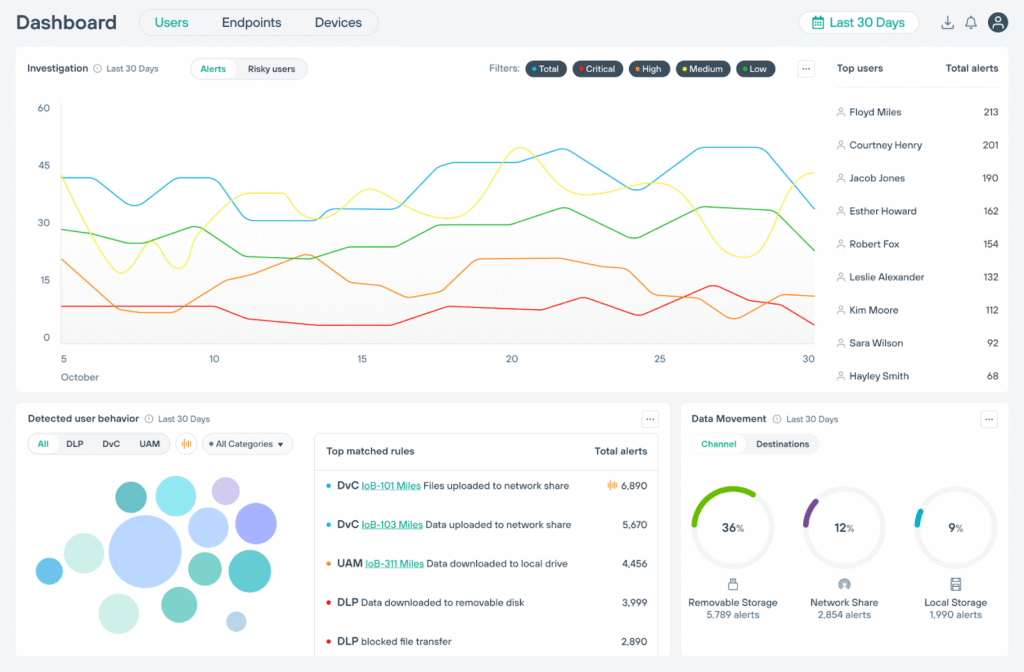
Forcepoint DLP helps organizations discover, classify, monitor, and protect sensitive information across hybrid and cloud environments.
It provides centralized visibility and enforcement for data at rest, in motion, and in use. This includes endpoints, web and network traffic, email communications, and cloud applications.
Key features
- Risk-adaptive protection engine: Uses behavioral analysis to contextualize user actions and dynamically adjust enforcement. Security policies evolve based on user role, device, location, and risk patterns.
- AI-powered data classification: With 1,700+ pre-defined classifiers, policy templates, and machine learning models, Forcepoint can accurately identify and categorize structured and unstructured data (PII, PCI, PHI, IP, and more), even across diverse content formats.
- Centralized policy management: Admins can define, deploy, and manage data protection policies from a single console.
Pros
- “Especially if you are using Forcepoint Proxy, I definitely recommend you to use it. The integration process is as simple and fast as possible, briefly 2 keys.” (Read full review).
Cons
- “I wouldn’t say I like its document part because if I read the documentation for the 1st time installation, I could not understand anything. I got stuck. And I felt difficulty in learning the force point Data Loss Prevention.” (Read full review).
