Secure & Privacy-Focused Employee Monitoring Software
Teramind’s #1 rated employee monitoring software helps companies track work time, enhance team productivity, and secure sensitive data while respecting privacy for both in-office and remote workers.
Trusted by 10,000+ organizations to improve productivity, security, compliance, and workforce analytics









Why Choose Teramind for Employee Monitoring
Real-Time Monitoring
Track employee activity and computer usage across Windows and Mac devices with minimal performance impact. Our user-friendly monitoring tools provide real-time insights into employee behavior, including screenshots, screen recordings, keystrokes, and app usage, allowing managers to make informed decisions.
Productivity Optimization
Improve workplace efficiency with employee productivity tracking that identifies bottlenecks and streamlines workflows. Teramind helps measure productivity levels, recognize top performers, and implement targeted coaching through detailed reports on work hours, idle time, and active time.
Risk Mitigation
Protect your organization from insider threats and data breaches with behavior analytics. Our employee monitoring system detects suspicious activities, unauthorized access to sensitive data, and potential security issues before they escalate.
Invisible Barriers to Business Intelligence? We Make Them Visible
Our employee tracking software integrates with your existing infrastructure to deliver actionable data that improves productivity and security for employees.
Activity Monitoring
Monitor and analyze how employees work through user activity tracking.
Screen Monitoring: Capture irrefutable screen recordings and screenshots that provide context for employee computer activity.
Application Usage: Track which apps employees use, for how long, and identify unauthorized software that could pose security risks to your work environment.
Keystroke Logging: Monitor keyboard input in sensitive applications to protect against data exfiltration and strengthen data security.

Privacy-Focused Monitoring
Balance effective oversight with employee trust through responsible employee monitoring tools.
Transparent Policies: Create clear monitoring guidelines for remote employees and freelancers that build trust through open communication.
Selective Monitoring: Target only work-relevant activities during work hours rather than implementing blanket surveillance of personal time.
Data Minimization: Teramind collects only necessary information with appropriate retention periods to respect employee privacy while meeting business needs.
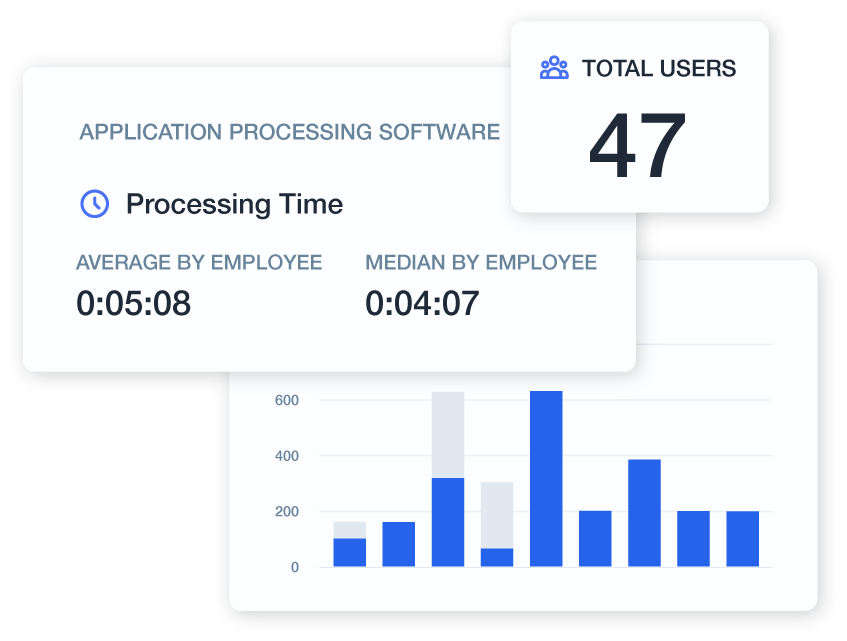
Website & Application Tracking
Gain visibility into how your team members use online resources and applications.
URL Filtering: Categorize and control website access and social media usage based on productivity impact with customizable policies.
Content Analysis: Evaluate the content of websites visited to identify potential policy violations without compromising employee privacy.
Time Distribution: Measure work time spent on business-critical versus non-productive applications with detailed breakdowns by department and individual.
