Strict cybersecurity measures are necessary when using Teramind’s employee monitoring and data loss prevention suite. Because it collects loads of data on employee activity and records user activity involving confidential company information, protecting collected user data from malicious actors or abusive administrators is crucial to the integrity of the agent. Teramind’s access control policies were developed with a zero trust security architecture in mind. At its core, zero trust security is built around the idea that no one should be trusted with data, not even administrators with privileged access. Using access control policies in Teramind puts this idea to work.
Authentication
Authentication is a main tenet of access control policies, asking users for additional verification before granting access.In case user credentials are compromised, this provides an extra layer of security that ensures the credentials can’t be used. Data breaches caused by stolen employee credentials are the costliest data events for businesses. And with 61% of data loss events being attributed to stolen credentials, additional authentication is fast becoming a standard practice for software and applications.
In order to protect employee collected data, Teramind offers multiple authentication processes to protect administration logins: two-factor authentication, dashboard logins, LDAP, IP access restriction and SSO.
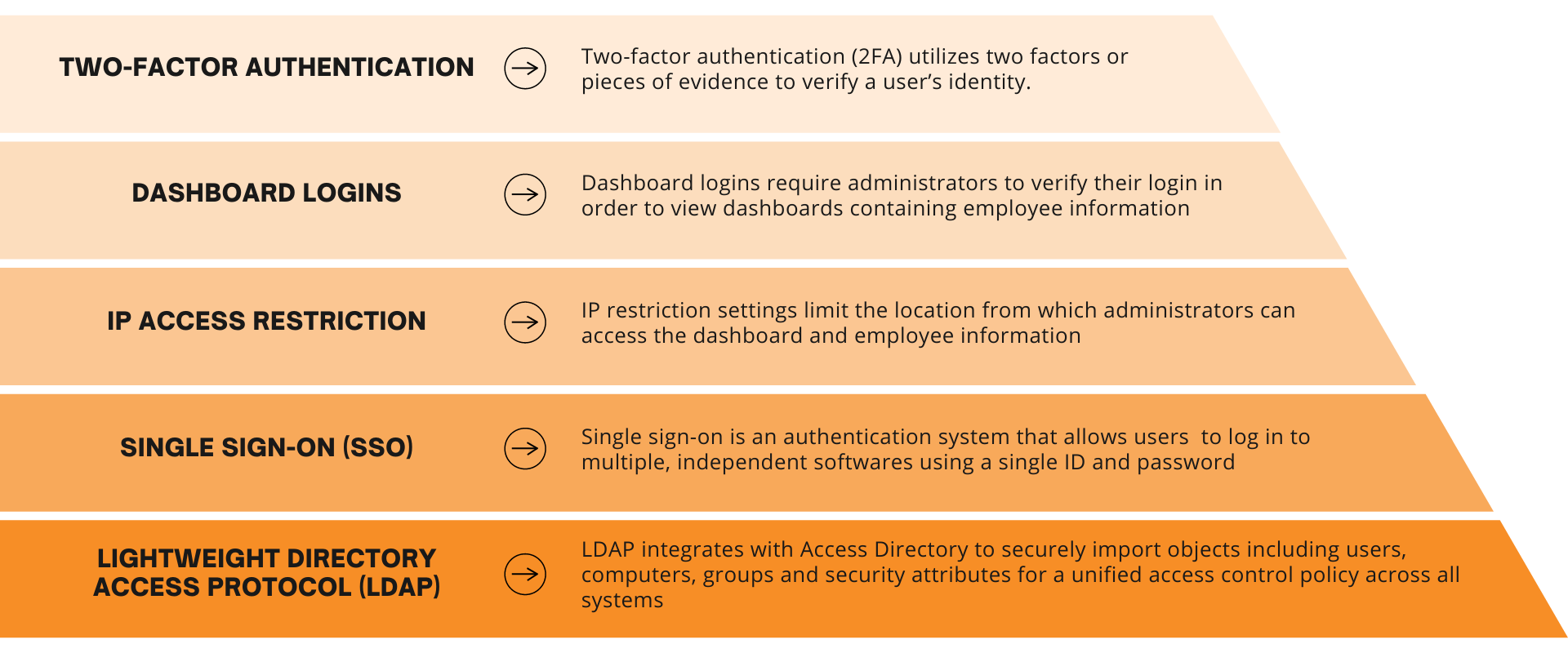
Like other authentication protocols, two-factor authentication requires users to verify their logins using a second factor or piece of evidence to identify themselves. Such authenticators like Google Authenticator provides a changing, random number to submit during login along with their user credentials.
Dashboard logins on Teramind work similarly, asking administrators to log in again when accessing the dashboard containing employee information. LDAP, or lightweight directory access protocol, provides protection to organizations importing their data, users and administrators through an active directory while IP restrictions limit where admins are able to login to the dashboard. For example, if an administrator attempted to log in from home rather than the office while an IP restriction was activated, their dashboard login would be denied.
Teramind also supports third-party SSO (single sign on) authentication for dashboard logins. If an organization already uses SSO for other applications or wants to migrate to an SSO architecture, Teramind is equipped for easy integration.
 Start running cybersecurity defense in your HR department
Start running cybersecurity defense in your HR department
Role-Based Access Control Policies
Since Teramind collects large amounts of employee data, it’s important to limit access to that data as much as possible. Restricting access to collected employee data isn’t just a good security practice either. Purpose limitation is a pillar of many data regulations and doing so keeps organizations compliant.
