We ended the year with a blast! A massive update was released over the holiday season consisting of 400+ new features, improvements, and bug fixes! Here’s a sample of what got published in our latest platform release. For a full rundown, check out the complete Release Notes here.
Table of Contents
Business Intelligence
Visualize Employee Locations with the Geolocation Map
We have added a new Map tab to the built-in, BI Reports > Geolocation* report. This tab will help you visualize geolocation coordinates (latitude and longitude) on a Map.
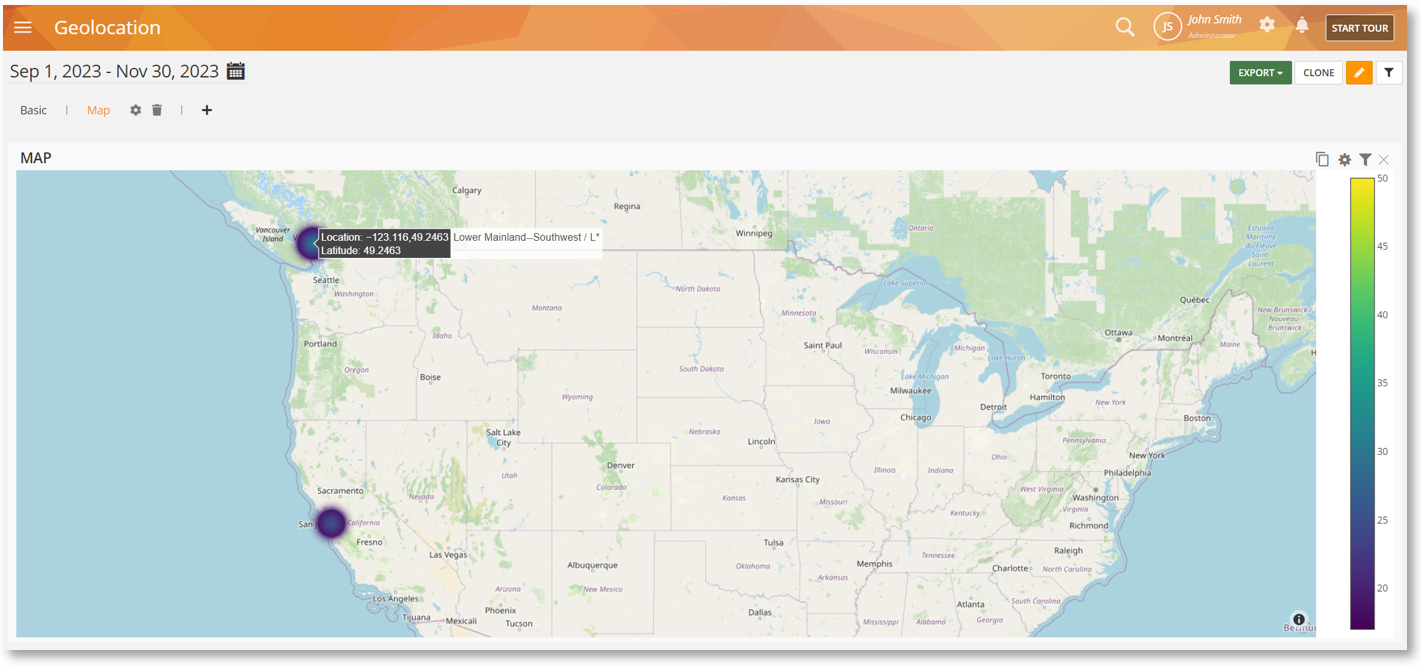
Note that you can also use the Geo Chart Widget to add a similar map to your own custom BI reports.
*As with all Teramind monitoring features, you can enable/disable geolocation tracking anytime.
|
i
|
Please see the BI Reports > Geolocation section on the User Guide for more information.
|
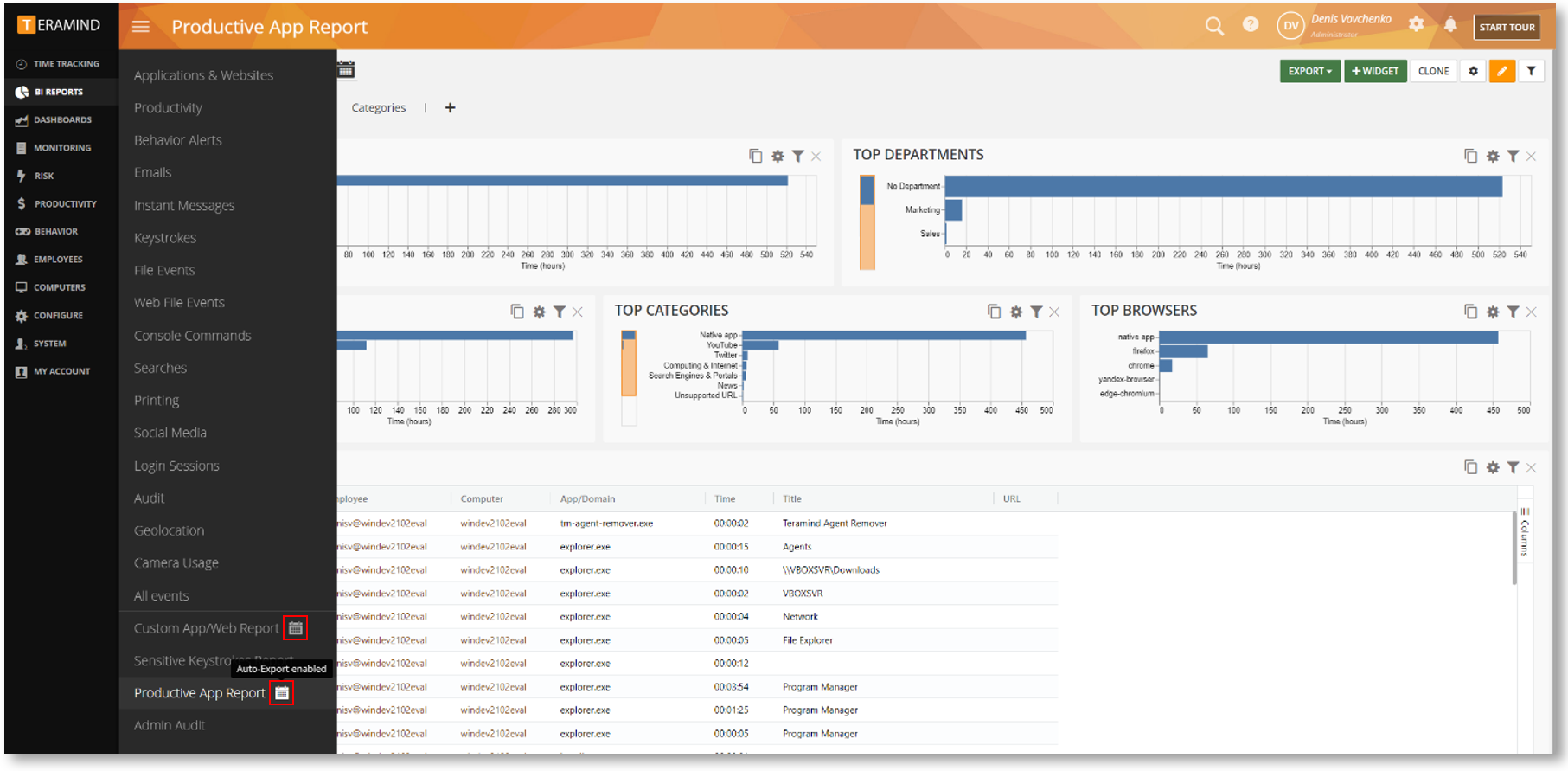
Easily Identify Reports Scheduled for Auto-Export
Previously, there was no easy way to tell if a cloned/custom BI Report was scheduled for auto-export (EXPORT > Schedule export).