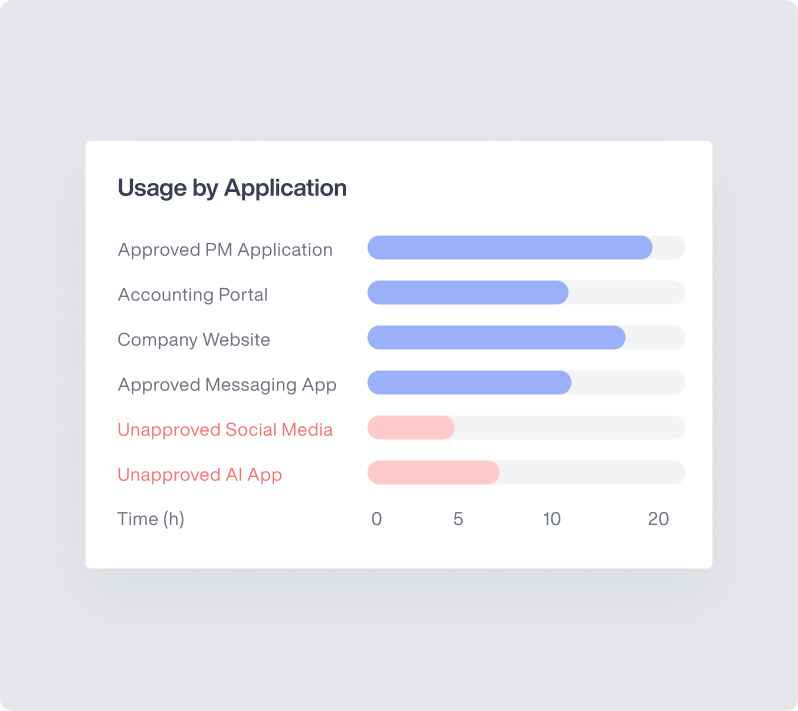
Productivity Analysis & Optimization
Transform activity data into actionable insights that drive employee performance improvements.
Work Habits: Identify optimal productivity periods and potential burnout indicators through analysis of daily and weekly work patterns.
Project Management: Integrate with productivity platforms like Jira, Zendesk, Redmine, and more to accurately measure effort and optimize resource allocation across remote teams.
Idle Time Analysis: Distinguish between productive breaks and excessive downtime to support healthy work habits while addressing team productivity concerns.
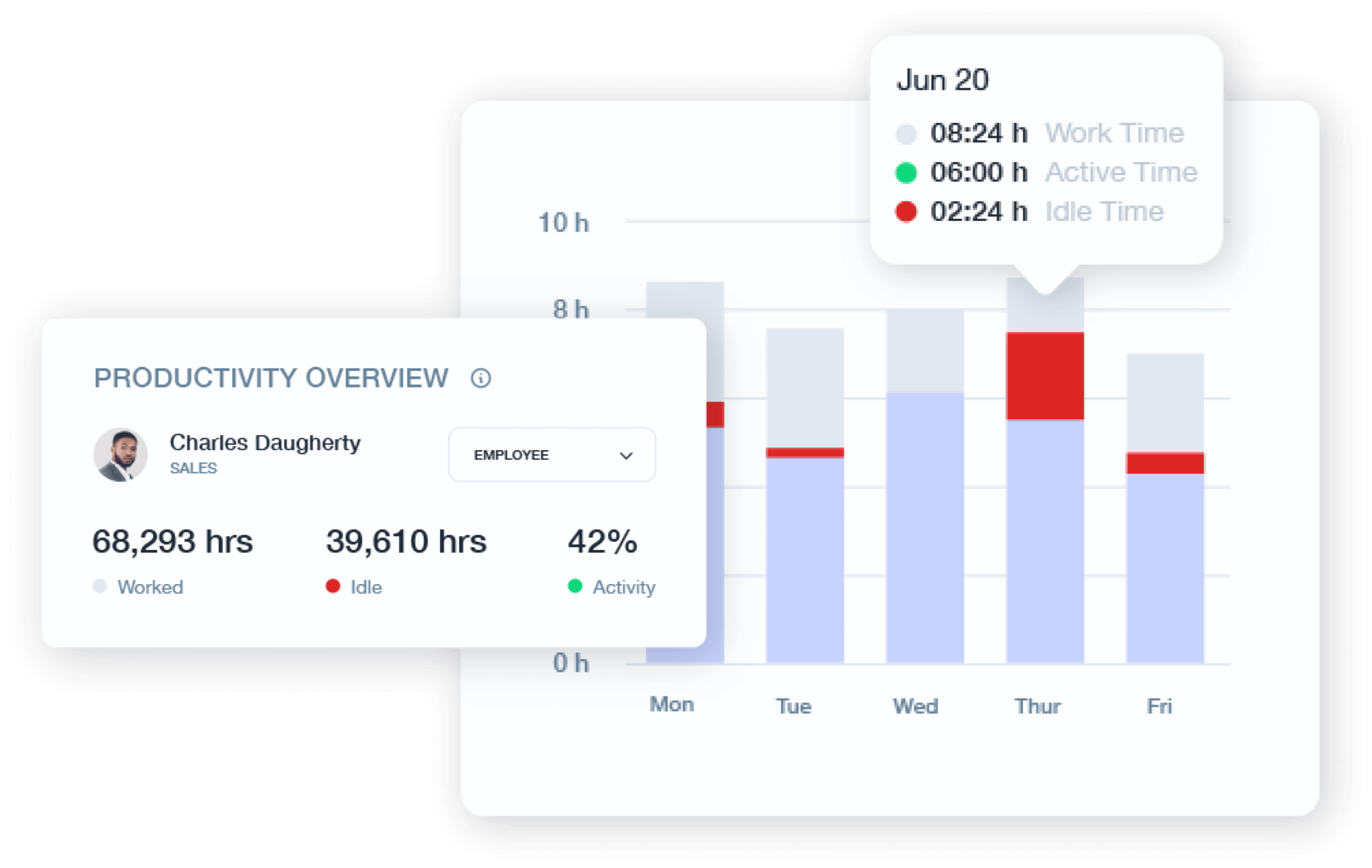
Insider Threat Detection
Protect your most valuable assets from intentional and accidental insider threats.
Behavioral Anomalies: Establish baseline behavior patterns and receive notifications when unusual activities occur that may indicate compromise.
Behavioral Data Loss Prevention: Monitor file transfers, email attachments, and clipboard activities to prevent unauthorized data exfiltration attempts.
Access Control: Verify appropriate resource usage based on role-specific permissions and detect potential privilege escalation attempts.
Customizable Reporting
Deliver targeted insights to stakeholders with flexible productivity reports and timesheets.
Executive Dashboards: Provide leadership with high-level metrics on productivity tracking, risk indicators, and compliance status through intuitive visualizations.
Team Performance: Benchmark department performance to identify best practices and opportunities for cross-functional improvements.
