Teramind’s privacy features help maintain employee privacy and compliance with privacy laws
The rise in popularity of employee monitoring software has provided solutions for the many issues businesses face surrounding cybersecurity and productivity assurance. While certain problems have been resolved by employee monitoring strategies, new issues have cropped up, especially in today’s privacy-minded digital world. A growing concern for employees and businesses alike is the abuse of employee monitoring software.
Mishandling collected data or misappropriating the software can have dire consequences. Businesses not only run the risk of losing employee confidence and endangering office culture, they’re also subject to heavy fines and possible lawsuits due to the increased prominence of growing privacy laws and regulations, like Europe’s GDPR and California’s CCPA.
Fortunately, such instances of maleficence can be avoided with proper management and by fully utilizing Teramind’s privacy suite features. Following these five best-practices, which can be implemented with Teramind’s privacy features, will help create a law-abiding and employee privacy first monitoring strategy.
 Learn How Businesses Benefit from Investing in Privacy
Learn How Businesses Benefit from Investing in Privacy
Capture Only Necessary & Useful Data
Customize configurations & settings to get only the data that you need.
Screen recorded sessions and keystroke logging are crucial features and at the center of employee monitoring. This type of employee surveillance provides valuable insight into workplace productivity and is the first step in detecting data breaches. But with improper and overuse of screen and keystroke recording, it can lead to an invasion of employee privacy, creating an environment of distrust. Relying on Teramind’s granular configuration controls help combat such offenses.
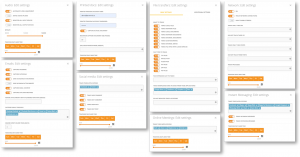
Teramind’s configuration settings allow for both broad personalization and pointed customization. Recording and activity monitoring can be set on the departmental or individual level, in addition to selecting individual website and application monitoring, file monitoring, email or messaging surveillance and network-use tracking. Limiting what is monitored, when it’s monitored and how it’s monitored is the first step to establish monitoring practices that respect boundaries and ensure employees’ privacy rights remain intact. In 2020, when much of the workforce moved home, the line between professional and personal activities blurred, but in employee monitoring it’s essential that this line remains defined.
Reasonable and legitimate tracking is key to creating healthy monitoring practices that don’t overstep; tracking only select activities, websites and apps is essential to achieving a privacy first monitoring strategy.
Exercise Full Transparency When Monitoring
The Revealed Agent keeps your employees comfortable and your monitoring compliant.
Employee monitoring software allows businesses to collect beneficial metrics for the purposes of productivity and can provide a frontline defense for data security. A misstep in deployment of surveillance strategies, however, can grossly violate privacy laws. The first of the seven pillars of Europe’s GDPR laws, for example, is consent and transparency. Not only must data subjects—or in the case of workplace surveillance, the employees—be notified that their work sessions are being monitored and recorded, consent must also be granted.
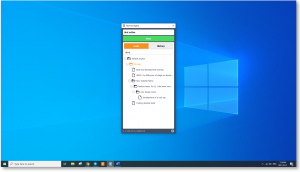
With this concern in mind, Teramind’s Revealed Agent resolves such transparency issues. Providing the necessary consent required by laws like GDPR, it can also allocate monitoring selections to the user. Users can select when system monitoring begins and ends and select what tasks and projects are being tracked. Giving employees the autonomy to control their recorded sessions offers clarity and provides surveillance transparency, a necessary aspect of employee monitoring for both legal and ethical purposes.
Store Employee Data Privately & Rationally
Teramind’s On-Premise Deployment lets you store your company data privately.
The possibility for data mishandling and privacy abuse goes beyond setting up and deploying monitoring software. The employee data obtained during monitoring sessions may also be subject to mistreatment if stored improperly. Teramind’s data retention and deletion policy features add another layer of assurance to defend against data being improperly used after it’s collected.
The Teramind Cloud—where monitoring sessions and activity logs are stored automatically—deletes data older than six months. By utilizing the On-Premise, or private cloud, data retention settings can be customized to better suit the privacy laws in your jurisdiction and the privacy of your employees. Additionally, On-Premise allows for the full deletion of collected data, including typically cached metadata.
Through Teramind’s data privacy export controls, restrictions can be put in place to limit where data can be exported to. Exported reports help pinpoint problems in workflow and are invaluable for productivity analysis, but exporting to the wrong location or network can impede employee privacy and, depending on your local privacy regulations, can be considered unlawful behavior. Limiting where outgoing data can go defends against such missteps and provides yet another layer of privacy and data protection.
Limiting the possibility of data exposure points is integral in protecting employees’ privacy and creating a privacy first monitoring strategy. This applies not just to where their data can go, but who has access to it as well.
 Learn How to Benefit from Building a Privacy Aware Team
Learn How to Benefit from Building a Privacy Aware Team
Control and Limit Access to Collected Data
Access permissions settings keep data safe and out of the wrong hands.
While supervisors, managers, executives and IT professionals can all garner relevant information from employee behavior data, limiting access to collected employee data is requisite to establishing a legitimate employee monitoring plan. Productivity and activity surveillance can quickly become uncensored and threaten employee privacy if it’s overly accessible. Custom permission settings and access controls that help minimize this risk are included in Teramind’s privacy features.
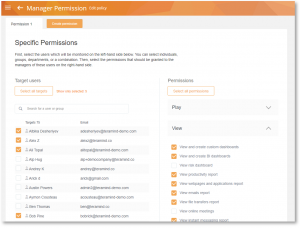
Role-based access control, or RBAC, enables permissions for groups or individuals to retrieve, view, or edit monitored employee sessions or activity logs. This segregation of access allows only those with expressed permission to obtain the employee data selected. Granting departmental privilege assures employee privacy and decreases the possibility of unauthorized employee data distribution. User authentication controls add even more security ensuring employee data remains protected, even if privileged user credentials are stolen.
Monitor Reasonably and with Restraint
Screen recording controls and audit logs ensure monitoring has limits.
Without oversight or prudent management, employee monitoring can quickly shift from useful to intrusive. Software administrators can endanger employee privacy if too much monitoring occurs. A balance must be struck between determining what data is useful and what’s considered over the line. Teramind can record employees’ screens with a feature called session recording. Limiting these screen recordings can protect against over-monitoring and are an integral part of any privacy first monitoring strategy.
In addition to configuring monitoring to avoid personal data & passwords, you can also limit screen recordings. Screen recordings can be configured to only capture activity surrounding a rule violation or set to display a message on the users screen when they’re being recorded. Limiting activity recording falls in line with purpose limitation guidelines set forth by the GDPR, and becomes particularly useful when monitoring remote team members or employees who use their personal computers.
Audit logs help keep employee monitoring in check too. These logs not only maintain compliance with various privacy laws, they also allow you to view administrator activities in order to make sure employee monitoring is being done in good faith.
 Learn more about Employee Data Privacy Laws in 2021
Learn more about Employee Data Privacy Laws in 2021
Conclusion
While software like Teramind will bolster productivity and business growth, it can also be exploited without proper implementation and oversight. The side effects can have detrimental implications, both ethically and legally. Not only can mishandling the software encroach on employee privacy, indecent use can result in illegal data handling practices.
The true purpose of Teramind isn’t to chaperone employee behavior and activity, but rather to stimulate productivity and strengthen data security. Issues surrounding increased privacy concerns and data usage can be easily mitigated, providing the deployment and management of the software takes full advantage of the privacy-first features.
Learn How to Setup Teramind for Privacy-Friendly Monitoring