With that in mind, access control policies in Teramind include role-based access options.
The top-down roles included in Teramind agent management are as follows: administrator, operational administrator, infrastructure administrator, department manager and employees. Dividing access to the Teramind agent limits vulnerability of insider threat among all staff, administrators included.
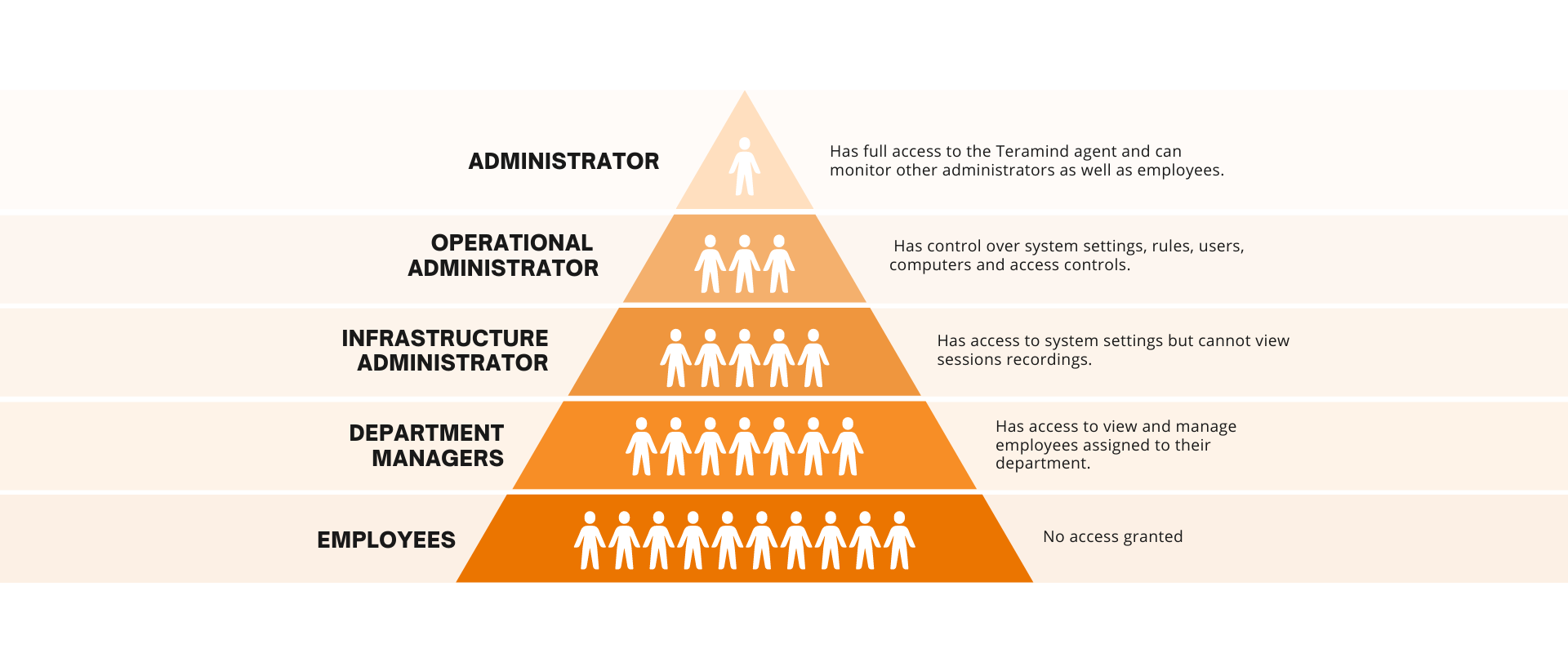
The administrator role has full access to the Teramind agent and can monitor other administrators as well as employees. While operational administrators have control over system settings, rules, users, computers and access controls, the infrastructure admin has similar access but cannot view sessions recordings. Finally, department managers can view and manage employees assigned to their department but don’t have system access otherwise.
Role-based access controls like these help manage privileged users and keep administrators on a need-to-know basis, lowering the threat to collected user data.