Now, you will see a calendar icon next to a cloned report that has the schedule export option enabled.
Get a Cleaner Alerts Description for Email Rules
Previously, the Description and the Matched Triggers columns on the Grid widget of the BI Reports > Behavior Alerts would show the whole email body from an email-based rule alert.
Now, the columns will only show the relevant text(s) that match the rule’s condition(s). This will make the report more streamlined and cleaner.
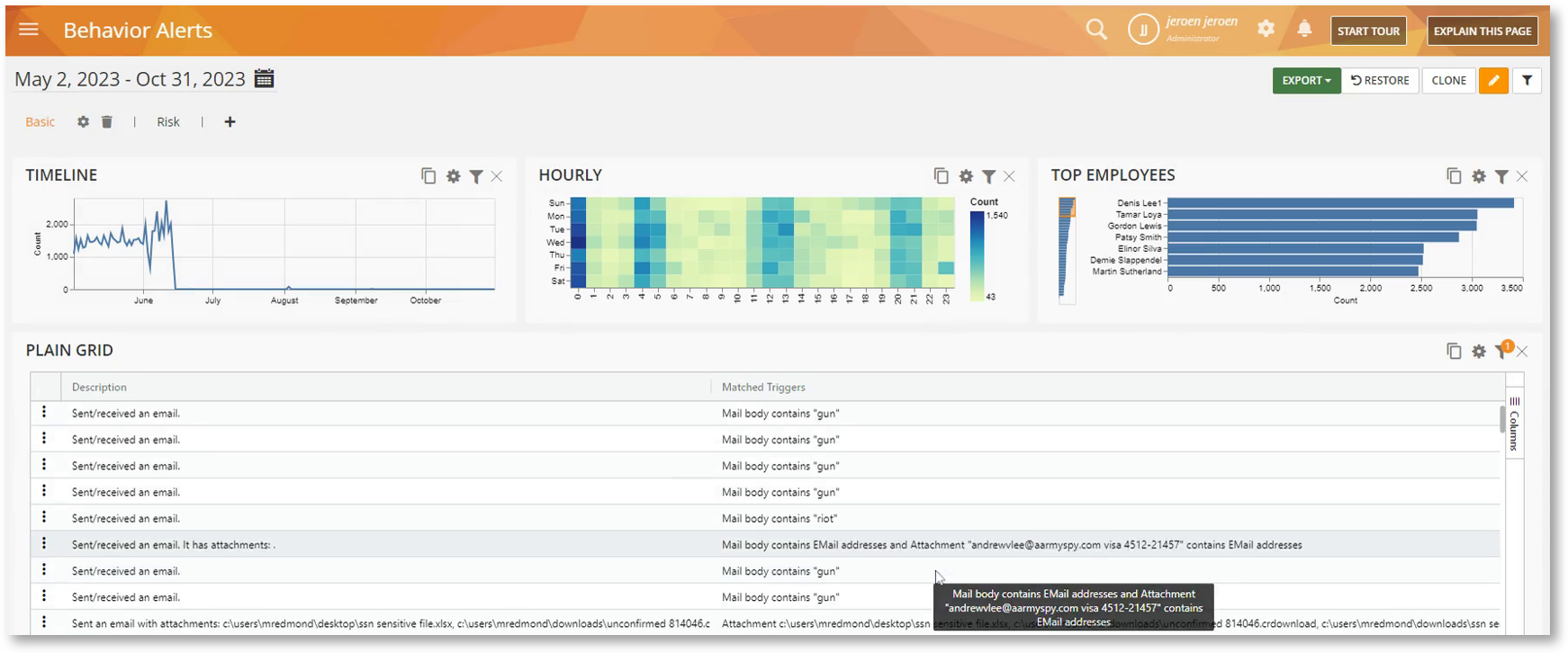
Note that you will still be able to view the full email by right-clicking an alert and choosing the Show details option.
Behavior Rules
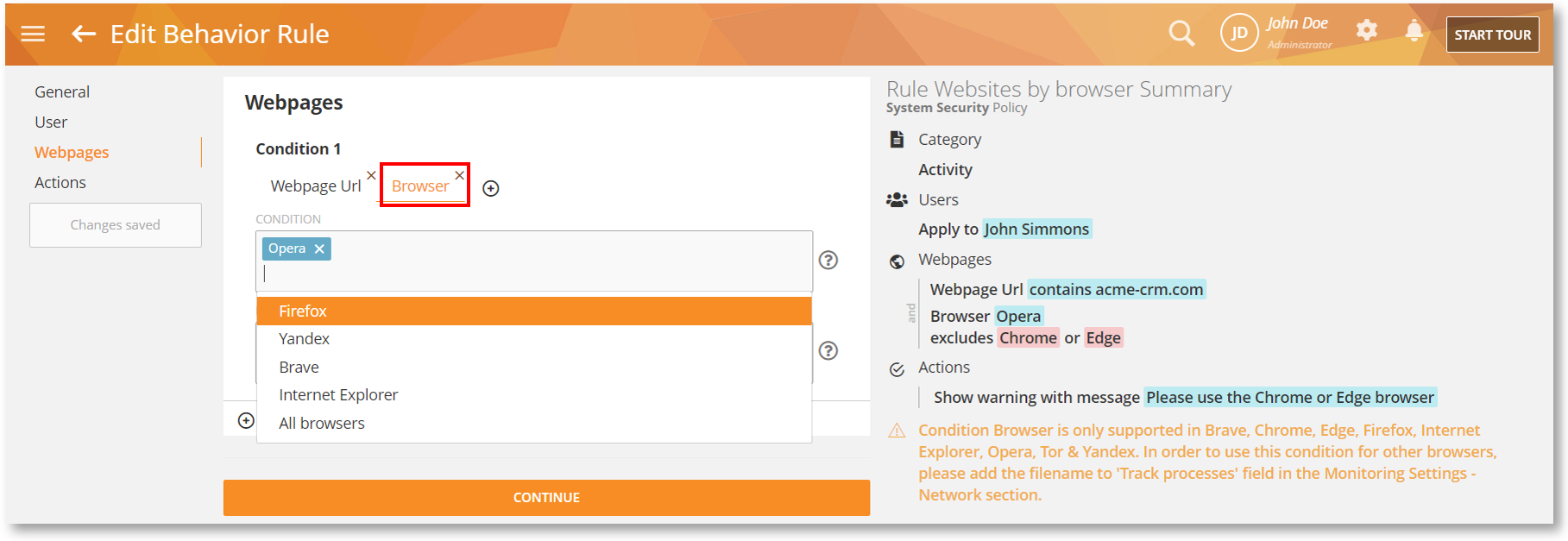
Intercept Specific Browsers with the New Rule Criterion
We have added a new criterion, Browser to the Webpages-based Activity rules.
