For many security teams, choosing Trellix (formerly McAfee Enterprise) made a lot of sense at the time. It came with a strong legacy in data loss prevention, broad endpoint coverage, and the promise of enterprise-grade control over sensitive data.
For organizations operating in regulated environments, that level of visibility and enforcement was often non-negotiable.
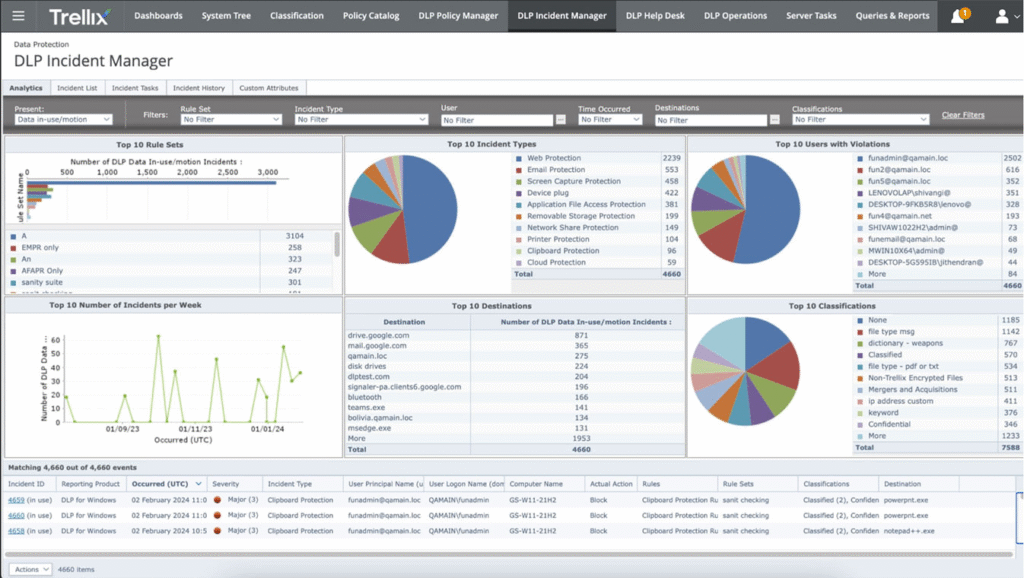
But the way data moves, and the way risk shows up has changed significantly. Insider risk for one has moved beyond files and now extends to the network perimeter.
Now, you have employees working remotely, cloud apps syncing constantly, and subtle behavior patterns that traditional DLP tools weren’t designed to surface. In that environment, many teams are finding that Trellix’s DLP approach can feel heavy, complex to tune, and slow to adapt to modern workflows.
This doesn’t mean Trellix is “bad” software. It means that what organizations need from a DLP platform in 2026 looks very different from what DLP was originally built to do.
That’s why more teams are exploring alternatives. In this guide, we break down the top Trellix DLP competitors to consider in 2026, focusing on solutions that reflect how data risk actually manifests today—and how modern security teams prefer to manage it.
Why Look for an Alternative to Trellix Data Loss Prevention?
The decision to explore alternatives rarely comes from one catastrophic failure. Instead, it comes from day-to-day friction. The small but persistent challenges that slow teams down, complicate compliance, or reduce confidence in alerts over time.
Based on real user feedback, here are five of the most common reasons companies begin reassessing Trellix DLP.
Evidence handling and storage can complicate compliance
One recurring concern is how DLP incident evidence is stored and managed, particularly in Trellix’s SaaS deployments that rely on third-party storage providers.
While this model may simplify infrastructure, it can introduce uncertainty around where sensitive evidence lives and how it’s governed [*].
Complex configuration
Trellix DLP is powerful, but many end users report that unlocking that power requires significant time, expertise, and tuning.
Initial configuration can be complex, and meaningful results often depend on extensive policy customization. This complexity slows deployment, increases reliance on specialized resources, and makes day-to-day management harder than expected.
For smaller teams (or teams without dedicated DLP specialists) the cost of ownership can quickly feel unjustified to the value delivered [*].
High false positives
Another common frustration is the volume of false positives during early deployment. Users frequently note that substantial tuning is required before policies produce reliable signals.
While tuning is expected with any DLP solution, the effort required here can be resource-intensive [*].
Endpoint performance impact on everyday workflows
Several users report noticeable performance degradation on endpoints, including slowed internet access or blocked websites that are essential for daily operations. In practice, this can lead to friction with employees and pushback from business units [*].
Alert fatigue from low-risk notifications
Perhaps the most damaging issue long-term is alert overload. Users describe being flooded with low-risk notifications, making it difficult to quickly identify incidents that genuinely require immediate attention.
When everything looks urgent, nothing does. Over time, this kind of noise erodes trust in the platform and increases the risk that real threats are missed [*].
Key Features and Functionalities to Consider in a Trellix DLP Alternative
When evaluating best alternatives to Trellix DLP, it’s important to shift the mindset from ‘replacing a tool’ to ‘fixing the operational gaps’ that led you to look elsewhere in the first place.
The features below are practical markers of a solution that will deliver real-world value:
Behavior and context-driven detection
One of the biggest limitations of legacy DLP tools is their dependence on static rules and content patterns.
While this approach can catch obvious violations, it often misses subtle insider risk or flags routine activity as suspicious. A modern Trellix DLP alternative should go beyond keyword matching and file types to understand how users normally behave.
Behavior-aware detection looks at patterns over time like how data is accessed, where it’s moved, and whether actions deviate from a user’s baseline.