Related → Forcepoint Insider Threat: Features, Pros, Cons & Alternatives
3. Fortra’s Digital Guardian
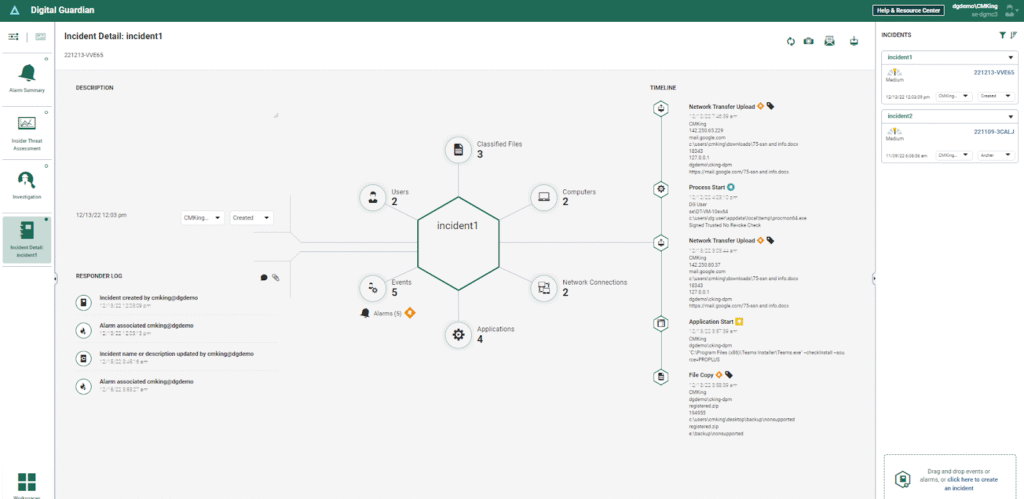
Fortra’s Digital Guardian is a comprehensive DLP and insider risk management platform that protects sensitive information at the endpoint, across networks, and into cloud environments.
It focuses on data context and control, continuously identifying valuable data, tracking how it flows, and enforcing protection policies wherever that data lives or moves.
Key features
- Classification engine: Tags and categorizes data based on content and context (keywords, patterns, and user behavior), allowing precise identification of sensitive assets such as IP, PII, PHI, and proprietary business data.
- Endpoint-embedded DLP sensors: Deploys lightweight, persistent sensors on endpoints (Windows, macOS, Linux) that continuously monitor file interactions.
- Unified endpoint and network monitoring: Correlates local device activity with network transactions to ensure that data moving off the endpoint (to websites, cloud apps, or external devices) adheres to policy.
Pros
- “The cross-platform endpoint coverage, including Windows, macOS, and Linux, is a strong feature.” (Read full review).
Cons
- “Takes time to learn and get it useful, many knowledge need to be used to control the product (mssql, IIS application…). Policy creation is way too complicated/ hard to use with the beginner.” (Read full review).
Related → 12 Fortra Alternatives (formerly Digital Guardian) for 2026
4. Mimecast Incydr
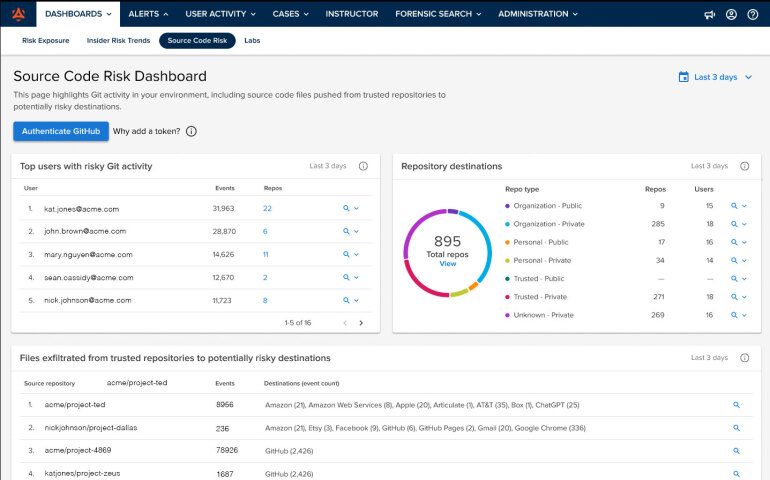
Mimecast Incydr is a SaaS-native insider risk management (IRM) platform designed specifically for modern, cloud-first work environments where employees collaborate across devices, applications, and locations.
Key features
- Lightweight endpoint agent: A minimal-footprint agent that monitors file activity on Windows, macOS, and Linux endpoints without impacting system performance or requiring VPN connectivity. The agent tracks file events locally and syncs telemetry to Incydr’s cloud backend.