Sometimes, you might want your users to use a certain browser for specific sites (e.g., a mainframe portal or a CRM SaaS application) for compatibility and security. Other times you might want to prevent the use of risky or unauthorized browsers (e.g., older versions of Internet Explorer, Tor, etc.).
This criterion will let you detect what web browser is used by the user and take any necessary action.
|
i
|
For more information, check out the Activity Rules: What Activities Can You Detect? > Webpages section on the Rules Guide.
|
User Management & Security
Create Granular Role-Based Access Control Policies
We are introducing a new Role-Based Access Control (RBAC) policy.
This type of policy will allow you to assign special management permissions in addition to the view/edit permissions to a regular employee. For example, you can assign a regular employee permission to edit other employees’ profiles, create behavior policies and rules, etc. – effectively elevating them to a unique role. Similarly, using the role policies, you can turn a department manager into a ‘semi-admin’ who can manage other users, computers, etc. like an admin but only those in his/her department (unlike an admin who has access to all users/computers).
When you create a new Access Control Policy (Configure > Access Control > New policy), you will be able to choose from the List (regular) or Role access control policies.
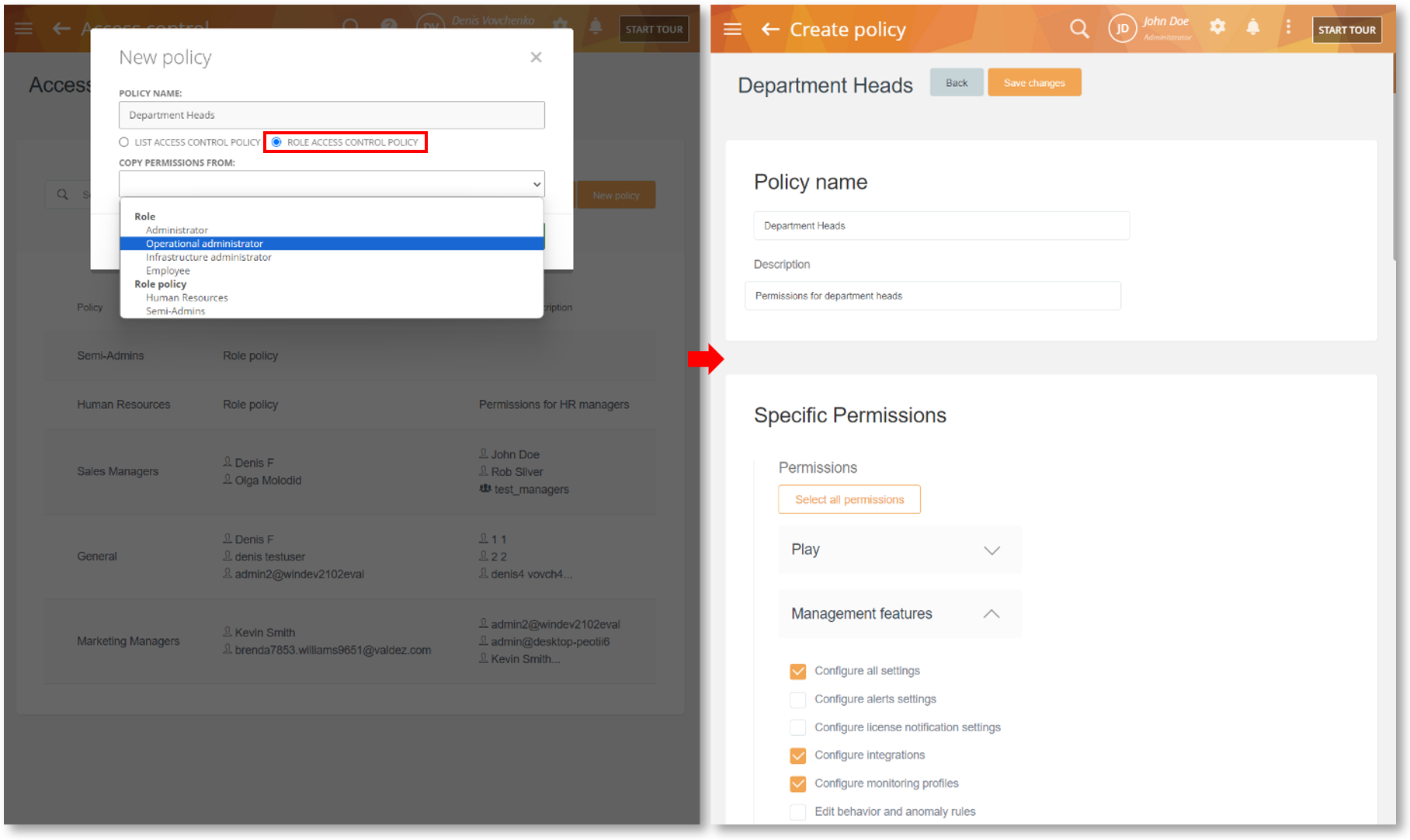
Once you have created a Role policy, you will be able to assign it to a user from their profile (Employees > Employee’s Details > EDIT INFO > RBAC tab).
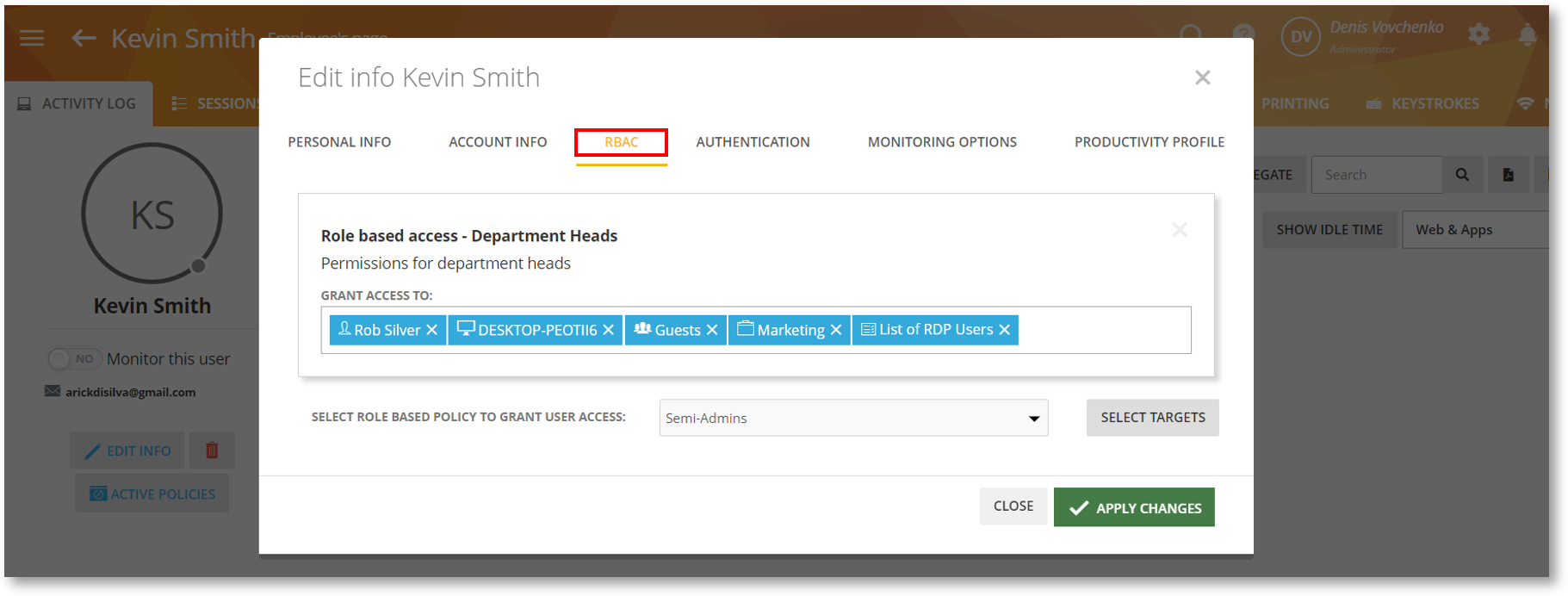
|
i
|
For more information, check out the Configure > Access Control Policies section of the User Guide.