Access Control Policy Editor
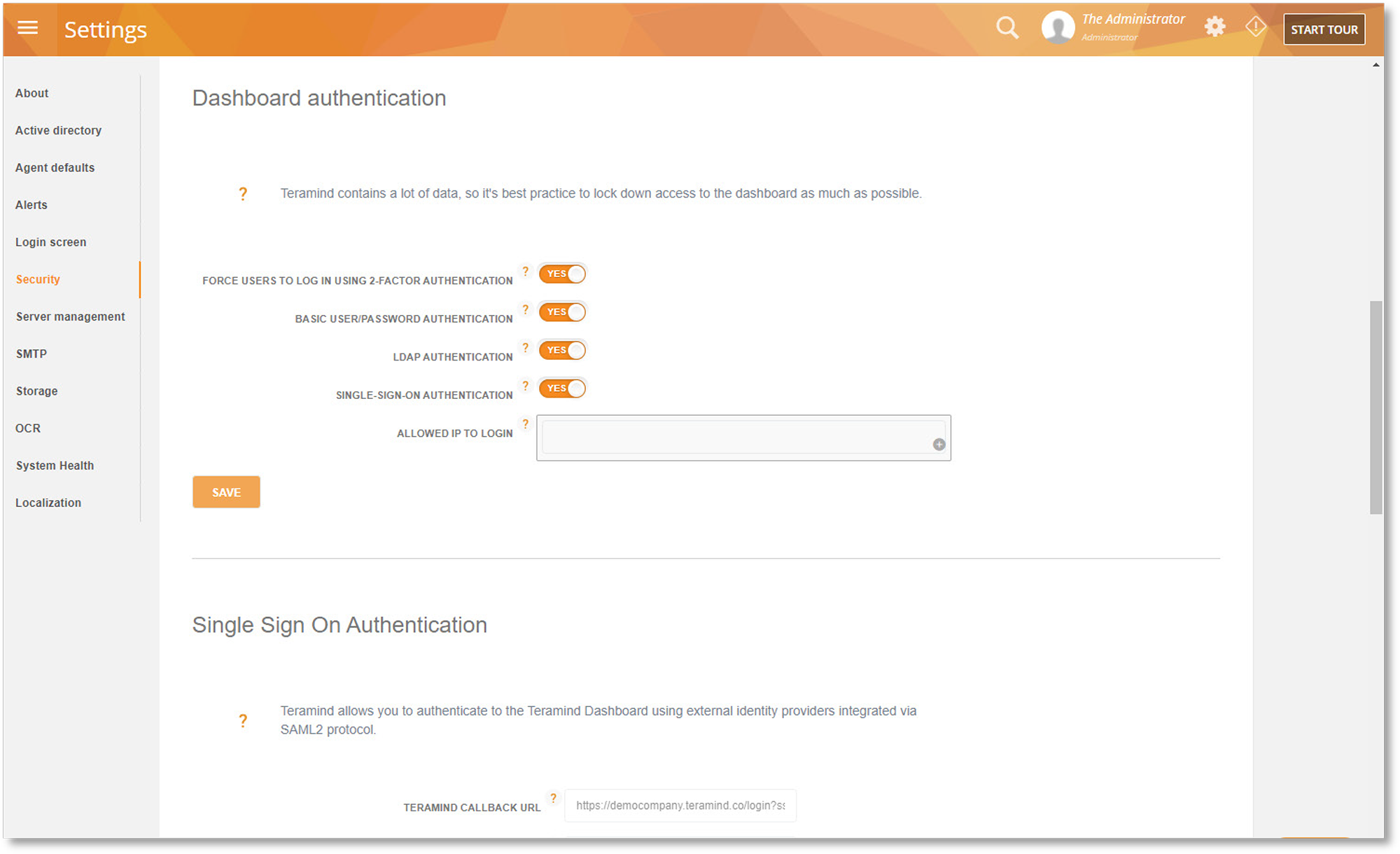
In addition to the role-based policies, Teramind also offers an access control policy editor to manage dashboard settings. When used as a productivity tracker, Teramind dashboards are useful to team leads and managers who may not necessarily need full administrator access to the Teramind agent. Access controls for such users are set up via the Access Control Policy Editor.