- Integration with SIEM and case management: Native integrations with security operations tools like Splunk, Elastic, Microsoft Sentinel, ServiceNow, Jira, Slack—that push Incydr alerts into existing security workflows.
- Departing employee monitoring: Specialized detection for employees who’ve given notice, been terminated, or are exhibiting departure risk signals.
Pros
- “Continuous database monitoring is done with this software more effectively. I make many backups with a single account, to have everything stored in one place.” (Read full review).
Cons
- “Sometimes it will lag on whatever work I’m currently performing whilst it does its schedule backup. I also feel their customer support system and FAQ not very easily accessible when needed.” (Read full review).
Related → Mimecast Incydr vs. Cyberhaven: The 2025 Showdown
5. Symantec DLP (Broadcom)
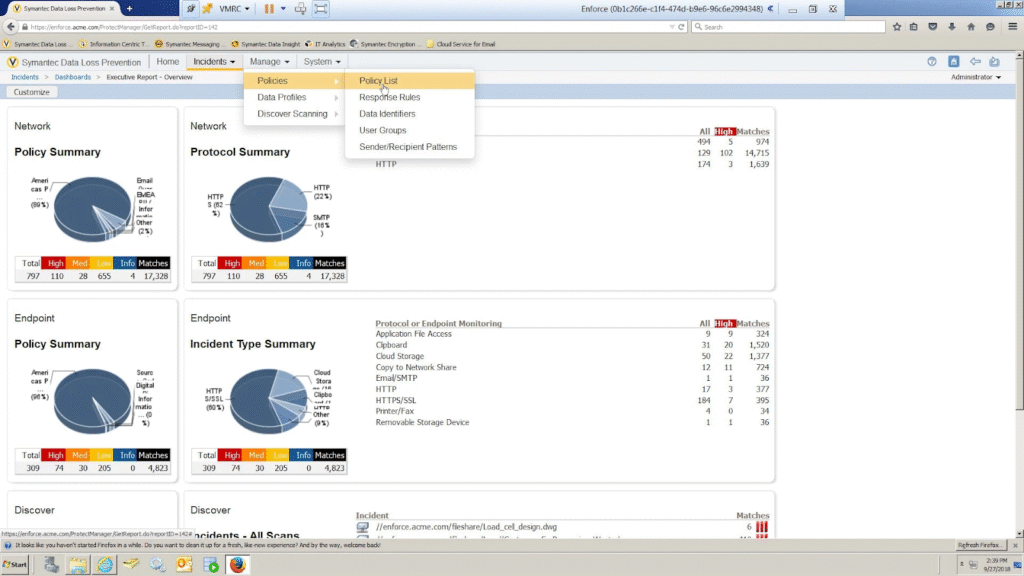
Symantec DLP helps organizations discover, monitor, and protect sensitive data across endpoints, networks, cloud environments, and storage systems.
Its biggest advantage is its broad channel coverage and deep inspection of data in motion, at rest, and in use, making it a longstanding choice for large enterprises and regulated industries with complex data protection needs.
Key features
- Exact Data Matching (EDM): A fingerprinting technology that creates hashes of structured data from databases or spreadsheets (customer lists, employee records, financial data). Then it uses those hashes to detect when that exact data appears anywhere in the environment, even if it’s been copied, reformatted, or embedded in other documents.
- Indexed Document Matching (IDM): Content fingerprinting that creates digital signatures of entire documents or document sections, allowing Symantec to recognize those documents.
- Network DLP with deep packet inspection: Inline network monitoring that inspects data moving across the corporate network in real-time (e.g., email traffic, web uploads, FTP transfers, etc.) and enforces policies before data leaves the organization.
Pros
- “This solution offers comprehensive data protection for endpoints, networks, and the cloud, and I appreciate its thorough content inspection capabilities.” (Read full review).
Cons
- “It tends to generate a high number of false positives, which means it requires considerable tuning to function effectively.” (Read full review).