|
Control Employees’ Access to Their Screen Snapshots Reports
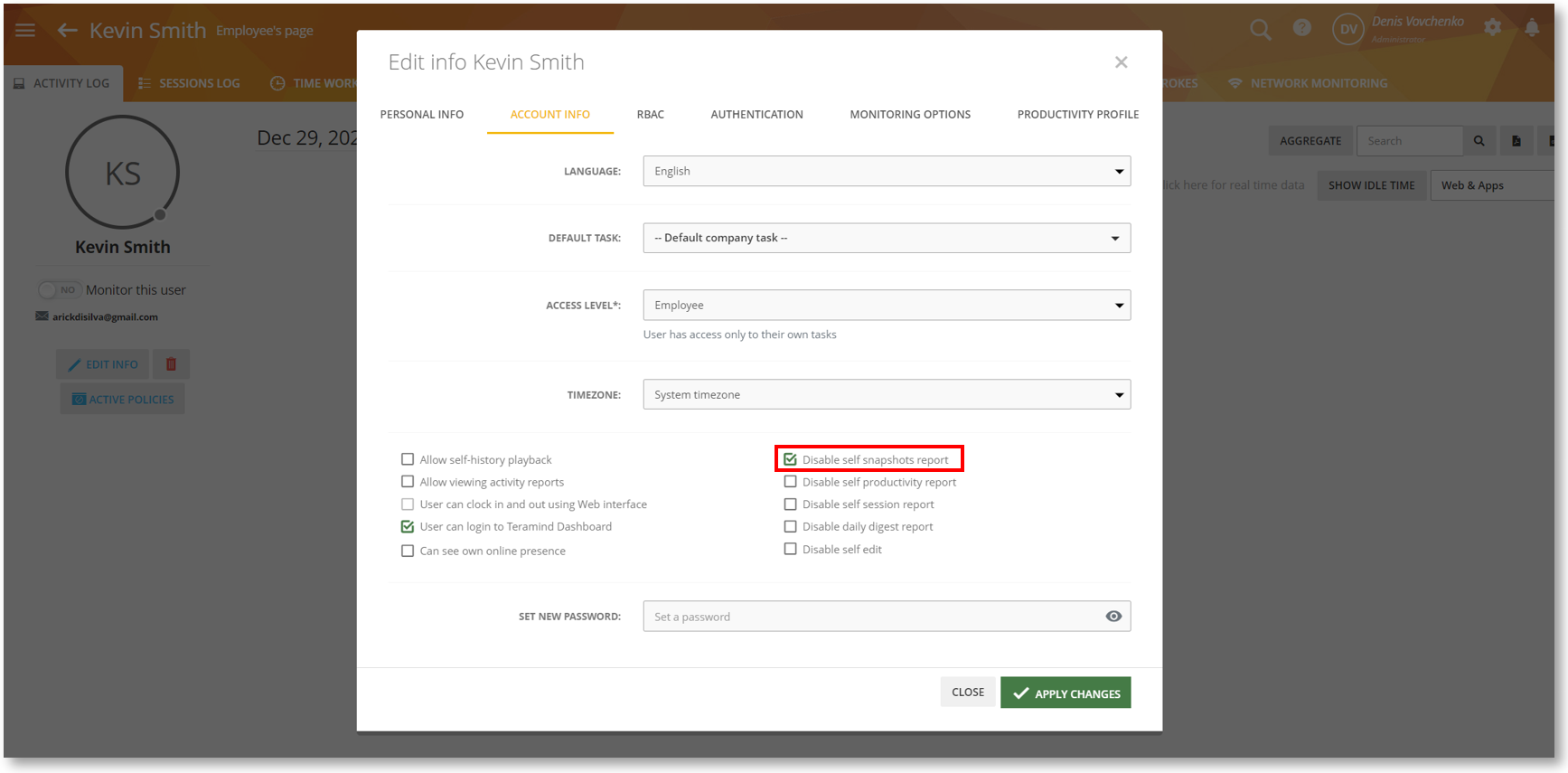
We have added a new option, Disable self snapshots report on the employee’s profile screen (Employees > Employee’s Details > EDIT INFO button > ACCOUNT INFO tab).
This option will determine if the employee will be able to view their Monitoring > Screen Snapshots report helping you be more selective about information exposures on a need-to-know basis.
Improve Your Login Security with the Password Expiry Time Option
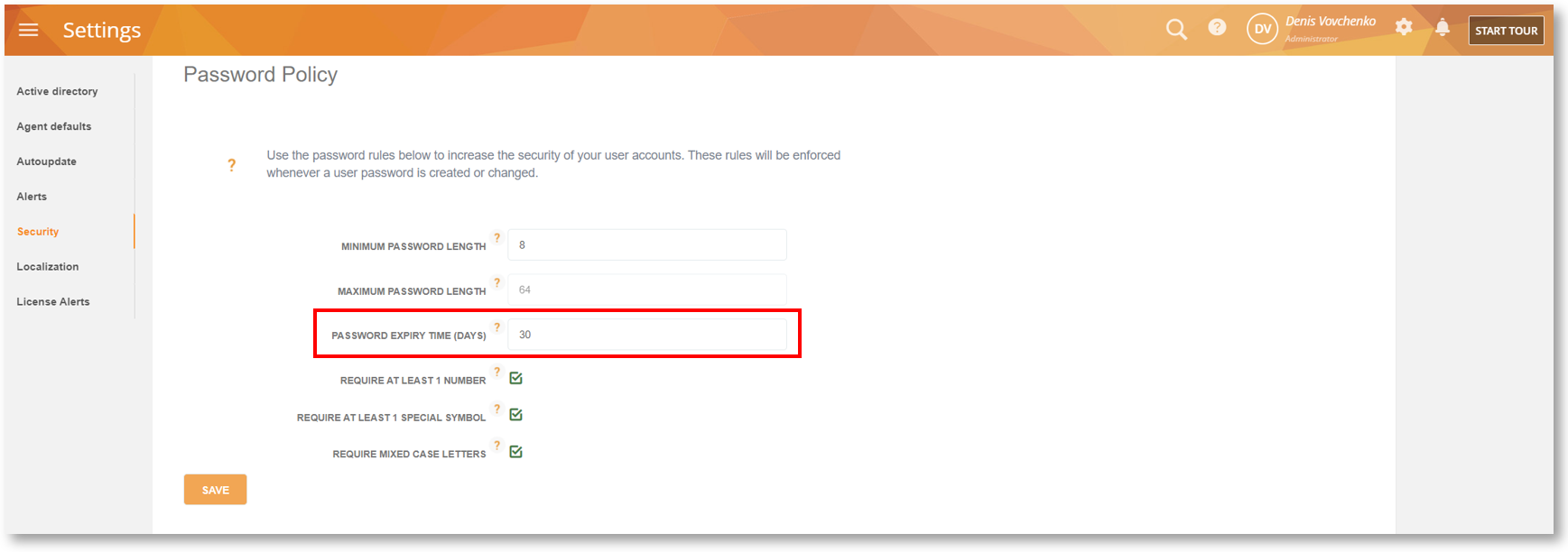
We have added a new option, PASSWORD EXPIRY TIME (DAYS) to the Settings > Security screen. This option will let you specify how long the password will stay valid. After this period, the user will be asked to change their password.