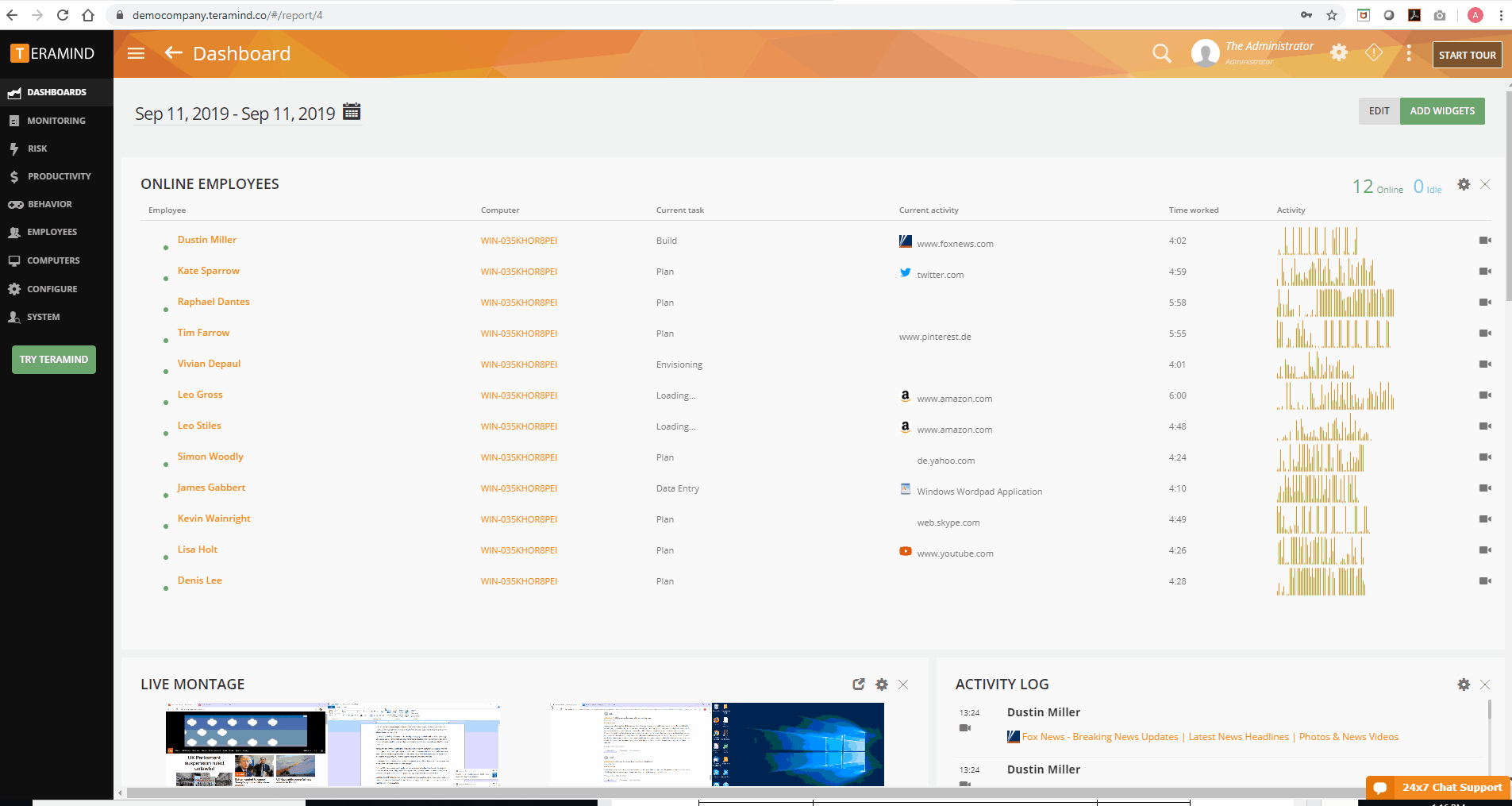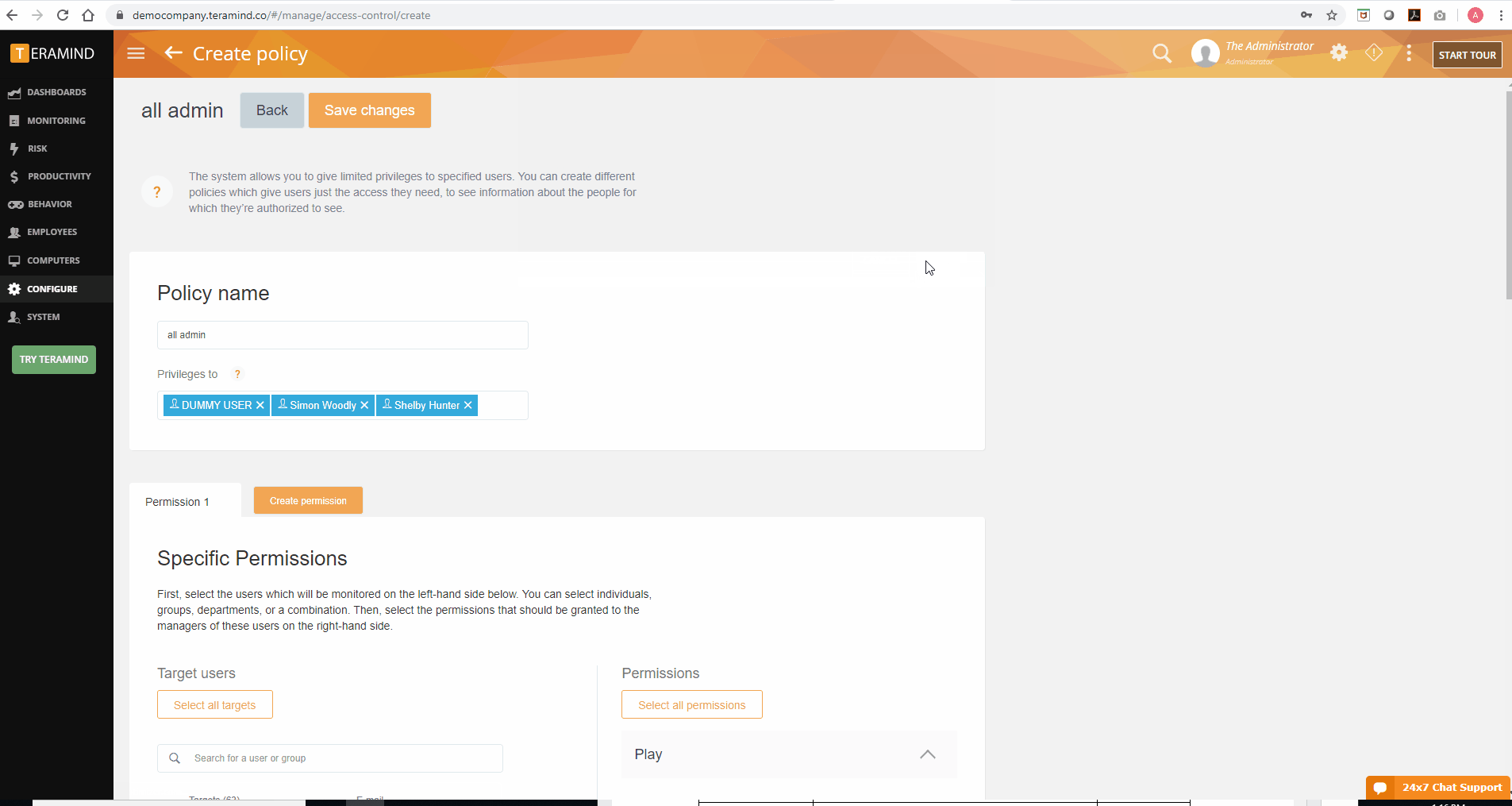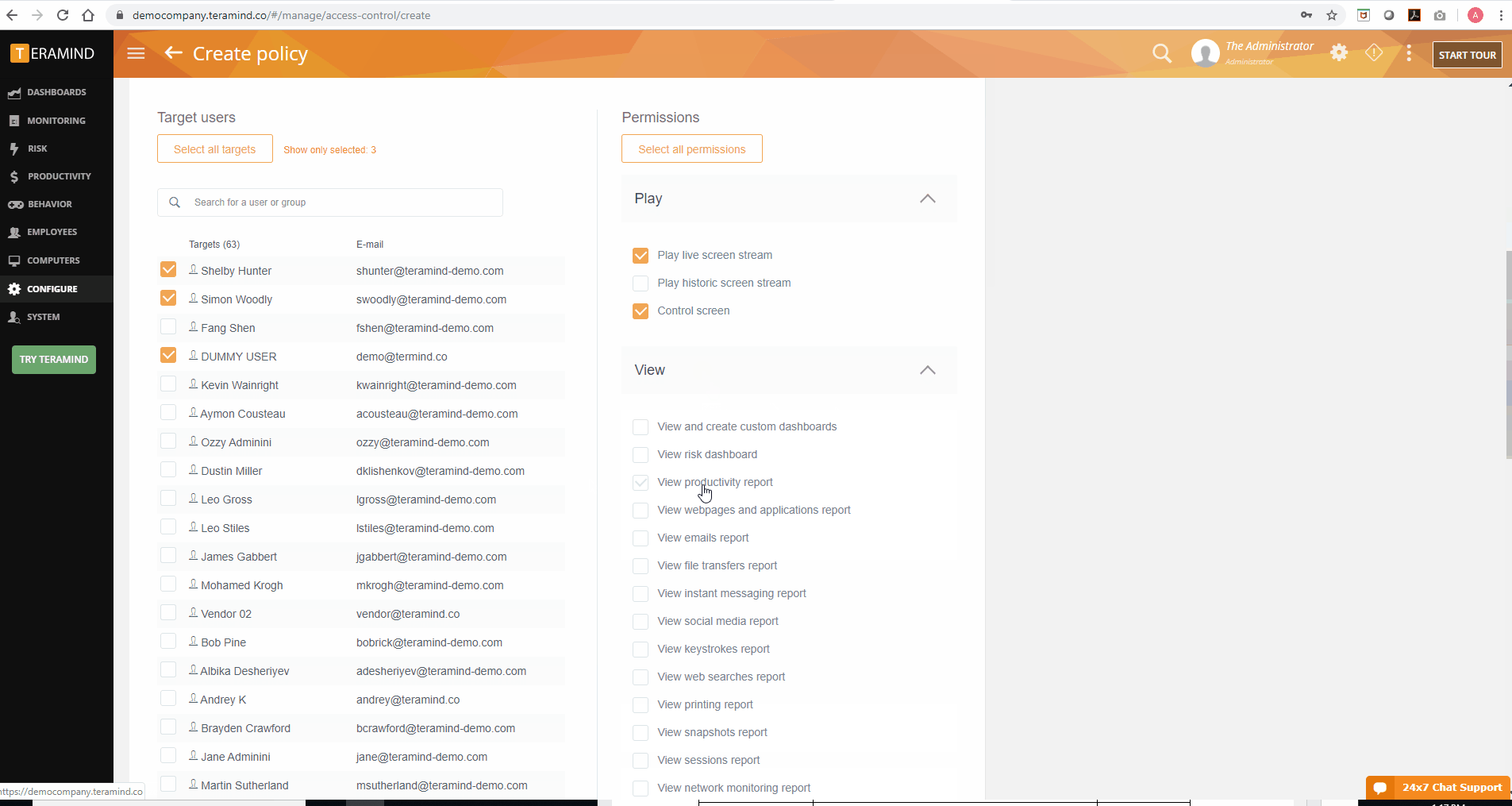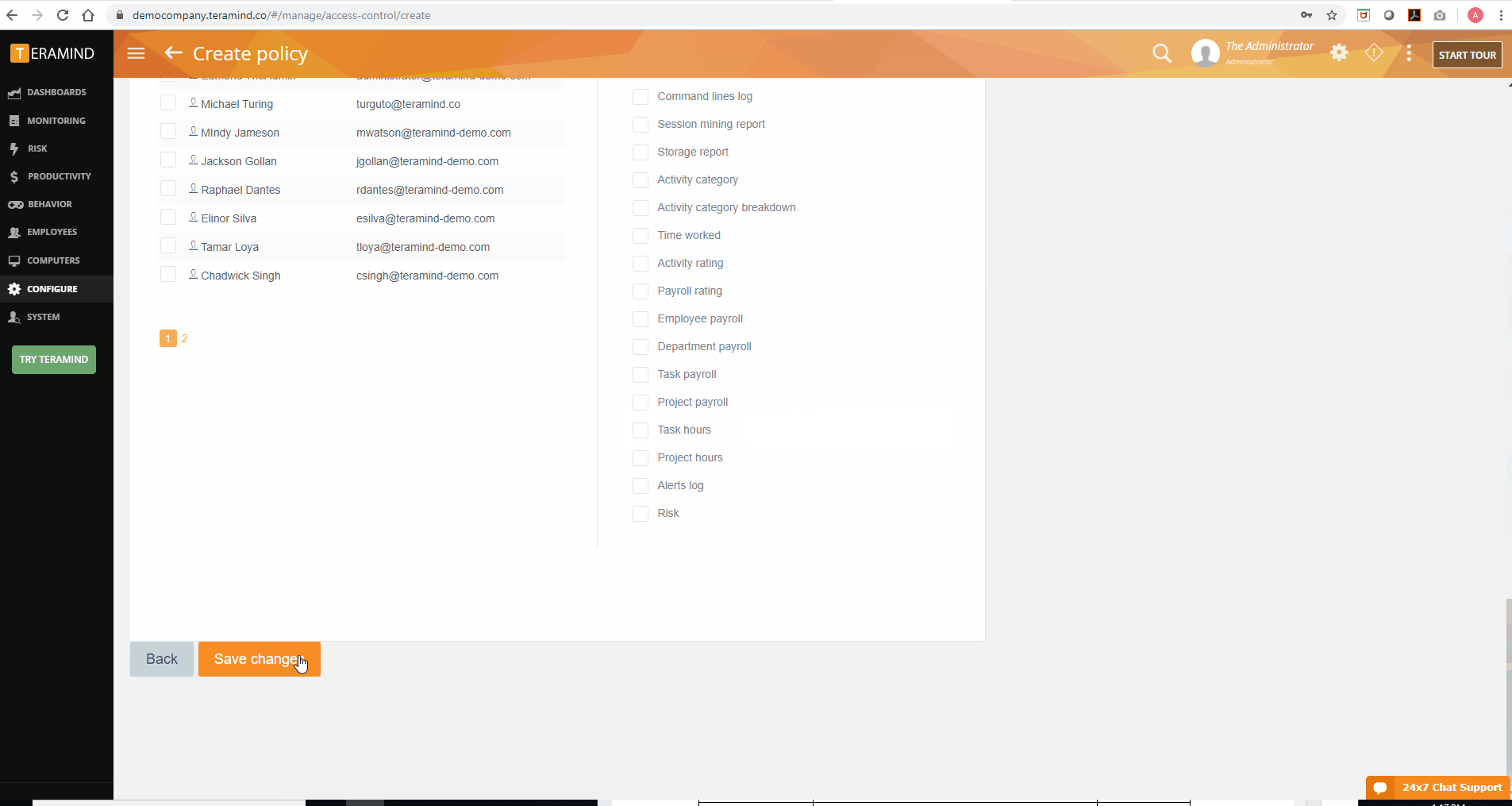
From the editor, admins can set policies to determine what information is available to such privileged users via the dashboard. Through policy creation in the editor, admins can customize individual access for each privileged user including which employees’ data they’ll be able to see and how much of that data is available for viewing. For example, a privileged user tracking the productivity of the IT department doesn’t necessarily