6. DTEX
DTEX is a behavior-focused insider risk management platform that prioritizes user intent detection over traditional data classification and policy enforcement.
It identifies users who are exfiltrating data because they’re disgruntled, preparing to leave, or have been compromised, then provides security teams with the context needed to intervene before damage occurs.
Key features
- Workforce cyber intelligence: Establishes baseline activity profiles for each user and then flags deviations that indicate risk.
- Ai3 risk assistant: Leverages generative AI to guide analysts through complex threat investigations. It provides contextual, natural-language insights into who did what, why, and how.
- Lightweight, scalable architecture: DTEX’s telemetry collection uses minimal endpoint resources (typically 3-5MB of data per user per day and <1% CPU), enabling enterprise-wide deployment.
Pros
- “The custom correlation rules are a huge benefit to targeting specific behaviour of employees.” (Read full review).
Cons
- “There are some issues with device ID replication that makes it difficult to create long term custom groups for testing or monitoring.” (Read full review).
Related → DTEX vs Teramind: Which Insider Risk Solution Is Best?
7. Microsoft Purview DLP
Microsoft Purview DLP is the native data loss prevention solution embedded within Microsoft’s broader information protection and compliance ecosystem.
It provides integrated data protection across the Microsoft 365 suite including Exchange Online, SharePoint, OneDrive, Teams, Outlook, Edge browser, and Windows endpoints.
For organizations already invested in Microsoft’s cloud infrastructure, Purview offers the advantage of seamless integration without requiring third-party agents, separate consoles, or complex deployments.
Policies created in Purview automatically apply across all Microsoft services, and the platform leverages Microsoft’s extensive cloud intelligence and threat data to detect sensitive information and risky sharing behaviors at scale.
Key features
- Sensitive Information Types (SITs) library: A pre-built catalog of over 200 data classifiers that recognize common sensitive data patterns (e.g., Social Security numbers, credit card numbers, passport IDs, HIPAA codes, etc.).
- Inline protection: When users attempt to share or transfer sensitive data—whether via email, Teams chat, file uploads, or endpoint transfers, Purview DLP can block actions, warn the user, or require justification.
- Endpoint DLP across Windows and macOS: Extends protection to local devices, monitoring and enforcing policies for sensitive items stored on Windows (10/11) and macOS systems.
Pros
- “MS DLP is very useful to secure our compliance data. It helps us to detect various type of private data across various workloads and we can block or monitor those data as per our requirement.” (Read full review).
Cons
- “After complex builder logic, it don’t provide an option to update multiple rules through powershell, which makes our job lengthy if we want to update multiple rules.” (Read full review).
8. Nightfall
Nightfall is a cloud-native DLP platform built specifically for SaaS apps and modern collaboration tools.
It provides API-based data protection across platforms like Slack, Microsoft Teams, Google Workspace, GitHub, Jira, Confluence, Salesforce, and dozens of other cloud services.
Key features
- API-native cloud DLP across 50+ SaaS applications: Nightfall connects directly to applications via OAuth or API keys, then continuously monitors messages, files, code repositories, tickets, wikis, and shared documents for sensitive data.
- GenAI detectors: Uses advanced machine learning and generative AI models built on 125 million parameters to identify sensitive data (PII, PHI, PCI, API keys, and secrets).
- Generative AI protection: Nightfall includes dedicated controls to prevent sensitive data from being processed by unauthorized AI tools or leaked through AI workflows.
Pros
- “I appreciate how Nightfall AI reduces noise by significantly cutting down on false positives, which in turn allows our security team to focus on true positives.” (Read full review).
Cons
- “Some of the advanced capabilities still require an agent.The dashboard and reporting has limited customization capabilities.” (Read full review).
9. Netwrix Endpoint Protector
Netwrix Endpoint Protector is a cross-platform DLP solution focused on securing data at the endpoint level across Windows, macOS, and Linux devices.