With this option, you will be able to reduce the risk of credential-based attacks as an attacker will have a limited amount of time in which to compromise a user’s password and get access to your instance.
Better Manage Your Deployment by Identifying Unlicensed Users
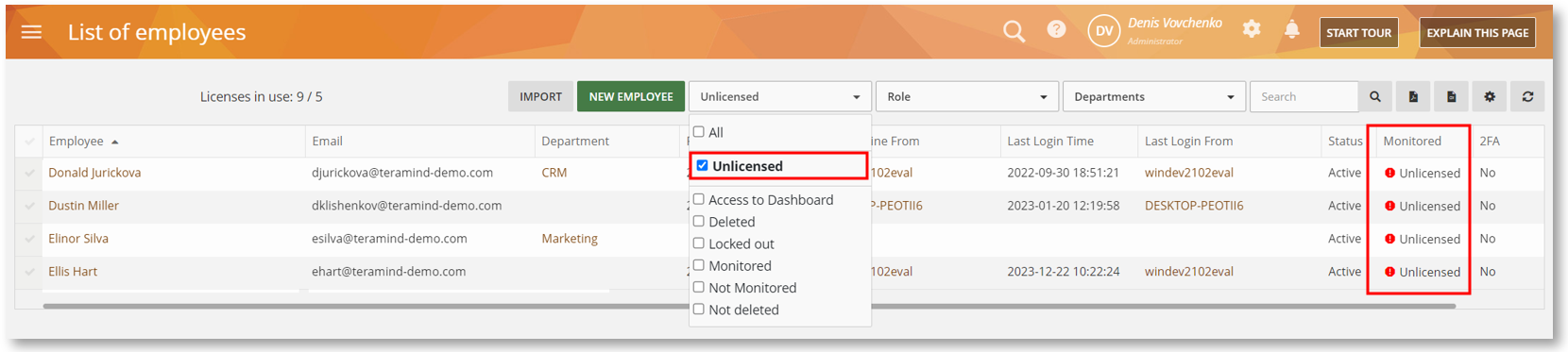
From now on, you will be able to see which users/employees are unlicensed under the Monitored column of the Employees report. You will also be able to filter the report by the Unlicensed condition.
This will help you find out if/why some users aren’t being monitored and take precautions to prevent license overuse.
Activity Tracking
Easily Monitor Departments and Groups with the Enhanced Monitoring Profile
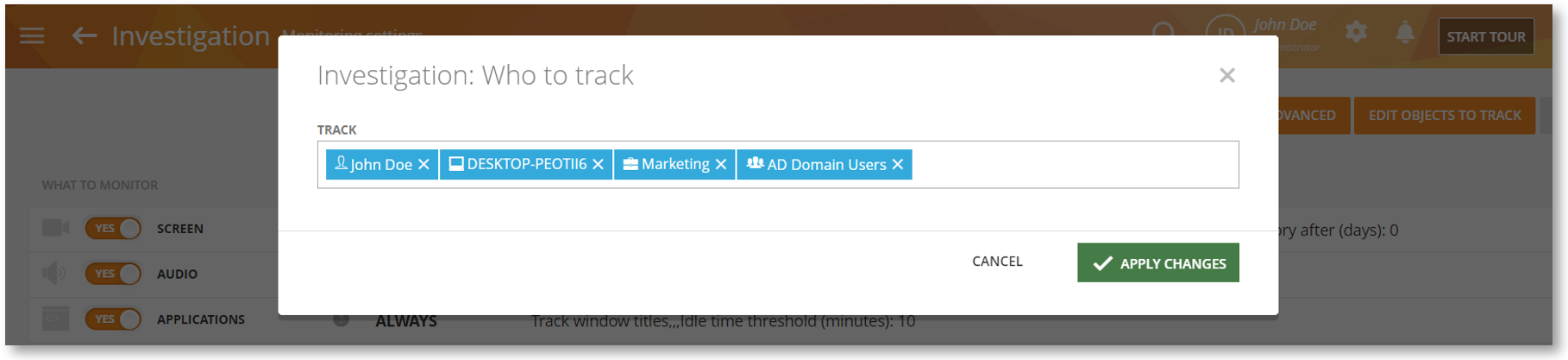
Previously, you could only add users and computers to a monitoring profile (Monitoring Settings > Monitoring Profile > EDIT OBJECTS TO TRACK).
Now, you will be able to add Departments and Active Directory Groups to the monitoring profiles.
You could already organize your data by departments or groups. This feature will let you similarly configure user tracking streamlining the entire data collection and reporting process. It will also speed up configuring monitoring settings for large teams by allowing you to assign AD groups and departments directly to a profile.
|
i
|
For more information, check out the Monitoring Settings section of the User Guide.