need the same dashboard access that someone monitoring the sales team needs. The editor allows admins to make such a differentiation.
 Strengthen Your Remote Team’s Cybersecurity Now
Strengthen Your Remote Team’s Cybersecurity Now
Data Export Restrictions
While Teramind collects critical data to monitor employee productivity and data threats, there’s a high likelihood that the data contains confidential information that must be protected. By protecting collected user data against unauthorized and excessive exports, you’re also protecting the organization from a possible breach. Data export restrictions limit which users can download the reports and screen recordings containing said data and where it can be downloaded.
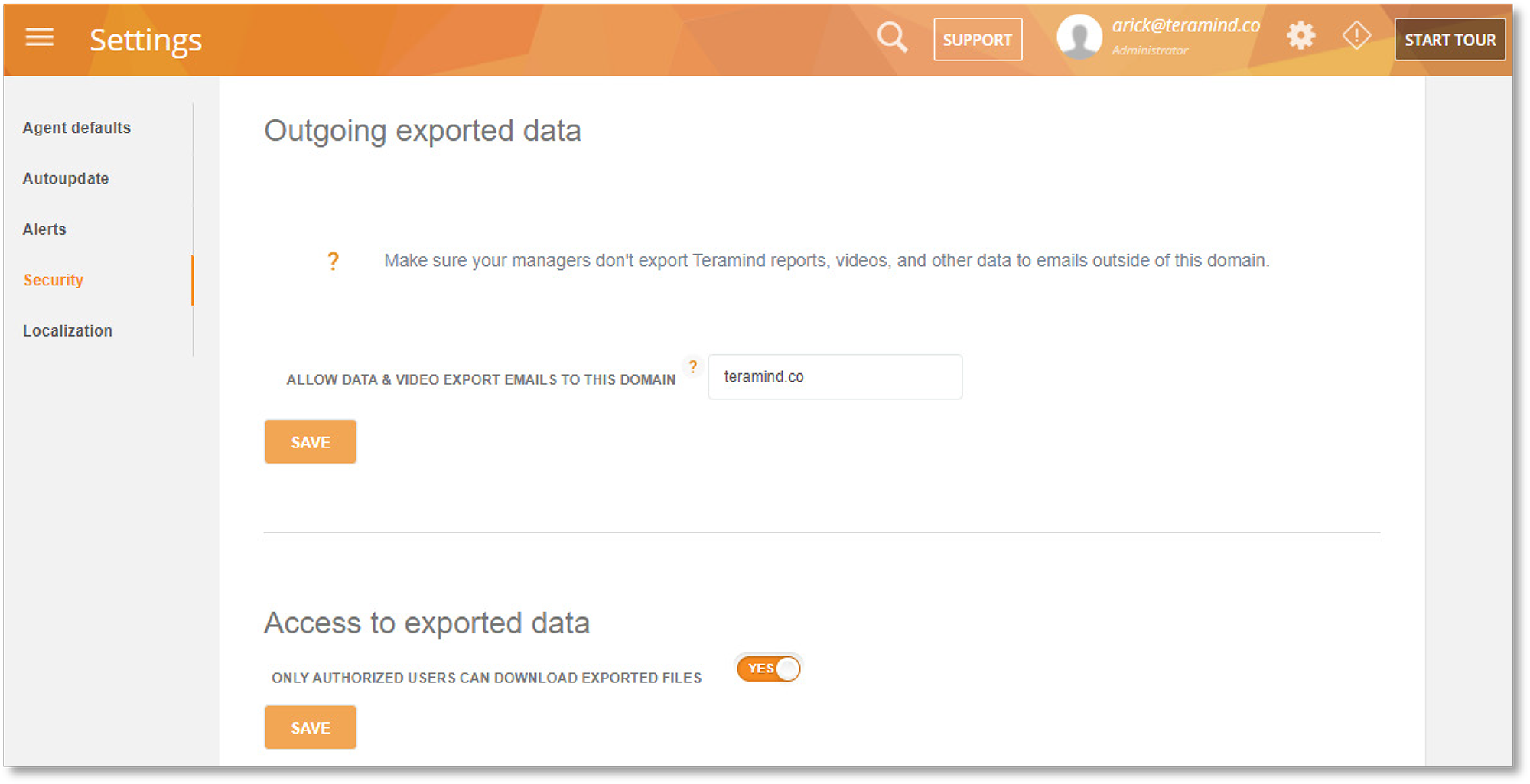
Here, admins can authorize a particular domain where exports will be sent. For example, work email domains rather than personal email accounts. Then, admins may also limit who can export data to limit out-of-agent access to confidential employee data and recordings.
