In January 2024, Cloudflare employee Brittany Peach achieved social media virality when she recorded a video of her former company firing her and posted the exchange on TikTok, where it was viewed millions of times and featured as front-page news across mainstream media platforms.
She’s just one of many employees recording and posting their layoff meetings online. This trend is accelerating as more companies make staffing cuts.
However, these videos reflect more than just a viral internet trend. They also unveil a severe workplace problem: employees don’t trust their employers.
Commenting on this trend, Johnny C. Taylor Jr., president and CEO of the Society for Human Resource Management, recently told Wired, “Both sides just don’t trust each other as much as they did.”
This swirling dynamic of diminished trust and potential job insecurity has many consequences, and increased exposure to insider threats is at the top of the list.
Insiders are leaders, employees, contractors, and trusted third parties with access to company data and IT infrastructure. When these insiders feel wrongly terminated or sympathize with recently laid-off coworkers, they are more likely than the average person to become an insider threat, leveraging their privileged access to steal information, misuse data, or otherwise compromise a company’s IT infrastructure.
Hackers are also happy to capitalize on diminished trust between employees and employers, actively soliciting workers and finding a receptive audience.
You Probably Didn’t Think Your Employee Would Do This
Every insider is unique, but they tend to fall into broad categories.
Some insiders are accidental, making mistakes that inadvertently compromise sensitive information. It’s a problem, but it’s also preventable and certainly not intended to hurt the company.
Others are malicious. They are angry, out for recompense, sabotage, or personal gain. These malicious insiders don’t have to try very hard or look very far for opportunities to achieve each of those goals.
Teramind consulted with an anonymous DarkNet hacker who uses their talents to achieve good in the world. This source showed us the alarming connection between once-ordinary employees and DarkNet bad actors, illustrating the close connections between malicious insiders and the web of black market opportunities on DarkNet.
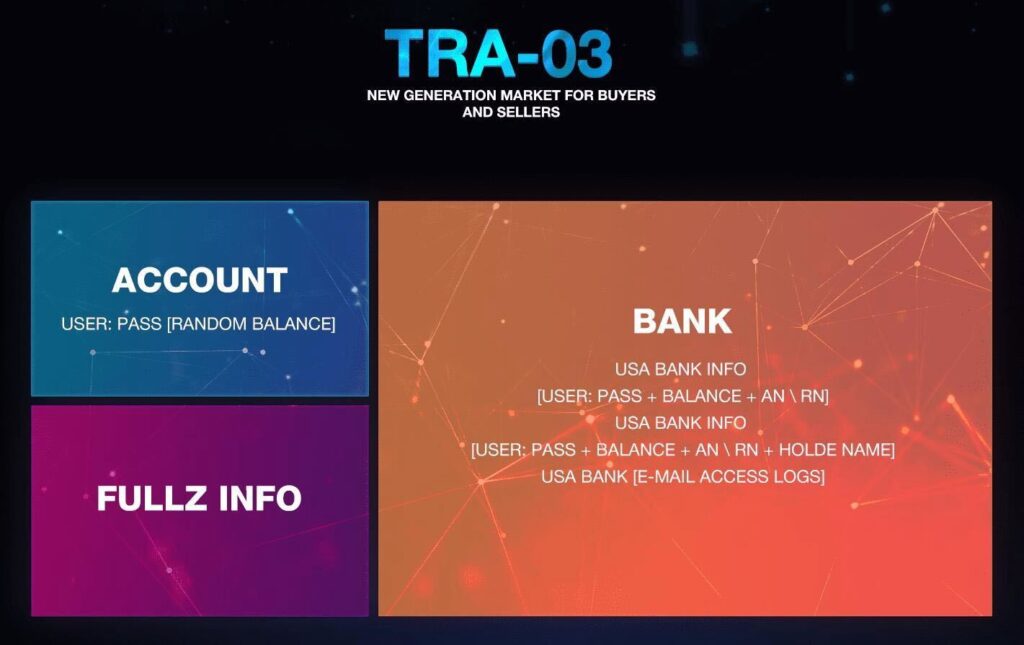
Here’s how it typically works…
Exiting Employees Seek Revenge
When employees are upset about a company’s direction, managerial decisions, or perceived workplace slights, they are an easy target for DarkNet hackers.