The platform takes a device-control-first approach to data protection. It granularly manages what users can do with USB drives, external hard drives, printers, Bluetooth devices, mobile phones, and other hardware that connects to endpoints.
Key features
- File tracing and audit trails: Detailed logging of all file activity on endpoints including which files were accessed, copied, modified, deleted, uploaded, emailed, printed, or transferred to removable media.
- Incident response: Provides detailed logs, alerting workflows, and analytics dashboards that give security teams visibility into policy violations, user behavior trends, and risk patterns.
- Offline device control: Device control policies are cached locally on endpoints and enforced by the agent without requiring constant connectivity to management servers.
Pros
- “It works smoothly across Windows, Linux, and macOS, and the setup was super quick. The console is easy to use, policies are clear, and device control are actually does what it should do.” (Read full review).
Cons
- “Linux agents do not appear on the console, so administrators must reach out to Netwrix support whenever a Linux agent is required.” (Read full review).
10. Proofpoint Enterprise DLP
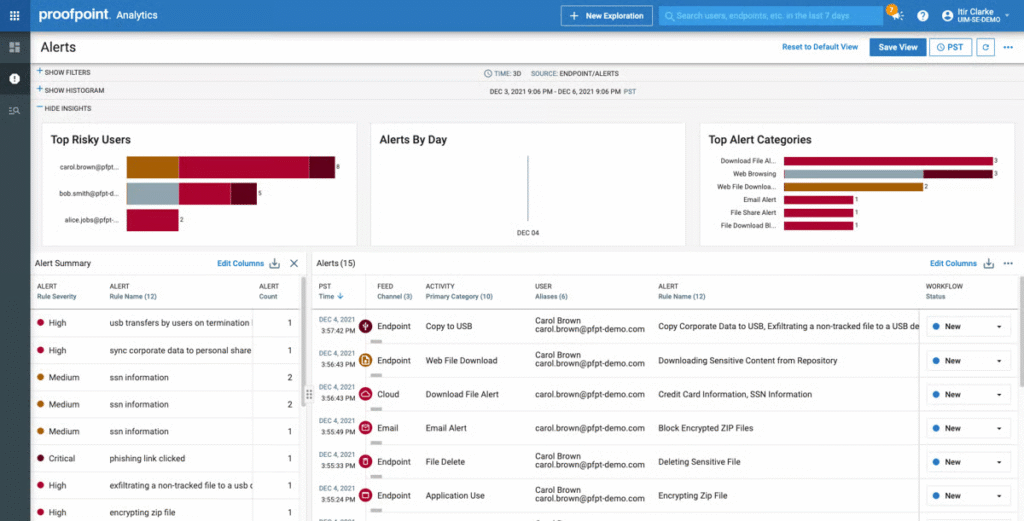
Proofpoint Enterprise DLP is a people-centric solution that helps organizations discover, classify, monitor, and prevent sensitive data exposure across email, cloud applications, endpoints, and collaboration tools.
It’s built on a cloud-native architecture with tight integration into the broader Proofpoint security ecosystem (including email security and threat telemetry).
Key features
- People-centric risk analytics: Correlates content telemetry with user behavior and threat context in a unified timeline view. This helps analysts distinguish between normal actions and true risk events — e.g., compromised accounts versus accidental leaks.
- Comprehensive multi-channel coverage: Protects sensitive data across email, cloud services (like Microsoft 365 or Google Workspace), endpoints, and web applications.
- Advanced content classification and inspection: Includes exact data matching, fingerprinting, and AI-augmented classification. This enables precise identification of structured and unstructured sensitive information even across varied formats (e.g., documents, spreadsheets, chat messages).
Pros
- “What I like best about Proofpoint Enterprise Data Loss Prevention (DLP) is its ability to accurately identify and prevent sensitive data from being shared or leaked, both inside and outside the organization.” (Read full review).
Cons
- “The initial cost is quite big and its hard to setup. Also if you are doing this with a 3rd party company there is also the worry what they are doing with your data and how valuable are they for so called “scams” and potential data loss.” (Read full review).
