Monitoring Settings: New Advanced Settings for Local Admin Accounts and Wireless Networks
Platform: Cloud, On-Premise (Release 560)
We introduced two new Advanced options using which you can impose restrictions on admins accounts and wireless network access. You can access these options by clicking the ADVANCED button from a User’s Profile page, under the MONITORING OPTIONS tab. Or, from the Monitoring Settings screen:
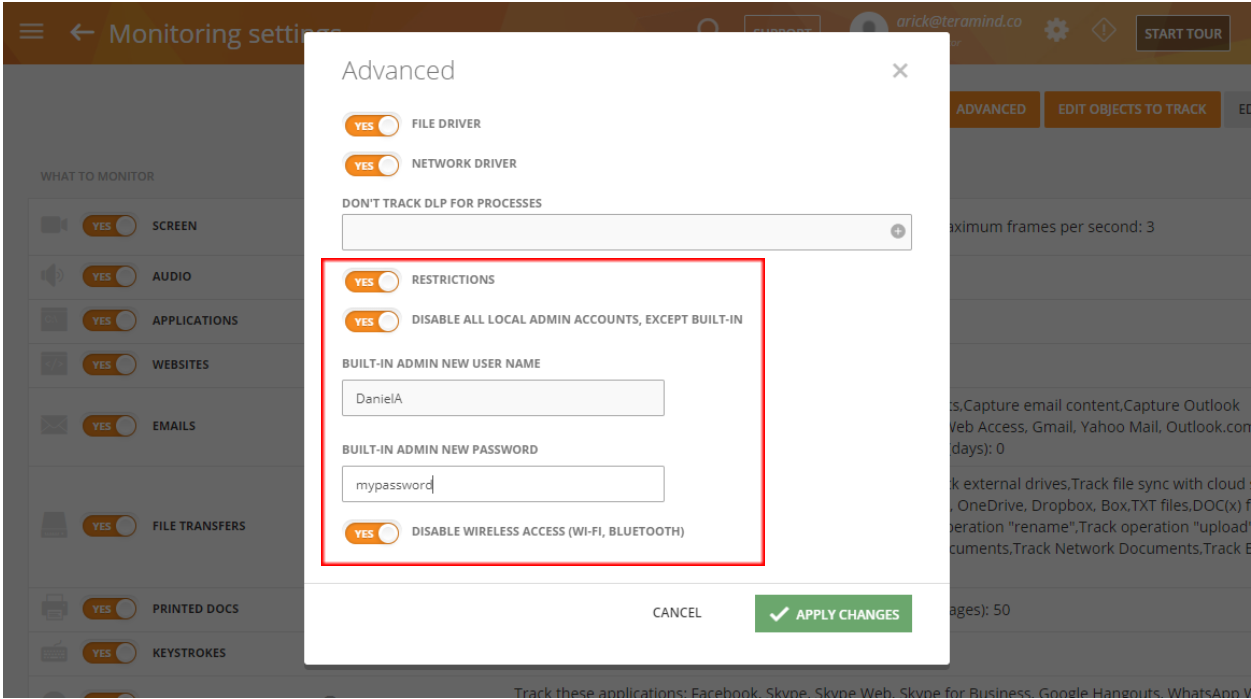
When you enable the RESTRICTIONS option, you will see two more options:
- If you turn on the DISABLE ALL LOCAL ADMIN ACCOUNTS, EXCEPT BUILT-IN option, you can specify a new admin user and password. Then, when a admin logs in as a current Windows user, a new admin will be created and all existing admin accounts will be disabled.
- If you turn on the DISABLE WIRELESS ACCESS (WI-FI, BLUETOOTH) then all Wi-Fi and Bluetooth network access will be disabled. Make sure the computer has an Ethernet connection before enabling!
Settings: New Options to Configure Dashboard Sessions
Platform: Cloud, On-Premise (Release 560)
Session timeout, session cookies and session lifespan are important access control mechanisms. Especially, if you are looking to stay compliant with PCI, SOX of OWASP then the ability to control session management will be mandatory.
Teramind already had strong security measures implemented for login sessions. For example, all credentials/tokens were stored in secure cookies with randomized AES encryption and there has been a default 2 hours life-time of session tokens, etc. However, most of those features were hidden away from the users.