|
Get Granular Control Over Files & Network Monitoring
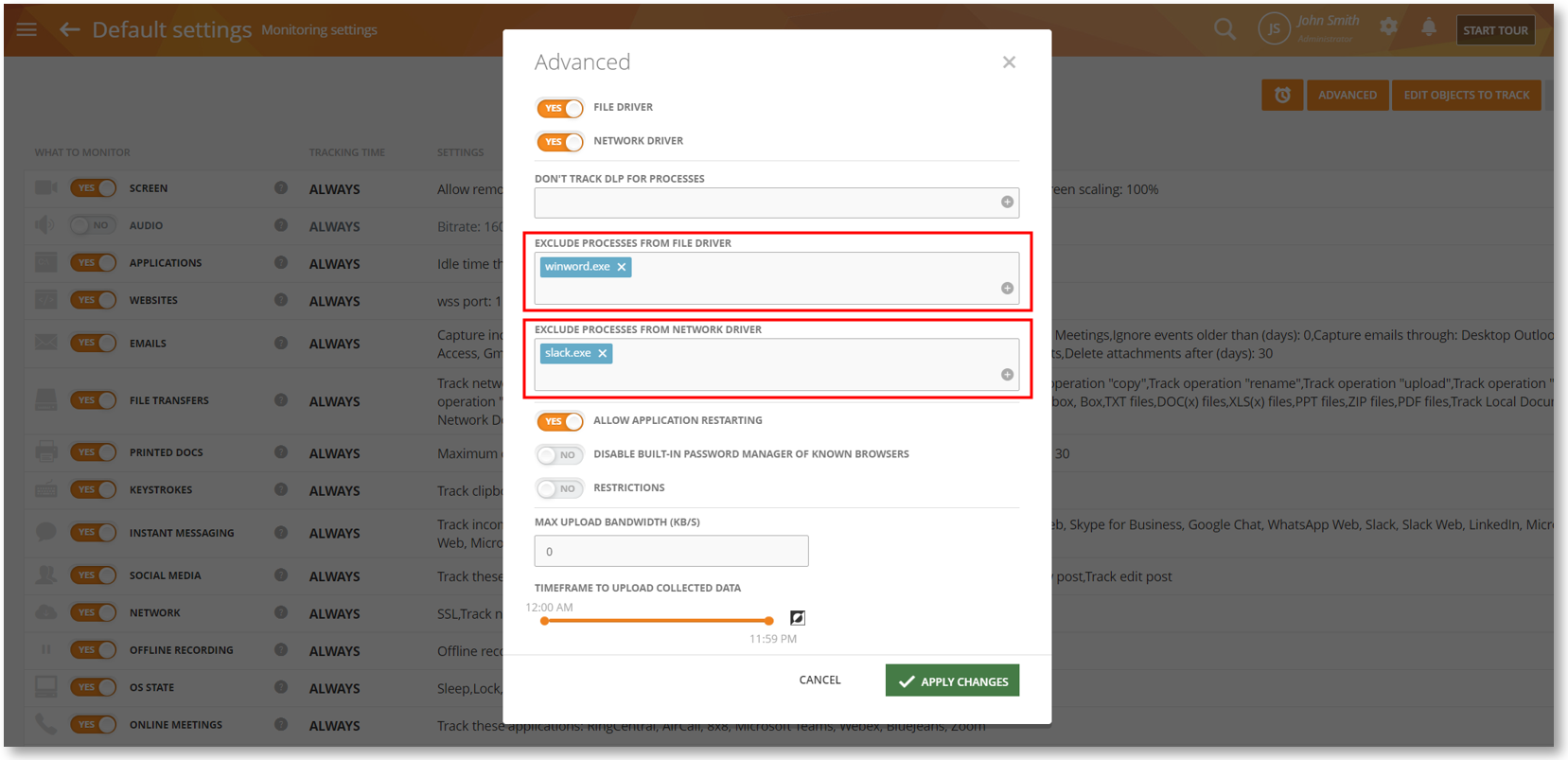
We have added two new options, EXCLUDE PROCESSES FROM FILE DRIVER and EXCLUDE PROCESSES FROM NETWORK DRIVER to the Monitoring Settings > Monitoring Profile > Advanced panel.
These are extensions of the existing FILE DRIVER and NETWORK DRIVER features. While those options allowed you to completely disable the drivers for all processes, with these new options you will be able to specify individual processes (e.g., “window.exe”, “slack.exe”, etc.) to exclude from file transfers and network monitoring.
These will be helpful for troubleshooting and performance tuning purposes such as identifying problematic applications by the process of elimination. These can also be used for privacy reasons such as preventing the capturing of file-related data in an app while still monitoring the app for other activities.
|
i
|
For more information, check out the Monitoring Settings > Advanced Monitoring Settings section of the User Guide.
|
Mac
Find Out Where Your Employees are with Geolocation Monitoring
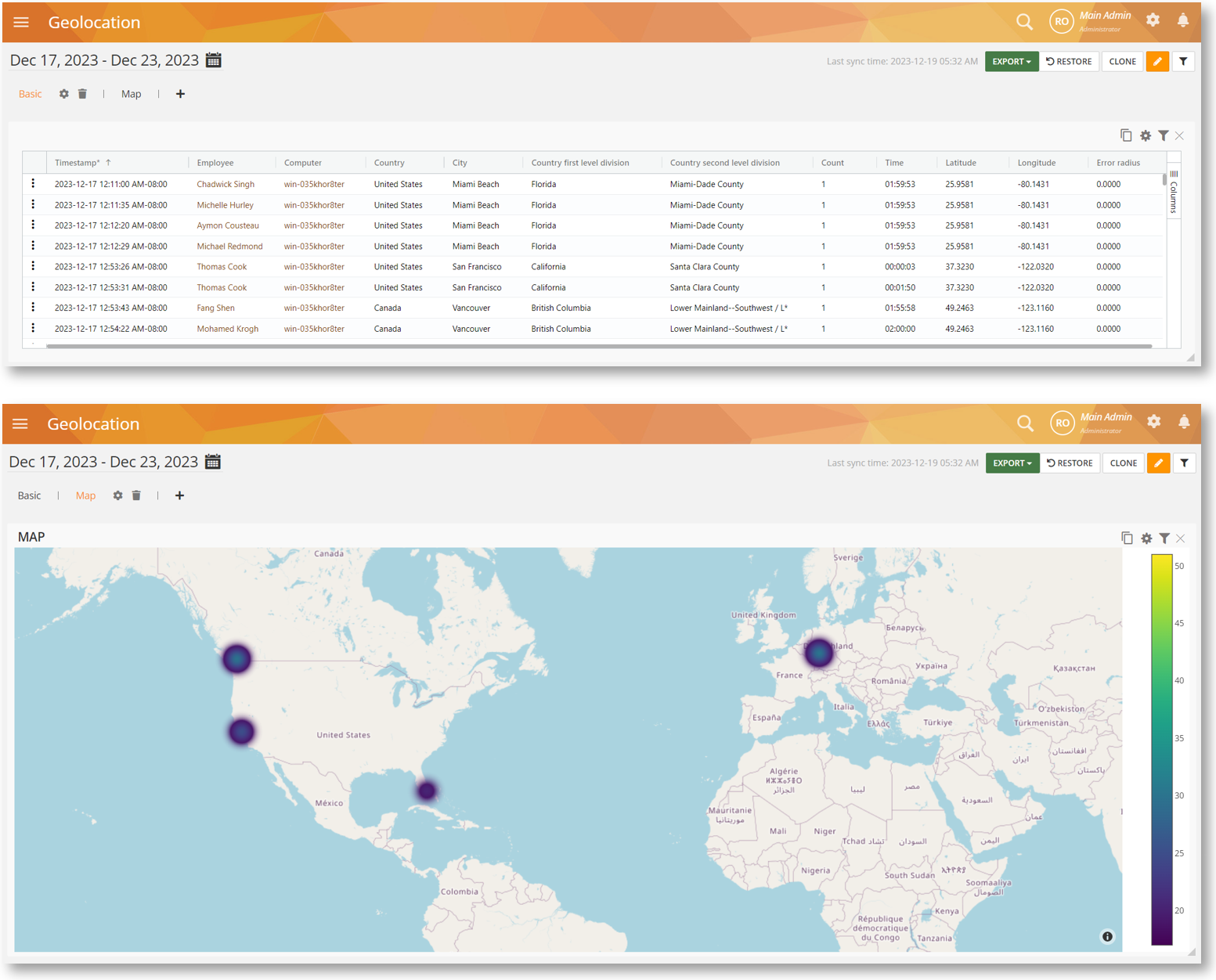
We are adding Mac support for Geolocation monitoring. You can track users’ geolocations from the BI Reports > Geolocation report.