Related → The 8 Best Proofpoint Competitors & Alternatives in 2026
11. Trellix Data Loss Prevention (Formerly McAfee DLP)
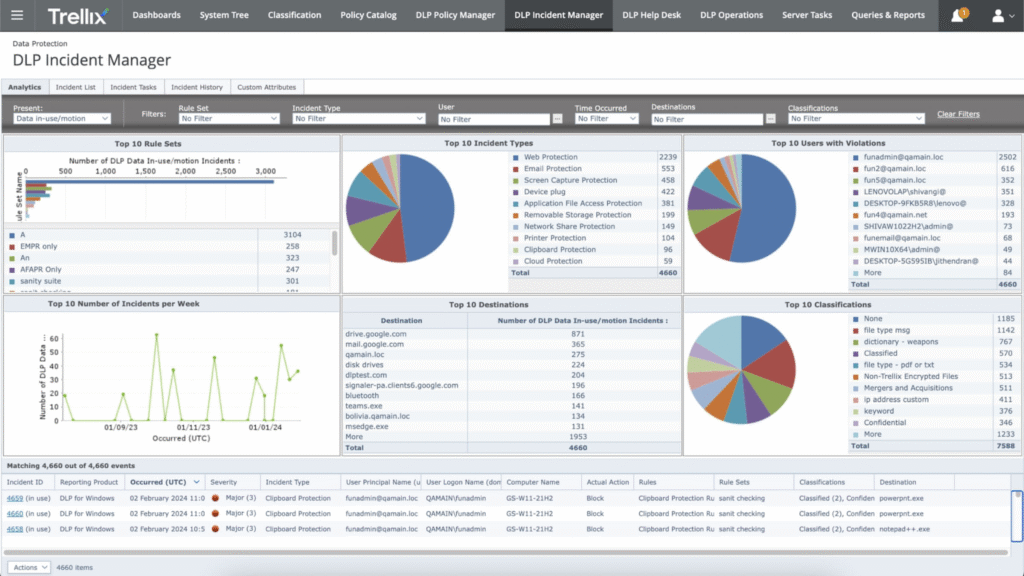
Trellix DLP is an enterprise-grade data protection solution designed to detect, prevent, and remediate sensitive data exposure across endpoints, networks, email, cloud applications, and storage environments.
It combines deep content inspection, robust classification, and centralized policy management to help organizations enforce consistent protection controls and comply with regulatory mandates.
Key features
- Enterprise-scale endpoint DLP agents: Lightweight agents deployed on Windows and select operating systems monitor local data interactions, enforcing policies even when devices are offline or outside the corporate network.
- Network and gateway DLP enforcement: Integrated network controls monitor data in motion (e.g., scanning HTTP/HTTPS traffic) to block or manage sensitive data transfers in real time.
- Incident triage and response workflows: Security teams can define automated responses (block, quarantine, notify, encrypt, or require user justification) and configure structured workflows for analysts to investigate and resolve incidents efficiently.
Pros
- “It is especially effective at monitoring and blocking any attempts to exfiltrate sensitive information from your company.” (Read full review).
Cons
- “I’ve noticed some performance degradation, such as slowed internet speed and blocking some websites which are needed for our operations.” (Read full review).