Unified data visibility across endpoints, cloud, and networks
Data no longer stays confined to endpoints or on-prem environments. It flows continuously through browsers, mobile devices, SaaS platforms, cloud storage, and collaboration tools. If a DLP solution only sees part of that journey, investigations become fragmented and risk assessments unreliable.
A strong alternative should provide end-to-end visibility across where work actually happens, correlating endpoint activity with cloud usage and web behavior. When all data movement is visible in one place, security teams gain a clearer picture of risk without stitching together evidence from multiple tools.
High-signal alerting and intelligent prioritization
Alert fatigue is one of the most common reasons teams lose confidence in DLP tools. When low-risk notifications flood the system, genuinely dangerous incidents become harder to spot — especially during high-volume periods.
Modern DLP alternatives emphasize signal quality over alert quantity. Instead of flagging everything, they prioritize incidents based on risk, context, and potential impact. This helps analysts quickly identify what requires immediate attention and reduces time wasted investigating benign activity.
Integrated forensic capabilities
Detection is only half the job. Once an incident is flagged, teams need to understand exactly what happened. That requires more than a basic alert.
Look for platforms that provide rich forensic context out of the box, including timelines of user activity, file interactions, and preserved evidence.
When investigations are intuitive and self-contained, security teams can resolve incidents faster and support audits, HR reviews, or legal inquiries without scrambling for data.
Flexible policy management
DLP policies should evolve as the business evolves. Rigid rule sets that require extensive tuning or cause operational disruptions make it harder for teams to adapt to new workflows or threats.
A capable Trellix alternative should support flexible, real-time policy enforcement, with the ability to test changes safely before applying them broadly. This allows teams to refine controls gradually, improve accuracy, and avoid breaking legitimate workflows while still enforcing protection consistently.
Cloud-ready architecture built for scale
As organizations move toward cloud-first and hybrid environments, DLP platforms need to scale without heavy infrastructure or complex deployments. Tools built for perimeter-based networks often struggle to adapt to remote work and SaaS-driven workflows.
Cloud-based or hybrid-ready DLP alternatives typically deploy faster, scale more easily, and integrate more naturally with modern environments. This lightweight architectural flexibility becomes increasingly important as teams grow and data movement becomes more distributed.
Comparison: Top 10 Trellix (McAfee) DLP Alternatives
| Solution | Behavioral Detection | Unified Visibility | Insider Risk | Endpoint Controls | Cloud/SaaS DLP | Ease of Deployment |
|---|---|---|---|---|---|---|
| Teramind | Continuous user behavior visibility | Endpoint, app, and web telemetry | Core strength | Deep endpoint telemetry | Yes (via connectors) | Easy |
| Forcepoint DLP | Partial (RAP); Context-aware | Broad across channels | Limited (implicit via context) | Yes | Yes (CASB/API) | Complex |
| Fortra’s Digital Guardian | Context-aware classification | Endpoint, network, and cloud | Yes | Deep endpoint | Yes | Complex |
| Cyberhaven | Data lineage & user behavior | Full end-to-end visibility | Yes (scoring) | Lightweight sensors | Yes | Medium |
| Mimecast Incydr | Behavioral patterns | Endpoint and cloud | Yes | Endpoint and cloud | Yes | Medium |
| Symantec DLP | Traditionally content-based | Wide across vectors | Limited (implicit) | Yes | Yes | Complex |
| Microsoft Purview | Content & ML-driven context | Cloud and endpoint | Emerging | Yes | Cloud/SaaS | Easy |
| Safetica | User behavior & alerts | Endpoint and cloud | Yes | Yes | Cloud apps | Medium |
| Trend Micro IDLP | Content-centric | Varies by module | Minimal | Yes | Cloud add-ons | Easy |
| Endpoint Protector | Content & context | Endpoint and cloud | Limited | Strong endpoint | Cloud support | Medium |
1. Teramind DLP
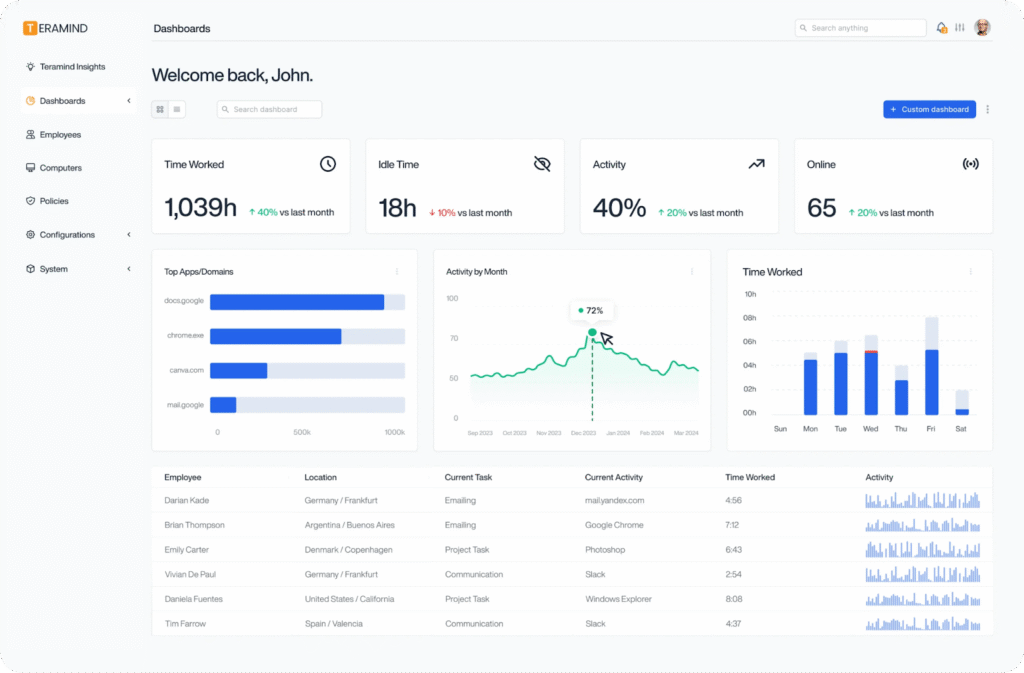
Teramind DLP takes a fundamentally different approach from traditional, policy-heavy DLP tools like Trellix (McAfee DLP).