On top of data export restrictions, the system log gives admins a way to monitor all privileged users so access isn’t taken advantage of.
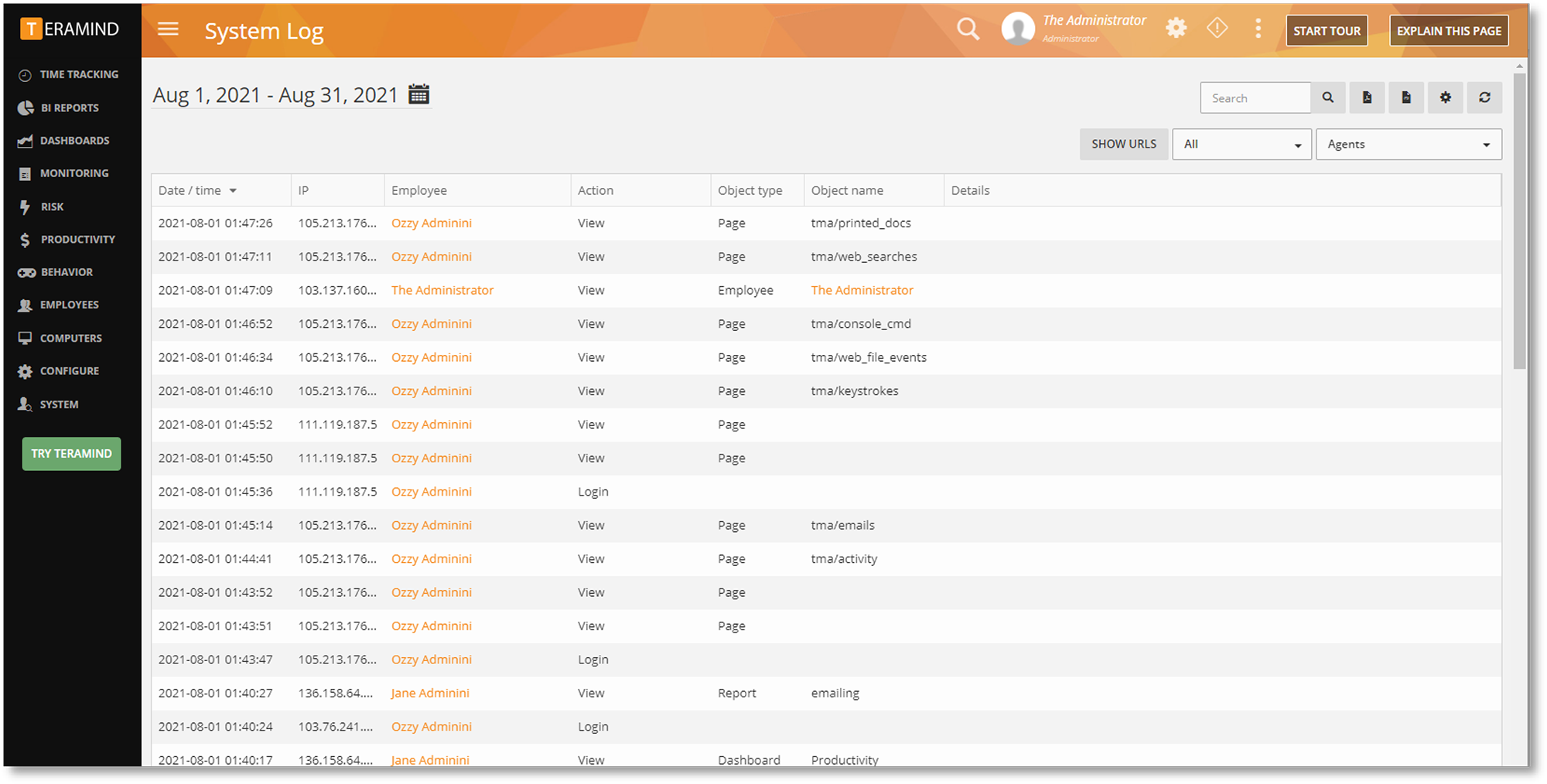
Rule-Based Access Control Policies
As an employee monitoring software, Teramind heavily relies on its Rules and Policies engine. Access control policies are no different. Rule-based policies let admins customize their access policies as needed.