Related → Proofpoint DLP vs. Trellix DLP: The 2025 Showdown
12. Cisco Umbrella DLP
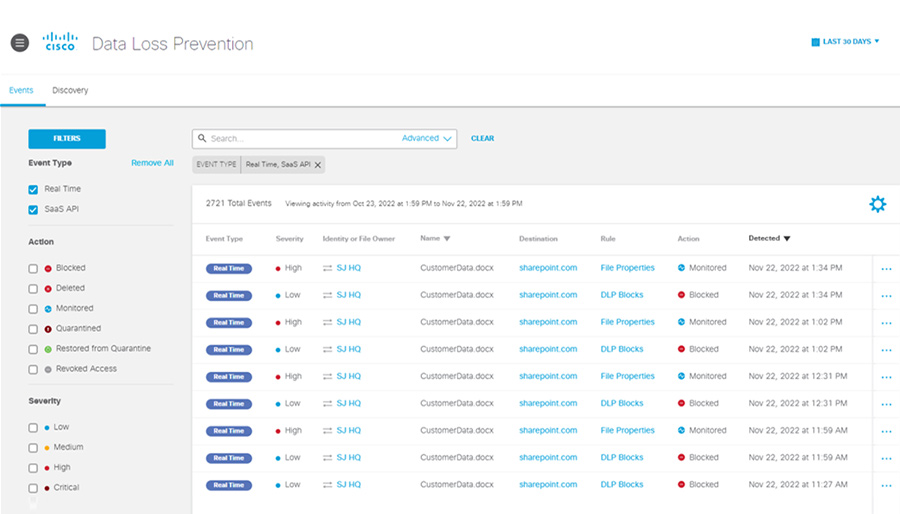
Cisco Umbrella DLP is a cloud-delivered data loss prevention solution integrated into Cisco’s broader Secure Access Service Edge (SASE) architecture, providing data protection as part of a unified platform that combines secure web gateway, DNS security, cloud firewall, and zero trust network access.
Key features
- Multimode cloud DLP (inline + API scanning): Umbrella supports both in-line inspection of outbound web traffic and API-based scanning of cloud app content.
- Cloud-native policy enforcement: With a cloud-first architecture, Umbrella DLP scales elastically and integrates natively with secure web gateway capabilities to enforce granular policies without on-premises hardware.
- Extensive pre-built data identifiers: The platform offers 80+ pre-built dictionaries for common sensitive information types (e.g., PII, financial data, healthcare records, etc.) with support for customizable identifiers tailored to your organization’s data classifications.
Pros
- “Implemented Cisco Umbrella as our de-facto DNS security solution for outbound internet traffic. Saw immediate wins, by seeing drastic reduction in number of the DNS requests towards crypto mining sites, CnC sites.” (Read full review).
Cons
- “Cisco Umbrella can be relatively expensive for smaller organizations, especially when scaling across many users.” (Read full review).
13. Zscaler DLP
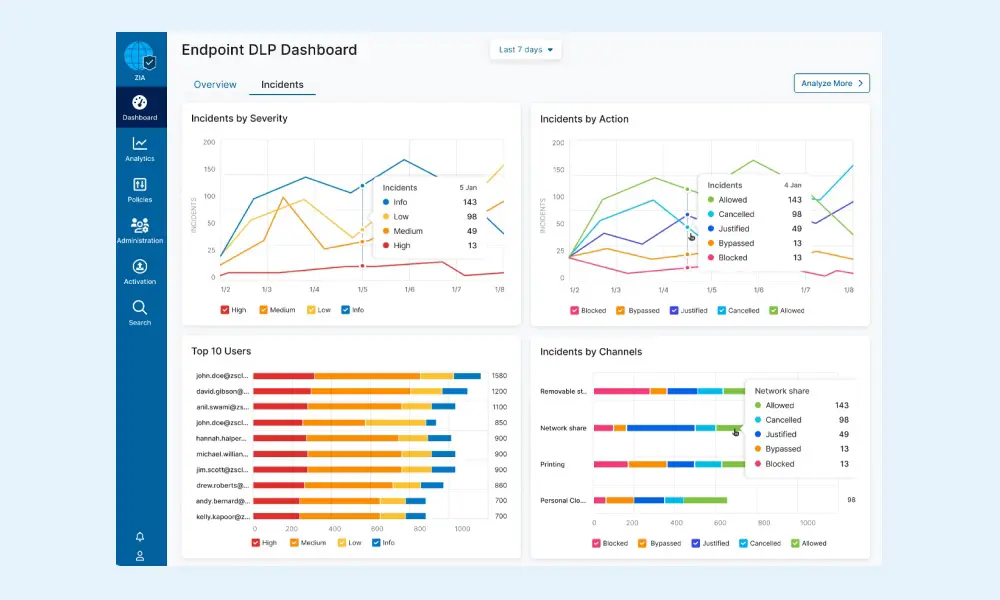
Zscaler DLP is a cloud-native data loss prevention solution built into Zscaler’s Zero Trust Exchange platform. It inspects data inline through its global security cloud, enabling real-time enforcement of data protection policies without adding network complexity.