Instead of relying primarily on static rules and pattern matching, Teramind focuses on continuous user behavior visibility, combining data loss prevention with insider risk detection and investigation in a single platform.
This makes it especially effective in environments where risk accrues in a series of small, contextual actions over time.
Here’s how it works:
Teramind uses full activity telemetry across endpoints, applications, and user sessions. This allows it to capture how data is accessed, created, modified, and moved—whether through files, browsers, cloud apps, emails, or screenshots. Then, it ties those actions directly to individual users.
The focus here is deciding whether that ‘behavior was normal’ under the set baseline rules.
Key Teramind DLP features
- User Activity Monitoring (UAM): Continuously records user actions across endpoints, including file operations, application usage, web activity, and system interactions. This creates a complete behavioral baseline that DLP policies can reference when determining whether activity is risky or routine.
- Content-based DLP rules: Teramind’s policy engine lets you create granular rules that detect sensitive data based on content inspection. This includes regex patterns, keyword dictionaries, and predefined templates for compliance frameworks like PCI DSS and HIPAA.
- For example, Teramind can identify and classify sensitive information across file transfers, email attachments, clipboard operations, and cloud uploads.
- User Behavior Analytics (UBA): Analyzes activity patterns to identify anomalies that may indicate insider threats or data exfiltration. By comparing actions against historical behavior, the system highlights high-risk deviations that traditional DLP tools often miss.
- Risk scoring: Assigns dynamic risk levels to users based on cumulative behavior, policy violations, and contextual signals. This helps teams prioritize investigations and focus on users who pose the highest potential risk rather than chasing isolated alerts.
- Session recording and playback: Teramind captures screen recordings, keystroke logs, and application activity for forensic investigation and compliance auditing. Security teams can review exactly what a user was doing when a DLP policy was triggered, providing the context needed to determine whether an incident was malicious, accidental, or a false positive.
- Optical Character Recognition (OCR): Built-in OCR capabilities that extract and analyze text from screenshots, images, and scanned documents to prevent visual data exfiltration methods.
How does Teramind compare with Trellix DLP?
When teams evaluate Teramind against Trellix DLP, the comparison falls on three categories:
- How protection feels in daily use
- How much noise it generates
- How easily analysts can act confidently on alerts
Behavior-focused detection vs. rule-heavy pattern matching
- Trellix DLP primarily relies on rule-based detection and content patterns. It looks for defined signatures, file types, or policy violations. That approach can work for well-scoped use cases—however, it often generates noise in modern environments where data movement is fluid and context matters.
- Teramind, on the other hand, builds risk detection around user behavior across time. It examines how the data appears and how users interact with it. This allows it to detect subtle indicators of risk that static rule sets miss and significantly reduces false positives as analysts get alerts with context.
Unified session evidence vs. scattered log outputs
- One of the biggest operational frustrations with Trellix is that the evidence supporting an alert can feel fragmented. Logs may show a file event here, a network action there, and it’s up to analysts to piece things together.
- With Teramind, every relevant user action is captured in a forensic session record tied to the incident — including screen video where permitted, application activity, and sequence of events. This makes the investigation clearer and faster, so analysts spend less time reconstructing what happened and more time deciding whether it matters.
Lightweight agent footprint vs. performance impact concerns
- Many teams adopting Trellix DLP have raised concerns about performance impacts — especially on endpoints and network throughput. Heavy agents or intrusive hooks can degrade user experience, leading to internal resistance or workarounds.
- Teramind’s agents are designed to collect rich telemetry while staying lightweight. The platform emphasizes minimal performance impact, letting security teams get visibility without compromising productivity.
Why is Teramind a first-choice DLP solution for security teams?
- “Its intuitive interface and comprehensive monitoring capabilities make it easy to track and analyze user activity effectively. The real-time alerts and detailed reports help quickly identify risks and ensure compliance, enhancing overall security.” [*]
- “Teramind can be drilled right down to the second of what an employee is doing. You can watch live feed, recorded feed, set up analytics to compare quickly and many other things. The customer support has been wonderful and any issues are taken care of within 24 hours.” [*]
- “One of the most valuable aspects of Teramind is its behavior alerts and customizable policies. These tools allow us to monitor communications, track potentially risky behavior, and understand overall employee sentiment.” [*]
How Arrivia Stopped an Insider Data Theft Ring with Teramind [Case Study]
For organizations frustrated by alert fatigue, complex configuration, or blind spots in Trellix DLP, Teramind represents a more modern, intelligence-driven alternative.