Compliance Documentation: Generate detailed activity reports that satisfy regulatory requirements while demonstrating due diligence in monitoring practices.
AI-Powered Alerts
OMNI is Teramind’s new rapid interface, an AI-powered alert system that shows you more of what you want to see – and less of what you don’t.
See data-related alerts grouped together in a news feed so you can quickly see trends. Click to see more directly from your dashboard and get ahead of potential threats.
Teramind's Employee Monitoring Tools
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Screen & Audio Recording
Monitor employee screens in real-time or record them for irrefutable evidence. Optionally, record audio input/output too.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix/Session Hosts Monitoring
Monitor employee activity within Citrix, terminal servers, RDP or virtual environments. Track application usage and ensure data security with specialized monitoring on your endpoints.
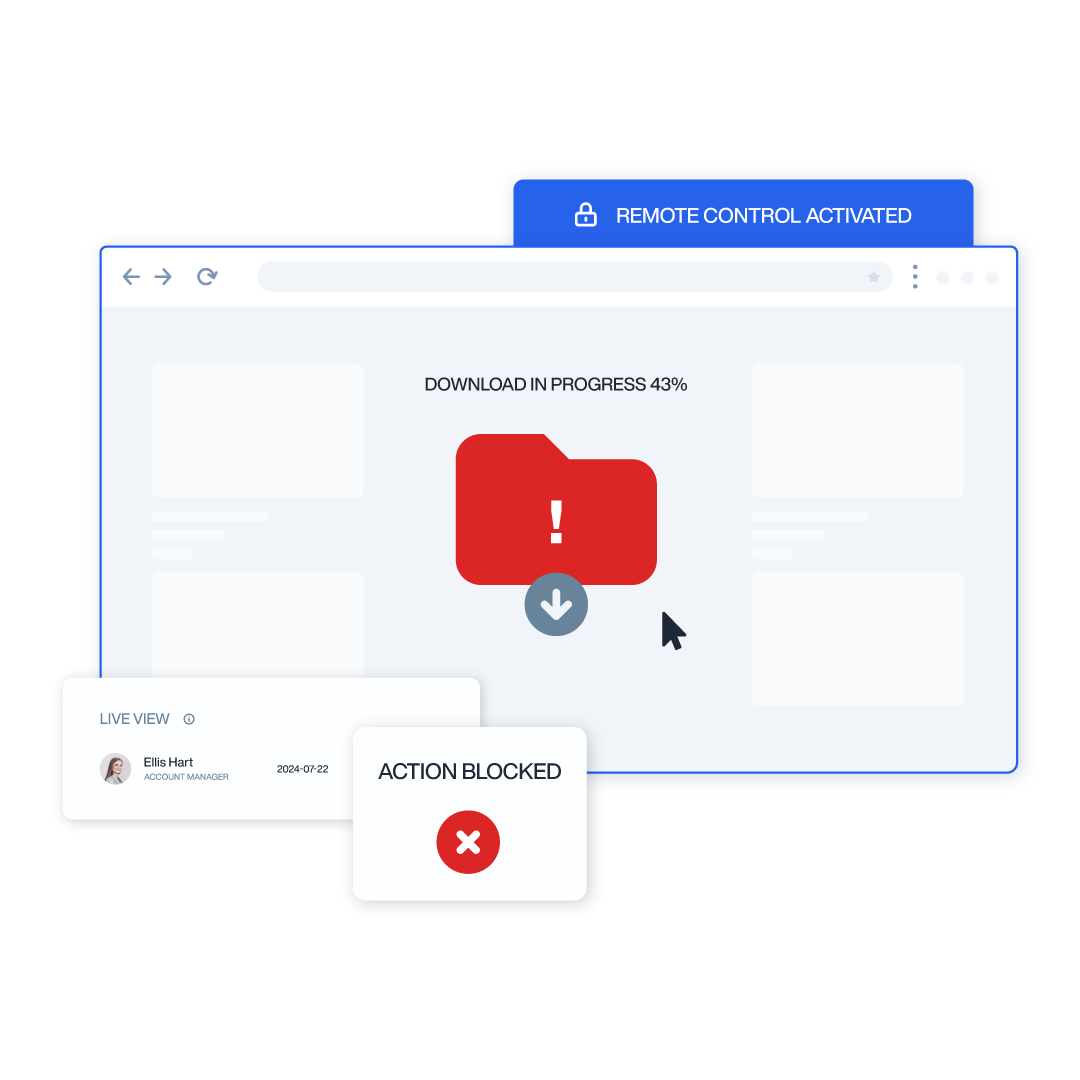
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Try a Live Demo
of Teramind
Interact with a live deployment of Teramind
to see how our platform works.

| Feature/Aspect | TERAMIND | ActivTrak | Hubstaff | Insightful | Monitask |
|---|---|---|---|---|---|
| Software Overview | |||||
| Primary Focus | All-in-one comprehensive solution | Workforce analytics | Time tracking focus | Productivity insights | Simple monitoring |
| Best For | All businesses | Mid-size teams | Field & remote teams | Office & hybrid teams | Small businesses |