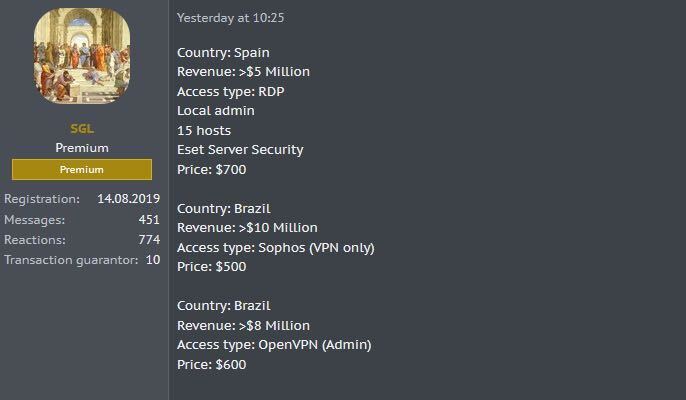
There are several DarkNet postings every day highlighting hackers willing to pay for their corporate access. It’s an easy way to make a quick buck while exacting revenge against a soon-to-be former employee.
These incidents can be especially difficult to detect after an event as hackers guarantee their account will not be used for the attack, just for entry. This allows hackers to reuse these credentials in the future and to preserve the relationship with the employee who may sell access at their next job too.
Insider Agents Help the Hackers
Insider agents work on behalf of an external group that, in some way (knowingly or unknowingly), helps the hacker.
For example, some work for placement companies that give 90-day trials to the people they select. The placement employee works for a short time, sells their access for quick cash, and moves on.
Some will work with a ransomware as a service (RaaS) group ahead of time, and for access, they receive 10-20 percent of the ransom collected. They then start searching for employment in a company. Once hired, they give access to the RaaS group, who then attempt to use ransomware and collect a significant ransom fee.
Third-Party Insiders Compromise Data Integrity
Contractors, vendors, and supply chains have both access and permissions on the network. Sometimes, it is easier to infect one of them than the direct employee with malware like backdoors or network crawlers that can call out.
With third parties, there is also the ability to discover zero-day exploits on their applications and use them against a company.
In almost every case, money’s the motivation, but employees can be bought for a shockingly small sum. For just a few hundred or thousand dollars, hackers can acquire login credentials that unlock access to invaluable corporate assets.
What Can You Do To Stop Insider Threats?
This Dark Net connection poses a serious threat to any company’s defensive posture. For as little as a few hundred dollars, your network is prone to front-door intrusion by a malicious hacker bent on costing your company millions of dollars in damage.
Fortunately, prevention is possible.
First, you have to know two things: what is your secret sauce (what makes your company unique?), and what would a hacker want from you?
Every organization has something valuable, so avoid the temptation to assume you are too small, too secure, or too anything. Hackers attack for three reasons: riches, reputation, and regulations.
If you can understand that about your company, you will understand how you are a target.
Next, build your network accordingly.
Find all your secret sauce and riches, and centralize them in one place. This allows you to focus your security efforts on a much smaller space.
Monitor who connects to this space and the data activity within it. The best practice would be to deal with virtual machines as your bridge to your centralized asset repository. By using virtual machines, employees can see work with the data, but they can’t email it, copy it, move it to an external storage device, or otherwise manipulate the information.
At the same time, limit administrative privileges and separate access to each of your crown jewels. Ensure that one admin has to log in with different accounts for each one to help data loss prevention (DLP) software identify abnormal patterns.
This makes it more difficult for a single user to steal something easily. It also makes it more likely that you will identify suspicious activity before it causes a serious problem.
Finally, leverage software that monitors endpoints, anomalous behaviors, and user activity to most effectively detect, investigate, and prevent insider threats.
The key components include:
• Endpoint Monitoring Solutions protect sensitive and confidential company data from loss caused by accidental, negligent, or compromised insiders.
• User & Entity Behavior Analytics Software exposes irregularities in system and user activities by leveraging advanced analytics to find suspicious behavior at any endpoint.
• User Activity Monitoring Platforms allow companies to identify and respond to malicious or risk activities with automated responses and enhanced, actionable insights.
By leveraging this powerful software, cybersecurity and leadership teams can capture and analyze behavior analytics that provide critical data insights and enforcement options for organizations, regardless of size or sector.
Defending Against Insiders In Any Form
Insider threats come in many forms, but today’s business environment makes it more likely that the risk of an insider doing the unthinkable is certainly elevated.
When coupled with the expansive ecosystem and market demand for their privileged information, it’s clear that companies can’t ignore this risk. Rather, every business and brand must take intentional steps to guard their data, intellectual property, and IT infrastructure against insider threats.
Teramind is your Insider Threat prevention partner. With a best-in-class solution suite that integrates key software solutions into a single, easy-to-deploy, and maintained platform, we are ready to help you fortify your organization against insider threats.