2. Forcepoint DLP
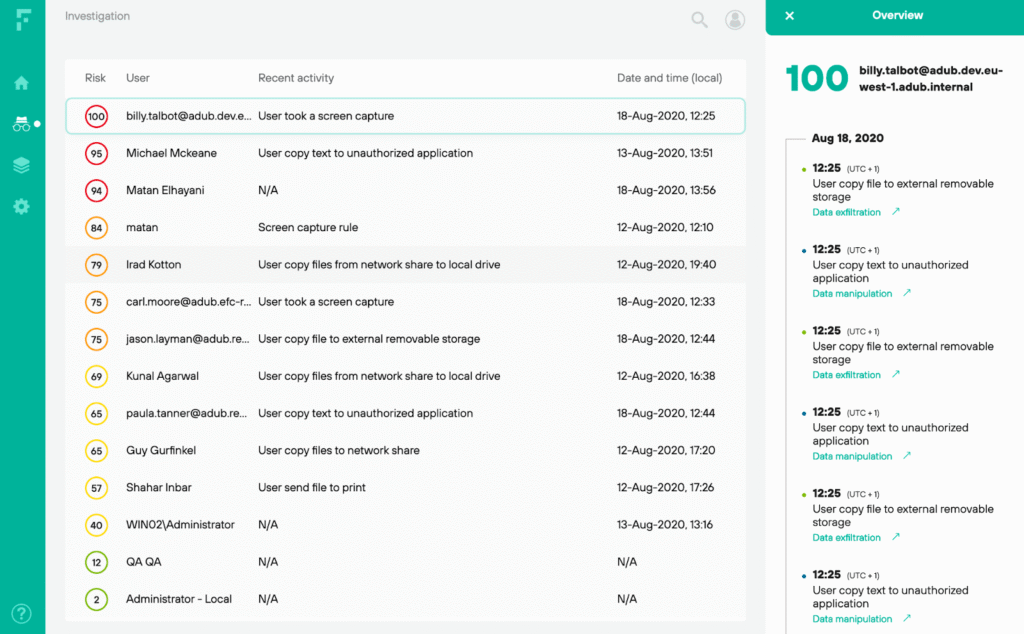
Forcepoint Data Loss Prevention (via Forcepoint ONE) is an enterprise-grade solution that provides unified data protection across network, endpoint, cloud, and email channels through a single management console.
The platform stands out through its integration with Forcepoint’s Risk-Adaptive Protection framework, which adjusts data security controls dynamically based on user risk scores.
For example, its content inspection engines combine fingerprinting, machine learning classification, and pattern matching to identify sensitive data across structured and unstructured formats.
Key features
- Risk-Adaptive Protection (RAP): Dynamically adjusts data controls based on user behavior and contextual risk signals. It factors in user behavior, data sensitivity classification, and contextual attributes like location, device posture, and application risk scores.
- Pre-defined templates & classifiers: Includes an extensive library of 1,700+ pre-defined policy templates and classifiers tailored for industry regulations and common sensitive data types (GDPR, PII, PHI, financial information).
- CASB and cloud integration: Integrates with cloud services through its CASB and API connectors, enabling visibility and enforcement in platforms like Microsoft 365, Google Workspace, and other SaaS tools.
What users say about Forcepoint DLP
- “Especially if you are using Forcepoint Proxy, I definitely recommend you to use it. The integration process is as simple and fast as possible, briefly 2 keys.” [*]
- “I wouldn’t say I like its document part because if I read the documentation for the 1st time installation, I could not understand anything. I got stuck. And I felt difficulty in learning the force point Data Loss Prevention.” [*]
Pricing
- Contact sales for more information.
Best for: Enterprises requiring risk-adaptive data protection that adjusts security controls dynamically based on user behavior.
Related → Top 12 Forcepoint DLP Alternatives & Competitors
3. Fortra’s Digital Guardian
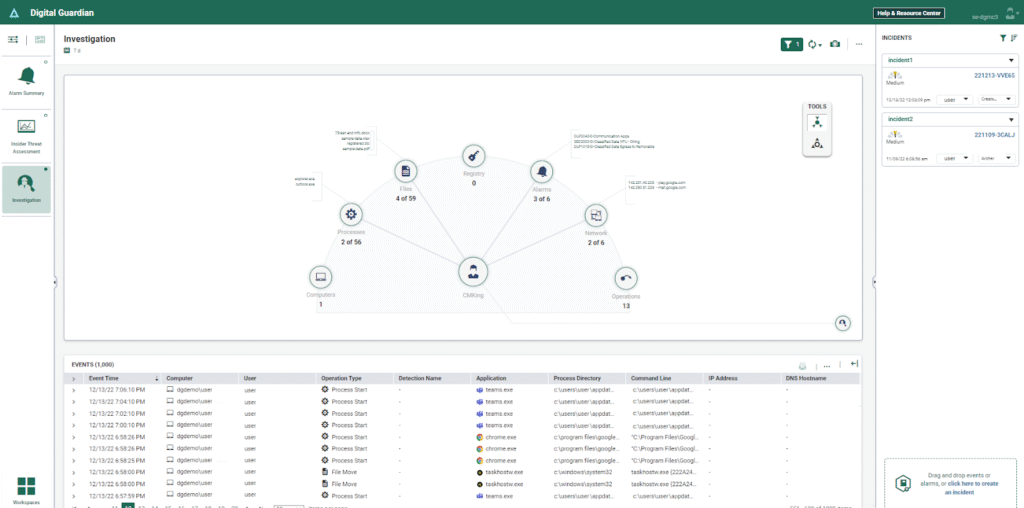
Fortra (formerly Digital Guardian) is another data loss prevention and protection platform that gives enterprises deep visibility and granular control over sensitive data wherever it lives.
The platform’s architecture is built around the concept that effective data protection requires understanding data context:
- who created it, how it’s classified, how it’s being used, and where it’s traveling.
This allows its endpoint agents and network sensors to capture detailed activity of all events. It can discover, classify, monitor, and protect both structured and unstructured information across endpoints, networks, cloud storage devices, and email.