| Pricing & Plans | |||||
| Starting Price | $14.00 /user/mo | $10.00 /user/mo | $4.99 /user/mo | $6.40 /user/mo | $4.99 /user/mo |
| Free Plan | 14-day trial | Up to 3 users | 30-day trial | 7-day trial | 10-day trial |
| Monitoring Capabilities | |||||
| Privacy Features | Fully customizable controls | Transparent only | Basic settings | Customizable | Limited controls |
| Keystroke Logging | Full keylogging | Not available | Limited | Not available | Not available |
| Screen Recording | Full video recording | Not available | Not available | Live screen viewing | Not available |
| Email Monitoring | Full email tracking | Not available | Not available | Not available | Not available |
| File Transfer Tracking | USB, network, cloud | Not available | Not available | Limited | Not available |
| Security & Compliance | |||||
| Insider Threat Detection | AI-powered UEBA | Not available | Basic alerts | Basic monitoring | Not available |
| OCR Capabilities | Real-time OCR | Not available | Not available | Not available | Not available |
| Compliance Support | GDPR, HIPAA, PCI, SOX | GDPR, SOC 2 | GDPR, CCPA | GDPR, SOC 2 | Basic GDPR |
| Productivity Management | |||||
| Idle Time Detection | Advanced detection | Smart idle tracking | Keyboard/mouse based | Customizable | Basic detection |
| Time Tracking | Automatic & Manual | Automatic only | Robust | Automatic & Manual | Automatic & Manual |
| Technical Specifications | |||||
| Platform Support | Win, Mac, Citrix, VMware | Win, Mac, Linux | Win, Mac, Linux, Chrome | Win, Mac | Win, Mac, Linux |