Using this BI report, you will be able to track the location down to the country, city, local divisions, and the actual coordinates (latitude, longitude). You will also be able to view the locations on a map. The feature works even when the user is offline.
This might be useful if you have a remote, dispersed team or have field workers who work on different job sites. You can use the information for security, scheduling, payroll, and compliance purposes. For example, check for attendance, identify if an employee is working from home, track when a user is traveling abroad, etc.
|
i
|
Note that there might be some limitations and/or differences between the Mac vs Windows versions of this feature. For more information, check out this article: What features are supported on Mac? > Monitoring > Geolocation.
|
Prevent Leaks and Other Data Risks with Files Activity Rules
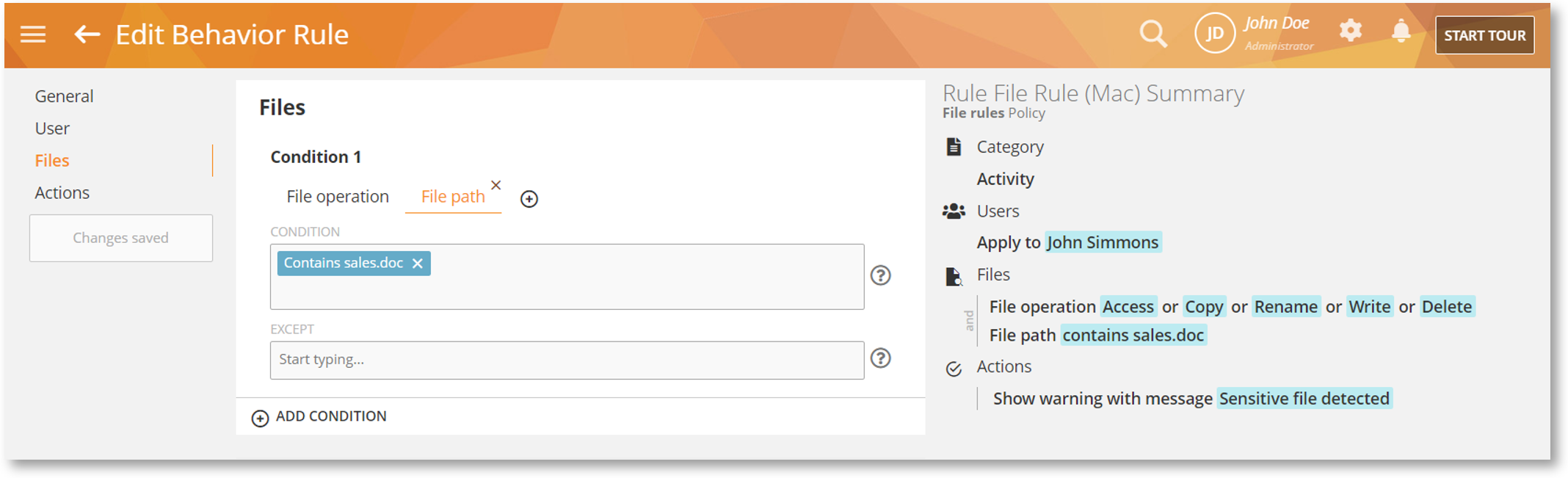
We have added Mac support for Files-based Activity rules.
With support for this type of rule, you will be able to detect file operations such as Access, Copy, Rename, etc., and take actions such as warning the user or blocking the activity.
This type of rule will help you detect and prevent data leaks, exfiltration, accidental deletion, tampering, and other threats to your data. Here’s an example:
|
i
|
Note that there might be some limitations and/or differences between the Mac vs Windows versions of this feature. For more information, check out this article: What features are supported on Mac? > Behavior Rules > Files.