Key features
- Managed detection and response (MDR): Fully managed DLP service where Digital Guardian security analysts monitor your data events 24/7, investigate policy violations, tune detection rules, and provide incident response support.
- Endpoint DLP: Offers deep visibility into sensitive data activity on Windows, macOS, and Linux systems. It also captures events at the system, user, and data level whether devices are on or off the corporate network.
- Deployment flexibility: Supports both on-premises and cloud-delivered deployment models, as well as hybrid configurations.
What users say about Fortra’s Digital Guardian
- “I have noticed that the dashboard performance can sometimes be sluggish, with insights taking more time to generate than anticipated.” [*]
- “The software surpasses expectations in safeguarding our data, offering outstanding security features that ensure the protection of our critical information.” [*]
Pricing
- Contact sales for more information.
Best for: Data-centric security programs prioritizing data classification and context, with optional managed DLP services.
Related → 12 Fortra Alternatives (formerly Digital Guardian) for 2026
4. Cyberhaven
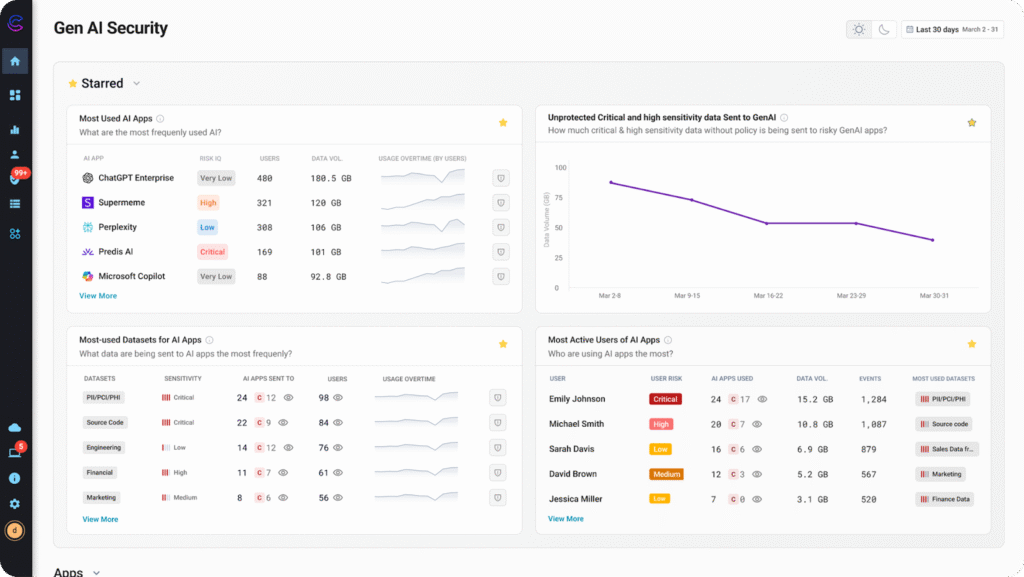
Cyberhaven represents a next-generation approach to data loss prevention. It combines traditional DLP functions with data lineage and insider risk awareness into a unified platform often referred to as Data Detection and Response (DDR).
The solution maps every piece of sensitive information back to its source and follows its path (where it originates, how it moves, who interacts with it, and where it travels) across endpoints, cloud services, apps, and user behaviors.
This continuous understanding of data context improves detection accuracy and reduces false positives compared to legacy DLP systems.
Key features
- Data lineage tracking: Continuously follows a piece of data from its point of origin through every interaction including files, cloud apps, user actions, and sharing events.
- Lightweight cross-environment sensors: Uses lightweight agents, cloud API connectors, and browser extensions to capture telemetry across endpoint, web, and cloud environments without significant performance impact or disruption.
- Real-time remediation and user coaching: This flexible response model allows organizations to intervene appropriately while minimizing disruption to legitimate work.
What users say about Cyberhaven
- “Creating custom policies with multiple conditions is not always straightforward. If you’re used to creating a SQL style query to “filter” data, where each statement reduces events.” [*]
- “Cyberhaven has user-controlled override functions that work on email, web, USB, and peripheral data transfers to keep availability “always on” in my enterprise.” [*]
Pricing
- Contact sales for more information.
Best for: Preventing sophisticated data theft through automated data lineage tracking and AI/LLM data exposure detection.
Related → Top 13 Cyberhaven DLP Alternatives & Competitors for 2026
5. Mimecast Incydr
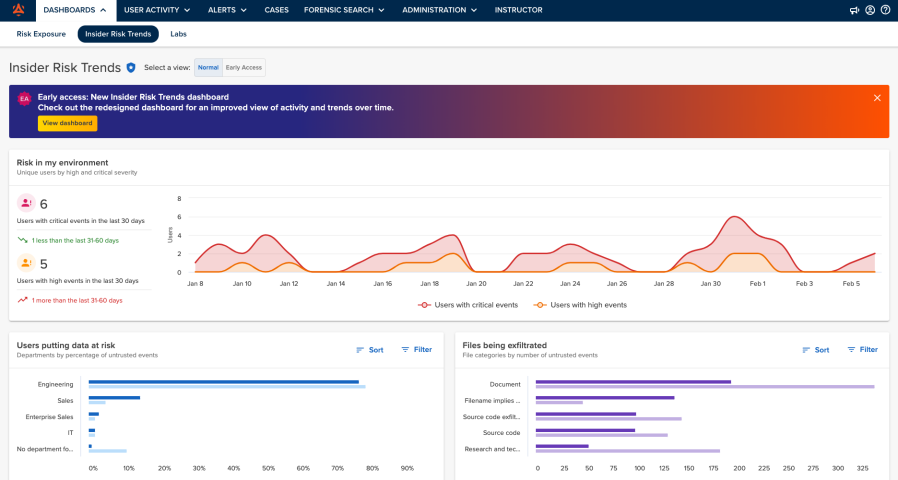
Mimecast Incydr is an insider risk detection platform specifically designed to address data loss scenarios involving trusted employees rather than external threat actors.