For example, rules can be created to detect unauthorized dashboard login attempts and privilege escalation attempts.
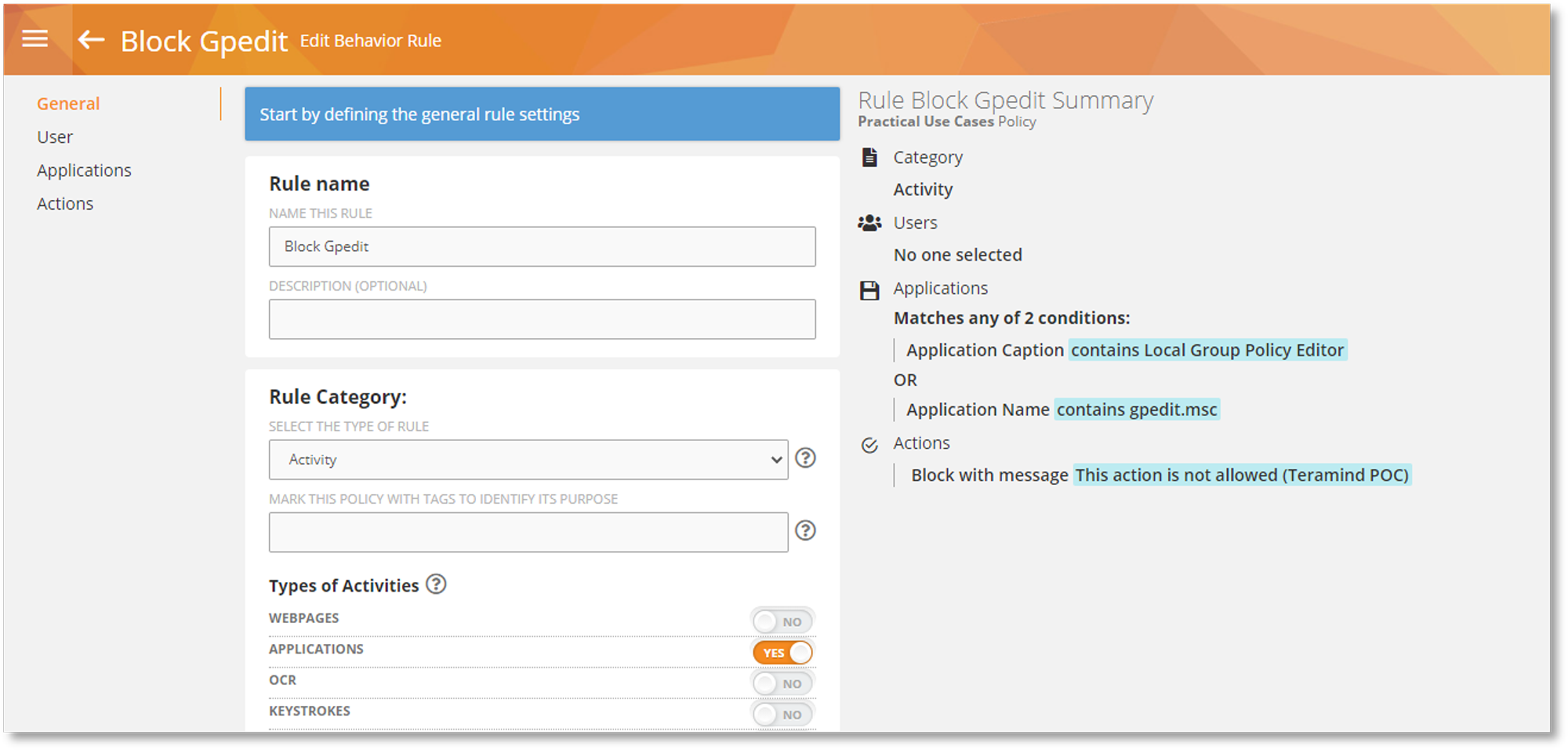
Using rule-based access controls keeps tabs on administrator and manager behaviors. When a rule is violated, automated actions can be activated. Depending on how the rule-based access is set up, these automated actions can alert other admins of the behavior, lock out the unauthorized user and/or block the action entirely.
Rule-based access control policies are crucial to Teramind when used as a data loss prevention software. These granular controls allow every Teramind user including administrators and managers to be held accountable for their actions while using the agent.
 Update your security model to Zero Trust and start seeing the benefits
Update your security model to Zero Trust and start seeing the benefits
Server Level Access Controls
Teramind offers cloud-based deployment and on-premise or private-cloud deployment. In addition to the access controls offered within the Teramind agent, there are additional access controls available via the host server. These access controls vary depending on which deployment method is being used.
For deployment using the Teramind cloud, the data centers use the strict and compliant access controls and physical securities like custom rack and cage security and specific administrative entitlements. On-premise or private cloud deployment also utilize access controls which vary further depending on the cloud provider.
More detailed and technical information regarding server level access controls can be found by visiting our Knowledge Base.
Zero Trust Security & Teramind
Teramind’s collected user data provides powerful insights to productivity and employee activity as well as data loss prevention. Ensuring that data is used securely, appropriately and by the right parties is critical to the success of the agent. Using access control policies in Teramind does just that. By protecting collected user data using Teramind’s access controls, you’re not only protecting the privacy of your employees but the organization as whole.
Learn More About Teramind’s Zero Trust Security & Access Control Features