|
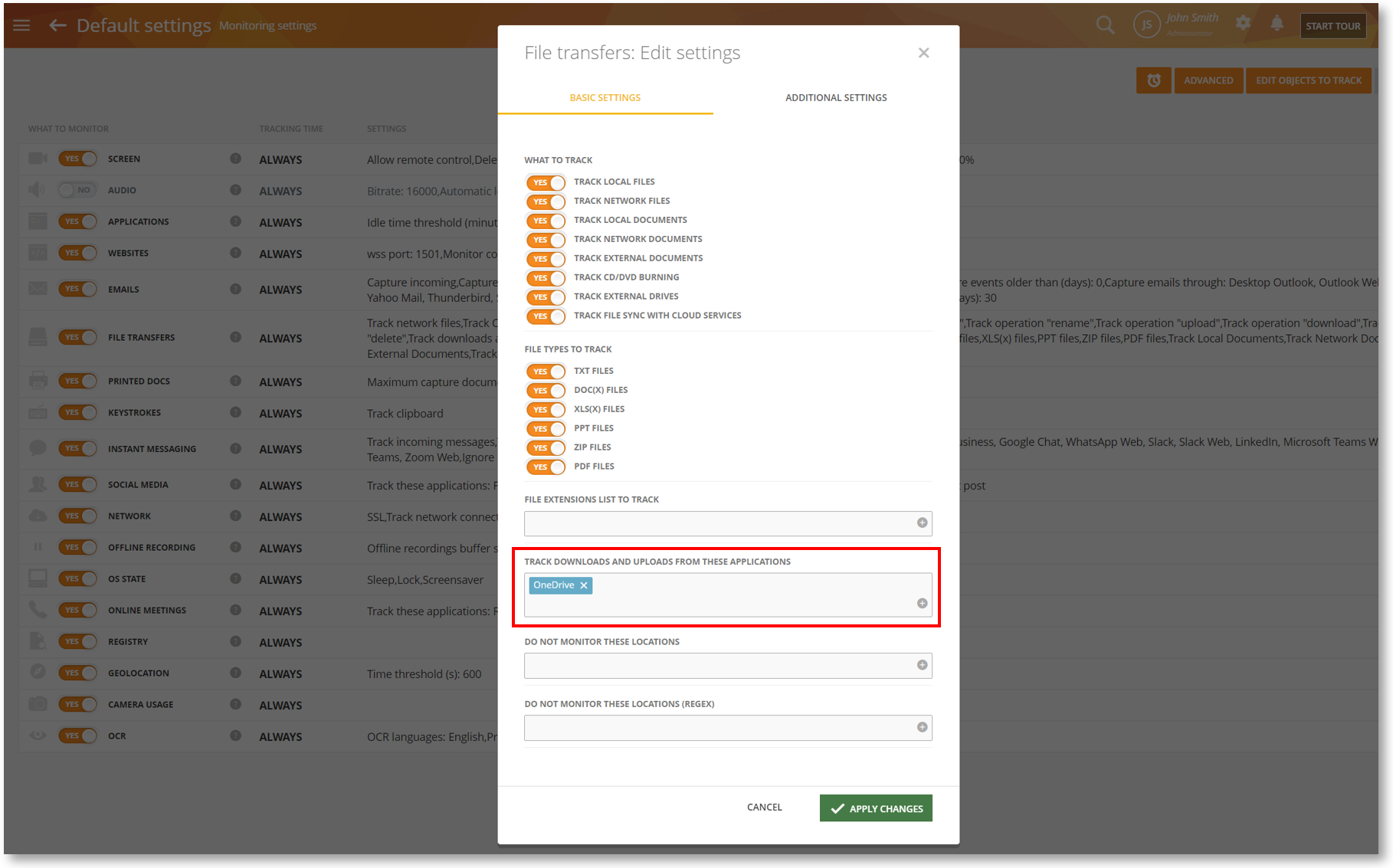
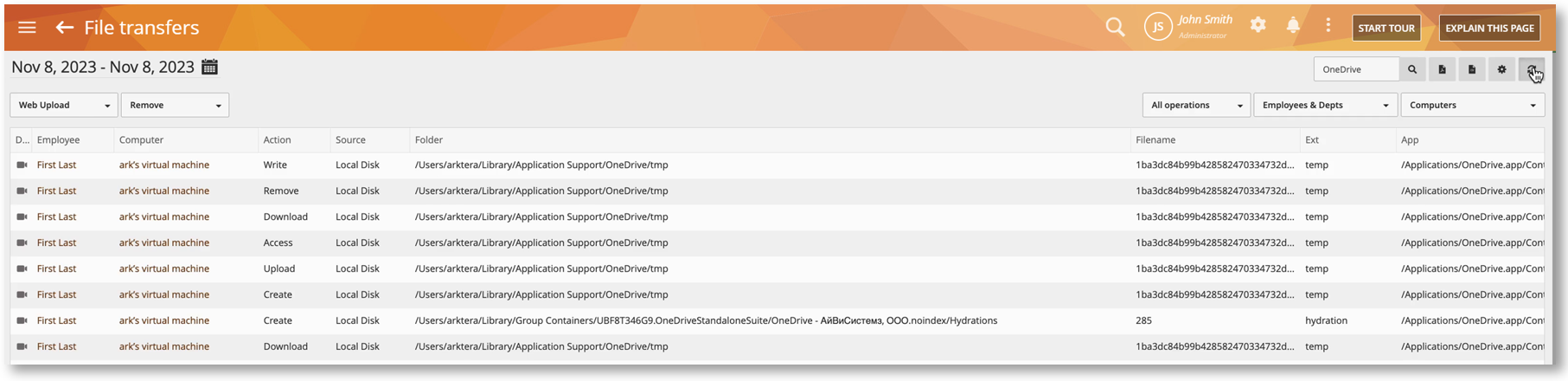
Detect Cloud File Transfers with OneDrive Monitoring
We have added Mac support for the TRACK DOWNLOADS AND UPLOADS FROM THESE APPLICATIONS option on the Monitoring Settings > Monitoring Profile > File Transfers settings screen. The activities can be viewed on reports such as BI Reports > File Events, Monitoring > File Transfers, etc. At the moment, this will let you track file uploads and downloads to/from the OneDrive app. In the future, we will add support for other apps such as Google Drive, Dropbox, etc.
Other New Features & Improvements
There are a lot more improvements packed into this release with several general enhancements to the deployment management, UI, settings, security, and performance. Below are just a few of them. Check out the full list here to get the details.
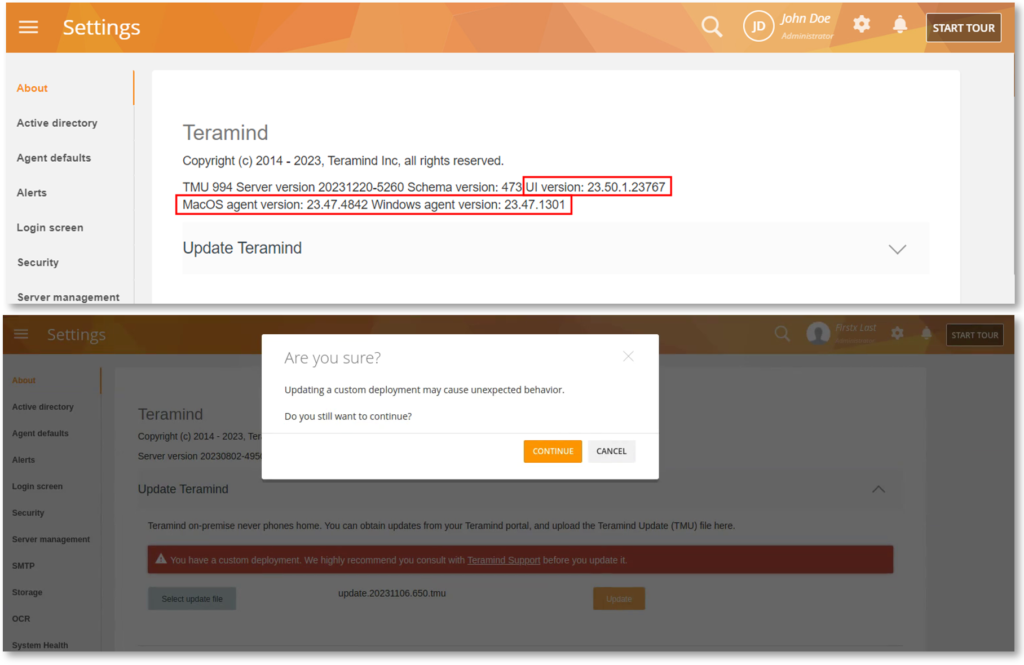
Easier On-Premise Deployment Management
New On-premise-specific improvements include: a new UI versioning scheme, the ability to view the Agent versions on the server, and showing a warning when trying to update a custom deployment.
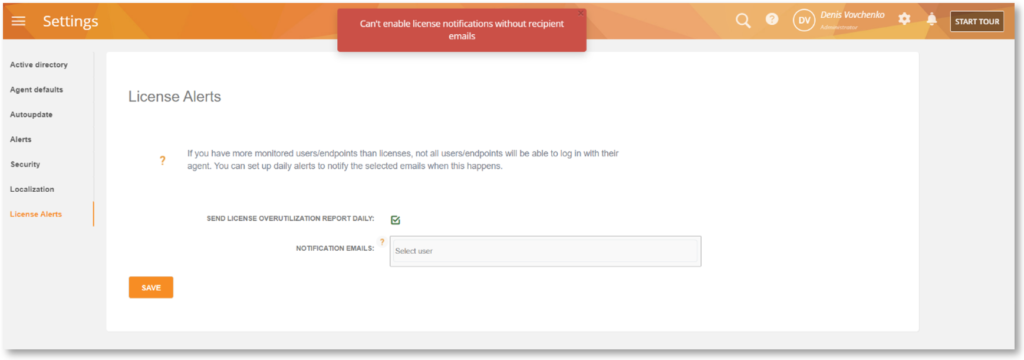
Better User Interactions
Email validation for License Alerts notification, Auto-hiding of the Camera icon (Session Player) for unauthorized users, better handling of notification messages, and more.