It watches for anomalous patterns, high-risk user actions, and potentially unauthorized data exfiltration in real time. This includes monitoring how sensitive data moves across user accounts, devices, and cloud services (especially SaaS tools like Microsoft 365 and Google Workspace).
Since its acquisition by Mimecast, Incydr has also strengthened its integration with email-centric workflows and security ecosystems.
Key features
- Incident triage: Organizes events into manageable cases and augment them with contextual signals. This makes it easier for security analysts to decide which incidents are urgent and which are routine.
- Forensic timeline reconstruction: Analysts can view step-by-step activity on a file or account, helping teams trace how sensitive data was used.
- Departing employee detection: Connects to Workday or Bamboo HR to identify employees who may be preparing to leave the organization and take proprietary data with them.
What users say about Code42 Incydr
- “Code42 It works as a highly compatible software with multi-user environments, generating peace of mind of having a safety net.” [*]
- “It’s very easy to set up the software. Its application interface is very user-friendly; love the minimalist UX/UI design yet it’s easy to navigate.” [*]
Pricing
- Contact sales for more information.
Best for: Organizations where sensitive data primarily flows through SaaS tools and shared drives.
Related → The 10 Best Mimecast Incydr Alternatives for Data Loss Prevention
6. Symantec DLP (Broadcom)
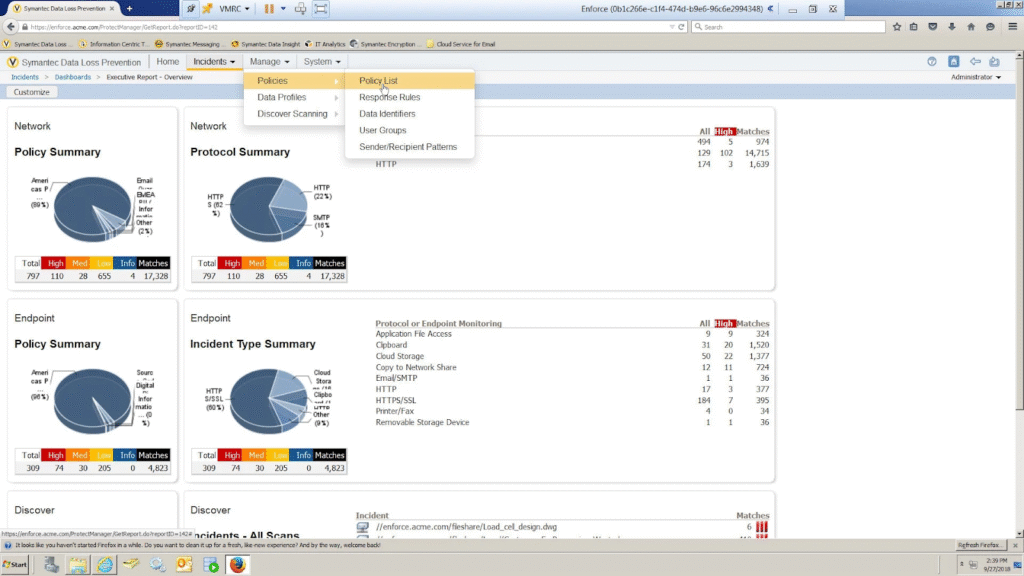
Symantec data loss prevention solution is one of the most mature and widely deployed in the market. It offers comprehensive data protection across network, endpoint, cloud, and storage environments through a unified policy engine.
The platform’s longevity has resulted in extensive integration capabilities with third-party security tools, pre-built detection templates for hundreds of regulatory frameworks and data types.
However, similar to Trellix DLP, Symantec’s breadth of capability also brings complexity. Large rule bases, extensive deployment footprints, and the need for careful tuning can require significant expertise and resources to maintain.
Key features
- Network prevent: Deploys as monitor-mode appliances that inspect traffic across web protocols, email (SMTP), FTP, HTTP/HTTPS, and cloud application APIs to enforce DLP policies at the network edge.
- Endpoint prevent: Provides granular control over data movement on Windows, Mac, and Linux systems. It monitors file transfers, removable media, network shares, email clients, web browsers, cloud sync applications, and printing operations.
- Symantec DLP Discover: Scans file servers, SharePoint repositories, databases, and cloud storage platforms to identify where sensitive data resides across your environment and assess exposure risk.
What users say about Symantec DLP (Broadcom)
- “I think it should be more effective on network traffic on endpoint devices and also it should monitor all AI softwares such as Cursor, Gemini, and ChatGPT.” [*]
- “I like that Symantec Data Loss Prevention is easy to use, not problematic, and always runs as expected, with a stable performance. The agents are very stable and effortless, and since we deployed them to all our endpoint devices, there have been no errors.” [*]
Pricing
- Contact sales for more information.
Best for: Large organizations that prioritize content inspection, exact data matching, and strict compliance enforcement.