From version 560, there’s now a set of Dashboard session options you can access from the Settings > Security tab:
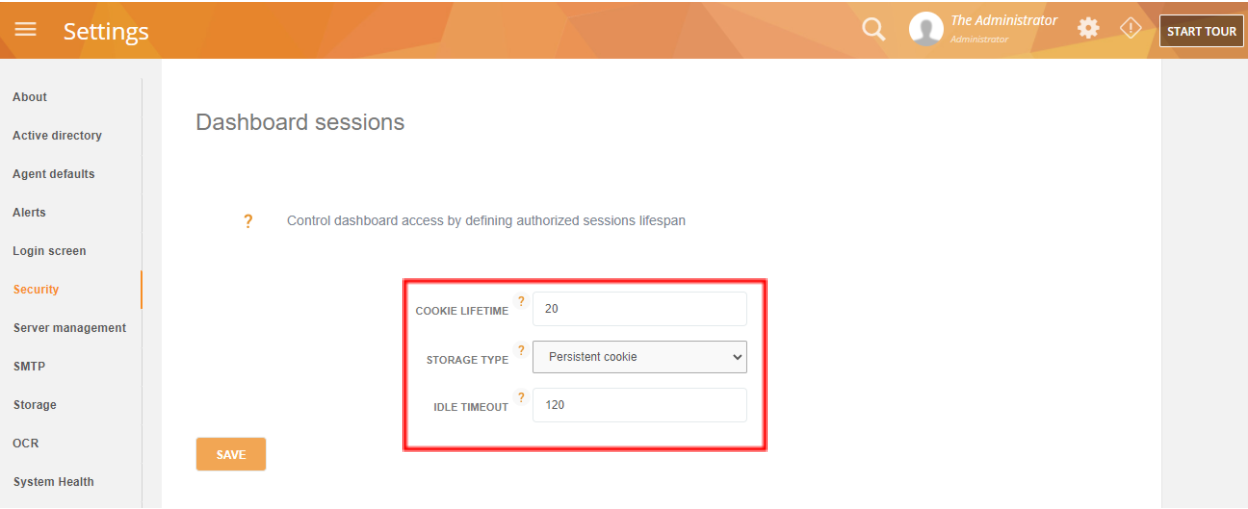
You can now control exactly how you want to manage your dashboard sessions including:
| COOKIE LIFETIME | Defines how long an authorization cookie will be valid (in minutes). An authorization cookie is a temporary secret used to authenticate the browser. It will be automatically updated in the background while the user is active. The update process takes a few seconds before it is going to expire. If the user closes the browser before the secret was updated, the session will be closed and the user will need to authorize again. |
| STORAGE TYPE | Defines whether it will be Persistent storage or Session storage.
A Persistent cookie is kept for the duration/lifetime of the Cookie lifetime. A Session cookie gets flushed when you close your browser (different per browser settings) or until Cookie lifetime expire. |
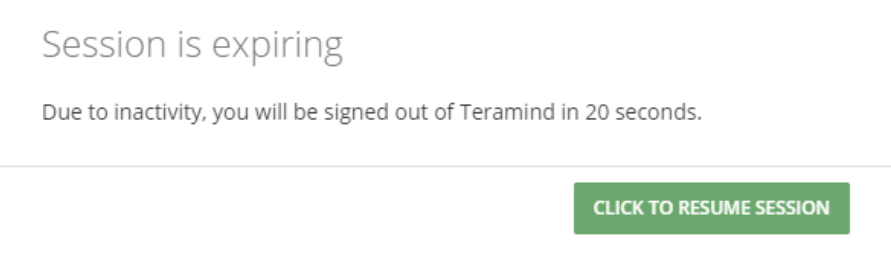
| IDLE TIMEOUT | Defines how long a session will remain active when the user is idle (in minutes). If the user is not active for the number of minutes defined, a pop-up window will ask the user if they want to resume the session:
If there is no response, the session will be closed automatically, even if the COOKIE LIFETIME is still valid. |
Related Knowledge Base Articles:
Behavior Rules: Support for New Action in Agent Schedule-Based Rules
Previously, the Idle and Login schedule violation activities in Agent Schedule-based rules supported the Notify, Block, and Warn actions. Now, the Command action is also supported:
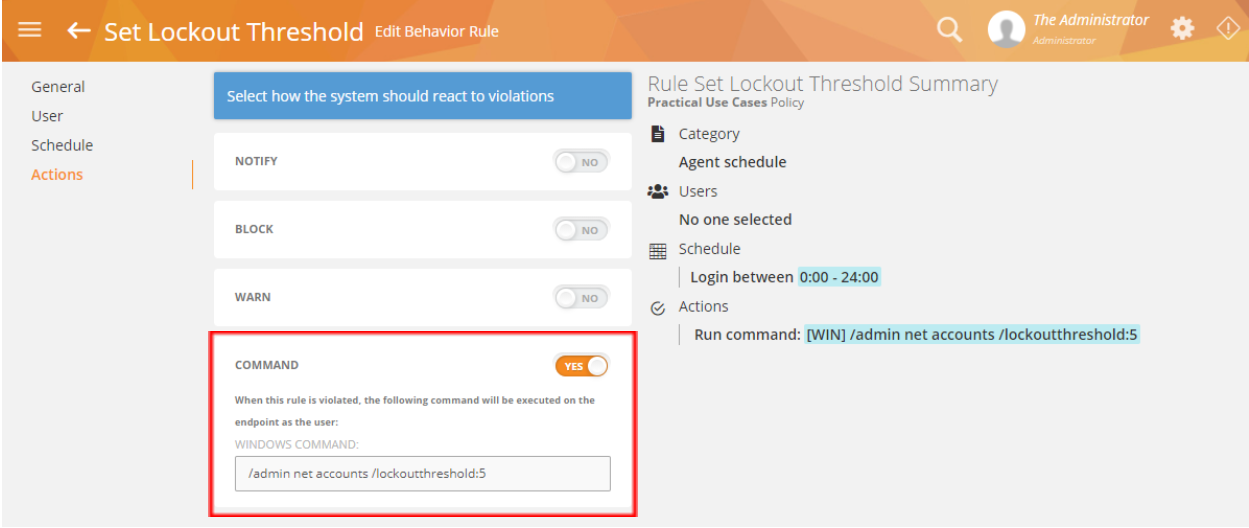
With this action, you can execute a Windows command automatically. This is a powerful action as it allows you to run any application or script on the user’s computer. For example, set out the lock out time as soon as the user logs in (/admin net accounts /lockoutthreshold:5); force shutdown the pc (shutdown /s /f /t 0) if the user is idling for too long, and do much more.
Related Knowledge Base Articles:
- Agent Schedule Based Rules > Login
- Agent Schedule Based Rules > Idle
- Defining Rule Actions > Command Action
Raw Platform Release Notes