Key features
- Centralized policy enforcement: Security teams can create and manage consistent DLP policies from a central console that apply identically across all data channels.
- AI-powered data discovery: Zscaler automatically discovers and classifies sensitive data in motion and at rest. This reduces manual configuration and improves detection accuracy for regulated data types like PII, PHI, financial records, and intellectual property.
- Optical Character Recognition (OCR): Zscaler can extract and classify sensitive text from images (e.g., scanned documents, screenshots).
Pros
- “It provides the safety and ease of mind for our networks and provide safe access to company resources online.” (Read full review).
Cons
- “Policy tuning is required, and performance issues can be observed in some cases.” (Read full review).
Teramind: The #1 Alternative to Cyberhaven
Cyberhaven promised you data lineage. It tracks every file transformation, historical touch, and basically every piece of context. What you got was complexity that requires dedicated analysts and false positives that bury your security team.
Teramind takes a different approach, focusing on the user instead of the file.
It monitors user behavior—i.e., what employees are doing, how they’re doing it, and whether those actions indicate malicious intent, negligence, or compromise.
For example, when someone exhibits departure risk signals, accesses data outside their role, or attempts to exfiltrate files, Teramind logs it. It records their screen, captures OCR from screenshots, scores their risk in real-time, and can block the action before damage occurs.
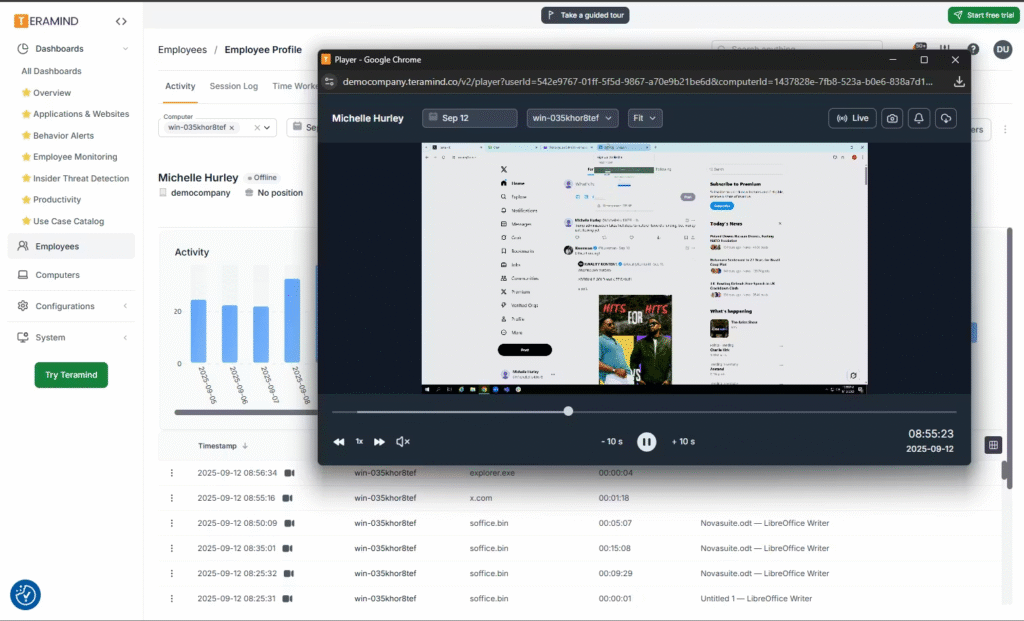
If Cyberhaven’s complexity is slowing you down and its cost is squeezing your budget, Teramind delivers the protection you actually need. See Teramind in Action →