Related → Mimecast Incydr vs. Symantec DLP: Features, Pros & Cons
7. Microsoft Purview DLP
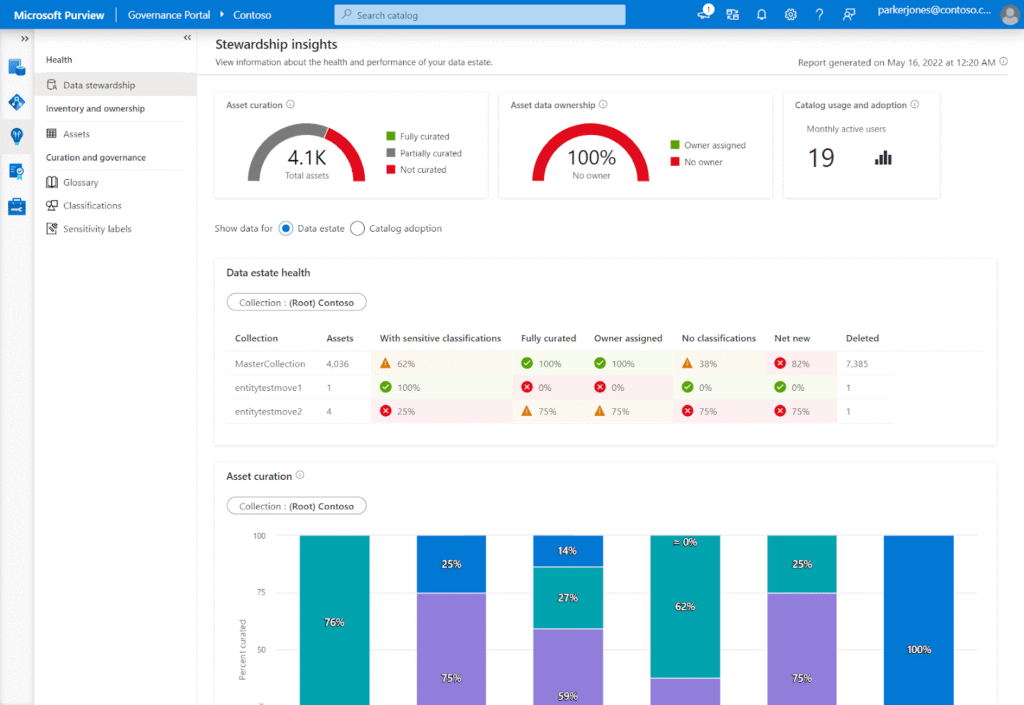
Microsoft Purview Data Loss Prevention (DLP) is Microsoft’s cloud-native solution built into the Microsoft Purview compliance and data governance platform.
It helps organizations identify, classify, monitor, and protect sensitive information wherever it lives or travels. This includes data residing Microsoft 365 services like Teams, OneDrive, Power BI, SharePoint, Exchange, and Microsoft 365 Copilot without requiring third-party agents or appliances .
Purview is designed to unify data governance, protection, and compliance controls under a single, scalable framework that fits naturally into Microsoft environments.
Key features
- Unified alerting and remediation: Teams can configure alerts, triage incidents, and take corrective actions directly from the DLP alerts page, with the option to extend workflows into SIEM or SOAR tools for automated handling.
- Sensitive data classification and labeling: Uses built-in and custom classifiers to automatically detect and label sensitive information such as financial, health, or personally identifiable data.
- Integration with Microsoft security ecosystem: Extends DLP signals into tools like Microsoft Defender XDR and Microsoft Sentinel, enabling cross-platform investigations and enriched alerts.
What users say about Microsoft Purview DLP
- “After complex builder logic, it don’t provide an option to update multiple rules through powershell, which makes our job lengthy if we want to update multiple rules.” [*]
- “Its interface allows users to set up DLP, making it easier to understand. It also allows us to try out a test to have an idea before going to production.” [*]
Pricing
- Starts from $12 per user/month.
Best for: Organizations already standardized on Microsoft 365, Windows, Azure, and Entra ID.
Related → How Endpoint Data Loss Prevention (DLP) Works
8. Safetica
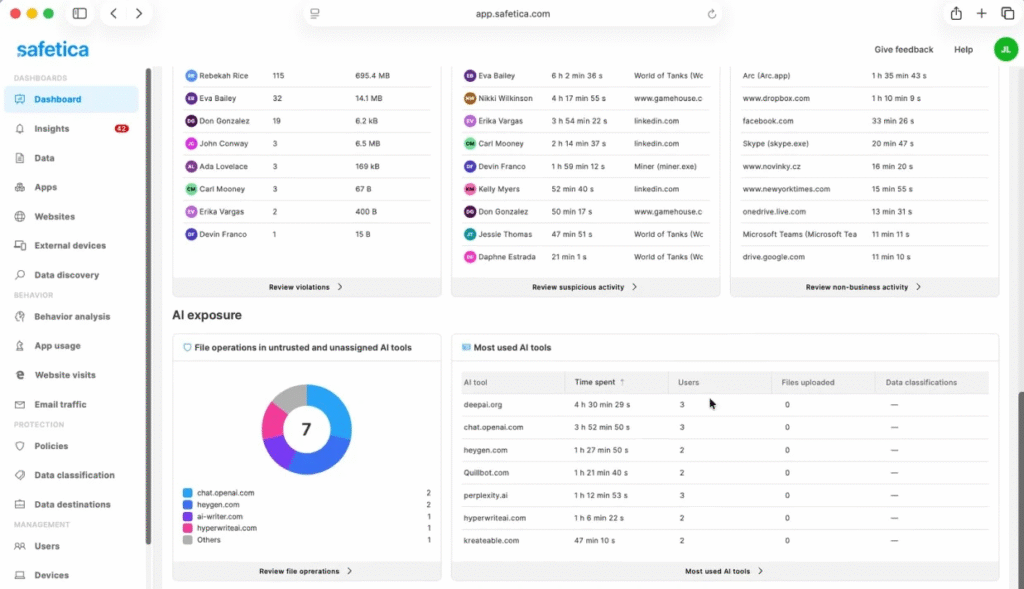
Safetica is designed around giving organizations clear visibility into how sensitive data is actually used—without adding unnecessary complexity.
It focuses on everyday employee behavior: which applications people use, like how files are shared, and when confidential data is accessed or moved. This behavioral analysis makes it easier to understand real data risk as it happens.
From there, Safetica combines deep data discovery with practical protection controls to prevent risky actions before they turn into incidents. It helps organizations identify potential insider threats early, while also guiding employees toward better data-handling habits through awareness and education.
Key features
- Cloud data protection: Extends DLP controls to cloud storage and productivity platforms such as Microsoft 365, helping organizations monitor and govern data as it flows through collaboration ecosystems.
- Endpoint and device controls: Enforces DLP policies across workplace devices, including laptops and BYOD environments.
- Insider risk detection: Combines data access patterns with contextual signals to identify abnormal or risky behavior before it leads to a serious incident.
What users say about Safetica
- “It is a tool that runs in the background, protecting data and preventing leaks, but without interrupting users or affecting the performance of the equipment.” [*]
- “For example, the initial setup can take time, especially if it’s your first time working with a DLP solution. There are many options and policies, and until you fully understand how they relate to each other, the process can feel a bit technical.” [*]
Pricing
- Contact sales for more information.
Best for: European mid-market organizations needing straightforward DLP with GDPR-compliant, privacy-conscious monitoring.
Related → Top 10 Safetica Alternatives & Competitors for 2026
9. Trend Micro Integrated DLP
Trend Micro IDLP is built directly into Vision One’s broader cybersecurity platform. It works alongside endpoint detection and response (EDR), email security, and cloud workload protection.
Because it’s part of the ecosystem, the DLP engine can correlate data loss events with threat intelligence, malware activity, and attack signals. This context helps teams quickly tell the difference between routine policy violations and high-risk incidents tied to active data breaches or insider threats.
Key features
- Endpoint protection: Monitors data interactions on devices and trigger notifications when policy rules are violated or suspicious behavior is detected.
- Advanced data identification: Uses predefined templates and customizable rules to detect sensitive information such as PII, financial data, and proprietary content. It can be configured to recognize specific data types and ensure appropriate controls are applied.
- Unified policy enforcement: Enables teams to create and apply DLP policies across multiple Trend Micro modules such as endpoint, network, and email — from a centralized console.
What users say about Trend Micro Integrated DLP
- “Trend Vision One is unified and intuitive dashboard, which makes it very easy to monitor, investigate and respond to security events across the entire environment.” [*]
- “I find the reporting part lacking. Currently, in Trend Vision One, reports cannot be scheduled with attachments; they only include links to view the report, which is a limitation. Trend micro does not having DLP features for MAC OS” [*]
Pricing
- Contact sales for more information.
Best for: Organizations wanting DLP integrated with EDR/XDR to correlate data loss events with threat intelligence.
Related → The 9 Best Endpoint Security Solutions In 2026
10. Endpoint Protector
Endpoint Protector is built to give security teams strong data protection controls across Windows, macOS, and Linux endpoints.
Its core focus is endpoint protection, with extended visibility into network traffic and cloud uploads. This makes it a practical fit for hybrid environments where sensitive data constantly moves between devices, SaaS apps, and collaboration tools.
Key features
- Policy automation: Teams can define recurring policy conditions or time-based controls. For example, enabling stricter enforcement outside business hours or for specific user groups.
- Content aware protection: Inspects data at rest and in motion using built-in and custom classifiers, keyword matching, and pattern analysis.
- Incident logging and reporting: Collects detailed logs of DLP events, including user identity, file details, device type, and policy triggers, and presents them in dashboards and exportable formats for compliance and audit needs.
What users say about Endpoint Protector
- “Setup takes a bit of time, especially when fine-tuning policies for different teams. The UI is sometimes feel dated and not very smooth to navigate. Reports and Linux support could can be improved.” [*]
- “It does a solid job at blocking unauthorized USB access and keeping sensitive data from being copied or leaked.” [*]
Pricing
- Contact sales for more information.
Best for: Cross-platform environments requiring consistent DLP enforcement across Windows, macOS, and Linux endpoints.
Related → What Is Insider Data Exfiltration and How Can Organizations Detect It?
Moving Beyond Trellix: Why Teramind Fits 2026 Reality
Teramind is built for how data risk actually shows up in 2026. Instead of relying on rigid rules and static content matching, it focuses on user behavior, context, and intent.
This gives organizations clearer signals, better investigations, and far less noise than legacy DLP platforms like Trellix.
That’s why many teams are no longer looking to tune Trellix further, but to move beyond it.
Why Teams choose Teramind over Trellix
- Behavior-first detection: Teramind focuses on how users actually behave over time, surfacing meaningful risk instead of flooding teams with low-value policy hits.
- Investigation-ready context out of the box: Every alert comes with full activity timelines and session evidence, so analysts can quickly understand what happened.
- Lightweight protection for modern work environments: Teramind delivers deep visibility across endpoints, browsers, and cloud workflows without degrading performance or disrupting productivity.
- Smarter prioritization with risk scoring: Dynamic risk scoring highlights the users and incidents that matter most, reducing alert fatigue and speeding up response.



